© 2024 Eclypsium, Inc.
Infrastructure security has long been on top of the list of concerns for businesses. Increasingly frequent reports of supply chain attacks add to those concerns, whether it’s “spy chip” hardware implants, tainted firmware, or counterfeit components.
Modern manufacturing logistics and the globalization of current supply chains make it difficult to trace the origin and safety of the components inside a device. Your data center supplier must be able to provide assurance that it has tamper proof supply chains from the manufacturing facility all the way into your hands. Current supply chain practices start with trusting the source, but processes are limited to screening out counterfeit components, particularly for products containing many subsystems.
Eclypsium has partnered with Intel® to provide critical supply chain visibility inside its operational platform.
The number of entities targeted by supply chain attacks increased 235% from 2021 to 2022.
74% of IT Security professionals surveyed say their organizations are very committed to achieving a secure supply chain.
Firmware attacks have risen more than 500% since 2018.
Protect Production Assets
Improve mean-time-to-detection and the security posture for your enterprise IT.
Reduce Supply Chain Risk
Make better IT procurement decisions and quickly assess the impact of supply chain threats.
Lower Hardware Costs
Extend the lifecycle of devices by validating trust in low-level components.
Achieve Regulatory Compliance
Easily implement security controls for device integrity and firmware security..
Intel® Endpoint Cloud Services
Intel® Transparent Supply Chain
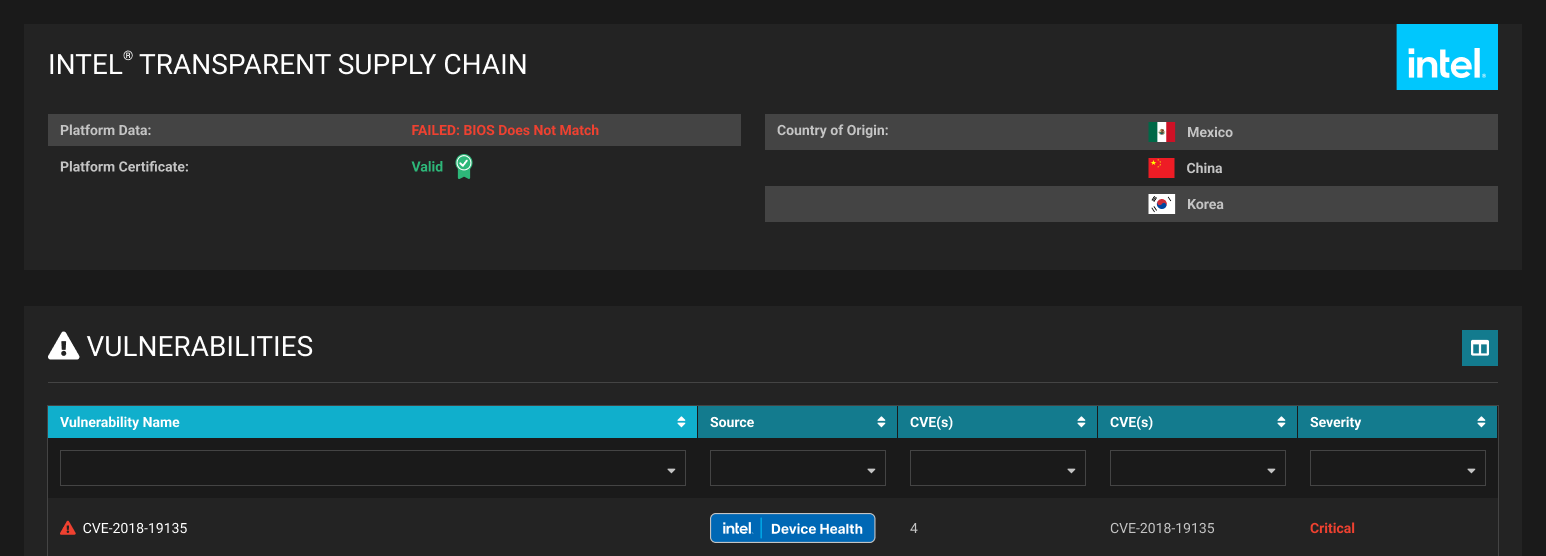
Intel® Transparent Supply Chain (Intel® TSC) is a set of tools, policies, procedures and data capture. It extends from motherboard production through the manufacturing factory floor to your data center, implemented on the factory floor enabling you to verify the authenticity of components, installed firmware, and the configuration of your systems.
- Trusted Computing Group compliant Platform Certificate
- Key “As Built” data fields covering details of sourcing and the supply chain
- Valuable tools to search, identify, and detect unauthorized changes within key below the OS areas such as firmware, microcode, and active components
Intel® Device Health
Intel® Device Health (Intel® IDH) automates the identification of foundational (e.g., bios, microcode, firmware) vulnerabilities across fleets of end points. Foundational vulnerabilities have potentially catastrophic consequences and are not found in most security scans.
- Accurate detection of infrastructure vulnerabilities at scale.
- Greater insights into PC fleet health to help teams prioritize remediation efforts.
- Full details including attack vector, base risk score and remediation recommendations.
Relevant Regulations
Regulation | Description |
|---|---|
Contractors’ Counterfeit Electronic Part Detection and Avoidance | |
Cybersecurity Supply Chain Risk Management Practices for Systems and Organization | |
Trusted device manufacturing, traceability, and transparency | |
NIST NCCOE SP1800-34 (A, B, C) | Validating the Integrity of Computing Devices |
Mandates plan to identify and mitigate relevant semiconductor supply chain security risks; access, availability, confidentiality, integrity, and a lack of geographic diversification in the covered entity’s supply chain |
Get A Demo
Take the first step in your journey to address digital supply chain risks and build a supply chain security program for your organization.