© 2024 Eclypsium, Inc.
Many of today’s enterprises are dealing with blindspots that create avoidable resource inefficiencies and security vulnerabilities.
Few security products go deeper than the OS, offering visibility into the core infrastructure code, manufacturing and patching processes, and digital supply chains that have made, and continue to power, your technology assets.
Enterprises need assurance they can’t get from a device manufacturer, or from a partial security solution, that the critical hardware, infrastructure code, and software they rely on has not been compromised.
Identify Verify Fortify
Enterprises need deeper and broader protection – now.
Eclypsium’s unified platform seamlessly patches and secures the low-level code that enterprise devices run on, so that your business can operate without interruptions, breaches, or risk.
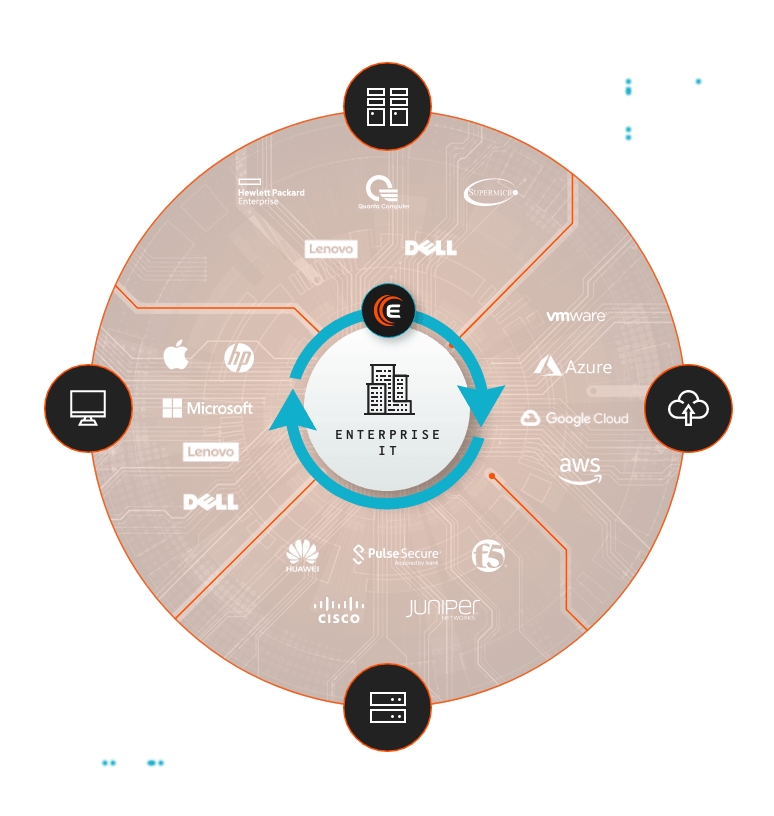
Identify every component of your devices for true visibility
IT estates today are sprawling and shadow-filled.
Enterprises need automatically-updating, complete inventories of their hardware, software and firmware that continuously monitors each device, and its components, across the digital supply chain.
Our platform goes beyond traditional endpoint security, automatically and objectively monitoring each connected product and device (including the new ones that pop up uninvited) for complete visibility and continuous vulnerability assessment.
Eclypsium discovers and illuminates your IT estate.
Laptops & Desktops
Servers
Cloud & Virtual Machines
Networking Devices
Verify that your infrastructure is trustworthy
You need to trust that your enterprise devices are authentic, compliantly manufactured, and have not been tampered with, whether throughout the supply chain or in a recent patch. You can’t rely on manufacturers or traditional security products to do this.
Each enterprise is responsible for navigating an increasingly complex marketplace, with evolving regulatory frameworks. That means taking nothing for granted, from the supply chain to daily technology use.
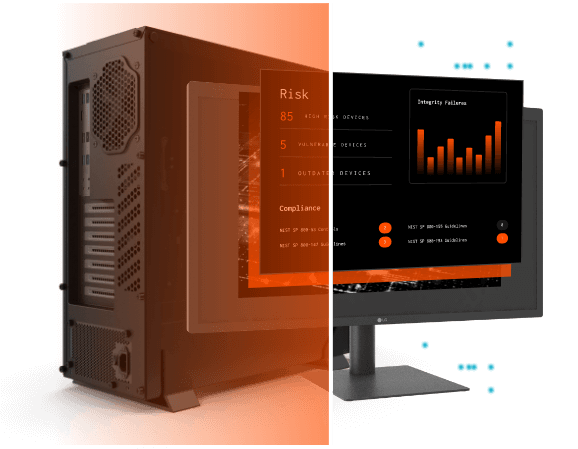
Assure that all components and protections are enabled and working together, that you’re compliant with standard regulatory frameworks, and that your configs and boot settings are getting the job done.
Eclypsium validates the trust you have in your devices.
- Verify integrity of every enterprise device
- Scale zero trust for every infrastructure code and device
- Verify that all equipment is genuine and has not been compromised
- Ensure compliance and align reports to standard regulatory frameworks
Fortify your entire estate, extending device lifespans
When you know your devices and infrastructure code are secure, it allows you to maximize the technology investments you’ve already made.
Continuously monitoring, updating, and patching your current devices means you don’t have to purchase new computers, phones, or routers on a regular basis just to stay ahead of emerging threats and regulatory changes.
Enterprises save resources and increase efficiency through remotely patching, updating, and fixing vulnerabilities on their existing devices.
Eclypsium keeps your existing devices running smoothly, with no downtime.
- Remotely patch and update your devices, with no glitches
- Identify and fix vulnerabilities and misconfigurations in your IT estates
- Assure that your current devices are safe and compliant to use for their natural lifespans
Trust every device with Eclypsium

ENDPOINTS

SERVERS