Attacks against enterprise VPNs have become some of the most common and critical threats facing enterprises today. As employees shift to working from home and become dependent on VPN access all day, every day, attackers have quickly found their newest high-value target. The industry has seen a spate of high profile vulnerabilities affecting leading VPN vendors that are being actively exploited by a wide range of threat actors. State-sponsored actors, including groups from China, Russia, and Iran, have heavily targeted VPNs as part of their operations. More recently, ransomware campaigns including REvil, NetWalker, and Maze have adopted the same techniques to gain enterprise access.
Organizations must know if their VPNs are at risk from these vulnerabilities. With Eclypsium, teams can easily maintain visibility into their VPN and other network infrastructure to find vulnerabilities, misconfigurations, as well as signs that the integrity of the device has been compromised. With this in mind, let’s take a look at some of the most recent alerts related to enterprise VPNs and how Eclypsium can help.
VPN Vulnerabilities, Alerts, and Bulletins
2020 has seen a steady drumbeat of VPN-related alerts from U.S. agencies, including CISA and the FBI. The following provides a chronological list of some of the most relevant examples:
- CISA Alert AA20-073A (March 13, 2020) – Calls out the increased importance of VPN security as organizations look to support increased demand for remote work due to the Covid-19 pandemic. Highlights the need to “update VPNs, network infrastructure devices, and devices being used to remote into work environments with the latest software patches and security configurations.”
- CISA Alert AA20-133A (May 12, 2020) – This alert details the CVEs most commonly exploited by foreign actors. The alert specifically notes an increase in attacks against VPNs including vulnerabilities in Citrix VPN appliances (CVE-2019-19781) and Pulse Secure VPN servers (CVE-2019-11510).
- USCYBERCOM Cybersecurity Alert (June 29, 2020) – Warning of foreign APTs likely to exploit CVE-2020-2021 affecting Palo Alto Networks firewalls and VPN devices.
- FBI Flash Alert MI-000130-MW (July 28, 2020) – Alert to the increase of Netwalker ransomware attacks on US organizations and agencies, noting that “Two of the most common vulnerabilities exploited by actors using Netwalker are Pulse Secure VPN (CVE-2019-11510) and Telerik UI (CVE-2019-18935).”
- CISCO Security Advisory (August 29, 2020) – Alerts to memory exhaustion vulnerabilities in CISCO’s IOS (CVE-2020-3566 and CVE-2020-3569) being exploited in the wild.
- CISA Alert AA20-258A (September 14, 2020) – Details a variety of TTPs associated with Chinese MSS-affiliated actors including the use of vulnerabilities affecting F5 Big-IP Traffic Management (CVE-2020-5902), Citrix VPN appliances (CVE-2019-19781), and Pulse Secure VPN servers (CVE-2019-11510).
- CISA Alert AA20-259A (September 15, 2020) – Details TTPs of Iranian threat actors targeting VPNs, specifically noting a variety of CVEs including the vulnerabilities noted previously CVE-2019-11510, CVE-2019-19781, and CVE-2020-5902 as well as CVE-2019-11539 affecting Pulse Secure.
- CISA Analysis Report AR20-268A (September 24, 2020) – Analysis of a cyberattack on a U.S. federal agency in which the threat actor leveraged a vulnerability in Pulse Secure VPN servers (CVE-2019-11510).
Using Eclypsium to Protect Your VPN and Network Infrastructure
These alerts make it clear that some of the very devices designed to keep an organization safe have themselves become some of the most popular targets for attackers. However, vulnerabilities in VPN appliances are often not included as part of an organization’s vulnerability management program.
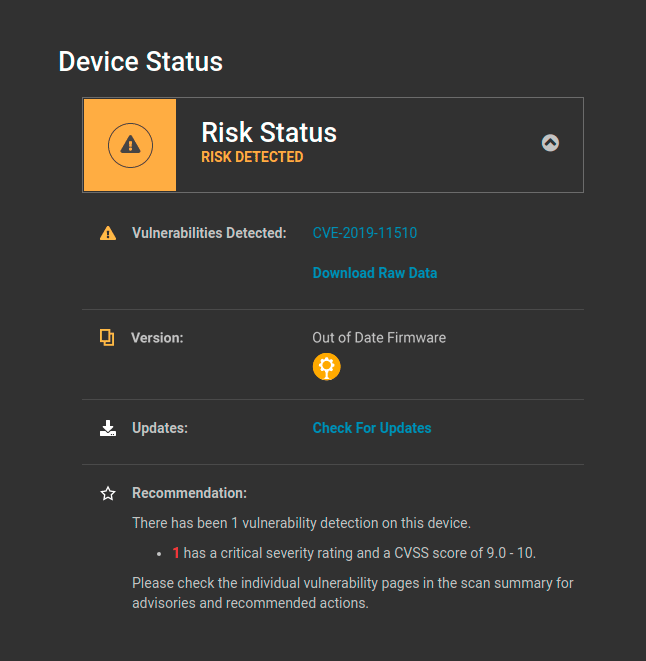
Scanning Pulse Secure VPN
Eclypsium allows security teams to easily and consistently assess their network infrastructure for vulnerabilities and compromises. This includes devices such as switches, routers, firewalls, and VPN appliances. The solution provides an automated view of the Risk status of each device, which allows staff to see devices with outdated firmware, as well as any related vulnerabilities and severity details. If a vulnerability is detected, staff can use Eclypsium to remotely apply firmware patches or updates in order to address the risk. Likewise, Eclypsium can reveal signs of compromise and exploitation of network devices and capture in the Integrity status. Any risk or compromise detection event can trigger alerts via Syslog while the REST API and easy integration with SOAR playbooks enable a variety of proactive responses.





