Internal conflicts within the notorious Black Basta ransomware group have led to a massive leak of the group’s internal chat messages. While the messages are disorganized and full of internal jargon, they contain a wealth of insight into the group’s operations and techniques. This type of disclosure can be a goldmine for security professionals because it can show precisely how attackers think and the specific details of how they execute their attacks.
As a result, we were more than eager to dive into the 200,000 or so messages to see what we could learn. And from the beginning, it was clear that Black Basta has a very strong interest in how they can compromise and co-opt an organization’s networking and security infrastructure. This should be no surprise, as such techniques have been a hallmark of many of the top ransomware groups for years. However, the chats revealed a wealth of new details including references to both known and unknown vulnerabilities affecting the top networking and security vendors in the industry including Palo Alto Networks, Cisco, Fortinet, Citrix, and F5.
Check out our Below The Surface Podcast episode discussing the Black Basta chat leaks and what they mean for security teams.
Key Findings
Our analysis began with the basics of looking for references to known CVEs, URLs, as well as vendor names and their associated device models. It was immediately clear that Black Basta is highly opportunistic in their attacks, and don’t limit themselves to just a handful of CVEs or devices or tactics. Overall, the messages referenced 62 specific CVEs.
However, deeper digging revealed that the CVEs were just the tip of the iceberg, as the Black Basta operators routinely referenced vulnerabilities in terms of specific devices instead of using CVEs. For example, while the data did not include CVEs specific to printers, the internal chats revealed that the group is testing exploits against printers from HP, Brother, and others.
As a result, it was important to go beyond just extracting CVEs, and instead dig into the actual conversations to understand what these bad actors were up to. This revealed references to many of the industry’s leading network and security infrastructure vendors. This included references to multiple techniques the team would use to try and compromise devices including:
- Exploitation of known vulnerabilities
- Acquiring access to 0-day vulnerabilities
- Credential-stuffing user and root credentials of victims from prior attacks
Suspected 0-Day Vulnerabilities
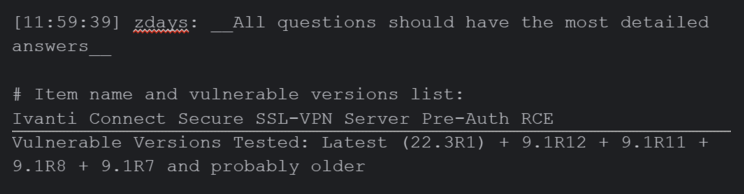
Naturally, references to 0-days are of particular interest. The messages included references to acquiring 0-day vulnerabilities for Juniper, Windows, Ivanti Pulse Secure, Sonic Panel, Wildix, and Unified Remote. For Juniper, they included the test runs on a publicly-facing device, which further complicates analysis of their messages.
Credential Stuffing
The group also exchanged shared credentials for target devices and infrastructure that had been exposed in prior breaches. This included user credentials such as credentials for VPN access as well as root credentials of devices. Attackers could then use these credentials in credential-stuffing attacks to try and gain access to a target.
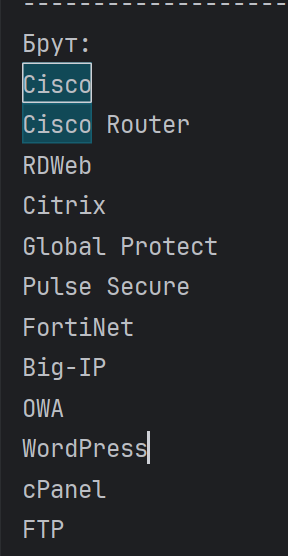
Additionally, the group also shared passwords for multiple publicly accessible RDP devices on port 3389. The actors also referenced attacking databases and other services with brute force as well.
Network and Security Infrastructure
All of these techniques were used when it came to attacking an organization’s network and security infrastructure. Like many ransomware gangs, Black Basta demonstrated a particular interest in VPN infrastructure including Palo Alto Networks, Cisco, Pulse Secure, and others. These devices have proven to be useful to attackers both as an initial infection vector and as a method to persist and spread in an environment.
Conversations showed that the group were also opportunistic when it came to targeting network devices. In addition to targeting large enterprise devices such as firewalls and load balancers, the group discussed digging deeper into the network and using ARP spoofing and intercepting traffic between targets on a compromised router.
Some of the notable vendors mentioned in the conversations include:
- Palo Alto Networks Global Protect – Credentials, Exploit, Malware
- Cisco SSL VPN – Credentials
- Fortinet devices – Credentials
- Pulse Secure VPN – 0-Day Vulnerability
- Watch Guard
- Android IPFire
- Juniper – 0-day Vulnerability
- TrendMicro
- F5 Big IP
- Citrix (NetScaler & maybe others) – Credentials
Other Tools and Techniques
Black Basta extensively uses tools like Shodan and ZoomEye to hunt their targets. The chats include over 100 unique shodan dorks (queries) used by the group to find specific resources that could be vulnerable to exploitation.
Additionally, the team seems to like Cobalt Strike (and seemingly has multiple active proxies for it). There are messages mentioning links to abuse.ch, and them looking at RATs and other malware. For example – they are mentioning analyzing this malware for Palo Alto and looking for exploit code.
Take-Aways on Vulnerability Use
While Black Basta does gravitate towards targets with publicly-known vulnerabilities, there are a few important points to keep in mind:
- They do purchase (or at least discuss purchasing) 0-days for various devices and systems when they see something interesting. We have seen at least 6 different targets this happened for, including SSL VPN appliances.
- Very often, they discuss vulnerabilities without actually mentioning a specific CVE, so the scope of their exploitation goes far beyond the 62 mentioned CVEs we see in the chat logs.
- The group is extremely opportunistic and ready to fully scan a network to hunt down persistence and data in it.
- Additionally, they are ready to launch more advanced attacks compared to just using a CVE. This includes techniques such as ARP poisoning, traffic interception, Active Directory attacks, credential stuffing, and so on.
- They do develop their own exploits for CVEs and, in fact, train members on the use of complex exploits.
It is thus impossible to pin group activity only to a specific set of CVEs where they just stop. We must assume that Black Basta uses techniques above and beyond the specific CVEs they mention.
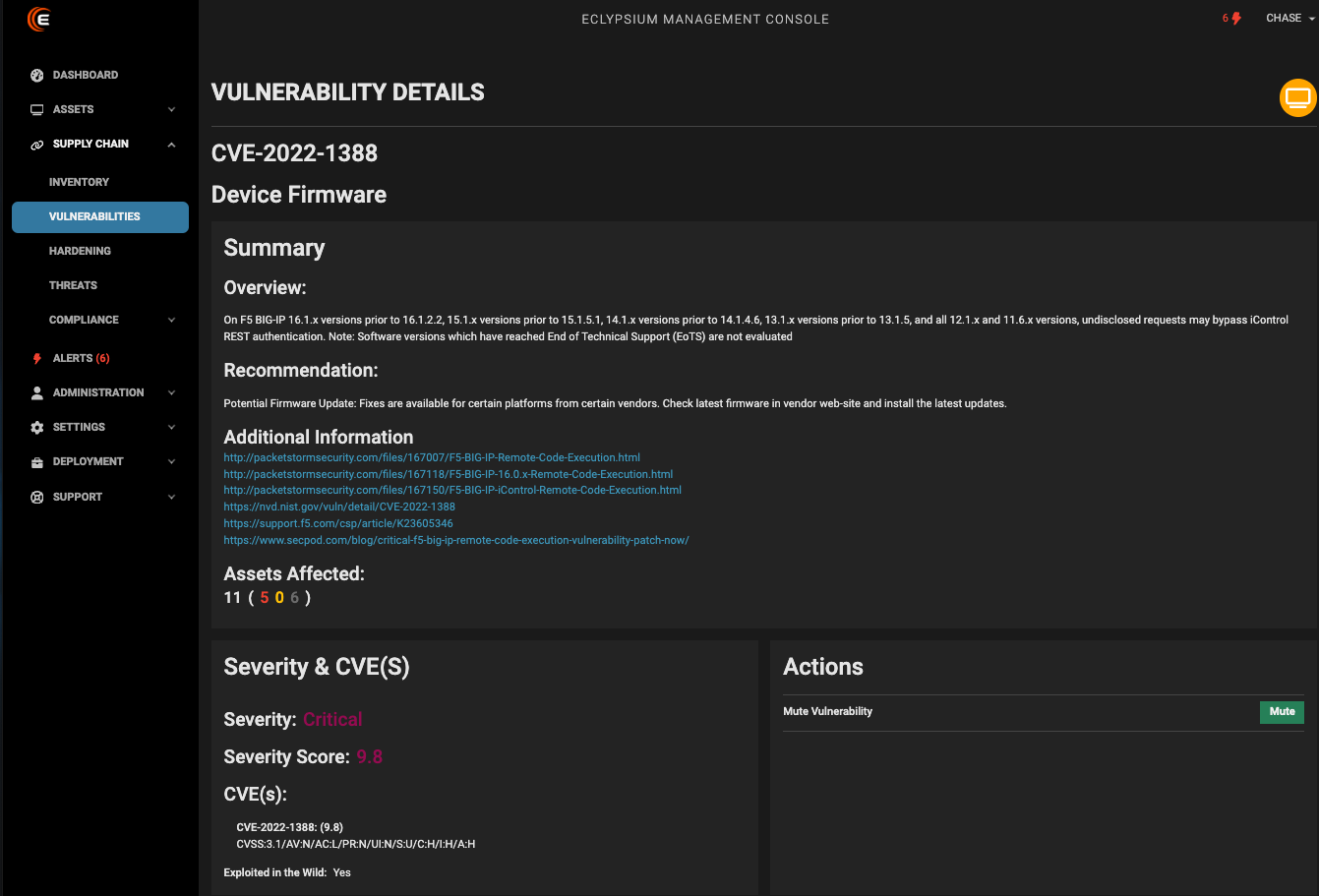
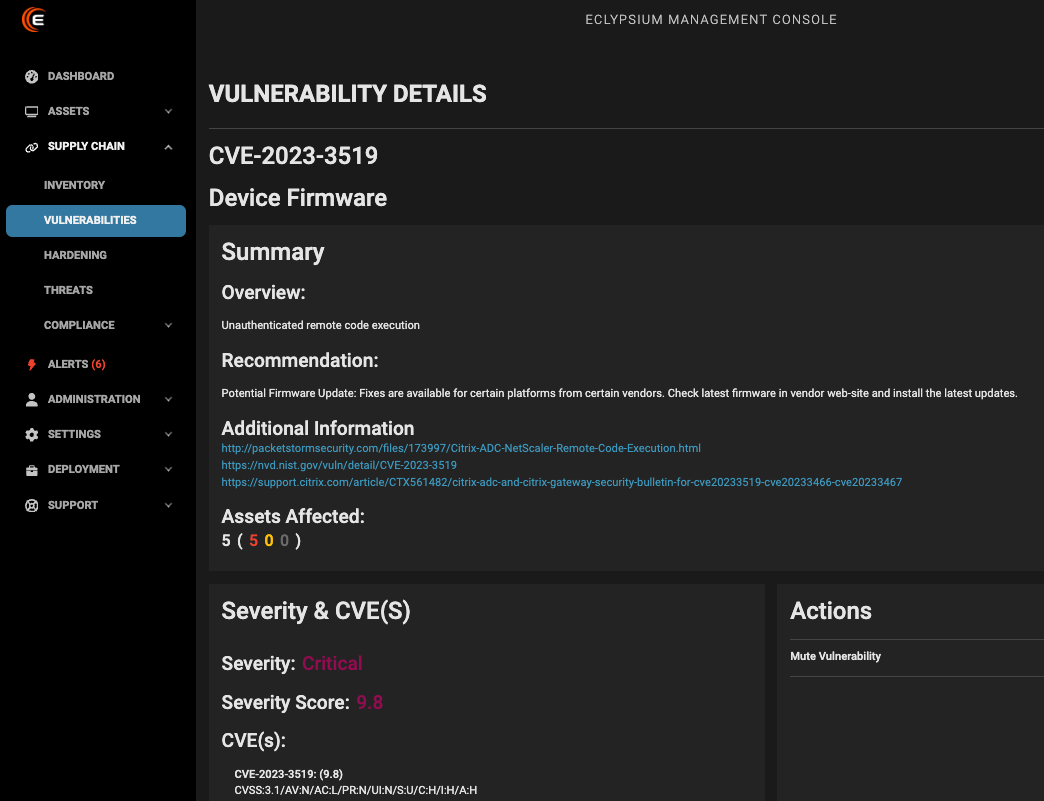
Nonetheless, Eclypsium is able to detect numerous of the highest risk, most critical CVEs referenced in the Black Basta chat leaks, including CVE-2022-1388, CVE-2023-3466, CVE-2023-3519, CVE-2023-36845, and many others. A sampling of these detections in Eclypsium’s platform is shown here.

Conclusion
This is one of those very rare occasions where a data leak is actually a good thing for security practitioners. Cybersecurity intelligence can often feel like trying to piece together a very large puzzle with only a few of the pieces. Many attacks fly under the radar, technical details are often never shared, and the exploits and techniques can vary from target to target. A leak such as this one lets us see all the various puzzle pieces in one place so that we can see the big picture of a highly successful ransomware operator’s playbook.
However, it is up to us as defenders to take advantage of these insights. We can see from these chats that ransomware gangs continue to heavily target networking and security infrastructure using known and unknown exploits as well as credential-based attacks. This means that yes, organizations need to remain fastidious when it comes to patching these critical assets. But likewise, it is a stark reminder that even patched devices may be compromised via 0-day vulnerabilities or exposed credentials. This means that security teams need to be able to verify the integrity of these devices and actively monitor them for any unexpected changes that could indicate a compromise of the device.






