Verizon DBIR 2025 Key Stats: Network Device Attacks, Third Party Risk, and More
Massive shifts in cyber attack behavior have been revealed in the 2025 Verizon Data Breach Investigation Report (DBIR). Here are a few of the most surprising stats with real world implications for cybersecurity strategy and attack surface management.
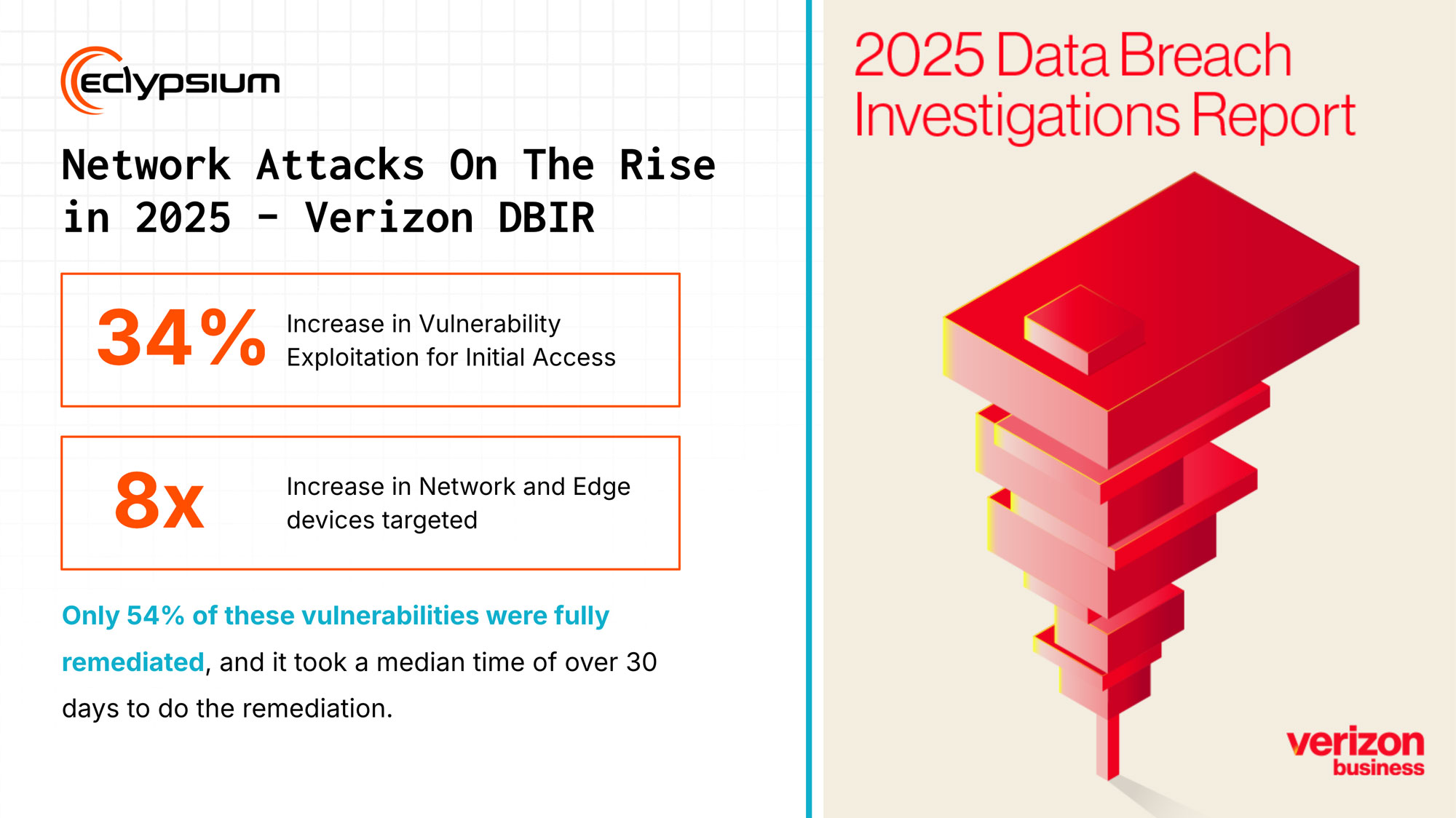
Network Device and Edge Device Exploitation Up ~8x
The exploitation of vulnerabilities in network edge devices, particularly VPNs, increased by almost 8x since last year’s DBIR report. Exploitation targeting these devices went from being involved in just 3% of breaches last year to 22% this year. Additionally, only 54% of the vulnerabilities were fully remediated, and it took a median 32 days for that remediation to take place. This represents a massive shift in attacker behavior towards an attack surface many organizations have difficulty managing. Edge devices such as VPNs, firewalls, and network routers often lack the security controls and visibility that user endpoints have, making them an appealing target for adversaries. This is consistent with earlier findings that half of CISA’s top Routinely Exploited Vulnerabilities impacted network devices and infrastructure.
The lack of security visibility and instrumentation for these network edge devices creates challenges for security teams trying to defend against such attacks. In 2025 Mandiant investigated attacks targeting Juniper routers and noted that: “Investigating further actions taken by the threat actor was hampered by the challenges inherent in analyzing proprietary network devices, which required novel methods for artifact acquisition and analysis.”
Mandiant also concluded that:
“The compromise of routing devices is a recent trend in the tactics of espionage-motivated adversaries as it grants the capability for a long-term, high-level access to the crucial routing infrastructure, with a potential for more disruptive actions in the future. A concerted effort is required to safeguard these critical systems and ensure the continued stability and security of the internet.”
Security teams should double down on efforts to secure network edge devices, particularly VPNs, firewalls, and routers, in the face of the growing trend of attacks targeting these vulnerable, hard-to-protect devices.
Vulnerability Exploitation is Catching Up with Credential Abuse
Another stunning finding from the 2025 DBIR is that vulnerability exploitation as a mechanism for initial access has nearly caught up with credential abuse. For years, credential abuse has reigned. Threat actors could purchase stolen credentials on the dark web for bargain basement prices and use them to gain entry into their victims’ networks.
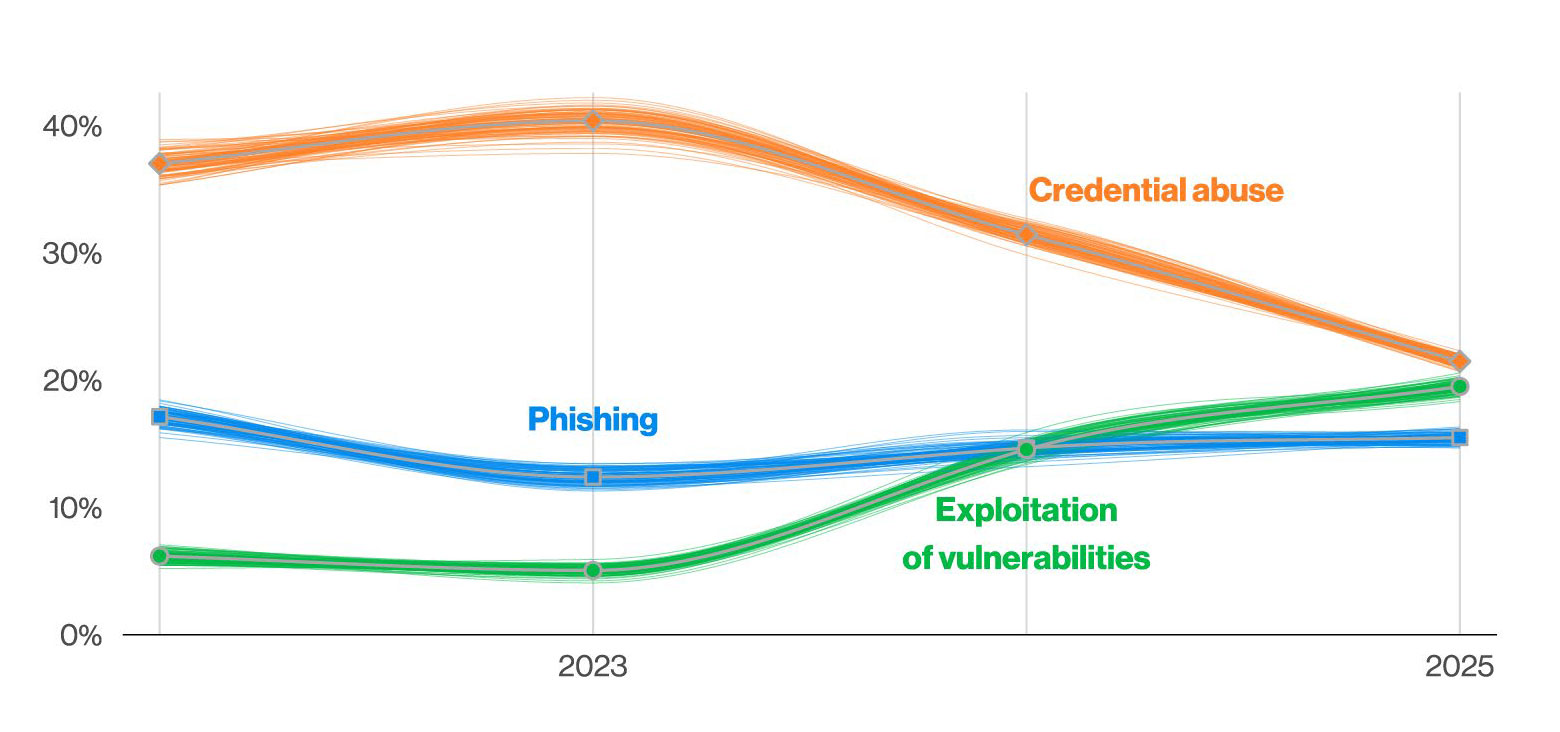
Known initial access vectors over time in non-Error, non-Misuse breaches (n in 2025 dataset=9,891)
Now, vulnerability exploitation, including both known vulnerabilities and zero days, has nearly caught up. Not only that, but credential abuse has fallen significantly. These changes indicate a massive shift in attacker behavior.
Further evidence of this shift came with the Black Basta ransomware gang’s chat log leaks in early 2025. The chats indicated heavy discussion within the organization of vulnerabilities, particularly in network gear, including everything from years-old CVEs to Zero Days. The group’s focus on vulnerabilities indicates that not only nation state actors, but financially motivated cyber criminal gangs see the potential in the growing number of vulnerabilities in network and edge devices.
Third Party Involvement in Breaches Doubled from 15% to 30%
The doubling of third party involvement in breaches highlights the significant interdependence between enterprises and their vendors. In addition to their own research, the DBIR cites a publication from Resilience cyber insurance stating that the third biggest driver of claims in 2025 was a Palo Alto Networks VPN vulnerability. Resilience also claimed that 40% of claims in the first half of 2024 were driven by vendor related events, including ransomware attacks and software vulnerabilities.
Defenders need to take security into their own hands. Trusting a vendor, even a firewall or VPN vendor, to protect your environment from intrusion is not working. Any network device, even a security device, that is exposed to the internet, needs layers of security monitoring and controls applied to it to ensure that it does not provide the attacker with the intrusion point they need to kick off a massive attack. The practice of Cyber-Supply Chain Risk Management (C-SCRM) will only grow in importance as these devices face increasing attacks.
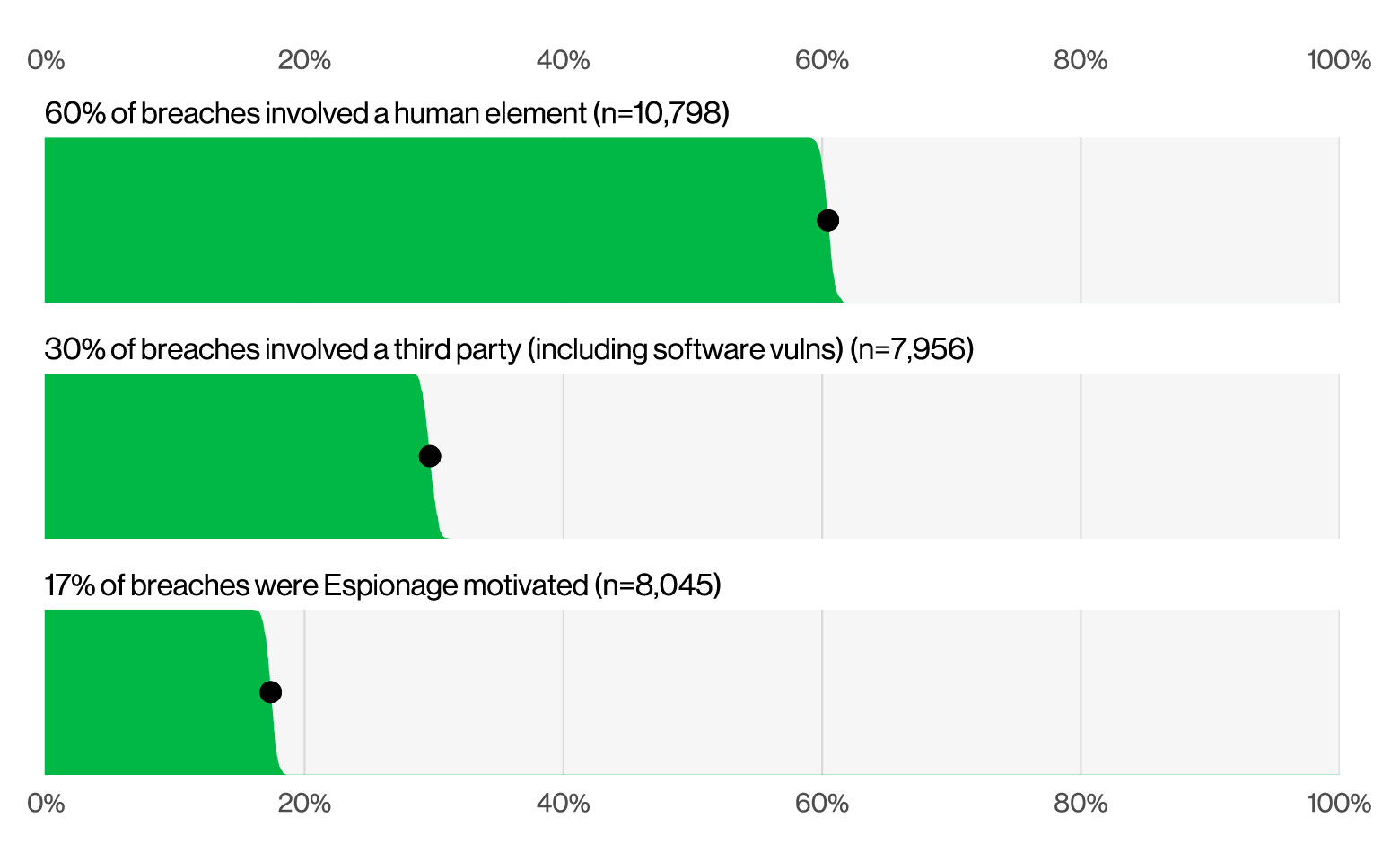
Select key enumerations in breaches
What’s a Defender To Do?
The stats in the 2025 DBIR paint a clear picture of changing attacker behavior and increasing urgency of security controls for network devices. VPNs and other network edge devices are in the crosshairs, vulnerability exploitation is on-track to overtake credential abuse as an initial intrusion vector, and third parties, including vendors of vulnerable software, are driving a growing share of data breaches. The importance of monitoring and securing your network devices, not only to protect them from attack, but to hold vendors accountable for the security of the products they sell, is imperative.
To protect network devices against growing attacks, you have to know what you have deployed in your environment, what vulnerabilities may be present, and whether patches are available. Eclypsium delivers continuous monitoring of every asset in your environment across the entire device lifecycle.
Learn more about protecting your environment from third party risk through Secure Device Lifecycle Management.
To learn more about securing network edge devices from increasing attacks, view our recent presentation on Protecting Your Exposed Network Edge from Ransomware, APTs, and Zero Days.
Interested in Eclypsium? Take a Tour of our Supply Chain Security Platform.





