New DoD Cyber Supply Chain Security Guidance from GAO and Secretary of Defense
The first half of 2025 has seen a flood of new cybersecurity guidance for the U.S. Federal government, and particularly the Department of Defense. The Cybersecurity Maturity Model Certification (CMMC) 2.0 final rule was published on December 16, 2024, starting the clock on a 60 day countdown toward implementation requirements. July saw the publication of the White House’s AI Action Plan, with heavy emphasis on cybersecurity requirements.
Most recently, July also brought a new directive from the Secretary of Defense and a report from the Government Accountability Office (GAO), both pressing the Department of Defense (DoD) and Defense Industrial Base (DIB) vendors to deeply scrutinize the provenance and security of critical technologies. The directives aim to to prevent vulnerabilities, backdoors, and other cyber risk from weakening the U.S. against adversaries.
Here’s a quick rundown of what the new guidance says about supply chain security, who it affects, and how Eclypsium can support DoD and DIB customers in achieving the new goals and requirements.
What the Defense Secretary’s DoD Supply Chain Directive Says
Defense secretary Hegseth’s memo to Pentagon leadership is less than a page long, but its implications are enormous. Key clauses include:
“The DoD will not procure any hardware or software susceptible to adversarial foreign influence that presents risk to mission accomplishment, and must prevent such adversaries from introducing malicious capabilities into the products and services that are utilized by the Department.”
Hegseth specifies several existing frameworks to be leveraged in achieving this challenging goal, including:
- Cybersecurity Maturity Model Certification (CMMC)
- Software Fast Track (SFT)
- Authority to Operate (ATO) process
- Federal Risk and Authorization Management Program
- Secure Software Development Framework (SSDF)
The memo also directs the DoD Chief Information Officer (and specifically Department CISO, David McKeown) to “issue additional implementing guidance within fifteen days”.
What the GAO Supply Chain Security Report Says
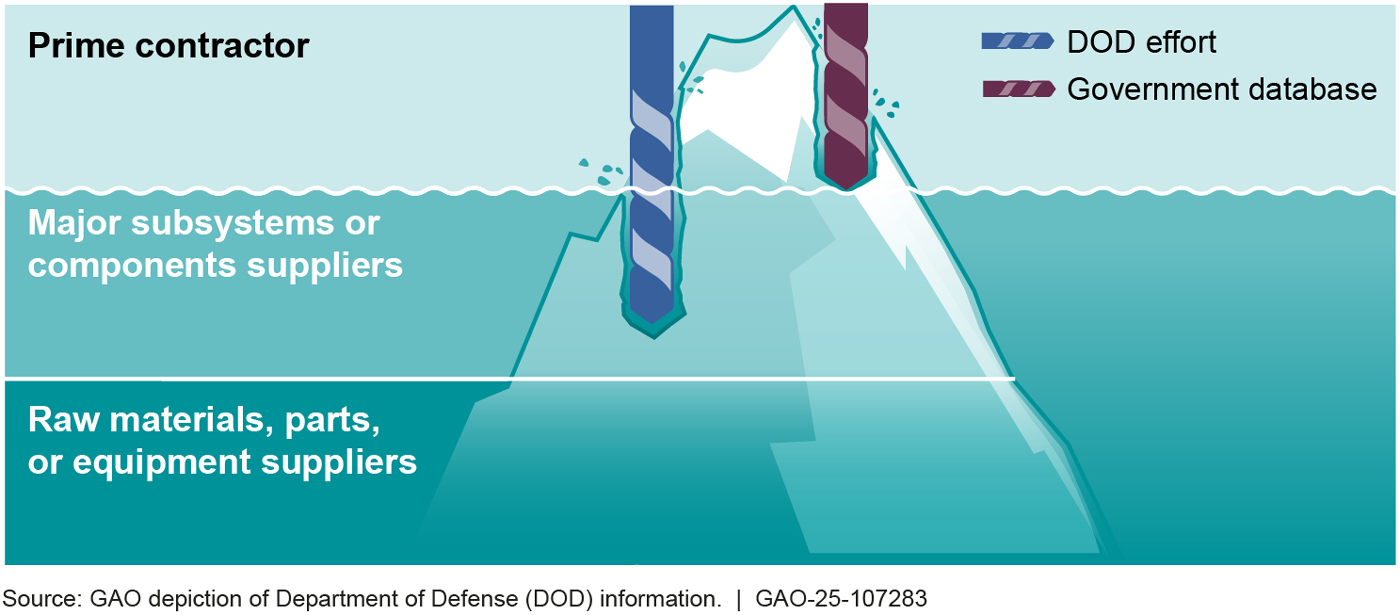
The GAO report highlighted the scale, complexity, and global nature of the supply chain used by the DoD to “produce weapons, as well as noncombat goods like batteries and manufacturing equipment. GAO highlighted that there are over 200,000 suppliers in the global supply chain for the DoD and Defense Industrial Base.
The GAO report focused more broadly than the Secretary of Defense’s memo, highlighting non-cyber risks, such as the potential of an adversarial supplier cutting off access to certain materials or products. The GAO and SecDef memos overlapped heavily in their focus on visibility and transparency. Both expressed serious concern about the lack of visibility into the sources of critical materials and components. This lack of knowledge creates significant risk of malicious components
How Eclypsium Directly Supports SecDef Guidance and GAO-Identified Supply Chain Security Gaps
Eclypsium’s core mission is to protect against threats below the operating system, precisely where nation-state adversaries like China and Russia focus their efforts when attacking supply chains. This directly addresses concerns about being “protected from the influence of top adversaries” and “secure against supply chain attacks.”
Ensuring Secure IT Capabilities with Unique Visibility and Protection
Eclypsium’s platform offers the deep visibility and validation needed to “ensure all information technology capabilities are reviewed and validated as secure against supply chain attacks.” This is achieved by the following:
- Generating Hardware/Firmware Level SBOMs: Providing transparency into device components.
- Verifying Integrity: Detecting unauthorized changes, tampering, and implants in firmware and hardware.
- Vulnerability Management: Identifying and prioritizing firmware and hardware vulnerabilities that are not visible to other security monitoring and management tools.
- Continuous Monitoring: Alerting to changes that might indicate compromise.
Supporting Defense Industrial Base (DIB) Fortification
Eclypsium directly supports fortifying existing programs within the DIB by supporting numerous standards and models, including:
- Cybersecurity Maturity Model Certification (CMMC): Helping meet CMMC requirements for device integrity and firmware security.
- NIST Standards: Eclypsium aligns with NIST SP 800-53, 800-161 (Supply Chain Risk Management), and 800-193 (Platform Firmware Resiliency).
- FedRAMP: Contributing to the assurance of foundational hardware and firmware layers for cloud infrastructure.
Eclypsium already supports DoD and DIB customers in gaining visibility and security for their technology supply chains by scanning and validating firmware and hardware components of mission critical network equipment, flyaway kits entering and leaving sensitive locations, satellite communications hardware, and more.
To learn more, check out www.eclypsium.com/public-sector






