Eclypsium Acknowledged for the Firmware Protection as A Service Category in two Gartner® Hype Cycle™ Reports
Firmware protection is gaining increased urgency as cyberattackers from ransomware gangs to nation state APTs target firmware vulnerabilities to maintain persistence in target environments. Eclypsium has been mentioned as a sample vendor in two Gartner Hype Cycles in 2025 under the Firmware Protection as a Service product category.
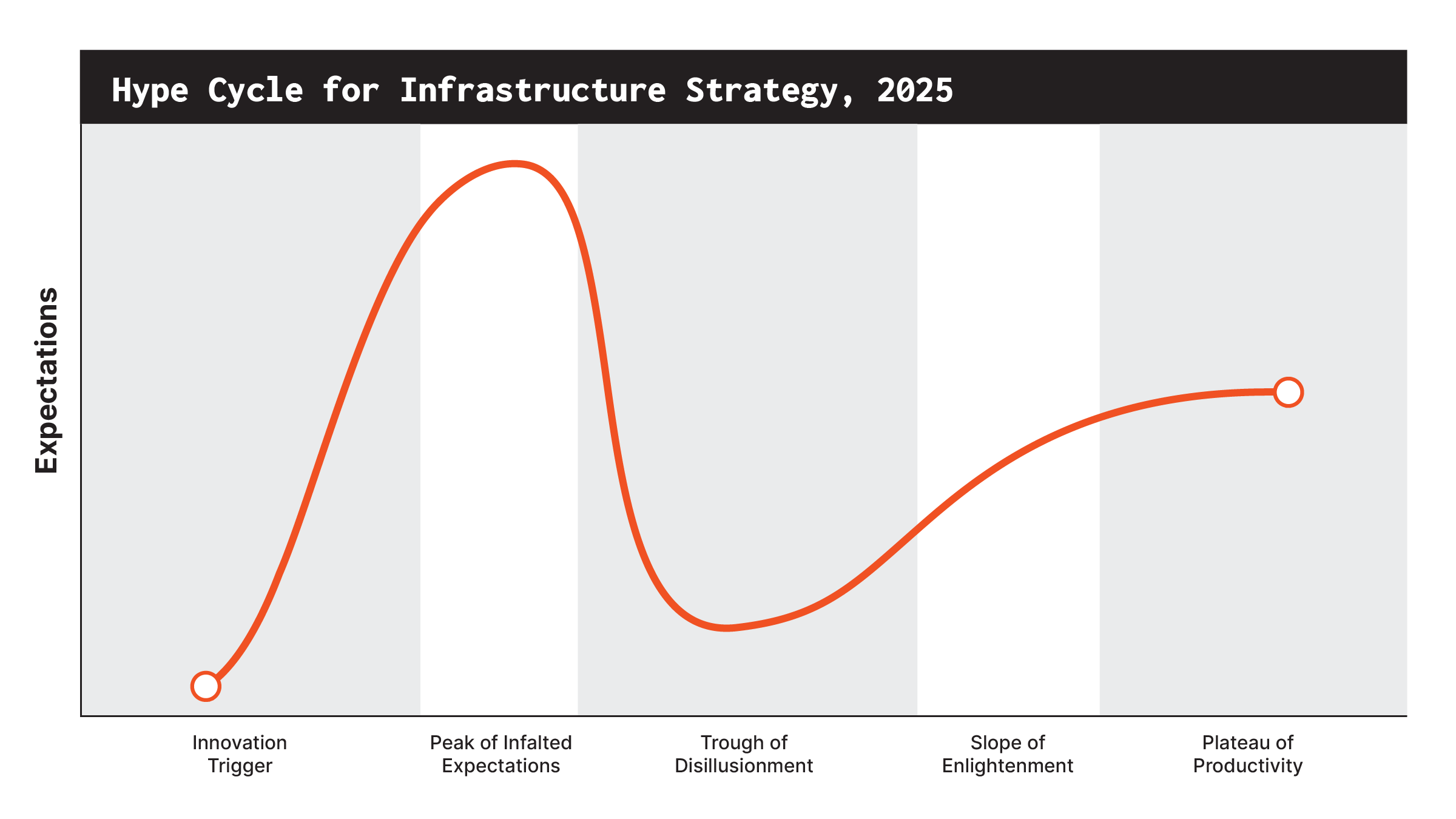
Why Firmware Protection Is Important to Infrastructure Strategy
In the Hype Cycle for Infrastructure Strategy, 2025, Gartner gave Firmware Protection as a Service a Benefit Rating of “High.” In the explanation for why FPaaS is important they noted that:
“As the threat landscape for infrastructure rapidly continues to change, infrastructure and operations (I&O) organizations need to adapt their strategies to prevent ransomware and malware attacks. FPaaS adds an extra security layer to prevent or mitigate damage to critical underlying hardware systems. FPaaS is quickly becoming an integral component of secure supply chain solutions.”
Eclypsium was also a Sample Vendor in the Hype Cycle For XaaS, 2025, in the Firmware Protection as a service category.
How Eclypsium Protects Firmware
While firmware protection is only a small component of what Eclypsium does, it is an important one. The firmware, BIOS, UEFI, and SecureBoot elements of enterprise computing devices are increasingly targeted by attackers. Just this year, we saw the release of HybridPetya, a ransomware malware tailored to bypass modern UEFI Secure Boot systems. 2025 also saw the introduction of a Baseboard Management Controller (BMC) firmware vulnerability to CISA’s catalog of Known Exploited Vulnerabilities (KEV). The number of firmware vulnerabilities on CISA’s KEV catalog has increased steadily over the past decade.
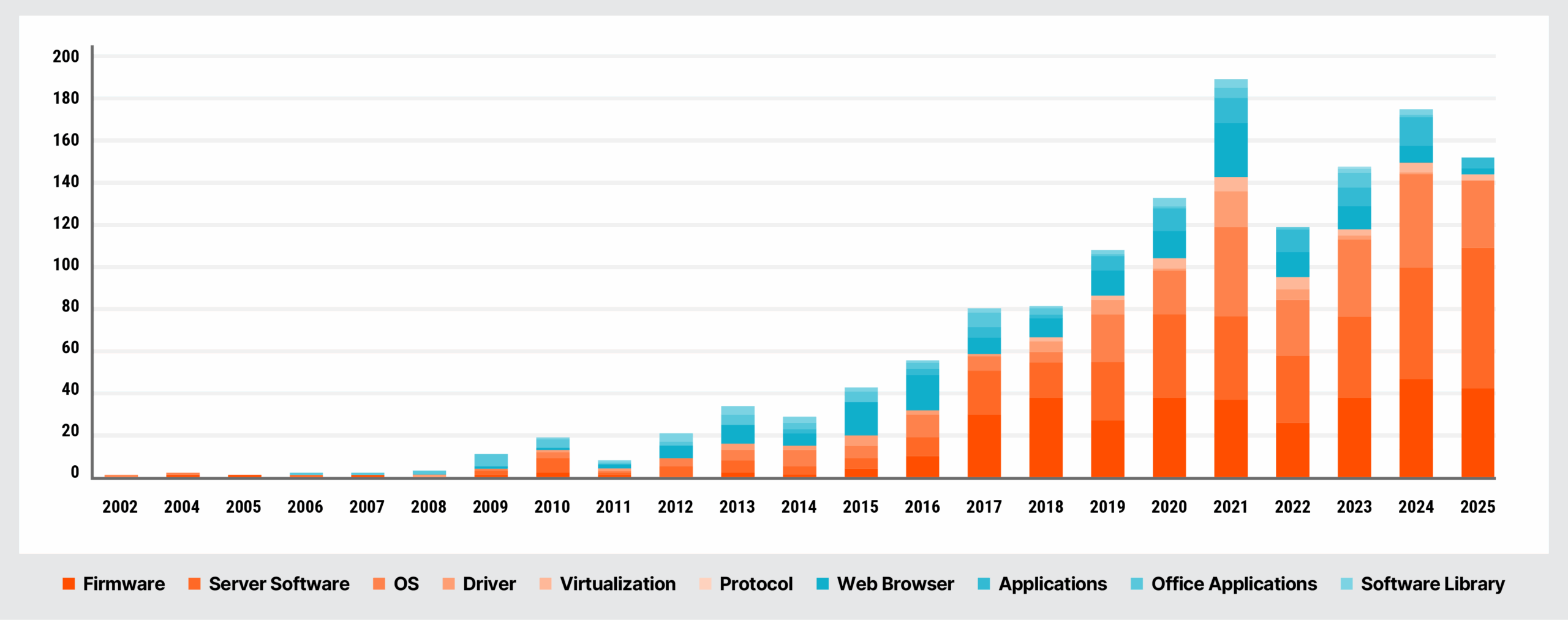
This means attackers in the wild are targeting firmware in systems hidden below the OS, evading EDR, vulnerability management, and other traditional security tooling.
In the past, UEFI malware was the realm of advanced, nation state attackers. Now, these tactics are becoming more accessible to mainstream ransomware groups and less sophisticated attackers.
Monitoring and protecting firmware requires adding new levels of visibility and analysis to the enterprise security lineup. It starts with the same foundation of all effective security operations: asset inventory, then progresses to vulnerability detection, threat detection, and remediation either by patching or implementing compensating controls. Eclypsium supports all of these requirements.
Inventory: Eclypsium delivers a complete inventory of the hardware components and firmware that make up enterprise IT infrastructure. To deliver this, Eclypsium scans all devices in the environment, from user endpoints like laptops to servers, network routers and switches, firewalls, application delivery controllers, IP cameras, and other IOT devices.
Known Vulnerability Detection: Eclypsium compares firmware running in the scanned environment against our industry-leading database of 12 million known-good firmware hashes to identify known vulnerabilities in the environment.
Unknown Vulnerability Detection: Eclypsium extracts, disassembles, decompiles, and emulates firmware to detect risky behaviors, unauthorized modifications, and unknown vulnerabilities. Eclypsium Automata uses AI driven analysis, among other methodologies, to deliver deep visibility into the inner workings of firmware and hardware components, to uncover hidden risk.
Threat Detection: Eclypsium deeply analyzes firmware behavior to discover indicators of compromise and evidence of active attack behavior in progress. Attackers use firmware and hardware level exploits to evade detection and maintain persistence, ultimately leading to greater harm and more difficult incident response. Eclypsium helps detect and eradicate these stealthy, persistent threats.
Remediation and Compensating Controls: Eclypsium provides automated firmware updates for many devices to ensure that vulnerable versions are patched as soon as possible. Beyond that, Eclypsium integrates with other security operations tools such as SIEM and SOAR, providing early notification and the ability to trigger automated workflows to isolate affected devices or implement other compensating controls.
Learn More about Firmware Protection for Infrastructure
Firmware and hardware supply chain attacks are the next frontier for cyberattackers who have been thwarted by effective OS-level security tools. Forward thinking enterprises and government agencies are already moving toward incorporating firmware and hardware supply chain security into their tooling.
Furthermore, recent laws and government memos are strongly indicating that supply chain security requirements such as Firmware Bills of Materials will be a requirement for vendors bringing digital products to market, or participating in defense industrial base projects to build critical defense technology.
To learn about cyberattacks and vulnerabilities specifically exploiting firmware, check out our white paper on the Top 5 Firmware and Hardware Attack Vectors
Gartner subscribers can visit the Gartner website to view the Hype Cycle for Infrastructure Strategy, 2025 and the Hype Cycle for XaaS, 2025 to learn more about these categories.
Gartner, Hype Cycle for XaaS, 2025, Jason Donham, 28 July 2025
Gartner, Hype Cycle for Infrastructure Strategy, 2025 Allessandro Galimberti, Jason Donham, et al., 17 June 2025
GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally, and HYPE CYCLE is a registered trademark of Gartner, Inc. and/or its affiliates and are used herein with permission. All rights reserved.
Gartner does not endorse any vendor, product, or service depicted in its research publications, and does not advice technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner’s research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.





