Enterprise devices include a variety of components that are critical to the security posture of the device. Components used for out-of-band management and Trusted Platform Modules (TPM) used to protect cryptographic keys on the device are just a few examples.
Vulnerabilities in these components can pose considerable risk to a device. For example, an attacker could use out-of-band management capabilities to gain powerful control over a device and leverage its independent communication channels to evade controls in the operating system. Likewise, by compromising the cryptographic keys of a device, an attacker could forge virtually any identity based control from the device. These issues become even more concerning when those vulnerabilities can be exploited over a network.
Two recent Intel security advisories, INTEL-SA-00241 and INTEL-SA-00404, provide a few examples that we can use to understand the risk of these vulnerabilities as well as how to detect and mitigate them in a real-world environment.
Vulnerabilities in Intel AMT
Intel Active Management Technology (AMT) is a built-in component found in modern Intel-based laptops and desktops that provides remote, out-of-band management of the device. Intel AMT runs on the Intel Management Engine (CSME or ME) and has its own network capability and TCP/IP stack that is completely independent from the operating system. Attackers have used this independent communication channel as a way to hide stealthy command-and-control traffic. Given that AMT is designed to provide administration over a system, any compromise gives an attacker tremendous control over a victim device.
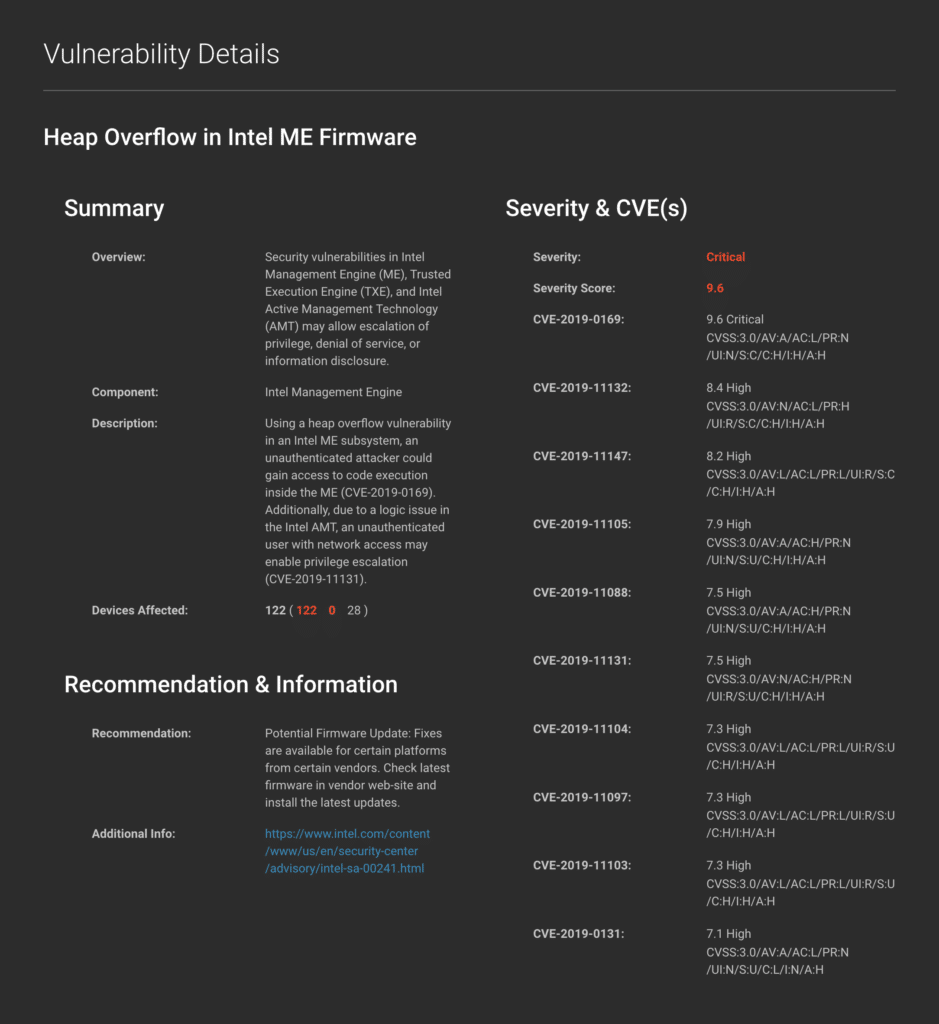
INTEL-SA-00241 and INTEL-SA-00404 include 5 unique AMT CVEs that could allow an attacker with network access to target AMT.
| CVE | CVSS (v3) Score & Severity | Description |
| CVE-2020-8758 | 9.8 Critical | Improper buffer restrictions that could allow an unauthenticated user to escalate privileges via network access. |
| CVE-2019-11131 | 9.8 Critical | Logic issue that could allow an unauthenticated user to escalate privileges via network access. |
| CVE-2019-11107 | 9.8 Critical | Insufficient input validation that could allow an unauthenticated user to escalate privileges via network access. |
| CVE-2019-11132 | 8.4 High | Cross site scripting issue that could allow a privileged user to escalate privileges via network access. |
| CVE-2019-0166 | 7.5 High | Insufficient input validation that could allow information disclosure by an unauthenticated user via network access. |
These are very significant vulnerabilities for two reasons. First, they can have a significant impact on an organization by leaking data or giving an attacker powerful privileges over a device without having to physically access the hardware. Secondly, many organizations lack visibility into these types of vulnerabilities and thus may be blind to an important part of their attack surface.
Vulnerability in Intel PTT or fTPM
The INTEL-SA-00241 advisory also included another significant vulnerability that could be accessed over a network. CVE-2019-11090 affected the Intel Platform Trust Technology (PTT) stemming from an issue with the firmware-based Trusted Platform Module (fTPM). Organizations should be aware of this vulnerability in spite of its relatively low CVSS score (5.8 Medium). Also known as TPM-Fail, the vulnerability is significant in that it can allow an attacker to recover 256-bit private keys from the device that are normally protected by the TPM. Such an attack would allow an attacker to forge signatures for any number of purposes.
The network accessibility of this vulnerability is particularly important. TPMs are designed in such a way that cryptographic keys should be impossible to obtain even when an attacker has physical access to the device. However in this case researchers were able to use a timing attack to obtain the keys from the network. This could potentially allow an attacker to remotely steal keys and impersonate high-value users or systems.
Protecting Your Organization
The Eclypsium Device Protection Platform provides the ability to automatically detect these and many other similar vulnerabilities in network devices and other enterprise infrastructure. The solution provides visibility into systems including the device configuration, hardware components, and firmware and can automatically identify devices that are vulnerable. This includes a wide variety of potentially vulnerable components including the system UEFI firmware, processor microcode, CSME and AMT, TPM, and many more. The system can then apply updates to outdated components to address the risk. The platform also verifies the integrity of components and monitors their behavior in order to detect the presence of known or unknown threats.
To learn more about how Eclypsium can help you detect and mitigate vulnerabilities in Intel AMT, or the dozens of other components in enterprise devices, request a demonstration.