New threats in the wild combined with the recently disclosed BootHole vulnerability have made securing UEFI Secure Boot a top priority for security teams. The NSA and FBI recently issued a Cybersecurity Advisory warning of a powerful new Linux-based rootkit known as Drovorub being used by a Russian intelligence service known as APT28. Additionally, new ransomware campaigns have been discovered using malicious bootloaders to take control over victim devices.
In order to mitigate these and similar threats, organizations need to be able to ensure the integrity of UEFI Secure Boot on their various devices. However, the recently discovered BootHole vulnerability puts the Secure Boot process of a wide range of Linux and Windows-based devices at risk. As a result, security teams need to know which of their devices are vulnerable, how to mitigate the vulnerability, and how to detect if systems have been compromised.
The issue stems from a buffer overflow vulnerability in the way that GRUB2 parses content from the GRUB2 config file (grub.cfg). This config file is a simple text file and typically is not signed. Thus an attacker is able to modify the config file and trigger a buffer overflow in GRUB2 that provides arbitrary code execution during the boot process, even when Secure Boot is enabled.
Windows and Linux Devices Affected
It is particularly important for enterprise security teams to recognize that systems are likely affected by BootHole even if they do not use GRUB2. In fact, the problem extends to any device that uses Secure Boot with the industry standard Microsoft Third Party UEFI Certificate Authority found in most Linux and Windows-based laptops, desktops, and servers.
The issue is that since the vulnerable bootloader is signed and allowed on a system, an attacker or malware could replace a system’s existing bootloader with the vulnerable version. On the next system reboot, the system would use the vulnerable version, which could be exploited and give the attacker code execution before the operating system is ever loaded.

Addressing BootHole in the Enterprise
Addressing the BootHole vulnerability requires multiple coordinated elements. In addition to deploying new signed bootloaders, the vulnerable versions also need to be revoked to prevent them from being used in an attack. This means that organizations need to make sure that they are using the latest stable OS and bootloaders, and that the dbx revocation database is up to date. It is important to note that organizations will need to first update their operating system and bootloaders before the dbx database is updated. Please refer to the Mitigations and Recommendations section of the BootHole blog for step by step guidance on updating systems. We have provided publicly available scripts that can be used to check devices for the presence of vulnerable bootloaders and shims.
The Eclypsium platform allows IT and Security teams to easily identify vulnerabilities and threats related to BootHole across an organization’s fleet of Windows and Linux devices. This includes the following key capabilities:
- Visibility into system bootloaders, EFI system partition, UEFI firmware, and revocation database.
- Automatically identify devices with vulnerable bootloaders and missing updates.
- Detection of malicious bootloaders and exploit code on compromised devices.
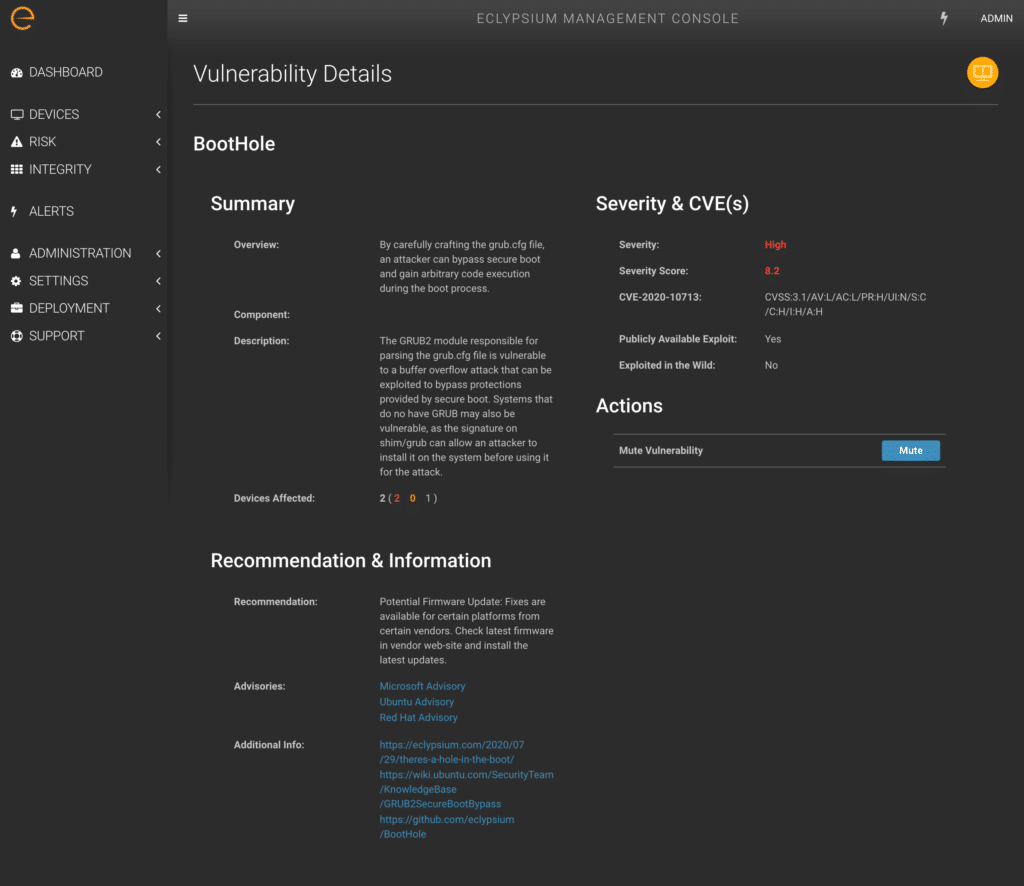
These capabilities allow organizations to quickly audit their environment and proactively address the risks of BootHole with a minimum of effort.
Alternatively, Eclypsium is offering a customized BootHole and Firmware Risk Report to help organizations identify issues related to BootHole and other firmware-related risks. Eclypsium engineers will perform an assessment of the environment and deliver a concise and actionable report of the key findings. This will include:
- A list of devices that are vulnerable to BootHole
- Devices with compromised or malicious firmware
- Devices with firmware vulnerabilities
- Devices with insecure configurations and UEFI Secure Boot settings
To learn more about BootHole, and how Eclypsium can help protect your organization from device-level vulnerabilities and threats, please contact the Eclypsium team at [email protected].
Join Eclypsium researchers Mickey Shkatov and Jesse Michael for a webinar, “Exploring The BootHole Vulnerability” on September 1st.