Introduction
Vulnerabilities in enterprise network and security devices are being aggressively targeted by APT and ransomware threat actors as initial access vectors into enterprises. Fortinet products are a prime example of this trend and highlight how devices that were intended to defend the network are increasingly being exploited to cause damage.
They also highlight the critical role that firmware plays in today’s enterprise attack surface. Security teams need to understand what makes these vulnerabilities unique, how they are being attacked in the wild, and the key steps to mitigate their risk. Let’s take a closer look.
Fortinet Vulnerabilities Attacked in the Wild
To date, attackers have primarily focused on four Fortinet vulnerabilities (CVE-2018-13379, CVE-2018-13374, CVE-2019-5591, and CVE-2020-12812). CVE-2018-13379 was the first vulnerability exploited in the wild and proved to be popular with a wide range of threat actors. Research from FireEye initially found that APT 5, a group believed to be Chinese state-sponsored attackers, were attacking this vulnerability in Fortinet VPN servers. Other state-sponsored attackers quickly followed suit including Russian SVR and Iranian groups.
Some of the most destructive ransomware groups quickly adopted these same techniques and began targeting Fortinet devices in order to gain access to victim networks and spread malware. This includes the notorious Conti and REvil ransomware groups, which were recently ranked as the #2 and #3 most common ransomware families in the wild, respectively. Of note, Maze, the #1 ransomware on the list, has similarly targeted PulseSecure VPNs and Citrix devices.
| CVE | CVSS Score / Severity | Associated Threat Actors | Affected Platforms |
| CVE-2018-13379 | 9.8 Critical | APT Actors, Agrius Ransomware, Conti Ransomware, Cring Ransomware, REvil Ransomware | Fortinet FortiOS 6.0.0 to 6.0.4, 5.6.3 to 5.6.7 and 5.4.6 to 5.4.12 |
| CVE-2018-13374 | 8.8 High | Conti Ransomware | Fortinet FortiOS 6.0.2, 5.6.7, and lower |
| CCVE-2019-5591 | 6.5 Medium | APT Actors | Fortinet FortiOS all versions 6.0.2 and lower |
| CCVE-2020-12812 | 9.8 Critical | APT Actors | SSL VPN in FortiOS 6.4.0, 6.2.0 to 6.2.3, 6.0.9 and lower |
Fortinet Attacks are Firmware Attacks
Security practitioners should keep several factors in mind as they look to protect their Fortinet attack surface and address any potential risks or threats.
- First, it is important to note that FortiOS is actually the embedded firmware of Fortinet devices as seen in the image below. Firmware is often missed by traditional vulnerability scans, which primarily focus on identifying OS- and application-level software vulnerabilities.
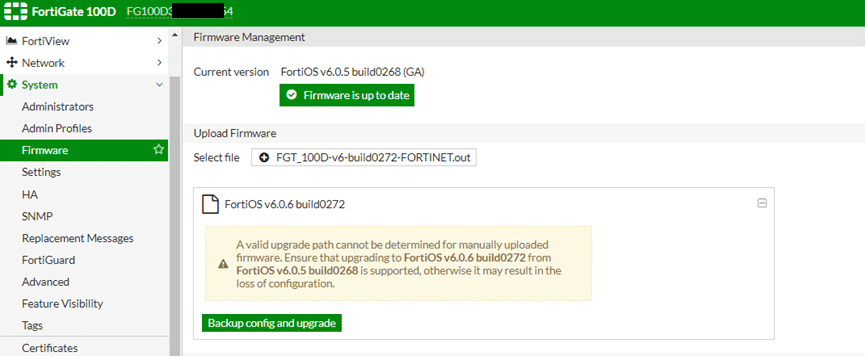
Source: https://kb.fortinet.com/kb/documentLink.do?externalID=FD46352
- Additionally, teams will need to ensure that they have visibility over their many Fortinet devices. Even a single overlooked device could allow attackers to gain access to the network. Next, teams must be able to verify the integrity of the firmware on their devices and ensure that any vulnerable devices are updated to a non-vulnerable version.
Identify, Verify, and Fortify Your Fortinet Devices
Eclypsium gives organizations the visibility and control to easily and consistently protect their Fortinet devices from the firmware layer up. With Eclypsium, security teams can:
- Identify – Eclypsium’s unique distributed discovery allows teams to proactively find all their Fortinet devices to ensure they have a complete picture of their attack surface. The solution provides insight into the firmware version that is currently running on the device and allows teams to search for specific versions.
- Verify – Next, security teams need to check for any vulnerabilities or signs of compromise in their Fortinet devices. Eclypsium automatically finds the specific vulnerabilities that are being attacked in real-world APT and ransomware campaigns. This ensures that staff can focus on the issues that really matter without generating large volumes of low-value vulnerability logs. Next, Eclypsium can verify the integrity of the firmware to ensure that it has not been altered. This includes the ability to compare the firmware to know good versions as well as detecting known and unknown threats.
- Fortify – The most fundamental safeguard is assuring that the patch levels in your Fortinet devices are current, updated and no longer vulnerable. Eclypsium helps security teams determine where patches still need to be applied or where configurations need to be hardened.
These key capabilities arm security teams with the tools to reliably protect their Fortinet devices and all the users and assets that they support. As with any active area of cybersecurity, attackers are constantly evolving and seeking out new vulnerabilities and techniques. Eclypsium specializes in the critical area of firmware security, including and network devices. Our industry-leading research ensures organizations stay up to date even as new risks and threats emerge. To learn more about the Eclypsium solution or to see a demonstration, please contact us at [email protected].






