The rapid rise of hardware- and firmware-related attacks and supply chain threats has been one of the most significant changes in cybersecurity in recent years. Unlike the small incremental changes that typically define the evolution of threats (e.g. new malware variant, new ransomware operator, etc.), this new wave of attacks has introduced profound and fundamental changes to the threat landscape.
Low-level threats have allowed attackers to burrow beneath the OS and its traditional protections at scale, ensuring their malicious code runs first and runs at the most fundamental levels that the OS and all applications depend on. It fundamentally changes the when and where the battle takes place on a given device.
Supply chain threats likewise change the when and where of cyberattacks, but on an even more profound level. Instead of attacking an enterprise directly, supply chain attacks shift the fight to the vendors, suppliers, and software repositories that underpin all enterprise technology. This can include software, firmware, and hardware. Thus, in many if not most cases, firmware attacks can be seen as a subset of supply chain attacks. They end up being very interrelated ideas. Firmware attacks go to the root of how technology works, and supply chain attacks go to the root of where technology comes from.
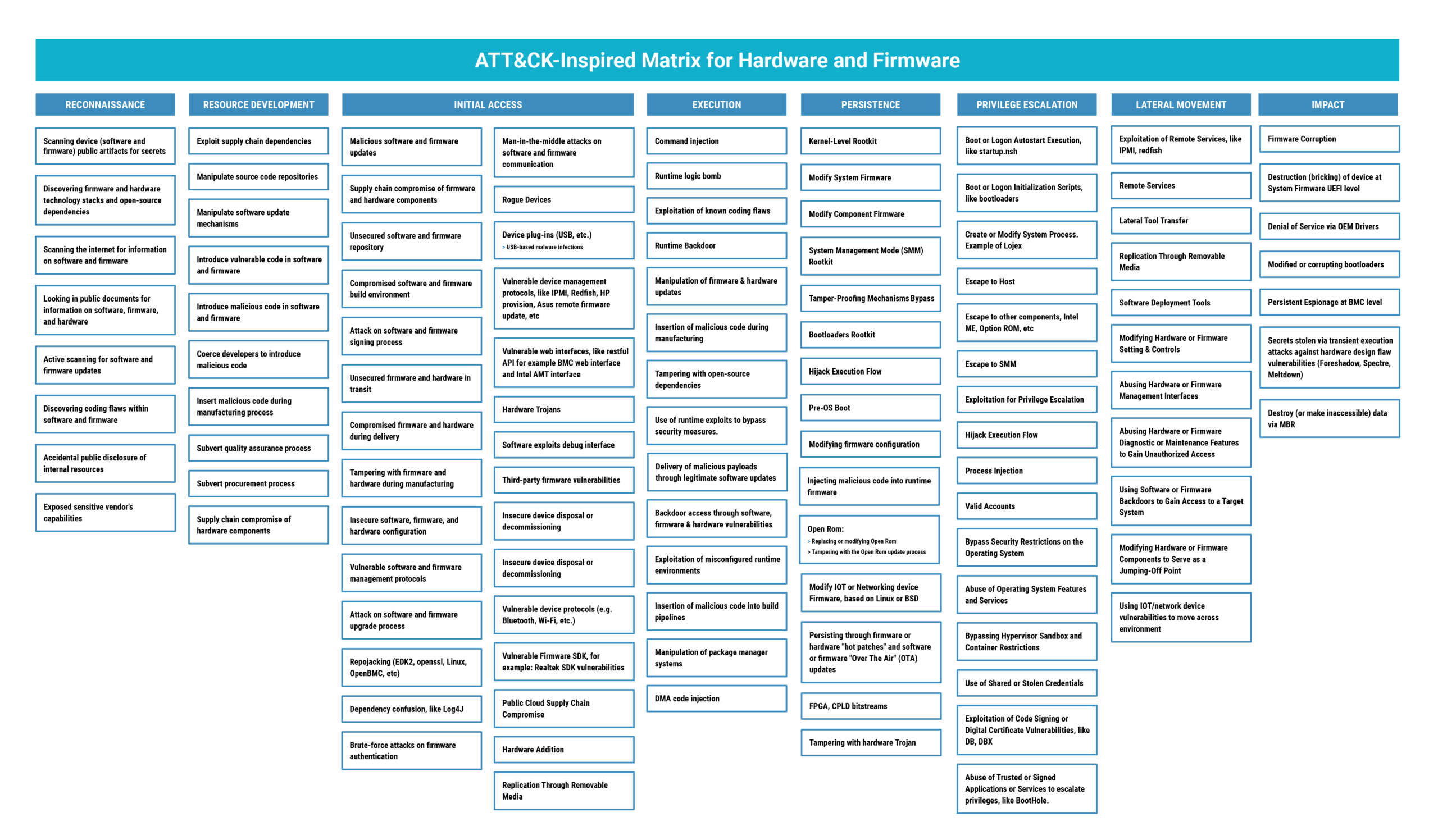
Drawing Inspiration from MITRE ATT&CK
Cybersecurity leaders and professionals have limited time and resources, so it is important that their efforts and decisions are informed by the tactics and techniques that attackers use in the real world. The MITRE ATT&CK framework has proven to be one of the most powerful industry tools in this regard. The framework identifies more than 200 attacker techniques that are categorized under 14 different high-level tactics. The tactics can largely be thought of as phases of an attack beginning with reconnaissance, progressing through various phases of an intrusion, and culminating in a theft or destructive impact.
Given the sudden popularity of supply chain and firmware threats, it makes sense to take a deeper look at these areas in the context of ATT&CK. Of course, ATT&CK does cover some of the basics of threats in these areas. But at the same time, it’s important to appreciate how broadly these areas apply to the lifecycle of attack. Many of the same issues that are often applied to operating systems and applications can apply to hardware and firmware. They will have their own vulnerabilities, provide their own infection vectors, and allow for some of the most powerful forms of persistence and defense evasion.
With that in mind, let’s take a deeper look at some of the ATT&CK tactics in the context of supply chain and firmware threats. While we don’t go into the details of every technique, we have compiled the following table to highlight some of the most important techniques within eight ATT&CK tactics.
Reconnaissance
Reconnaissance involves a variety of active and passive adversary techniques to identify target assets and vulnerabilities. Almost any reconnaissance effort that can be applied to software will likewise apply to firmware, and the same techniques applied to enterprises can be applied to the supply chain. This can include:
- Actively scanning for flaws within software and firmware
- Looking for artifacts in publicly available update code and update processes
- Identify any open-source dependencies related to firmware and hardware technology stacks
Ultimately, the supply chain provides a great avenue for attacker reconnaissance since there are many suppliers and sub-suppliers (or even logistics partners) who could have code available or that may unintentionally expose sensitive information that could be used later in an attack.
Resource Development
Resource Development allows an adversary to acquire infrastructure that will support active phases of an attack.
- Acquiring servers or implanting firmware backdoors in networking devices such as switches or bare-metal cloud services through:
- Directly manipulating source code repositories used by supply chain vendors to introduce malicious code or vulnerabilities
- Manipulate a vendor or supplier’s software or firmware update processes
- Coerce developers or manufacturing staff to introduce malicious code within a product
Initial Access
Supply chain and firmware attacks truly change the game when it comes to initial access. Instead of a direct assault on an enterprise, supply chain threats arrive in the guise of trusted vendor products and code.
- Targeting any of the dozens of suppliers and subcontractors that work on a product prior to delivery to the customer
- Directly inserting implants in vendor code, manipulating update processes, attacks on vendor signing processes
- Changing low-level device configurations
- Manipulating code in transit or delivery
- Targeting a variety of vulnerable components such as device management protocols (e.g. IPMI, Redfish, etc), debug interfaces, or management web interfaces
It is important to note that VPNs, routers, and security appliances have become some of the most common initial access vectors for advanced adversaries and virtually all major ransomware operators.
Execution
Attackers have many ways to gain code execution through firmware or supply chain attacks. Any implants inserted during the manufacturing process can instantly give an attacker code execution under the guise of valid code. Likewise, Direct Memory Access (DMA) injection or attacks against System Management Mode (SMM) can give attackers code execution below the level of the operating system. Firmware or supply chain vulnerabilities can also often be remotely exploitable. And as with all types of code, attackers can use social engineering to trick users into running the attacker’s code to exploit firmware vulnerabilities or trick them into performing malicious firmware updates.
Persistence
Persistence has always been a key driver behind supply chain and firmware attacks.
- Supply chain attacks by nature will compromise code that an enterprise considers to be “valid” or trusted. If the supply chain is compromised, an organization’s reimaging efforts may only serve to reinfect a given device.
- Firmware code is integrated into system components themselves, instead of residing on traditional storage drives. This not only hides the attacker’s code from traditional security scans but also ensures the code will persist even if a system’s drives are completely erased, re-imaged or even replaced.
- Attackers can establish persistence by gaining control of a device’s boot process to ensure their malicious code is always run during startup. Firmware rootkits and vulnerabilities such as BootHole can allow an attacker to execute their code before the operating system is even loaded.
Privilege Escalation
IT infrastructure products from PCs to virtualization software rely on a wide range of highly privileged code, options, and settings that control the fundamental nature of how a given asset works.
- A kernel-level rootkit can give attackers access to the most trusted layer of the operating system known as Ring 0.
- Malicious bootloaders can allow attackers to gain control of the boot process to load an attacker-controlled OS or patch an existing OS to disable protections.
- Gaining control of System Management Mode (SMM) can allow attackers to run malicious code at runtime that is completely invisible to the higher-layer operating system.
- Attackers can escape from VMs to access the underlying host.
These are just a few of the ways that attackers can abuse low-level vulnerabilities to gain unexpected privileges that can be very hard to detect with traditional security controls.
Lateral Movement
As covered earlier, network devices have proven to be incredibly popular targets for attackers. In addition to initial access, these assets provide attackers with the ability to spread to other hosts and areas of the network. This can allow ransomware operators to spread from a single device to hundreds or thousands. Attackers have also used IoT devices as a way to easily move across a network. This is because IoT devices and network devices both often lack the ability to support local security agents.
Attackers can also use a vendor’s management capabilities in order to spread from asset to asset. For example, attackers can target BMCs, IPMI, or Redfish as a way to control and spread across servers in cloud or datacenter environments. On laptops, attackers can likewise abuse diagnostic and management interfaces such as Intel Active Management Technology (AMT), a feature offered as part of Intel ME and CSME (Converged Security and Manageability Engine).
Impact
Attacks are ultimately about the impact, and once again, this is another area where supply chain and firmware threats are in a class by themselves. One important factor is that supply chain attacks are often massive in scope by their nature. Instead of infecting devices one by one, attackers can use the supply chain itself to deliver malicious code to thousands of devices. From an enterprise perspective, this can mean that entire fleets of devices could be compromised. The low-level nature of supply chain and firmware code also provides the ideal conduits to steal data or cause direct damage. The same ability to sit below the OS and to use or abuse networking or management interfaces can provide stealthy mechanisms for data exfiltration. Access to firmware either at the system or component level can allow attackers to permanently disable devices.
Hopefully, these examples have helped to illustrate some of the big picture around the importance of the below-the-OS attack surface and supply chain security. Supply chain and firmware attacks are not individual techniques or discrete attacks. They are fundamental security disciplines that cut across all types of devices and assets and across virtually all phases of the attack lifecycle. This is why it is imperative to have a lifecycle approach to supply chain security. At Eclypsium, this is our specialty, and if you would like to learn more, please drop us a line at [email protected].
Further reading:
- Check out our full ATT&CK whitepaper to learn more about how Eclypsium protections apply to the ATT&CK framework.
- Read our whitepaper, Network Infrastructure on the Front Line for a deeper analysis of recent attacks on network infrastructure and how to defend against them.