As the supply chain for information technology components and raw materials is squeezed by the AI boom, the secondary market is heating up, and introducing new cyber risk into the IT supply chain.
A 2019 report from the Defense Systems Information Analysis Center of the U.S. Military cited dozens of instances of counterfeit integrated circuits (ICs), memory units, and other components making their way into U.S. missile systems, U.S. Navy helicopters, airplanes, and more. The report estimated that 15% of spare and replacement parts for DoD equipment are counterfeit. The DoD’s Supply Chain Risk Management Guidebook highlights the many ways supply chain issues, including counterfeits, introduce cyber risk into U.S. defense systems.
More recently, in January 2026, Tom’s Hardware reported on how the ongoing DRAM shortage was driving up the prices of the most recent and coveted graphics cards. This price surge led online scammers to start reselling other hardware, rebranded as the latest graphics cards. The report noted that “graphics card scams have always been around, and they flourish during hard times, such as the COVID era or the cryptocurrency mining boom.”
Bloomberg also wrote about the global impact of the looming chip shortage, and Yahoo Finance chimed on the effects the semiconductor supply chain is having on the automobile market. No industry is safe from the AI supply chain squeeze, and the pain felt by consumers who just want an upgraded gaming PC or electric car is already hitting the world’s biggest enterprises, too.
With the increased market for second-use IT hardware, the potential for counterfeit products to make their way into global enterprises, and introduce unmitigated cyber risk, is rising fast. While major OEMs like Cisco have robust programs in place to combat counterfeiting of their products, the changing market conditions are driving increased cyber supply chain risk across the board. Enterprise technology buyers can’t count on manufacturers to mitigate this risk.
Why Is Cyber Risk From Counterfeits in the Supply Chain On The Rise?
The current GPU boom is directly tied to the worldwide push to build out AI data centers being framed as critical infrastructure for the global economy and the defenses of leading nations. The boom is already driving a significant chip shortage, driving prices up and increasing the incentive for counterfeiters to attempt to sell shoddy goods into the booming secondary market.
The refurbished data center equipment market is expected to grow from 40.2 billion in 2024 to over 140 billion in the next decade. The also-growing secondary market for refurbished network equipment was 14.2 billion in 2024, and is expected to double in the next decade.
Counterfeiting takes various forms, and is not limited to the manufacture of completely fake goods. Relabeling older hardware to look like the latest version is common. We recently X-Rayed some counterfeit USB cables to highlight the difference in quality between the real deal and the fake. Counterfeit consumer USB cables are annoying, but relatively low impact. But they illustrate the difficulty in recognizing fakes without looking deeply into the hardware.
How Does Counterfeiting Increase Cyber Risk?
When counterfeit servers, network hardware, and GPUs sneak into the supply chain, the stakes go up considerably. The risk isn’t just that the hardware underperforms or fails early. It’s that counterfeit gear can introduce vulnerabilities that are nearly impossible to detect through normal security operations.
Counterfeit network hardware may ship with modified firmware, or firmware that’s simply never updated past an early version. That means missing security patches, weaker encryption implementations, and in some cases, hardcoded credentials or undocumented remote access capabilities. A counterfeit router or switch running compromised firmware can sit inside a network perimeter for years, passing traffic and logging data, without triggering any software-based security tool. Those tools are scanning for malicious code in software. They’re not looking at whether the hardware itself is legitimate.
The more serious end of this risk involves hardware trojans: malicious logic embedded at the chip or circuit board level during manufacturing. These can be designed to activate under specific conditions, exfiltrate data, or degrade performance in ways that are hard to attribute to sabotage rather than ordinary hardware failure. Detecting them typically requires electron microscopy or other forms of physical analysis that almost no enterprise IT team performs.
The Cisco counterfeit router cases that played out through the 2000s and into the 2010s offer a useful reference point here. Cisco documented multiple instances of counterfeit routers that had been sold through unauthorized resellers, including to U.S. government agencies. Some of those devices had modified firmware.
The Regulatory Dimension
For organizations in the defense supply chain, this isn’t just a security concern. NDAA Section 889 restricts the use of certain foreign-manufactured technology in federal contracts, and CMMC requirements increasingly govern how contractors manage their technology supply chains. Counterfeit hardware that turns out to originate from a prohibited manufacturer could create compliance exposure on top of the security risk.
CISA has also been pushing critical infrastructure operators to take hardware supply chain security more seriously, alongside its better-known work on software vulnerabilities. The underlying logic is the same: you can’t secure systems whose components you can’t trust.
How Counterfeits Get Into The Enterprise or Data Center
Counterfeit hardware tends to enter through procurement. During shortage periods like the current GPU crunch, legitimate channels run dry and buyers start looking at gray market resellers, secondary marketplaces, and unfamiliar vendors. The pressure to source hardware quickly, combined with cost constraints, creates conditions where provenance doesn’t get scrutinized the way it should.
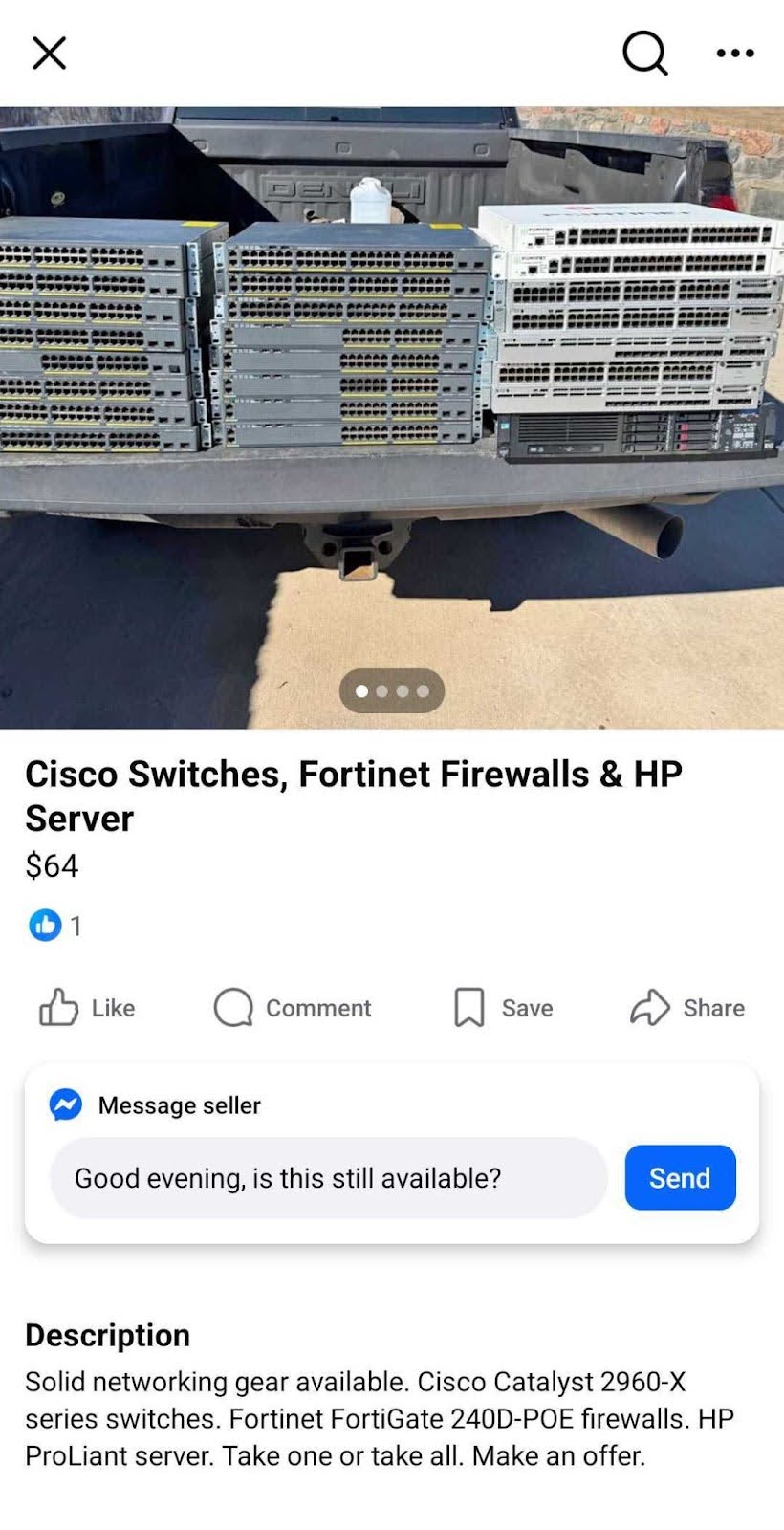
This is a particular challenge for smaller organizations and government contractors who can’t always afford OEM pricing but are still handling sensitive systems and data. A counterfeit component purchased through a gray market reseller to fill a gap during a shortage doesn’t announce itself as such. It shows up in a box, it works (or seems to), and it gets racked.
Relabeling older hardware to pass as newer models is common and relatively easy to execute. Without detailed physical inspection or cryptographic attestation from the manufacturer, a relabeled switch or server can be indistinguishable from the real thing in a normal procurement workflow.
Why Detection Is So Hard
Software vulnerabilities can be found with scanners. Counterfeit hardware usually can’t be identified without physical inspection, and even then it requires expertise and equipment that most organizations don’t have.
This creates an asymmetry that’s worth taking seriously. An organization can run vulnerability scans continuously, patch software remotely, and respond to software-based threats in near real time. Hardware-based compromise requires someone to physically identify, remove, and replace the affected device, assuming they knew it was compromised in the first place. In a large data center environment with thousands of network devices, that’s a significant operational challenge.
Eclypsium is working to reduce the barrier to entry for organizations to secure IT infrastructure across the entire device lifecycle, from procurement to operational lifetime to IT asset disposition. Eclypsium provides a complete, accurate Hardware Bill of Materials (HBOM), along with Software Bills of Materials (SBOMs) and Firmware Bill of Materials (FBOMs) for network equipment and other IT infrastructure, as well as servers, workstations, IP cameras, and more to mitigate the rising risk of supply chain attacks.
Read a case study about how the Eclypsium platform already helped a major global satellite communications provider uncover counterfeit IT devices in their IT environment.






