The Eclypsium team is pleased to announce version 2.16 of the platform. This release introduces new features that further support our supply chain coverage, including the detection of recent threats and device analysis.
Supply Chain Vulnerability & Threat Coverage
Eclypsium dynamically updates content to ensure customers have the latest vulnerability and threat coverage. Below is a list of major vulnerabilities that were added since our 2.14 release:
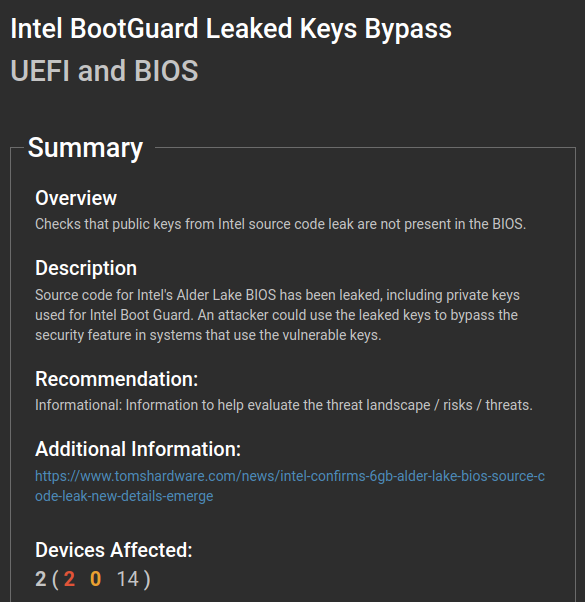
- Intel BootGuard Leaked Keys Bypass – In October 2022 Intel confirmed UEFI source code and keys for the Alder Lake platform. Eclypsium can detect if the BootGuard keys from this leak are being used on Eclypsium-monitored systems.
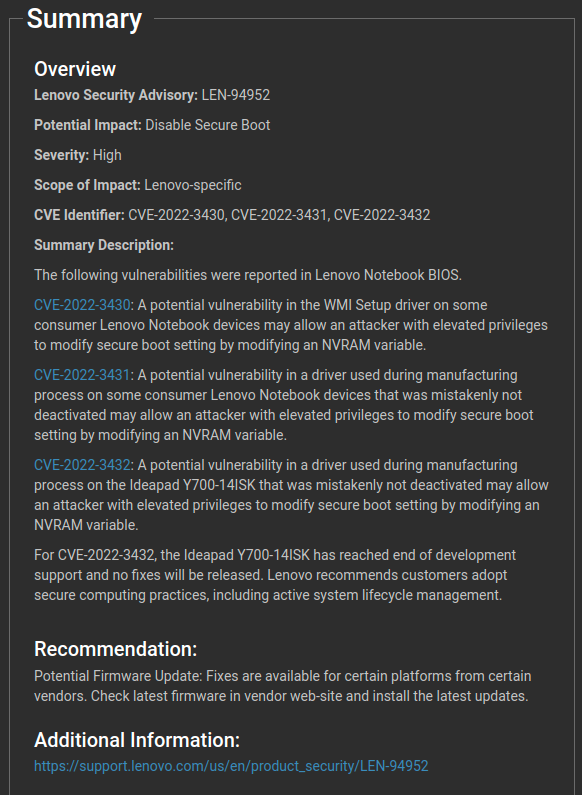
- Vulnerabilities in UEFI DXE drivers used in manufacturing were mistakenly shipped with certain model Lenovo laptops that allow attackers to manipulate NVRAM variables and bypass UEFI Secure Boot. There are three CVEs associated with these vulnerabilities:
- CVE-2022-3430 (WmiSetupUnderOsDxe)
- CVE-2022-3431 (BootOrderDxe)
- CVE-2022-3432 (BdsDxe) – Please note for this particular vulnerability Lenovo has stated: “For CVE-2022-3432, the Ideapad Y700-14ISK has reached end of development support and no fixes will be released. Lenovo recommends customers adopt secure computing practices, including active system lifecycle management.” Eclypsium recommends enabling baselining for all devices and creating alerts that will trigger when firmware changes (as in this case there is no new firmware and a change would be an indicator of malicious activity).
Device Coverage
Eclypsium regularly adds new devices to our network device capability. Authenticated scans are now supported for Cisco ASA and Cisco WLC:

Display wireless networks for Cisco WLC: