CVE-2020-12812, a five-year-old authentication bypass flaw that should have been relegated to history, is being actively exploited. Coming on the heels of two brand-new SAML authentication bypass vulnerabilities (CVE-2025-59718 and CVE-2025-59719) discovered in late 2025, Fortinet administrators must be on high alert and work to remediate them as quickly as possible, as the trend of network device exploitation is continuing.
CVE-2020-12812: The Ghost of Christmas Past
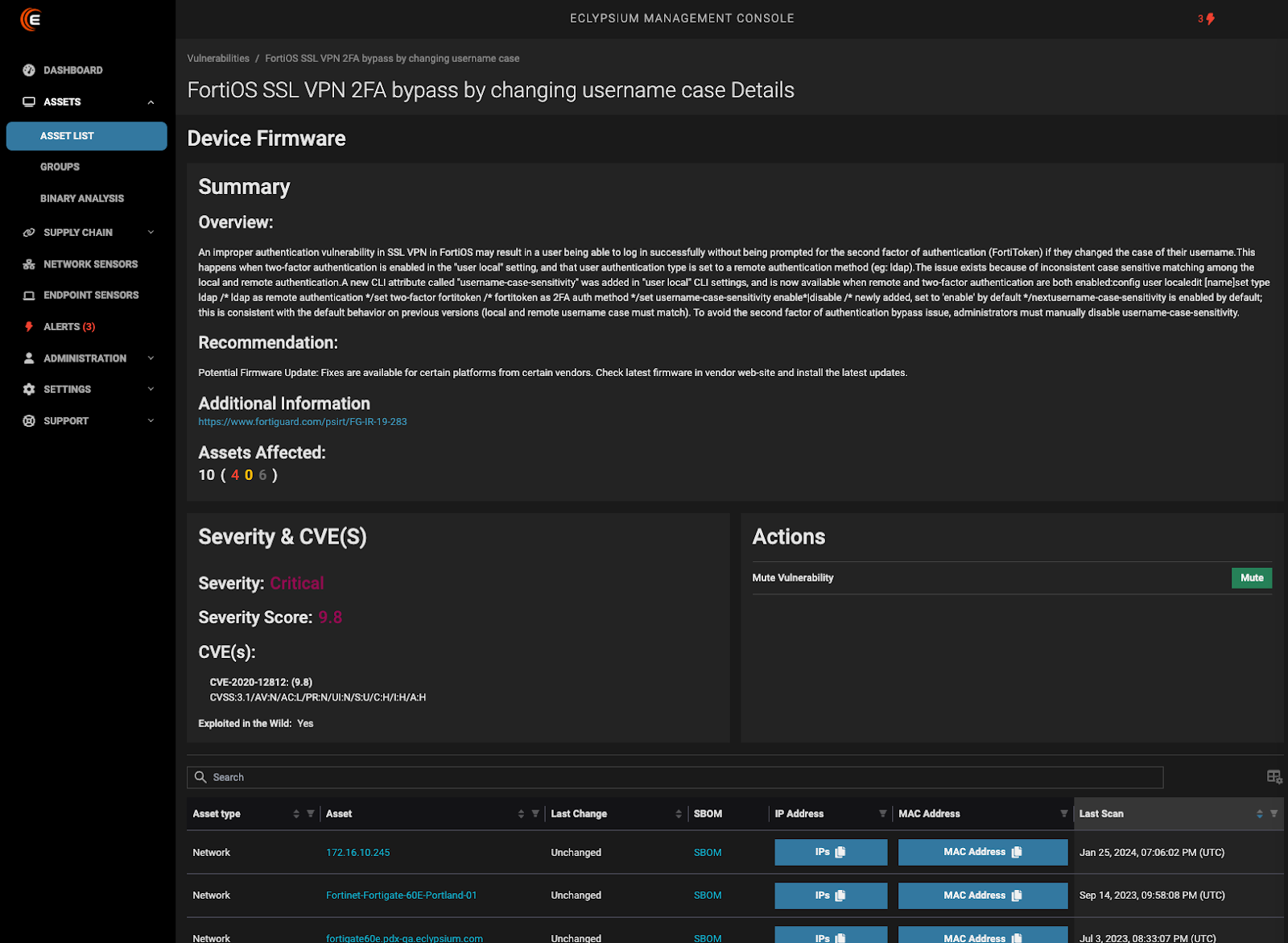
Let’s start with the old vulnerability that refuses to die. CVE-2020-12812 was initially disclosed in July 2020 as an improper authentication flaw in FortiOS. With a CVSS score ranging as high as 9.8, this vulnerability allows attackers to bypass two-factor authentication by simply changing the case of their username.
FortiOS treats usernames as case-sensitive by default, whereas LDAP (Lightweight Directory Access Protocol) does not. When a user has local 2FA configured but is also a member of LDAP groups used in authentication policies, entering a username like “JSmith” instead of “jsmith” causes FortiGate to fail to match the local 2FA user and authenticate directly via LDAP, bypassing the second factor entirely.
Fortinet issued a fresh warning in late December 2025 about “recent abuse” of this five-year-old flaw. Advanced persistent threat (APT) groups, including APT5, Iranian-backed actors, Russian SVR operatives, and notorious ransomware families like Conti, REvil, Hive, and Cring have all been observed exploiting CVE-2020-12812 in the wild. CISA added it to the Known Exploited Vulnerabilities (KEV) catalog back in July 2021, specifically flagging it for use in ransomware attacks.
Perhaps most alarming is that, as of January 2026, Shadowserver tracks over 10,000 Fortinet firewalls still vulnerable to this attack, with more than 1,300 in the United States alone. Five years after disclosure and patches, a substantial attack surface remains exposed for those who have not yet applied patches or implemented hardened configurations.
The Bigger Picture: Infrastructure Devices in the Crosshairs
These Fortinet vulnerabilities aren’t isolated incidents; they’re data points in a larger, accelerating trend. Network edge devices have become the preferred initial access vector for threat actors across the spectrum, from financially motivated ransomware gangs to sophisticated nation-state operations.
The Numbers Don’t Lie
The statistics paint a stark picture. The Verizon Data Breach Investigations Report (DBIR) for 2025 documented an 8x increase in exploitation targeting network edge devices, particularly VPNs, compared to the previous year. Exploitation of these devices jumped from 3% of breaches in 2024 to 22% in 2025. Mandiant’s M-Trends 2025 report indicated that 33% of incidents began with vulnerability exploitation, with 21% of ransomware attacks specifically leveraging vulnerability exploitation for initial access.
Perhaps most damning, one cyberinsurance company reported that organizations using on-premises VPNs faced up to 6.8 times the risk of cyberattack compared to those without VPNs. This finding should give pause to any organization that deployed network security appliances, assuming they would reduce risk. The reality is that they won’t without a proper monitoring program. Trust but verify.
Why Attackers Love Network Edge Devices
The appeal of network infrastructure as an attack target comes down to several fundamental factors that I’ve been discussing for years, including:
- Unmonitored and Opaque: Network devices typically lack the visibility, logging, and monitoring capabilities of traditional endpoints. Due to hardware and software constraints, it’s exceptionally difficult to gain insight into what these devices are actually doing or what they’re not supposed to be doing. Traditional endpoint detection and response (EDR) tools and vulnerability scanners can’t penetrate these appliances deeply enough to detect compromise.
- Purpose-Built with General-Purpose Risks: While marketed as purpose-built appliances optimized for specific functions such as routing or firewall services, under the hood, these devices typically run commodity x86 or ARM processors with general-purpose operating systems like Linux or BSD.
- Complex Code in Update Packages: Eclypsium’s analysis of network device update packages in 2025 found one that had grown in size by 10x over two years and 100x since 2020, with Python imports increasing from zero to over 140, at least one of which contained a known vulnerability. The growing complexity of network device code has resulted in a larger attack surface.
- Lack of Security Software: I’ve encountered very few network infrastructure devices running endpoint protection software because it’s not supported. Not only is security software absent, but fundamental protections such as memory randomization (ASLR) and data execution prevention (DEP) are often missing as well. When a device’s primary job is to route packets or inspect traffic, its security features are usually an afterthought.
- Perfect Position for Command and Control: Network edge devices are ideally located for attackers exposed to the Internet while simultaneously connected to the internal network. This dual-homed positioning makes them perfect candidates for command-and-control (C2) infrastructure, as it can be difficult to distinguish malicious traffic from the device’s legitimate function of maintaining Internet connections.
- Persistence That Survives Everything: When attackers compromise network devices at the firmware level, they establish persistence that survives reboots, patches, and even many incident response efforts. Firmware implants, bootkits, and backdoors installed on network infrastructure can outlast traditional remediation.
How Eclypsium Helps Defend the Network Edge
Traditional security tools weren’t designed to protect network infrastructure, and that gap has become a critical vulnerability. Endpoint agents can’t run on most network appliances. Vulnerability scanners often can’t see into firmware layers where the most dangerous threats reside. Network monitoring tools are designed to detect suspicious traffic patterns, not compromised infrastructure itself.
This is where Eclypsium’s supply chain security platform makes a fundamental difference, providing visibility and control over the firmware and underlying components of network devices that have historically been opaque to security teams.
Discover: Component Level Inventory for Complete Attack Surface Visibility
The first step in defending anything is knowing it exists. Eclypsium’s distributed discovery capabilities proactively identify all Fortinet devices and other network infrastructure across your environment, ensuring you have a complete picture of your attack surface. The platform provides detailed insight into the firmware versions and underlying operating systems (often a customized flavor of Linux) running on each device and enables security teams to search for specific vulnerable versions across the entire fleet.
This matters because even a single overlooked device can provide attackers with the entry point they need. When you’re managing hundreds or thousands of network devices across distributed locations, automated discovery is essential.
Harden: Patch Management and Configuration Hardening
The most fundamental safeguard is ensuring that patch levels are up to date and that devices are properly configured. Eclypsium helps security teams determine where patches still need to be applied and identifies configuration weaknesses that need to be hardened.
For CVE-2020-12812, the Eclypsium platform can identify vulnerable configurations where the specific combination of local 2FA users linked to LDAP exists, allowing teams to prioritize remediation efforts.
Detect and Respond: Detect Vulnerabilities and Threats That Matter
Once you know which devices you have, you need to determine whether they’re vulnerable or already compromised. Eclypsium automatically identifies the specific vulnerabilities actively exploited in real-world APT and ransomware campaigns. This risk-prioritized approach ensures security teams can focus on the issues that really matter without drowning in endless low-priority vulnerability logs.
The Eclypsium platform detected CVE-2025-59718 in customer environments immediately upon disclosure. Earlier this year, Eclypsium successfully identified systems vulnerable to CVE-2024-20399 (the Velvet Ant Cisco NX-OS vulnerability), as well as four additional Cisco vulnerabilities disclosed in August 2024. In the context of the Pacific Rim attacks on Sophos firewalls, Eclypsium demonstrated the ability to detect UEFI implants, bootkits, and a comprehensive list of security misconfigurations, including disabled Intel Boot Guard, missing BIOS write protections, and unlocked flash descriptors.
But Eclypsium goes beyond vulnerability detection to verify firmware integrity—ensuring that the firmware running on your devices hasn’t been altered or backdoored. The platform can compare current firmware to known-good versions and detect both known and unknown threats. It can also compare versions and configurations across groups of devices in your environment against a known-good profile, to identify the needle in the haystack when a single device goes off-book and starts looking malicious. This integrity verification is crucial because sophisticated attackers often install persistent backdoors or modify system binaries to bypass security checks, as observed in the Pacific Rim campaign, where attackers swapped out the cryptographic verification binaries themselves.
Continuous Monitoring: The Key to Early Detection
Perhaps most importantly, Eclypsium provides continuous monitoring for integrity verification and threat detection in device firmware, underlying operating systems, configurations, and components that traditional security tools such as EDR and vulnerability management can’t see. By correlating deep device inventory with vulnerability intelligence, threat data, and behavioral analysis, the platform helps security teams detect exploitation attempts early—before attackers can establish the persistent foothold they’re seeking.
This capability for ongoing firmware integrity verification matters because many threats make subtle configuration changes that may not be immediately apparent. When threat actors compromise network devices, they’re often playing the long game, establishing access that can persist for months or years. Continuous verification is your defense against that patience.
What Needs to Change
The current state of network edge security is unsustainable. All three of the latest Fortinet vulnerabilities require vendor patches, configuration changes, and compensating controls. While standard mitigations like “don’t expose management interfaces to the Internet” remain important, it’s clear that more systemic change is needed to counter the success attackers are having at the network edge.
“Trust the Vendor” Must Evolve: Network devices increasingly contain complex, risky embedded code. Whether it’s firmware or the underlying operating system, the code inside network appliances introduces risk that’s difficult to measure and manage. Requiring Software Bills of Materials (SBOMs) and maintaining detailed inventories of all network devices and their subcomponents should be table stakes for rapid remediation when vulnerabilities are disclosed.
Treat Network Appliances as Sources of Risk: Network edge devices need the same level of monitoring and threat detection as endpoints. Unfortunately, this is often impossible by design because vendors don’t build their appliances to support EDR, vulnerability management, or other established security tool categories. Third-party validation and monitoring capabilities independent of the vendor are crucial for establishing the visibility defenders need.
Implement Proactive Compensating Controls: When the F5 breach was disclosed in 2025, we learned that 44 vulnerabilities were known to attackers before F5 could even disclose or patch them. Many organizations have “n-1” firmware update protocols for network gear to avoid bleeding-edge issues, but unless you’re actively monitoring firmware integrity and the underlying OS, you might never know when it’s compromised. Using third-party tools for validation and vulnerability management is a proactive step to ensure you understand which vulnerabilities exist in your environment and whether they’re being exploited, whether the vendor discloses them or not.
Conclusion
The exploitation of CVE-2020-12812 represents more than just another round of vulnerability advisories. It is a clear signal that network infrastructure devices remain attackers’ preferred entry point into enterprise environments. The speed of exploitation, the sophistication of the techniques, and the breadth of threat actors involved all point to network edge devices as a persistent weak point in enterprise security postures.
The devices we deploy to protect our networks, from firewalls and VPNs to load balancers and routers, have themselves become the attack surface. The lack of visibility, the difficulty of applying traditional security controls, and the devices’ attractive positioning make them ideal targets. When threat actors compromise network infrastructure at the firmware level, they establish persistence that can outlast traditional incident response efforts and survive reboots, patches, and even complete system rebuilds.
The solution requires a fundamental shift in how we approach network device security. These appliances can no longer be treated as devices that we trust by default. They need continuous monitoring, firmware integrity verification, and the same level of scrutiny we apply to endpoints and servers. Third-party validation tools like the Eclypsium platform provide visibility into firmware and low-level components that vendors often don’t expose and that traditional security tools can’t reach.
As we move further into 2026, the attacks on network infrastructure will only intensify. Defenders need to move beyond reactive patching and embrace proactive, continuous verification of the devices that underpin their networks. Because when attackers control your infrastructure, they control everything that runs on top of it.
Related Resources:






