Software bills of materials (SBOMs) have been around for years, but they’re historically ill defined, hard to generate, update, and use. So most organizations don’t.
But a series of new laws and cybersecurity guidelines issued from 2023-2025 may signal a change that will drive more organizations to make practical use of SBOMs, as well as Hardware Bills of Materials (HBOMs) and Firmware bills of materials (FBOMs). The global gold standard for cybersecurity risk standards is NIST 800-53, and in revision 5 it was updated to explicitly mention firmware and hardware as critical parts of any risk management program. This change is already influencing other cybersecurity standards and guidelines to deepen their SBOM requirements.
This post will summarize recent guidelines, regulations, or government memos that encourage increased usage and standards around SBOMs, FBOMs, and HBOMs. We’ll cover what the requirements actually say, how to achieve them, and how to add value for your team’s cyber risk management programs with SBOMs.
Department of Defense Supply Chain Security Guidance from GAO and the Secretary of Defense
In July of 2025, the Secretary of Defense issued a new directive to the DoD highlighting the complexity and risk in the global supply chain. The memo stated:
“The DoD will not procure any hardware or software susceptible to adversarial foreign influence that presents risk to mission accomplishment, and must prevent such adversaries from introducing malicious capabilities into the products and services that are utilized by the Department.”
The memo urged DoD and defense industrial base (DIB) suppliers to adhere to existing supply chain security standards including:
- Cybersecurity Maturity Model Certification (CMMC)
- Software Fast Track (SFT)
- Authority to Operate (ATO) process
- Federal Risk and Authorization Management Program
- Secure Software Development Framework (SSDF)
The memo also urged DoD Chief Information Officer and department CISO David McKeown to issue additional implementation guidance within 15 days. The pressure to actively secure against supply chain threats to DoD programs is rising. The effective use of SBOMs, FBOMs, and HBOMs will be foundational to mitigating risk against critical defense resources.
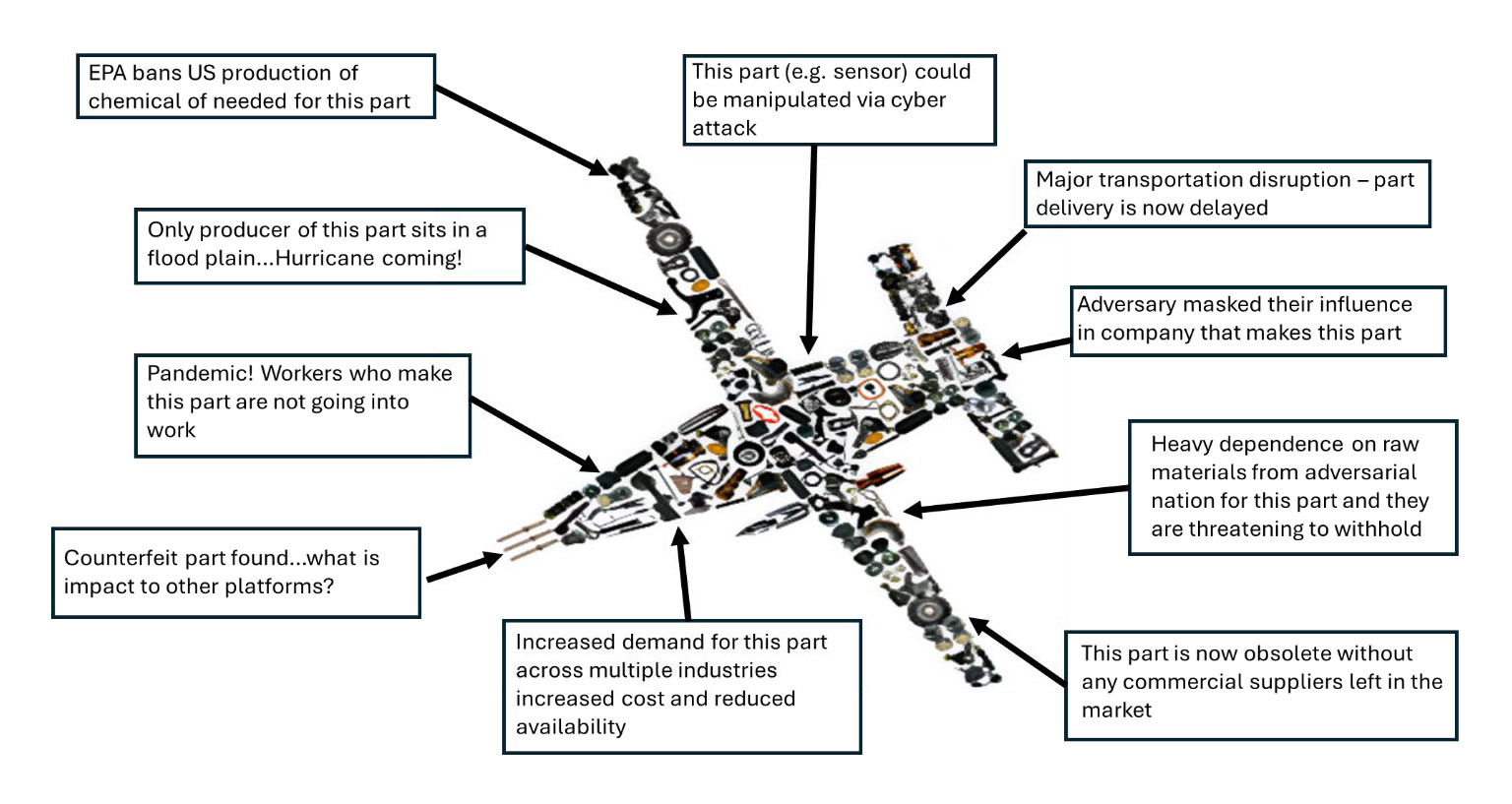
The memo came out after a recent GAO report on the risks to the DoD from heavy dependence on foreign suppliers for critical resources, from microelectronics to the raw materials used for manufacturing DoD technology. That report referenced the recently finalized DoD Supply Chain Risk Management Guidebook that highlighted the many risks to U.S. weapons systems that are introduced through the complex global supply chain that fuels the department.
CISA’s 2025 Minimum Requirements for a Software Bill of Materials
Next up, CISA has released a document titled 2025 Minimum Requirements for a Software Bill of Materials. The document lists and describes each element that should be included in an SBOM to make it practically useful for mitigating risk and vulnerabilities.
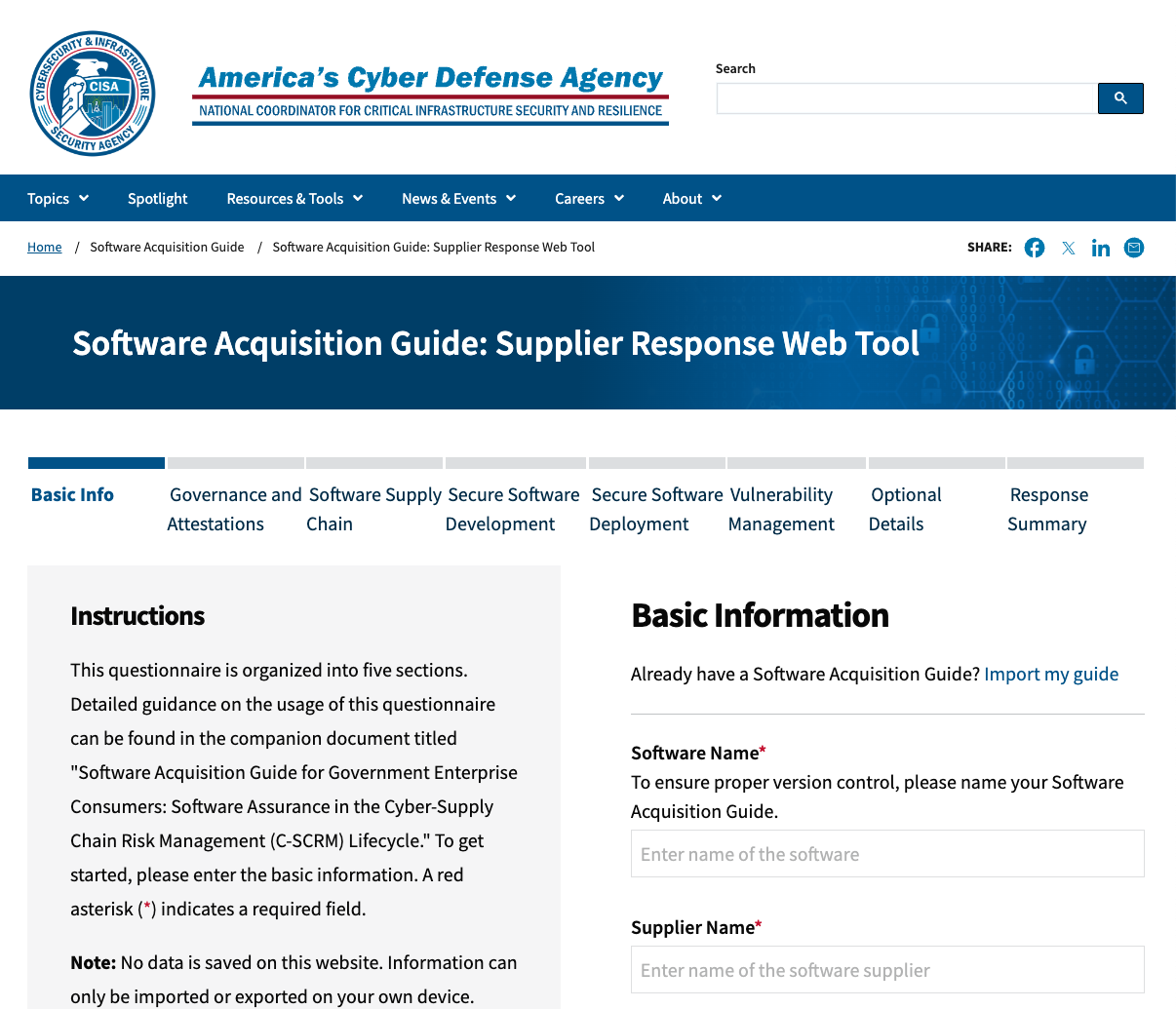
In addition, CISA has released an Interactive Software Acquisition Guide to help organizations assess the security practices of their software vendors. The guide is structured as a progressive checklist that walks organizations through a detailed audit of their supplier’s governance and attestations, software supply chain, development, deployment, vulnerability management, and more.
Golden Dome for America Requires Hardware, Firmware, and Software Bills of Materials
The Golden Dome for America (GDA) is a new missile defense initiative in the United States. Secretary of Defense Pete Hegseth released a memo to Pentagon officials describing detailed requirements for protecting the supply chain of hardware, firmware, and software to be used in GDA.
The GDA memo is notable for its specific inclusion of Firmware Bills of Materials (FBOMs) and Hardware BOMs alongside SBOMs.
For specific details, check out our summary of the SBOM requirements in the GDA memo.
EU Cyber Resilience Act Features Significant SBOM Requirements
The EU Cyber Resilience Act (CRA), requires all organizations bringing “products with digital elements” to the market to provide detailed SBOMs, handle vulnerabilities, and deliver patches in a timely manner. The law went into effect in December, 2024, and will be fully enforced starting in 2026.
The new regulation features extensive requirements for vendors all along the digital supply chain to make SBOMs available to their customers. SBOM requirements laid out in the CRA include:
- Comprehensive Component Inventory: The SBOM must list all software components, including firmware, used in the product, from the operating system down to the smallest modules.
- Detailed Metadata: The SBOM should include metadata for each component, such as version numbers, licensing information, and known vulnerabilities.
- Machine-Readable Format: The SBOM must be in a format that can be easily processed by computers, facilitating automated analysis and vulnerability management.
- Regular Updates:The SBOM must be updated whenever the product’s software is modified, including patches and new features.
- Accessibility: The SBOM must be provided to market surveillance authorities upon request and included in the technical documentation.
Notably, these SBOMs must list software included in “all integrated components” of digital products, meaning that firmware, a growing target of cyberattacks, must be included, and is subject to the same vulnerability handling requirements.
Check out our FAQ on the EU CRA SBOM and supply chain due diligence requirements for more info.
NSA Guidance On SBOM Management
In 2023 the NSA released extensive guidance on how to effectively use Software Bills of Materials as part of a Cybersecurity Supply Chain Risk Management (C-SCRM) program. While not a law or regulation, this document fills in an important part of the supply chain risk management picture for government systems: guidance for practical execution.
In practice, supply chain risk management and SBOM usage are difficult to execute inside government organizations. As noted in the GAO report on supply chains that we referenced above, there are many layers to the DoD’s supply chain. And the lowest layers that provide microchips, subcomponents, and even raw materials for critical defense systems are the most globally distributed, and the most opaque. Standards and practices for supply chain security exist, but effectively executing these programs requires staff and expertise that is often in short supply.
The NSA’s cybersecurity information sheet (CSI) on SBOM management offers practical guidance that ranges from organizational best practices to technical standards to help organizations make practical use of SBOMs and C-SCRM best practices.
Supply Chain Security Practices Must Accelerate To Meet Growing Risk
For decades, cyberattacks have focused on the easiest and most effective attack surfaces, which have been user facing systems, management interfaces, web applications, and devices exposed to the internet when they shouldn’t be. Firmware and hardware components have been a cybersecurity blind spot.
The proliferation of defenses and cybersecurity tools to protect these attack surfaces have imposed increasing costs on attackers targeting these traditional attack surfaces. Now, firmware and hardware level attacks are on the rise, especially by nation state APT groups like Salt Typhoon and Volt Typhoon. Their focus on firmware, end-of-life network devices, and other undersecured targets is driving a shift toward stricter supply chain security and a need for greater protections at the foundational level of critical technologies.
These regulations will require fundamental shifts in how governments and enterprises protect themselves against increasing supply chain attacks.
Check out our supply chain security toolkit for more resources on how to run effective C-SCRM programs.






