Introduced in 2006, Cisco’s NX-OS powers the Cisco Nexus series network switches primarily targeted at large enterprise data centers and service providers. Cisco’s NX-OS represents a different architecture than Cisco IOS (Internetworking Operating System), implementing a Linux sub-system that allows for better memory management, process scheduling, and device driver support. In addition to allowing Cisco to tap into the vast ecosystem of open-source software and tools, NX-OS allows for modularity and the ability to add and remove support within software. NX-OS provides the administrator with an IOS-like interface to manage devices, powered by Linux at the core.
Touted as a privilege escalation vulnerability, CVE-2024-20399 represents a vulnerability in NX-OS that allows an attacker to “jailbreak” devices, jumping from the NX-OS layer down to the Linux operating system. Cisco became aware of this vulnerability being exploited in the wild, reportedly in April 2024, and released an advisory and associated patches on July 1, 2024. The very same day Sygnia, a cyber defense and threat intelligence company, released an initial report claiming responsibility (in a good way) for discovering threat actors using what was then a 0-Day exploit against NX-OS devices. CVE-2024-20399 carries a 6.7 CVSS score from NVD, and a 6.0 CVSS score from Cisco as it requires an attacker to already have administrator-level privileges on the device. On July 2, 2024, this vulnerability was added to the CISA KEV (Known Exploited Vulnerabilities) catalog.
Sygnia identified the threat actor(s) as a group based in China dubbed “Velvet Ant”. The July 1 article builds on previous research released in June 2024 that tied Velvet Ant’s activity back to the exploitation of F5 load balancers. Threat actors exploited vulnerabilities on Internet-Facing F5 devices to maintain persistence and establish C2 (Command and Control) channels. SSH tunnels were established to communicate with internal hosts infected with the group’s malware (named “PlugX”) and since the F5 devices were exposed to the Internet traffic was not blocked.
Back to the most recent incident, the July 1 article makes reference to threat actor behaviors as follows: “exploitation led to the execution of a previously unknown custom malware that allowed the threat group to remotely connect to compromised Cisco Nexus devices, upload additional files, and execute code on the devices.” It is unclear at this time how Velvet Ant was able to gain initial access to the network and then gain access to the Cisco Nexus switches as administrator.
A new article was published on August 24, 2024 – China-Nexus Threat Group ‘Velvet Ant’ Leverages a Zero-Day to Deploy Malware on Cisco Nexus Switches – that included more detailed findings of Velvet Ant activity, including:
- The discovery of “VelvetShell”, the malware toolkit deployed to the underlying Linux OS
- Detailed analysis of VelvetShell, including IoCs (Indicators of Compromise)
- Velvet Ant used functionality in VelvetShell to tunnel/proxy network communications and upload/download files
Given this is just one more example of in-the-wild exploitation of network devices recently, it is important for organizations to apply patches to affected devices and monitor for new vulnerabilities and threats. The Eclypsium platform supports both F5 load balancers and Cisco NX-OS devices in the context of firmware integrity and vulnerability detection. In the example below we’ve detected a system vulnerable to CVE-2024-20399 and four new vulnerabilities disclosed by Cisco on August 20, 2024, including two patches for vulnerabilities that allow a local attacker to escalate privileges.
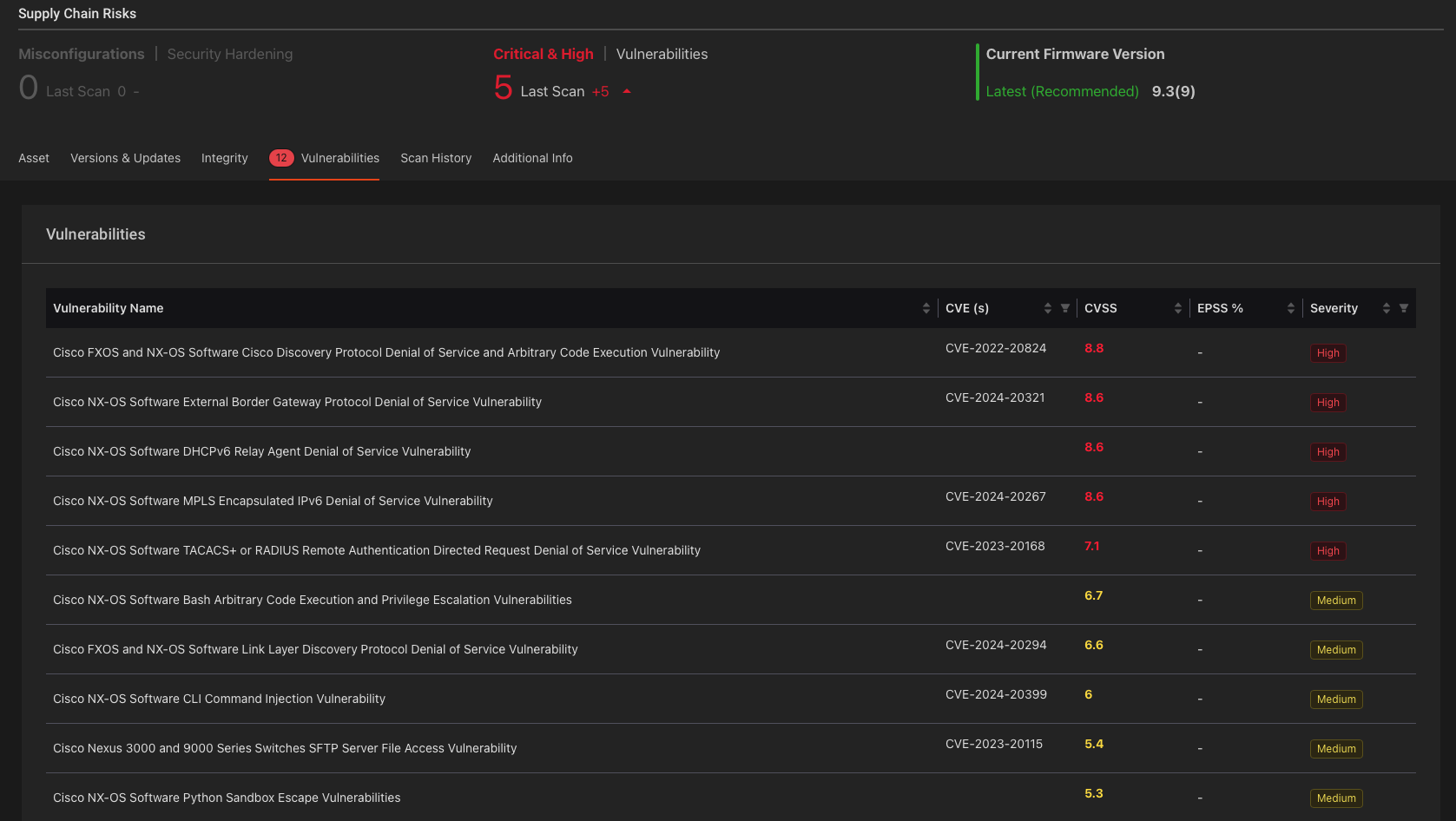
The Velvet Ant TTPs reinforce the need to ensure your organization has good security practices on all devices, including switches and load balancers. Attackers are successfully compromising these devices and using them as both C2 servers and jumping-off points to reach deeper into the network.
References:
- China-Nexus Threat Group ‘Velvet Ant’ Exploits Cisco Zero-Day (CVE-2024-20399) to Compromise Nexus Switch Devices – Advisory for Mitigation and Response
- China-Nexus Threat Group ‘Velvet Ant’ Abuses F5 Load Balancers for Persistence
- China-Nexus Threat Group ‘Velvet Ant’ Leverages a Zero-Day to Deploy Malware on Cisco Nexus Switches
- Cisco NX-OS Software CLI Command Injection Vulnerability
- CVE-2024-20399 (NVD Entry)






