The discovery of the backdoor in xz utils compression software last week has shone a spotlight on the threats to the digital supply chain. Wired has an excellent analysis on the attack, theorizing the years-long campaign may have been by the Russian foreign intelligence service (which was also behind the SUNBURST aka Solarwinds attack). Here are our key takeaways and how we’re protecting Eclypsium customers’ operational systems:
The First of Its Kind, But Not the Last
The xz backdoor (CVE-2024-3094), for all its sophistication and extensive effort put into both gaining access far upstream in the supply chain and obfuscating its intentions, likely failed to achieve its creators’ ultimate goal. However, cybersecurity plays out over longer timelines than the current media frenzy will support, and the fact is that the specific mission to backdoor a critical component in the supply chain succeeded. Supply chain attacks aren’t a new problem as malicious packages are being found on GitHub and in NodeJS with significant frequency. What is new with the xz backdoor is that an actor gained trusted access to code used ubiquitously across the industry, disabled security tooling designed to detect the exact functionality they were leveraging, and implanted a highly sophisticated backdoor in a widely used utility. This may have been the first attack of its kind, but it certainly won’t be the last. Threat actors learn from their mistakes, and the next attempt will be better designed, taking performance impact into account as a possible detection vector.
An Opportunity for a Tabletop Exercise
This was a win, albeit a lucky one, and it should serve as both a wakeup call to the industry at large and an opportunity for organizations to practice what their response process will look like when “the big one hits.” The xz backdoor was a near-miss digital supply chain attack, but organizations shouldn’t simply breathe a sigh of relief because they weren’t impacted this time. There has been some speculation around whether this backdoor was intended to be discovered to throw attention off the “real” backdoor and while this reeks of conspiracy theory, it’s not completely without merit. Advanced threat actors don’t spend all their effort on a single target of opportunity, they go after many as they know every compromise has a limited lifespan. It’s safe to assume that there are other projects being at least investigated as potential targets, if not being actively targeted, and it’s even within the realm of possibility to say one has been successful—you don’t know what you don’t know.
Coincidentally, in March CISA released materials to help with a tabletop exercise involving a widespread open-source supply chain attack.
Commitment to Open Source Projects
A fact frequently overlooked until incidents like this is the corporate world’s reliance on Open Source Software (OSS). Open source has done amazing things for computing: IoT devices, smart homes, smart cars, nearly every piece of technology today contains some open source code. Tech giants have created massive wealth by leveraging OSS and in the process, created an imbalance in terms of responsibilities. Many critical OSS components are built using libraries and dependencies created and maintained by a few people, sometimes even one developer. By its nature, open source is free, which means maintainers of even the most popular open source tools still generally need to hold regular jobs. Unlike commercial software companies, with armies of paid developers fixing bugs, testing new features, and examining code changes through the lens of security, open source projects rely on volunteers.
This is an unsustainable model; corporations with resources need to reconsider their relationships with the open source community because it’s unfair to the project maintainers, customers, and the ecosystem at large to take everything but give nothing in return. The same situation happened with Log4j, another hugely popular software package which made the news in 2021 when it was exploited en-masse. While Log4j’s impact was far larger, the situation was very much the same. A critical component of software relied on by multibillion-dollar companies like Apple, Twitter, and a myriad of others, Log4j was and continues to be a volunteer project run largely for free, by developers who aren’t financially supported to maintain it. Their efforts in patching the vulnerabilities were exemplary, but this didn’t shield them from criticism as though they were directly responsible for the reliance the world had built on a project they worked in their spare time.
How Eclypsium Can Help
The xz backdoor was identified before it made its way into more stable versions of Linux. Some versions of Alpine, Arch, Debian, Fedora, Gentoo, Kali, OpenSUSE Linux distributions are affected. Eclypsium has added detections for the presence of the xz backdoor in production systems as part of our ongoing extraction and analysis of firmware and software binaries. These detections will work automatically after a new install. In addition, Eclypsium customers can upload Linux images that they suspect may have this backdoor to the Eclypsium backend for analysis using the Upload function (see screenshots below). Specifically, our current detection looks for:
- Artifacts of the malicious versions of the library
- Artifacts of the malicious crypto materials, including keys
- IFUNC hijack method
In addition to basic fingerprinting of malicious code, the Eclypsium platform also performs advanced static analysis of firmware binaries to detect unknown threats that use similar techniques to the xz backdoor.
Ultimately, our goal is to provide additional layers of defense against increasingly frequent and sophisticated supply chain attacks. Organizations need to transition to a posture where third-party code (whether open source or proprietary) is suspect and should be validated and monitored. To that end, we have developed multiple techniques for analyzing IT infrastructure code to detect threats and vulnerabilities.
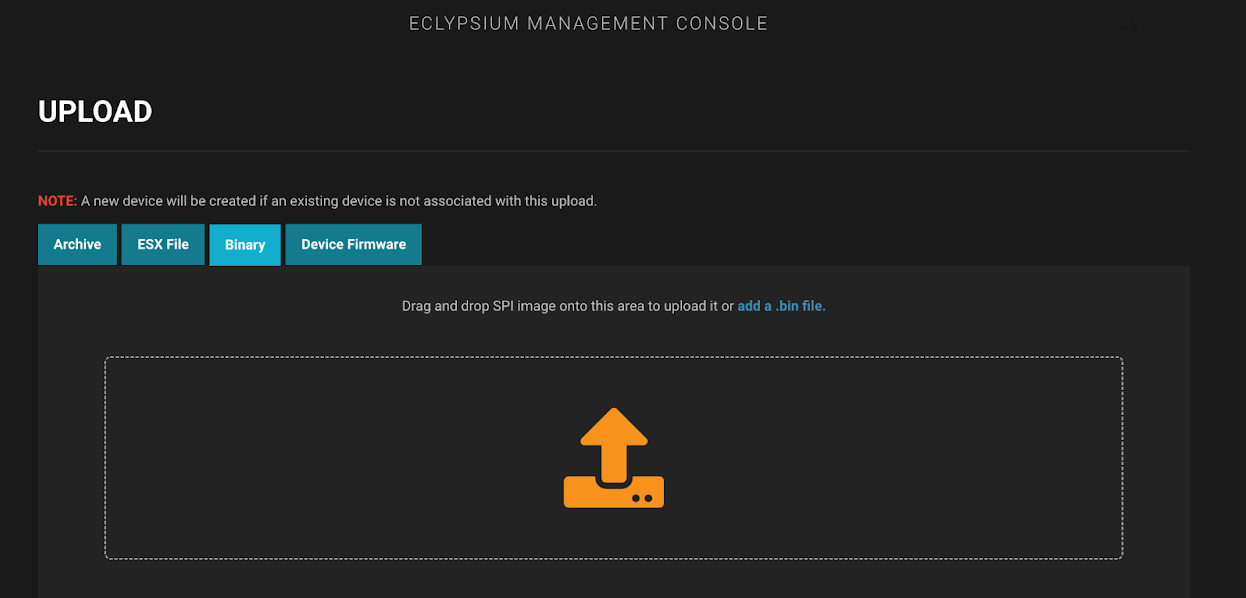

More broadly, the Eclypsium platform helps customers to quickly identify systems affected by certain widely used components. In the case of the xz backdoor, the vector was an open-source utility primarily used in Linux distributions. But the same type of supply chain complexity affects other IT infrastructure. This Eclypsium product tour shows how the platform helps organizations quickly assess their exposure to supply chain incidents using the example of vulnerable Infineon TPMs and a firmware bug in HPE SSDs that threatened data loss.
Further Reading






