© 2025 Eclypsium, Inc.
Eclypsium ensures the integrity of every device in your IT infrastructure.
Why Now?
Cyber attacker tactics have shifted, targeting endpoint firmware and network edge devices, where traditional EDR and vulnerability management can’t see.
Eclypsium monitors these hidden attack surfaces, detecting threats, and alerting on compromised integrity and vulnerabilities other tools miss.
“The roots of trust in your IT infrastructure are extremely important, yet are extremely difficult to inspect and not well understood. Eclypsium’s supply chain security solution solves these critical problems simply”
– Tim Lisko, Senior Director of Security Engineering, DigitalOcean
Stop Threats That Persist Below The Surface
Attackers hide where your EDR can’t monitor. Eclypsium’s unified platform monitors and protects low-level code, firmware, network edge devices where adversaries live off the land and persist even after a total OS re-install.
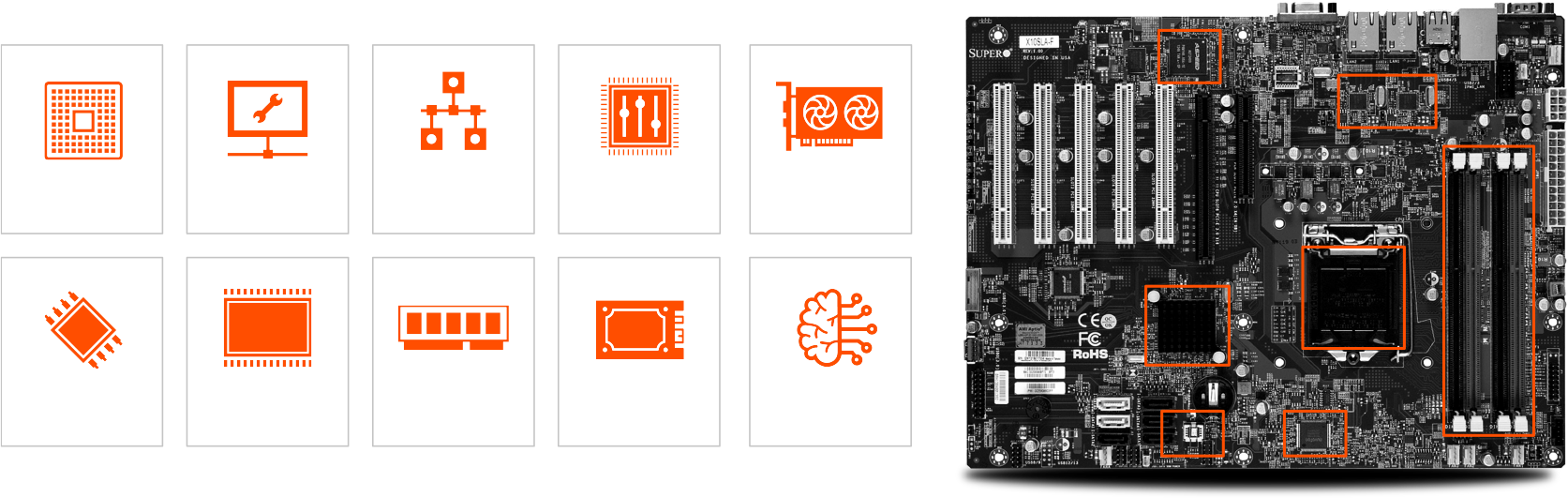
Inventory and Identify Every Component
Eclypsium delivers on-demand Software Bills of Materials (SBOMs), Firmware BOMs, and Hardware BOMs, for a more complete inventory than ever before.
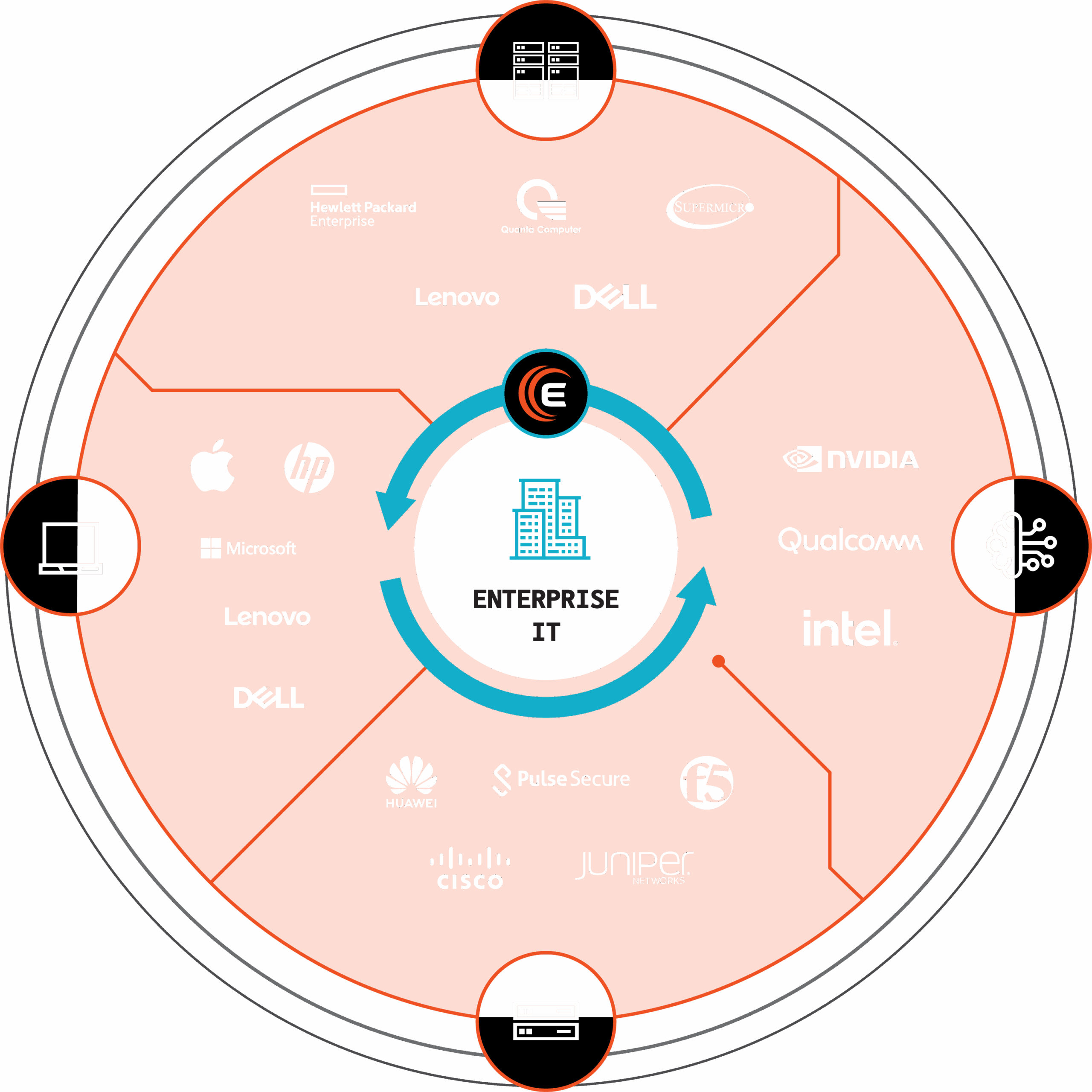
Eclypsium discovers and illuminates your IT estate.
Laptops & Desktops
Servers
Networking Devices
AI Data Centers
Harden Your Infrastructure Against Rising Supply Chain Threats
- Monitor firmware integrity and configuration drift
- Automate Patching for Proactive Protection
- Manage and mitigate known and unknown vulnerabilities
Download the Eclypsium Supply Chain Security Platform Solution Brief to Learn More
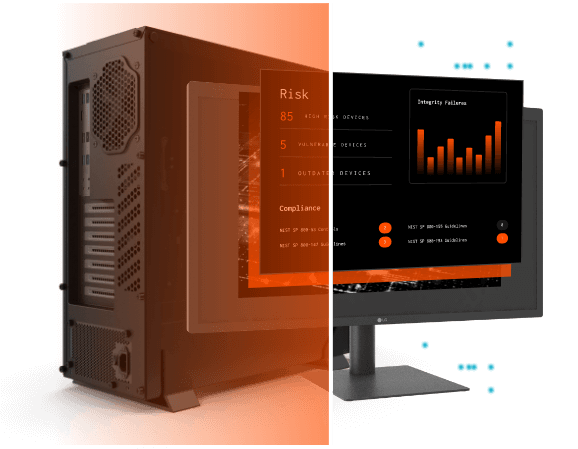
Detect & Respond To Threats Hiding Below the Surface
- Detect Indicators of compromise in hardware, firmware, and software
- Catch attack tactics and tampering that evade or disable EDR agents
- Automate response actions with configurable alerts, REST APIs, and SIEM/SOAR Integration
Case Studies_
Learn How Global Banks, Satellite Communications Providers, and AI Data Centers Are Using Eclypsium To Secure Their Digital Supply Chains and Protect The Foundations of their IT Infrastructure.