As far back as the spring of 2017, UEFI bootkits began to appear in the wild. The first such implant was named “Spy Shadow Trojan”, and was discovered by the Qihoo360 research group based out of China. Someone had purchased a laptop off of a marketplace and the device kept adding a backdoor spy admin account named “aaaabbbb“ to the Windows OS: a rudimentary, but effective attack on that device’s supply chain lifecycle, one that is commonly abused.
After doing a forensic analysis of the device’s UEFI, the researchers discovered an advanced, flexible, and powerful UEFI implant; one capable of repeatedly re-infecting the Windows OS, and one that could run on a wide swath of modern-day Windows devices including Windows 10. This is likely the first ITW (In The Wild) UEFI implant discovered, predating even the infamous LoJax UEFI implant that APT 28 (Russian GRU) leveraged in a multi-year campaign. These earlier Spy Shadow Trojan’s known targets were located in China, Iran, Russia and Vietnam, complicating attribution of the threat actor(s) behind the campaign.
Fast forward to today, some 5 years later, and an upgraded version of the implant has been discovered again in the wild. Kaspersky determined the implant they’ve dubbed “CosmicStrand”, to be every bit as powerful as its predecessor and hints at a possible campaign running for years, with very few samples discovered in the wild. While that may be comforting to hear for some, it shouldn’t be; UEFI-level firmware attacks are often found to be multi-year campaigns which go undiscovered precisely because they are nefariously difficult for most security solutions to detect.
In fact, the primary attacker objective in developing and deploying such bootkits is to subvert every other control within the Windows OS and the 3rd party cyber solutions built to support it. When an attacker can operate at this level, they no longer need to contend with today’s AV/EDR/XDR technologies, allowing them to accomplish their objectives be they espionage, data exfiltration or total destruction of a device. In fact, we don’t yet know if there is an APT or criminal nature to the threat actors behind CosmicStrand. That says a lot: UEFI implants are useful for any actor, with any objective, including those who might shift from espionage to destruction.
Detecting CosmicStrand With Eclypsium
Eclypsium uses a variety of detection techniques to identify both known and unknown versions of firmware implants, backdoors, rootkits, malicious bootloaders, and other related threats. In this case, we were able to natively detect CosmicStrand on Day-0 in multiple ways including:
1. Detecting Unknown UEFI Implants Without the Use of IOCs
Firmware implants are used in a wide range of threats from common malware and ransomware to highly targeted APT attacks. As such, there is no guarantee that a particular implant will have been seen before, especially since most UEFI-targeting attacks are associated with long-running multi-year campaigns. As is the case with CosmicStrand, Eclypsium detects implants even when no signatures or IOCs exist. In this case we were able to detect the implant using the following techniques.
- Known-Good and Known-Bad Firmware Checks
One such method is by performing a set of known-good integrity checks of UEFI and component firmware on the device. The solution includes an extensive library and baseline of the UEFI firmware components present on each model and version of devices of the majority of manufacturers. If the firmware is modified by an attacker, Eclypsium will detect the change and alert that the firmware has changed and is unrecognized.
Conversely, if a known-bad UEFI image is detected on a system, Eclypsium identifies the threat and an alert is generated:

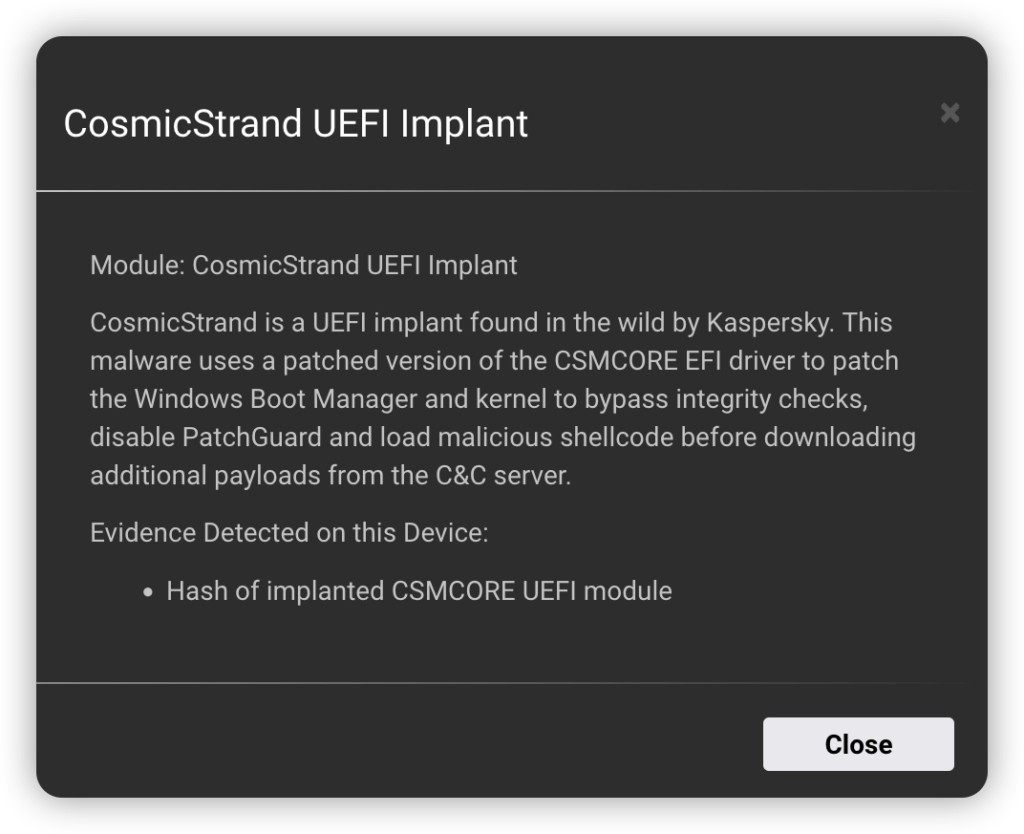
- Firmware Analysis
Eclypsium performs automated and extensive static and heuristic analysis of the firmware itself. In this case, our detection logic identifies operations and characteristics of the firmware images, file systems, executables, and configuration which reveal malicious and suspicious contents and activity. In the case of CosmicStrand:
- Detecting Patient-Zero Unknown Threats
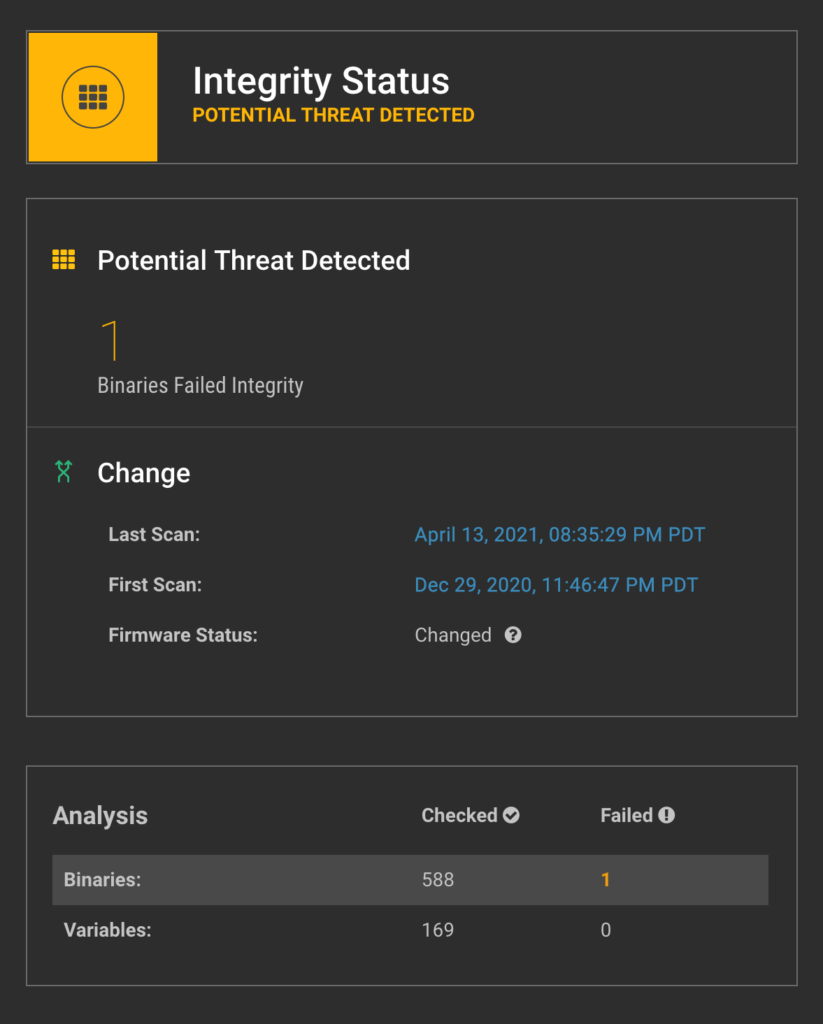
Given that the majority of UEFI-based threats discovered in the wild are long-running campaigns that had not been discovered for years prior, it is not uncommon for UEFI implants to not yet have a known-bad signature. Thankfully, Eclypsium has been able to detect these “Patient Zero” threats for as long as the solution has been around, whether or not a signature is available.
In this case (and any others like it) Eclypsium will have detected the modified and suspicious firmware component, flagging it as an unknown “Potential Threat”, with a firmware binary failing whitelist (meaning we know it is a firmware component that did not ship from the system vendor). In this way, a customer would have been alerted to investigate this system even as far back as 2017, the inception of this long-running campaign.
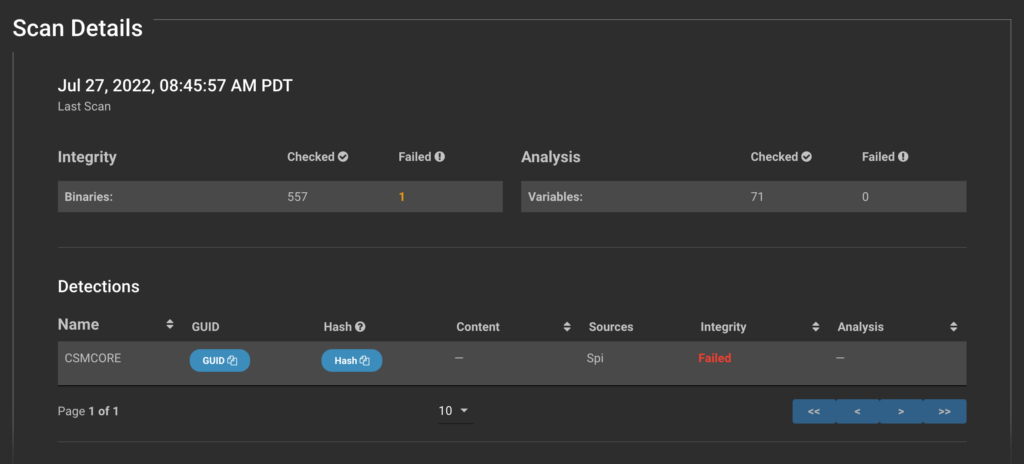
2. Detecting Known UEFI Implants Using IOCs
First, we want to thank Kaspersky for giving us access to this CosmicStrand sample, allowing us to build a custom detection rule for our customers.
The Eclypsium platform uses signature detection in those cases when known IOCs (in this case, ones our researchers derived from the sample provided by Kaspersky) can provide high-confidence detection and alerting. Organizations can leverage this capability to effectively hunt for specific campaigns that may be targeting their vertical, for example.

Recommended Actions
- Eclypsium detects this implant both through advanced UEFI integrity checks that alert after any tampering with UEFI firmware is discovered and specific indicators of compromise for this threat.
- On-premises Eclypsium customers should validate that the latest content updates are installed on their instances to ensure detection is active in Eclypsium scans.
- As of today, indicators of CosmicStrand have not been found in any of the devices that are scanned into Eclypsium’s cloud environment. Eclypsium continues actively scanning across available data.
- If you or a partner detects an instance of CosmicStrand (or any other UEFI implant, known or unknown) and would like to have it analyzed by our research team, please contact us.






