Most organizations trust IT products to be developed and shipped securely by default. But the reality is that each piece of your IT infrastructure depends on an incredibly complex supply chain. Every hardware, firmware, and software component can include vulnerabilities or even malicious low-level code.
Attackers take advantage of supply chain complexity, targeting vulnerabilities in hardware, firmware, and software components. These types of threats evade EDR and can maintain persistence after patching and rebooting—leading to devastating results.
“The roots of trust in your IT infrastructure are extremely important, yet are extremely difficult to inspect and not well understood. Eclypsium’s supply chain security solution solves these critical problems simply.”
Tim Lisko, Senior Director of Security Engineering
DigitalOcean
How do you learn about these risks before purchasing an IT product? Upon receipt, how can you validate that what you have received is what is expected? And once in production, how can you continuously monitor and remediate risk to these low-level components?
Defend Against Supply Chain Threats
The Eclypsium supply chain security platform protects hardware, firmware, and software components. With Eclypsium, your teams can quickly and simply implement critical security controls to protect against below-the-surface threats: asset inventory, vulnerability management, and threat detection.
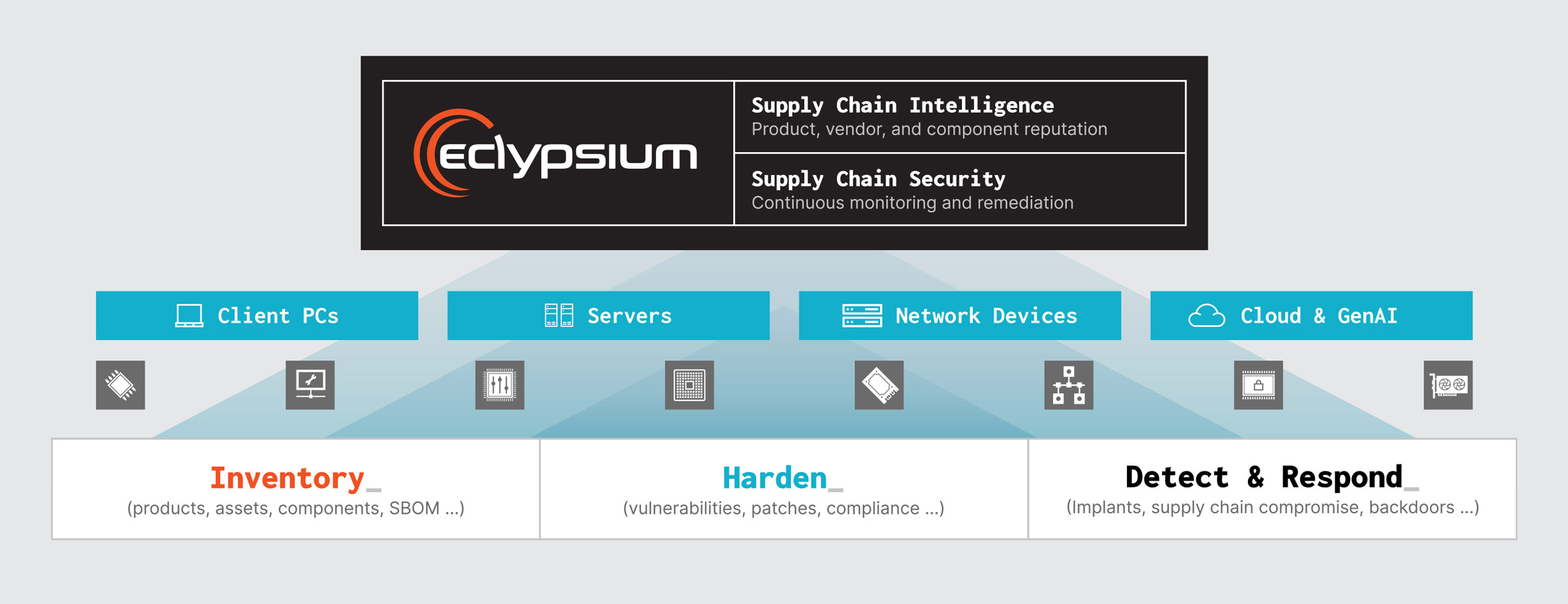
| INVENTORY | HARDEN | DETECT & RESPOND |
| Dynamic inventory of production assets – Build an inventory of every piece of enterprise IT infrastructure, down to the hardware, firmware, and software level. On-demand SBOMs – Generate software bills of material on demand, including hardware and firmware components of devices. Assess product risk – Equip security and procurement teams to understand the risk inherent in those products before purchase. | Prioritize infrastructure vulnerabilities – Gain insights into low-level vulnerabilities in hardware, firmware, and software components. Simplify compliance – Track issues at the hardware and firmware levels in frameworks such as NIST 800-53. Automate firmware updates – Schedule and automatically apply critical firmware patches. | Detect threats that evade EDR – Alert on implants and other indicators of compromise for low-level components of your IT infrastructure. Defend against tampering and counterfeit components – Validate that assets have not been tampered with and have authentic components. Correlate with other data – Send alerts to SIEM and SOAR to give analysts improved context. |
Automata Binary Analysis System
The Eclypsium platform is powered by the most sophisticated binary analysis system on the market. Eclypsium Automata replicates the domain expertise and reverse-engineering techniques of our expert security research team. Importantly, Automata runs 24/7 and analyzes 100% of new binaries in customer environments, protecting against previously unknown threats, vulnerabilities, and misconfigurations. It uses multiple methods and ML models, and scales to handle millions of firmware and software binaries without requiring any action from the customer.
Eclypsium Benefits
- Protect Production Assets: Improve mean-time-to-detection and the security posture for your enterprise IT at the most fundamental levels.
- Lower Hardware Costs: Extend the lifecycle of devices by baselining and detecting change low-level components.
- Reduce Digital Supply Chain Risk: Make better IT procurement decisions and quickly assess the impact of supply chain threats.
- Regulatory Compliance: Easily implement security controls for device integrity and firmware security.
About Eclypsium
Eclypsium’s cloud-based platform provides digital supply chain security for critical software, firmware and hardware in enterprise infrastructure. Eclypsium helps enterprises and government agencies mitigate risks to their infrastructure from complex technology supply chains.






