Free Salt Typhoon Risk Assessment
Eclypsium is offering a free risk evaluation to companies that are concerned they may have been affected by Salt Typhoon. Start your free risk evaluation here.
The landscape of global cyber threats continues to evolve, with sophisticated, state-sponsored campaigns from China gaining attention and including network appliances and devices as targets. Among these are four major Advanced Persistent Threat (APT) groups: Volt Typhoon, Salt Typhoon, Flax Typhoon, and Velvet Ant. Each of these groups exhibits unique strategies, but all are believed to be aligned with China and their broader geopolitical objectives, particularly cyber espionage and targeting critical infrastructure (although there is some debate, regardless, network infrastructure is in the cross-hairs). Below is a breakdown of each campaign/threat actor group, along with some resources to help everyone understand the techniques and differences between them:
Volt Typhoon: Stealth and Espionage
Volt Typhoon—also known as Vault Typhoon—has been active since at least 2021, specifically focusing on U.S. critical infrastructure. This group operates using stealth techniques known as living-off-the-land (LOTL), which means they rely on built-in system tools instead of traditional malware, making detection more difficult. Volt Typhoon’s campaign has primarily targeted communications infrastructure, including in Guam, a critical U.S. military hub. The group often gains access via compromised Fortinet devices and proceeds to extract credentials to pivot further into the network, staying hidden by using proxy devices like SOHO routers and firewalls.
Once inside a target network, Volt Typhoon avoids the use of malware and instead executes system discovery and credential theft through command-line tools like PowerShell and Windows Management Instrumentation (WMIC). This allows them to exfiltrate data while remaining under the radar. The group’s long-term strategy focuses on pre-positioning within infrastructure systems, allowing them to launch destructive attacks if tensions between China and the U.S. escalate.
- Threat Intelligence Research: Volt Typhoon Compromises 30% of Cisco RV320/325 Devices in 37 Days – “Our data indicates that predominantly Cisco RV320/325 devices were impacted in the last 37 days. Cisco RV’s are network edge devices. It appears that, in keeping with previous reports, Volt Typhoon may aim to use these compromised devices to transfer stolen data or connect to target organizations’ networks.”
- Volt Typhoon (Mitre Att&ck)
- Routers Roasting on an Open Firewall: the KV-botnet Investigation
- Volt Typhoon targets US critical infrastructure with living-off-the-land techniques – “Volt Typhoon proxies all its network traffic to its targets through compromised SOHO network edge devices (including routers). Microsoft has confirmed that many of the devices, which include those manufactured by ASUS, Cisco, D-Link, NETGEAR, and Zyxel, allow the owner to expose HTTP or SSH management interfaces to the internet.“
Salt Typhoon: Targeting ISPs and Data Persistence
Updated December 16, 2024
Since this article’s publication, a wave of new disclosures has surfaced, indicating that Salt Typhoon has maintained extensive persistent access to telecommunication carrier systems in the U.S. and abroad. These disclosures spurred the FCC and CISA to issue new guidance to cyber harden telecommunications networks, as well as the U.S. Senate Subcommittee discussions about potential cyber legislation. We have published new material about Salt Typhoon and the FCC and CISA Guidance. See links below for additional further reading.
While Salt Typhoon (also known as FamousSparrow, GhostEmperor, and UNC2286) has not garnered as much publicity as other APT groups, it has been linked to significant intrusions within U.S. Internet Service Providers (ISPs). Salt Typhoon’s campaign has focused on compromising routers and other network devices to establish persistent access. Their activities have been primarily espionage-oriented, to collect sensitive data, such as authorized wiretaps, from ISP networks while maintaining a low profile. This threat actor mirrors some tactics from other Typhoon groups, especially using LOTL techniques to prolong their foothold in target environments. Salt Typhoon exploits several known vulnerabilities, including Ivanti Connect Secure VPN, Fortinet FortiClient EMS SQL Injection Vulnerability, Sophos Firewall Code Injection and Microsoft Exchange ProxyLogon. The group likes to use legitimate tools like Windows Management Instrumentation Command (WMIC.exe) or PsExec to penetrate further into networks. Once inside, the group uses “backdoor” malware known as GhostSpider, SnappyBee, and Masol RAT.
- Detecting and Mitigating Salt Typhoon + Other Chinese APTs
- Impact of Salt Typhoon: FCC and CISA Issue Urgent New Guidance to Secure Telcos
- FCC Fact Sheet: Impacts of Salt Typhoon Attack and FCC Response
- China’s Salt Typhoon Hacks AT&T and Verizon, Accessing Wiretap Data: Report
- U.S. Wiretap Systems Targeted in China-Linked Hack
- Salt Typhoon APT Subverts Law Enforcement Wiretapping: Report
Flax Typhoon: Hijacking IoT Devices
Flax Typhoon stands out because it uses Internet of Things (IoT) devices as entry points into its targets’ networks. This APT group has been observed exploiting public-facing servers and leveraging well-known vulnerabilities to gain access. They primarily focus on entities in Taiwan but have been expanding globally. Their tactic involves using tools like China Chopper and SoftEther VPN to establish persistence. Flax Typhoon relies heavily on hands-on activity, and once they have gained administrative access, they use the Remote Desktop Protocol (RDP) to maintain control over compromised systems.
What makes Flax Typhoon particularly dangerous is its extensive use of compromised IoT devices—such as cameras and DVRs—to build botnets that can be used for command and control (C2) purposes. These botnets allow the group to launch attacks, exfiltrate data, and scan for additional vulnerabilities, making them a versatile and persistent threat.
Velvet Ant: Yet Another Chinese APT
Velvet Ant is one of the lesser-known Chinese APT groups but has been growing in prominence due to its focus on supply chain attacks. The Group has been observed targeting critical software updates and firmware supply chains, with the aim of indirectly infiltrating larger networks. While detailed reports on Velvet Ant are still emerging, the group’s approach bears similarities to previous campaigns by Chinese APTs, which exploit trusted relationships between software providers and their customers.
- Eclypsium Blog Post: Squashing the Velvet Ant: How Eclypsium Protects Cisco NX-OS and F5 Load Balancers
Mitigation Strategies
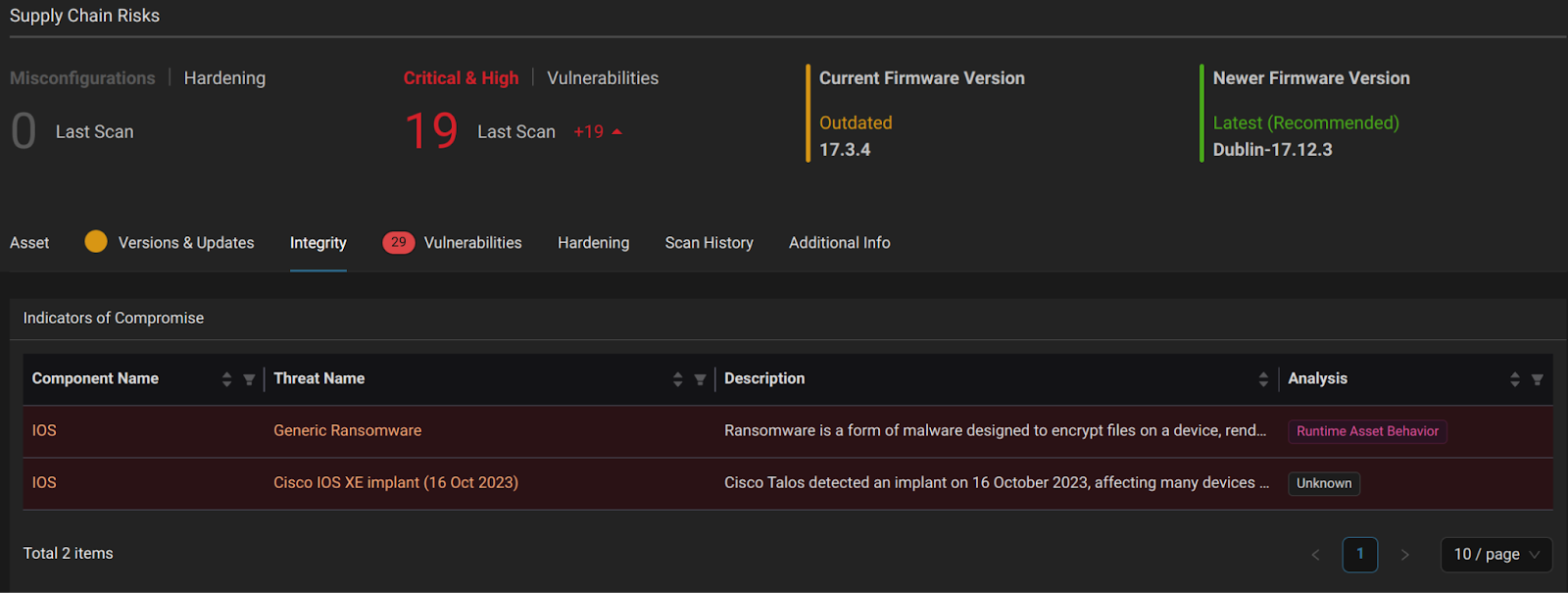
Defending against these campaigns is challenging, given these groups’ stealthy techniques and legitimate tools. Organizations must prioritize behavioral monitoring to detect unusual command-line activity, ensure network devices are correctly configured, and regularly audit user privileges. Patch management is crucial, as many actors exploit known vulnerabilities in IoT and network devices. The Eclypsium supply chain security platform provides several techniques for discovering vulnerabilities, threats, and integrity violations in network infrastructure. The example below represents findings from a Cisco IOS XE device, including detection of known threats:
In summary, the activities of Vault Typhoon, Salt Typhoon, Flax Typhoon, and Velvet Ant illustrate a well-coordinated effort by China to conduct espionage, data collection, and potentially destructive cyber operations across various sectors. Staying ahead of these threats requires a robust defense strategy that includes detection and prevention strategies that include your IT infrastructure devices.