© 2025 Eclypsium, Inc.
Why Is Firmware Security Urgent Now?
Cyberattacker tactics are shifting to target undermonitored attack surfaces. Exploitation of firmware vulnerabilities is on the rise by both ransomware gangs and nation state APTs. And attackers are moving faster than ever to target newly disclosed vulnerabilities. As attackers turn up the volume of attacks on firmware, defenders trust Eclypsium to help them stay ahead.
TRUSTED BY LEADING ENTERPRISES
Eclypsium Protects Enterprises Against Firmware Attacks_
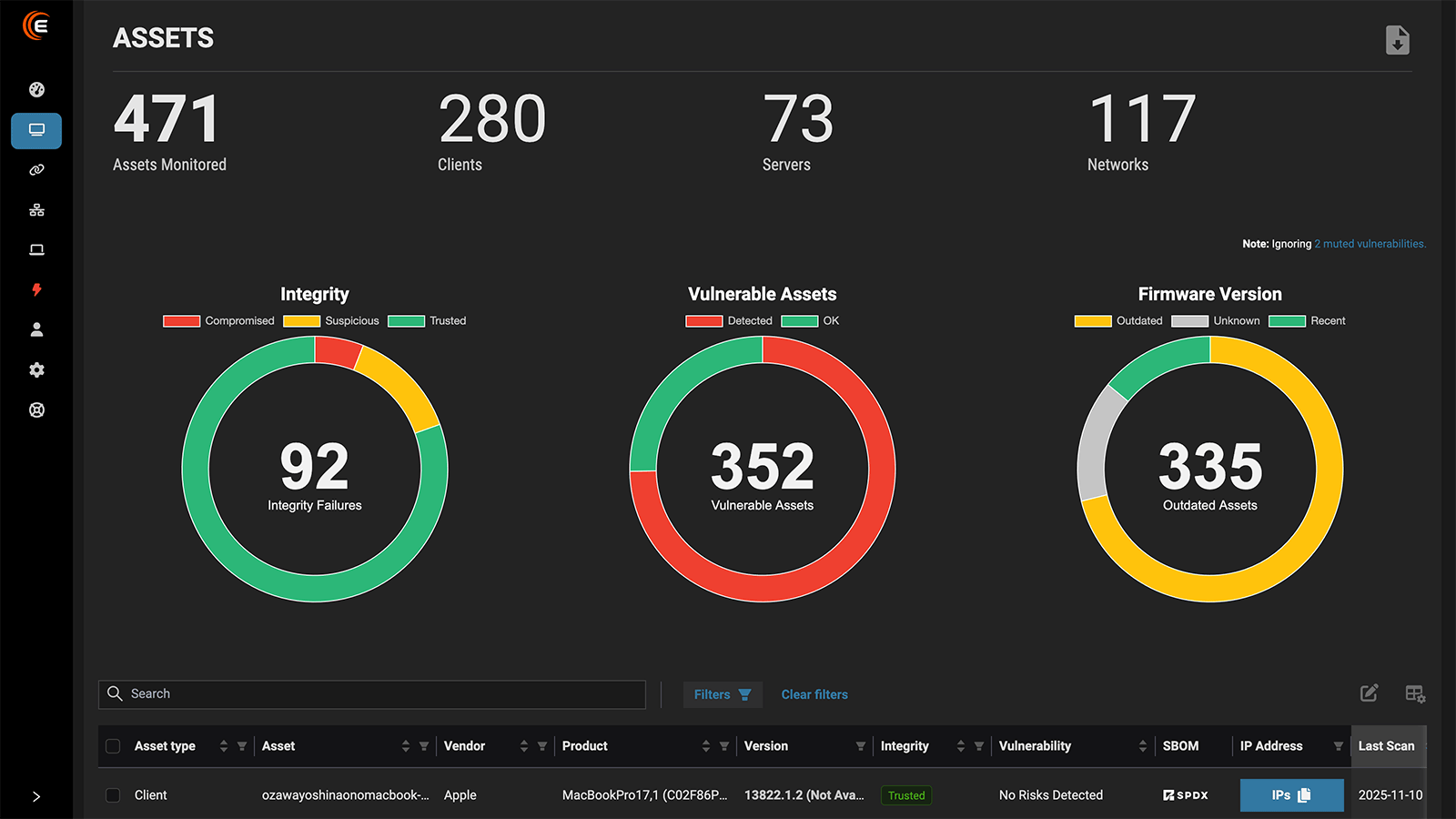
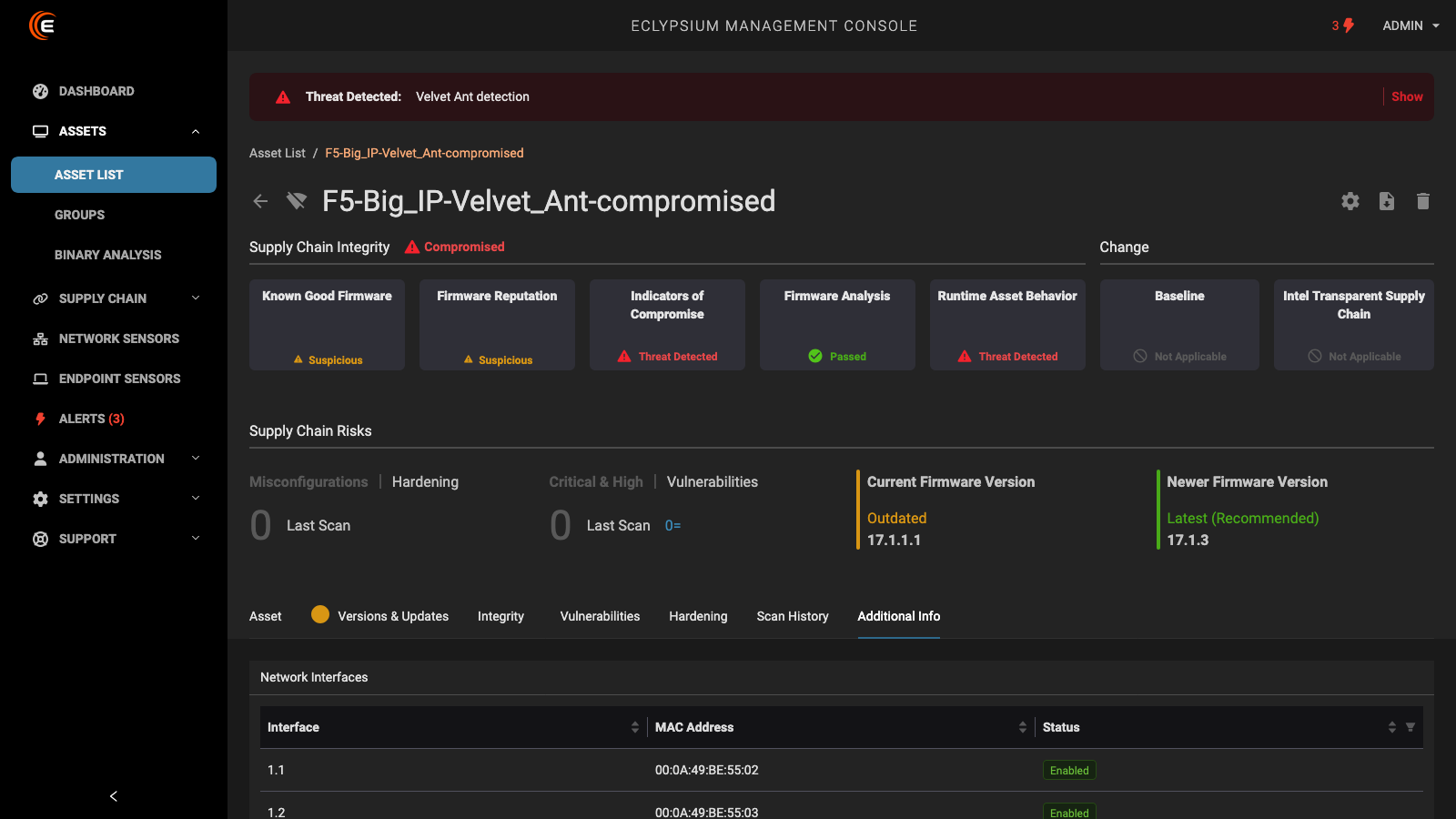
Unlike EDR and legacy vulnerability management tools, Eclypsium is the only platform that monitors firmware security and integrity continuously using a unique database over 12 million known-good hashes. Eclypsium covers every major vendor, and we’re always adding more, providing a single SaaS solution to identify risk and protect enterprise IT infrastructure against stealthy firmware attacks. Recent firmware attacks Eclypsium can detect and mitigate include HybridPetya, BMC&C (CVE-2025-54085), and BlackLotus.
Firmware Vulnerability Management
Continuously monitor firmware for known and unknown vulnerabilities
Active Threat Detection
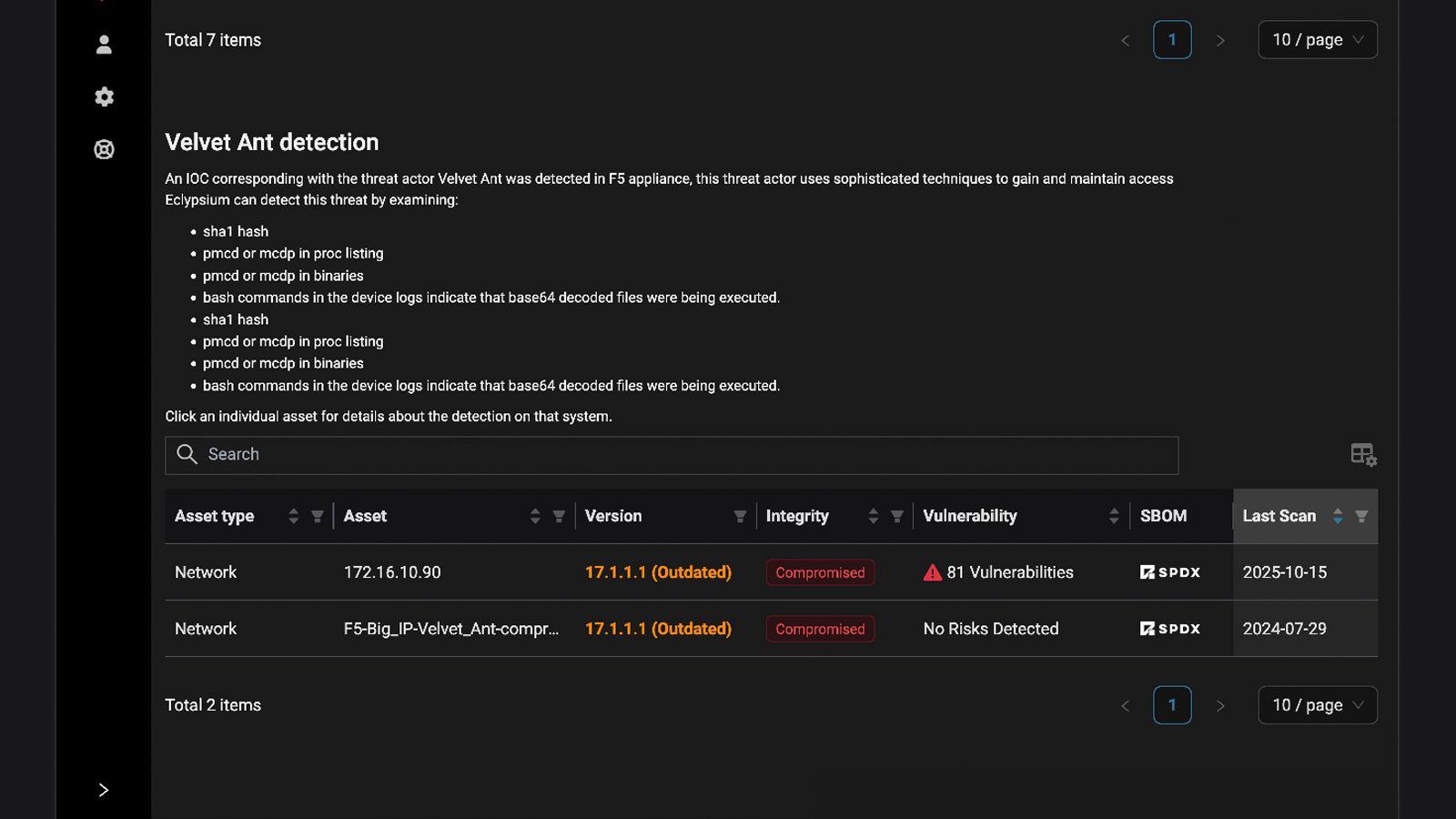
Detect bootkits, implants, and indicators of compromise targeting firmware in endpoints, servers, and network devices.
Integrity Monitoring and Automated Patching
Monitor the integrity of firmware continuously, so you know when anything changes. Automatically update firmware to stay secure.
Stop Stealthy Ransomware
Like HybridPetya that evades detection by EDR agents by hiding below the operating system and hijacking the boot process.
Why Attackers Target Firmware
Compromising firmware offers numerous benefits for attackers trying to remain hidden, or seeking to do as much damage as possible to demand high ransoms. Firmware is everywhere, from endpoints to servers, and even in network routers and switches, offering a hidden, powerful attack surface, no matter the attacker’s motive.
Persistence Past Reboot
An attacker with firmware level access can maintain access even if the device is rebooted, reimaged, or has the entire operating system reinstalled.
This persistence enables long term espionage, as well as repeated ransomware attacks stemming from a single initial infection.
EDR Evasion
Firmware level attacks enable the adversary to turn off EDR agents, or simply operate in areas EDR can’t see.
Firmware compromise also allows adversaries to evade SecureBoot, UEFI, and other boot-level security features to avoid being detected and removed.
Damage Force Multiplier
An attacker with firmware access can permanently brick the target device.
Firmware compromise on some components, like BMCs, allows attackers to cause physical damage by manipulating voltage levels within the device, potentially melting components or causing a fire in the data center.
Want To Learn About the Top 5 Firmware and Hardware Attack Vectors? Get Our eBook.
Why Firmware Attacks Are Hard to Defend Against
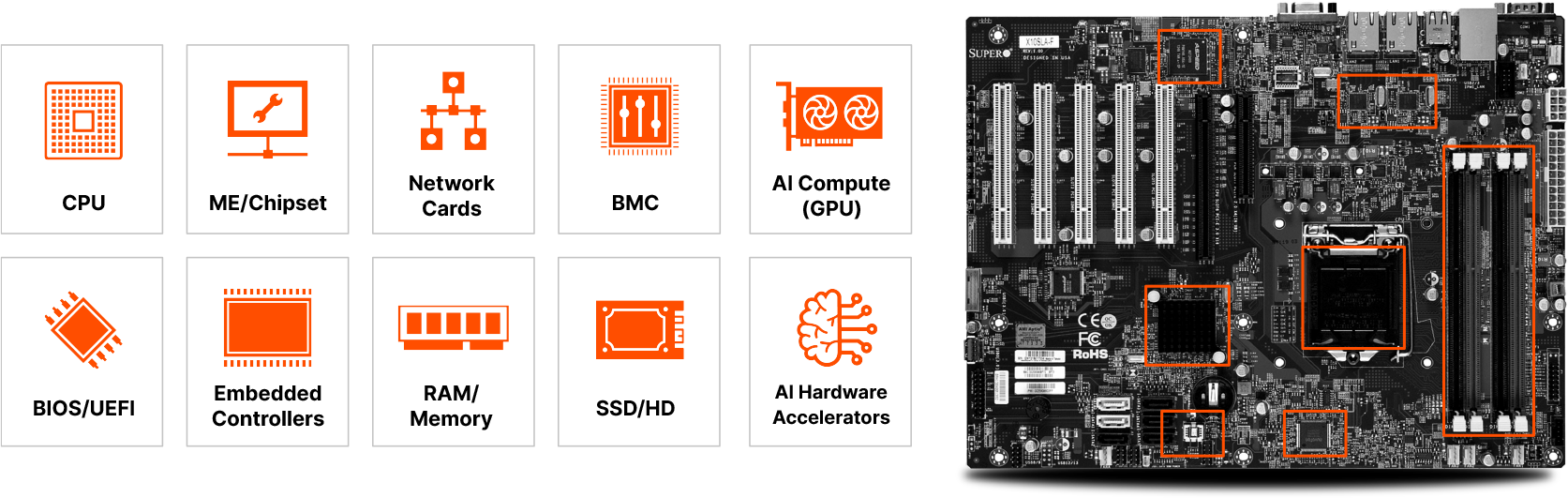
Firmware is everywhere. Firmware exists on numerous chips and components in every computing device, from laptops to servers to VPNS, network switches, routers, and firewalls. The ubiquity of firmware, and challenges in monitoring it, make it a perfect hiding place for adversaries.
Supply Chain Opacity
Firmware is produced by vendors several layers deep in the IT supply chain, making it challenging to track provenance and validate that the firmware is current and secure.
Monitoring Gaps
EDR and vulnerability management tools don’t look closely enough at firmware to detect misconfigurations, unknown vulnerabilities, or indicators of compromise.
Eclypsium analyzes firmware in your environment deeply so you see every risk.
Lagging Patches
Firmware patches are slow to be released, and even slower to be deployed in enterprises. As attackers accelerate their targeting of newly disclosed vulnerabilities, firmware is more exposed than ever.
How Eclypsium Stops Firmware Attacks_
Identify and Inventory
You get a complete inventory of devices in your environment and the firmware versions they’re running, and whether they’re current and secure or outdated and misconfigured. Don’t trust the supply chain to deliver secure firmware. Validate it yourself before deployment, during operations, and even when you decommission your devices.
Verify and Validate
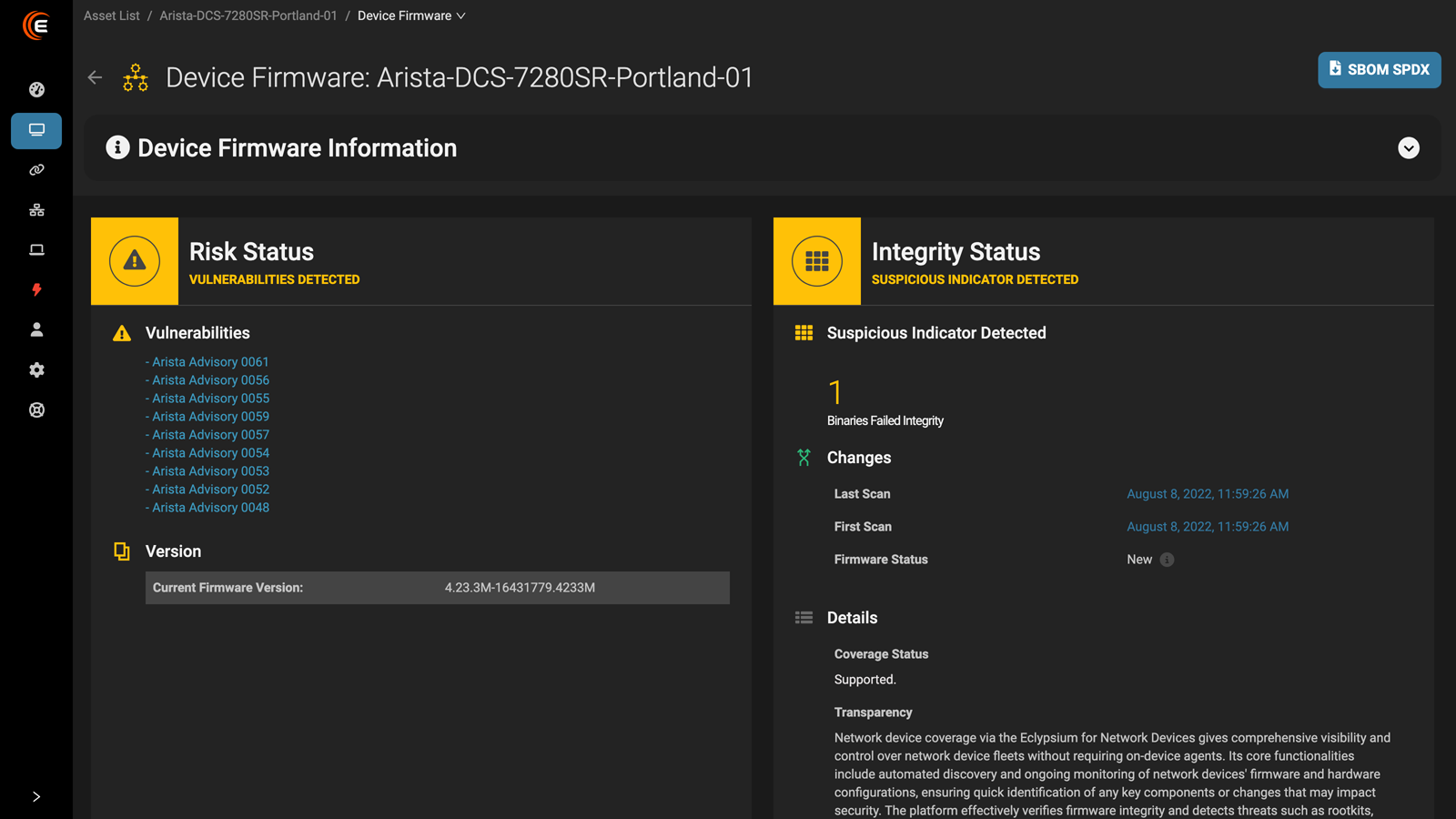
You get confirmation that your devices haven’t been compromised or tampered with, and are free of implants and backdoors.
Fortify and Harden
Assess device-level configuration and compliance. Keep devices secure and extend their lifespan by remotely patching or updating out-of-date or vulnerable infrastructure code.
Detect Known and Unknown Threats
Catch malicious implants and backdoors, attacker indicators of compromise, and unpatched vulnerabilities for a comprehensive view of risk in your IT infrastructure.