UPDATE: CISA has issued an emergency directive about an active attack against CISCO ASA devices.
A massive surge in scans targeting Cisco Adaptive Security Appliance (ASA) devices was observed by GreyNoise in late August 2025, with over 25,000 unique IPs probing ASA login portals in a single burst. This anomalous activity is highly suggestive of coordinated reconnaissance ahead of potential new vulnerability disclosures and/or pending End-of-Life (EOL) for the ASA platform. This article examines the details behind this scanning campaign, including evolving attacker tactics, the current state of Cisco ASA lifecycle support, and how Eclypsium can empower network defenders through specialized device security features.
According to the report, the first observed event involved more than 25,000 IP addresses targeting the ASA web login path, a sharp deviation from the usual baseline of fewer than 500 per day. A second, more minor wave followed days later. Detailed fingerprinting showed that over 80% of the August 26th activity—about 14,000 out of 17,000 IPs—was driven by a single botnet cluster based in Brazil. Both waves showed overlapping Chrome-like user agents, indicating a common scanning toolkit, and focused on Cisco logon pages as well as Telnet/SSH – a clear indication of a targeted Cisco campaign rather than opportunistic probing.
GreyNoise, once you’ve created an account, allows you to access reports, such as the Cisco ASA Scanner, which tracks IPs scanning Cisco ASA devices. As it turns out, August 25, 2025, was not the only date we can observe these scans:
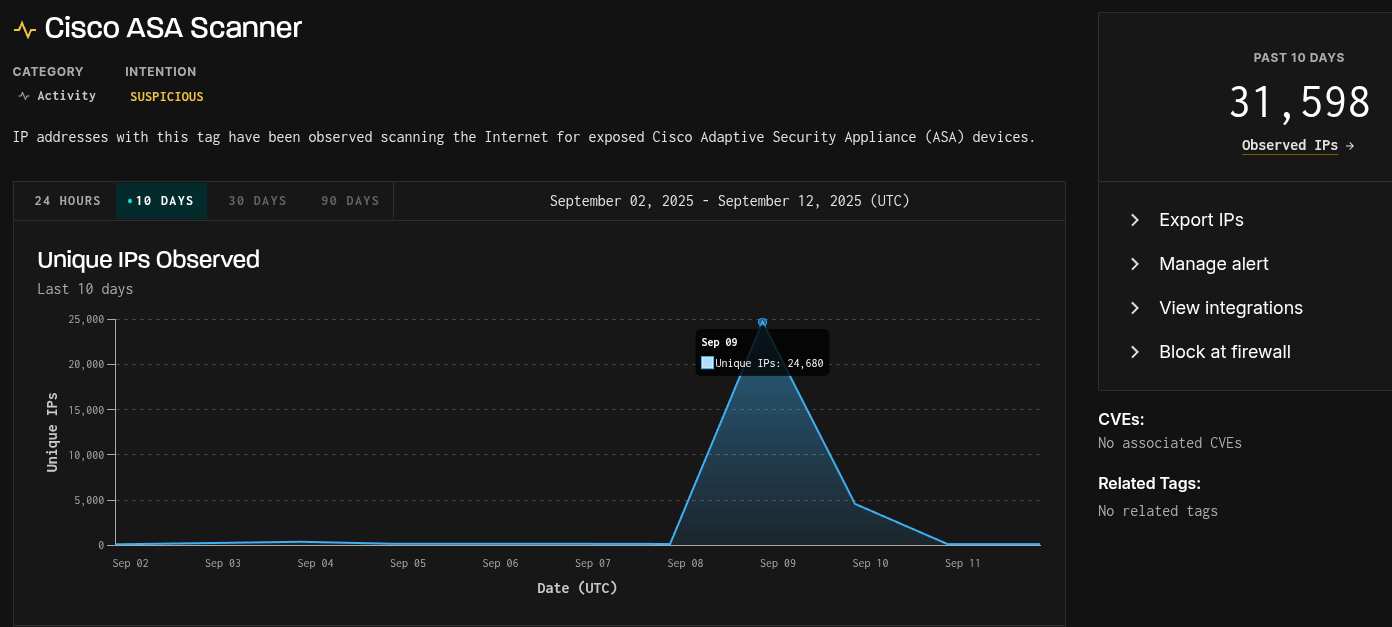
Again, on September 9, 2025, we see approximately 25,000 IPs scanning for Cisco ASA devices. Digging a bit deeper, the majority of the IP addresses from the September 9th spike are also associated with the botnet from Brazil. This is a regular scanning activity for a group of threat actors.
Existing Cisco ASA Vulnerability & Attack Landscape
While there may be a 0-day vulnerability and associated exploit in the wild that we do not know about (yet), Cisco ASA devices have been plagued by a long list of vulnerabilities. Many of which have high CVSS scores or are known to have been exploited in the wild, including by ransomware groups and advanced persistent threats. Below is a detailed rundown highlighting notable vulnerabilities, high-severity issues (CVSS 7.5+), CISA KEV entries, and available public attack tools and exploits:
- CVE-2014-2120 (CVSS 6.1, CISA KEV): A decade-old WebVPN input validation flaw allowing cross-site scripting (XSS) attacks, with recent exploitation attempts still ongoing as of December 2024. Commonly used by threat actors in malware campaigns such as AndroxGh0st.
- CVE-2018-0296 (CVSS 7.5, CISA KEV): A vulnerability in the web management interface of ASA devices that allows attackers to cause a denial of service condition and, in some cases, retrieve sensitive information about the device without authentication. An exploit for this vulnerability has been published (use with caution, as the author notes this may cause a denial of service condition).
- CVE-2020-3452 (CVSS 7.5, CISA KEV): Path traversal flaw in web services for ASA and Firepower devices, allowing unauthenticated remote attackers to read sensitive files from the exposed web services file system. This “read-only” bug was heavily exploited via crafted HTTP requests, with multiple public proof-of-concept (PoC) exploit scripts available.
- CVE-2021-40117 (CVSS 8.6): Vulnerability in the SSL/TLS message handler in ASA software allowing remote, unauthenticated attackers to crash affected devices (denial of service) via specially crafted packets.
- CVE-2022-20829 (CVSS 9.1): Critical flaw affecting ASA and FTD (Firepower Threat Defense) software, potentially allowing attackers to execute code or disrupt operations by uploading malicious ADSM packages. Rapid 7 researcher Jacob Baines is credited with the discovery and released a tool called “TheWay” that allows you to create ADSM packages.
- CVE-2023-20269 (CVSS 9.1, CISA KEV): This credential brute-force bug in ASA and FTD SSL VPNs has been actively exploited by groups like Akira and LockBit ransomware, allowing attackers to gain unauthorized VPN access. No patch was initially available, but workarounds existed (e.g., disabling weak authentication and group policies).
- CVE-2024-20353 (CVSS 8.6, CISA KEV): Allows attackers to send crafted HTTP requests to ASA/FTD web servers to crash (reload) the device. It is actively exploited (via the ArcaneDoor campaign) and listed in the CISA Known Exploited Vulnerabilities (KEV) catalog.
- CVE-2024-20481 (CVSS 5.8, CISA KEV): A denial of service vulnerability in the Remote Access VPN (RAVPN) service, exploited in the wild to crash VPN services until the device is manually restarted. Also in the CISA KEV catalog.
Vulnerabilities Exploited in the Wild (CISA KEV & Ransomware)
Many of the vulnerabilities above (notably CVE-2020-3452, CVE-2023-20269, CVE-2024-20353, CVE-2024-20481, and CVE-2014-2120) are all known to be under active exploitation and are called out in CISA KEV advisories, underlining their risk for defenders. Multiple proof-of-concept scripts and exploit modules exist for high-profile ASA bugs, particularly for CVE-2020-3452 and various SSL VPN vulnerabilities. For example, automated brute-force tools leveraging the +CSCOE+ login page to extract group names and perform credential spraying have been spotted in the wild and described in public incident reports. These conditions have enabled ransomware actors (e.g., Akira, LockBit) to repeatedly leverage vulnerabilities to compromise ASA devices, demonstrating a notable real-world impact, lateral movement, and persistent abuse. Espionage campaigns like “ArcaneDoor” have also used zero-day exploits against ASA targets, leveraging them to install custom implants for persistent access and data exfiltration. Exploit code for XSS and information disclosure vulnerabilities (such as CVE-2014-2120 and CVE-2020-3452) circulates in open-source security communities and on platforms such as GitHub and Exploit-DB.
Cisco ASAs continue to be a prime target due to their widespread deployment at the edge and a history of slow patch adoption. Speaking of widespread deployment, just how large is the Cisco ASA attack surface? Below are the results of a Shodan query that spotted over 113,000 ASA devices exposed to the public Internet:
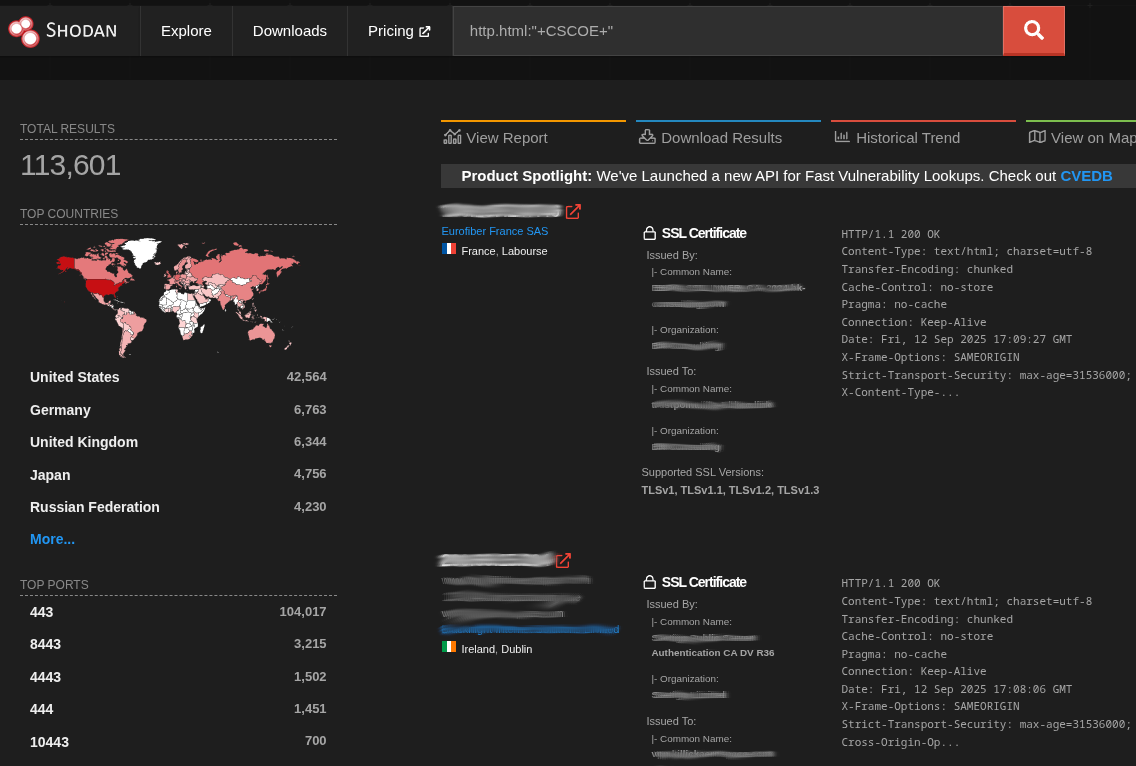
As many of the vulnerabilities listed above are cataloged in the CISA KEV and have reliable, publicly available exploit tools, if you have Cisco ASA systems deployed, they must be patched and hardened. Coupled with continued increased scanning and a plethora of targets on the Internet, the risks to organizations are dramatically amplified.
Attacker Tactics: Proactive Reconnaissance for 0-Days
Large-scale scanning surges like these are often early indicators of pending vulnerability disclosures—critical CVEs for the targeted technology have historically followed up to 80% of such cases. The intent is clear: map the attack surface and “tag” potentially exploitable devices before proof-of-concept exploits or 0-day vulnerabilities are public. Notably, this proactive enumeration also means that attackers can return for exploitation the moment new CVEs are released, regardless of the patch levels at the time of scanning. Recent high-profile incidents, such as the “ArcaneDoor” campaign, have highlighted how ransomware and espionage groups leverage ASA devices for initial access or persistent backdoors. Threat actors like Akira and LockBit have also been known to target these systems actively.
Cisco ASA: End of Life, Ongoing Exposure
Cisco has begun discontinuing sales and support for many ASA product lines, with final orders for several models and subscriptions scheduled to cease in 2023–2024. Customers with active service contracts will continue to receive some degree of technical support, but the sunset dates mean fewer patches or updates are forthcoming. This “end-of-support” status increases the appeal for attackers, as orphaned or unpatched devices become much more attractive targets for exploitation. This could be part of the motivations by threat actors: continually identify Cisco ASA devices in anticipation that new vulnerabilities will be discovered in devices for which there will be no patch. We explored the risks of EOL devices in the article: EOL Devices: Exploits Will Continue Until Security Improves.
How Eclypsium Protects Cisco ASA Devices
Eclypsium continuously monitors the integrity of Cisco ASA devices and many other network appliances to detect integrity failures, vulnerabilities, and indicators of compromise:
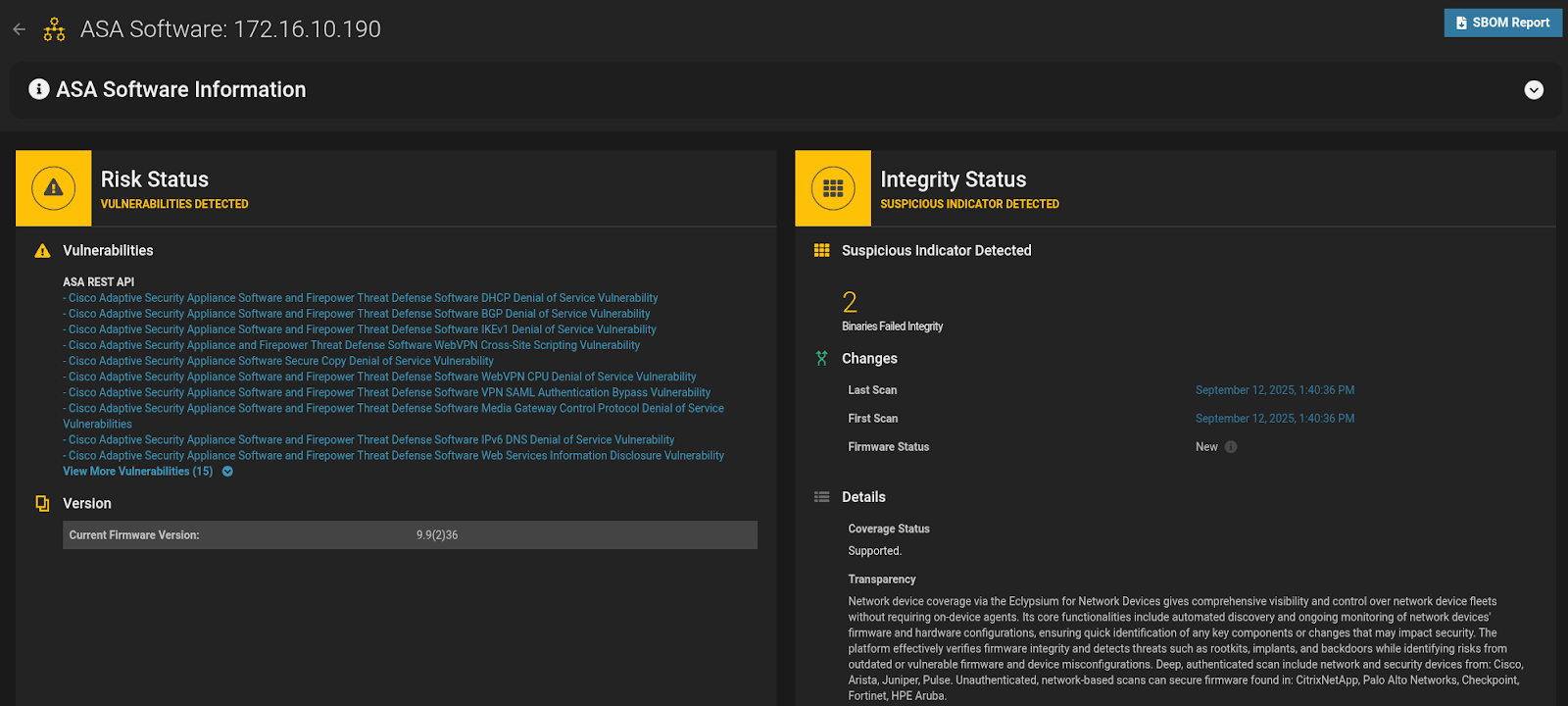
- Firmware Integrity Monitoring: Eclypsium continuously verifies the integrity of Cisco ASA firmware, detecting unauthorized changes, rootkits, implants, and other threats—even in devices where agents cannot be installed or support has ended.
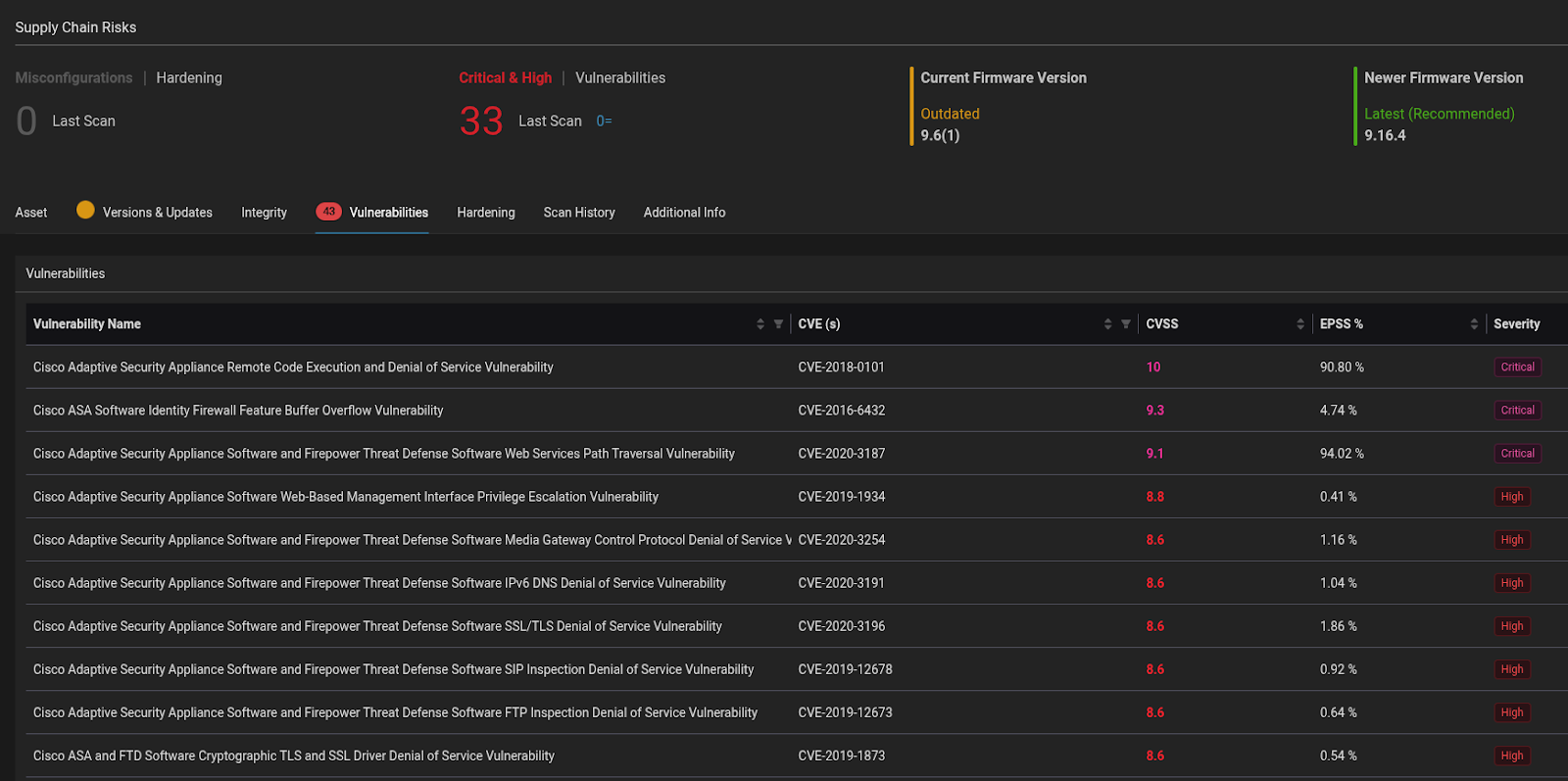
- Authenticated Vulnerability Scanning: The platform automatically discovers devices, identifies firmware versions, and matches them against vulnerability databases, surfacing both known CVEs and insecure configurations. Eclypsium provides risk prioritization and update recommendations to guide remediation work.
- Threat Detection: Eclypsium monitors Cisco ASA devices for signs of compromise, including indicators of the “ArcaneDoor” campaign and other targeted threats, leveraging threat intelligence to spot both known and unknown threat behaviors. Continuous device baselining highlights unexpected changes or anomalous activity. For a complete write-up of the “ArcaneDoor” threat, see our article “Defending Against ArcaneDoor: How Eclypsium Protects Network Devices”.
- Automated Remediation and Response: Integration with SIEMs, SOAR platforms, and custom workflows enables dynamic alerting, policy enforcement, and automated incident response—reducing the mean time to detection and remediation for ASA-specific threats.
- Supporting Legacy and End-of-Life Devices: Even as Cisco support winds down, Eclypsium continues to monitor and protect end-of-life hardware, offering a lifeline for organizations that cannot immediately decommission or replace aging network appliances.
How to Defend Against Attacks on Cisco ASA Devices
- Immediately limit internet exposure of Cisco ASA web interfaces, Telnet, and SSH endpoints.
- Enable strong authentication methods such as MFA on remote management portals
- Adopt continuous firmware integrity monitoring, alongside vulnerability scanning and threat intelligence, to detect and mitigate exploits, even on unsupported or legacy appliances.
- Leverage proactive threat data to block, rate limit, or geofence suspicious reconnaissance activity targeting exposed assets.
The August scanning surge is a potent warning: attackers are investing in mapping the ASA threat landscape before the next critical 0-day drops. Eclypsium enables defenders to stay ahead, maintaining trust, compliance, and resilience for a platform facing both operational and end-of-life security challenges.
If you’d like to learn more about how we ensure the integrity of your network devices and end-of-life hardware, we’d love to provide you with a live demo.
Related Resources:






