Canadian telecommunications companies are the most recently disclosed victims of China’s Salt Typhoon advanced persistent threat (APT) group, as reported by Bleeping Computer and other outlets.
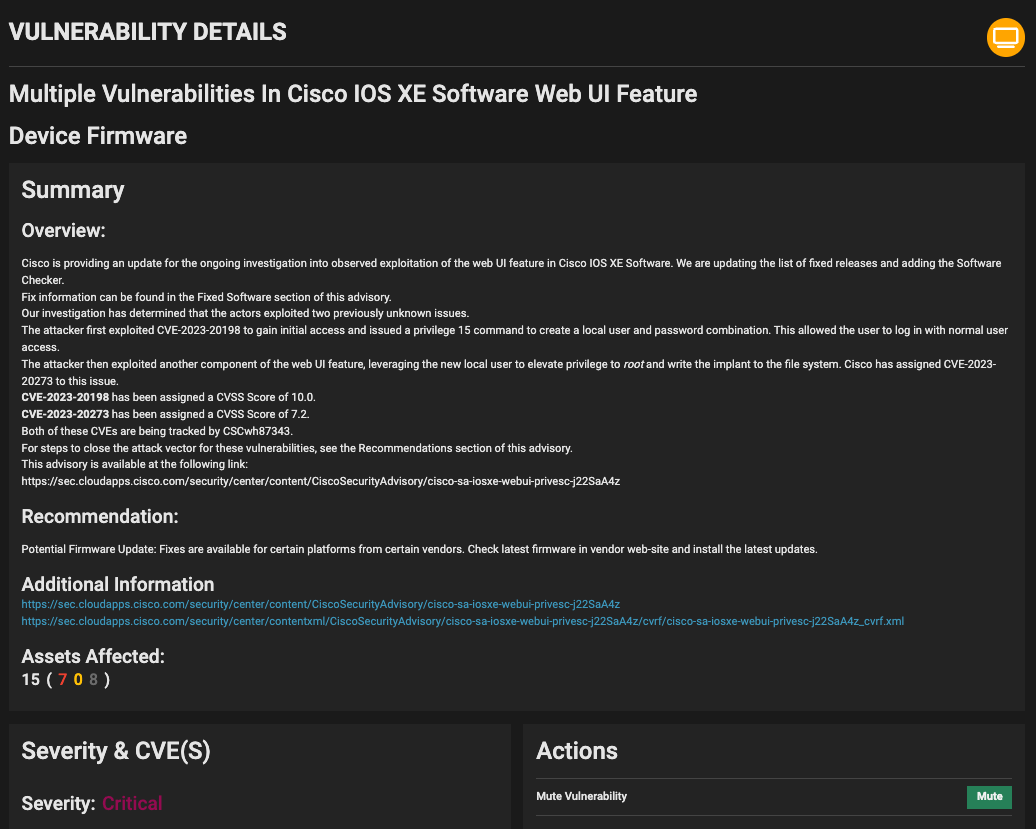
According to a report from Canada’s cybersecurity authorities, Salt Typhoon exploited CVE-2023-20198 to compromise a Canadian telecommunications company. The attack demonstrated textbook exploitation: threat actors used the vulnerability to create arbitrary accounts with administrative privileges, then configured Generic Routing Encapsulation (GRE) tunnels for persistent access and data collection.
This news follows quickly on the disclosure that Salt Typhoon breached global satellite communications company Viasat in February, marking a significant escalation beyond traditional terrestrial telecom targets. These breaches reveal a dangerous blind spot in how we secure the infrastructure that connects our world: the network appliances that form the backbone of global communications.
The attacks on Canadian telcos leveraged one of Salt Typhoon’s signature tools, CVE-2023-20198, a critical Cisco IOS XE vulnerability that was disclosed on October 16, 2023. Despite earning the maximum CVSS score of 10.0 and being actively exploited as a zero-day from the moment of discovery, this 18-month-old flaw continues to serve as a primary attack vector for sophisticated threat actors.
The persistence of CVE-2023-20198 in active attack campaigns, from traditional terrestrial telecoms to government-focused satellite providers, highlights a troubling reality: while endpoint security has evolved dramatically, network infrastructure remains a dangerous blind spot that organizations consistently fail to adequately protect. This blind spot is being targeted by numerous nation state APTs, as well as financially motivated private cyber threat actors.

Salt Typhoon Stays In The Headlines
Salt Typhoon has sporadically made headlines since late 2024, when a wave of disclosures revealed that worldwide telecommunications companies had been successfully breached by the threat actor. The most recent disclosure of Canadian telcos, and Viasat having been breached serve as a reminder that the threat is far from neutralized. Here’s a quick video Eclypsium produced in February when the last big wave of Salt Typhoon headlines hit:
These incidents are not isolated. Research from Recorded Future revealed that between December 2024 and January 2025, the Salt Typhoon group (also tracked as RedMike) attempted to exploit over 1,000 internet-facing Cisco network devices worldwide, primarily targeting telecommunications providers. The scope was truly global, with victims spanning from the United States to South Africa.
A Vulnerability That Refuses to Die
What makes CVE-2023-20198 particularly dangerous is its simplicity and effectiveness. The flaw allows unauthenticated remote attackers to create accounts with “level 15 access”, the highest level of administrative control on Cisco devices. As Tenable’s analysis noted, this gives attackers “full control over the router.”
The vulnerability’s continued exploitation is evidenced by current threat intelligence. GreyNoise researchers observed 110 malicious IP addresses actively targeting CVE-2023-20198, with attacks originating primarily from Bulgaria, Brazil, and Singapore. This isn’t just nation-state activity, the broad geographic distribution suggests multiple threat actors are leveraging this flaw.
The Infrastructure Security Blind Spot
The persistence of CVE-2023-20198 exploits points to a fundamental problem in how organizations approach cybersecurity. While enterprises deploy sophisticated endpoint detection and response tools, behavioral analytics, and zero-trust architectures for user devices, network infrastructure often remains an afterthought.
Recent analysis shows that edge devices ”typically lack security monitoring and detection solutions, such as endpoint detection and response (EDR) agents.” Unlike endpoints, these devices typically lack antimalware capabilities, endpoint detection and response agents, or detailed logging that security teams can monitor through SIEM platforms.
After investigating a different attack targeting Juniper enterprise routers, Mandiant concluded that: “The compromise of routing devices is a recent trend in the tactics of espionage-motivated adversaries as it grants the capability for a long-term, high-level access to the crucial routing infrastructure, with a potential for more disruptive actions in the future. A concerted effort is required to safeguard these critical systems and ensure the continued stability and security of the internet.”
Threat actors are clearly taking notice of this unprotected attack surface. The 2025 Verizon Data Breach Investigation Report noted an 8x increase in exploitation of vulnerabilities on network and edge devices. Exploitation overall saw a sharp increase, nearly catching up with credential abuse as an initial access vector.
This creates a perfect storm: critical infrastructure devices with significant network privileges, limited visibility for defenders, and a patching cadence that lags far behind endpoint systems.
The Cascading Effects of Unpatched Edge Devices
When threat actors compromise network infrastructure using vulnerabilities like CVE-2023-20198, the consequences extend far beyond a single device. The Salt Typhoon campaign demonstrates these cascading effects:
- Persistent Access: By creating GRE tunnels and administrative accounts, attackers establish long-term presence that survives most incident response efforts. Cisco Talos researchers found evidence of threat actors maintaining access “for over three years” in some environments.
- Lateral Movement Platform: Compromised network devices provide an ideal pivot point for accessing other systems. With administrative control over routing and switching infrastructure, attackers can monitor traffic, redirect communications, and access network segments that would otherwise be protected.
- Intelligence Collection: In the telecommunications sector, network device compromise enables massive intelligence collection. Salt Typhoon’s access may have allowed them to monitor U.S. law enforcement wiretapping platforms and intercept communications from political figures.
How To Mitigate Network Edge Vulnerabilities
The solution requires fundamentally rethinking network infrastructure security. Organizations must apply the same security rigor to network devices that they’ve developed for endpoint systems:
- Continuous Monitoring: Implement firmware-level monitoring that can detect persistent implants and backdoors that traditional security tools miss.
- Validate Network Device Integrity: Rather than trusting network devices to be secure by default, implement monitoring and verification systems that can detect anomalous behavior.
- Patch Management Automation: Include network infrastructure in enterprise patch management programs with the same prioritization and urgency applied to endpoint systems.
How Eclypsium Can Help
Eclypsium has written extensively about our ability to detect CVE-2023-20198 as well as other CVEs associated with Salt Typhoon, as well as Volt Typhoon, Flax Typhoon, Silk Typhoon, and other Chinese APT groups.
Eclypsium also offers a free assessment specifically on the risks associated with Salt Typhoon, to discern whether your environment may be a good candidate for one-time or ongoing scanning to detect and mitigate Salt Typhoon tactics. Request a Salt Typhoon assessment here.
The CVE-2023-20198 story isn’t just about a single vulnerability, it’s a wake-up call about a systemic blind spot in enterprise security. As threat actors like Salt Typhoon continue to demonstrate the intelligence value of network infrastructure compromise, organizations can no longer afford to treat these devices as secure black boxes.
The fix for CVE-2023-20198 has been available since October 2023. The fact that it continues to enable successful attacks 18 months later speaks to a broader challenge that requires immediate attention: bringing network infrastructure security into the modern era.
For a deep dive into securing network edge devices from the firmware up, check out our recent webinar: Protecting the Exposed Network Edge from APTs, Zero Days, and Ransomware.
Organizations can find Cisco’s patches and mitigation guidance in their security advisory for CVE-2023-20198. For those unable to patch immediately, Cisco recommends disabling the HTTP Server feature on internet-facing systems.






