Survey of AFCEA Attendees Shows Government Shutdown Has Major Impact on Cybersecurity Readiness

The results are in from the Eclypsium survey of over 100 government employees and affiliated entities about cybersecurity risk to the U.S. Federal government and Department of Defense. This survey was conducted during last week’s AFCEA TechNet Indo-Pacific event in Honolulu, HI, where agencies, industry, academia and military services personnel gather to focus on regional defense issues, and discusses defense policies and challenges and their relevance to both industry and government through the lens of the region that stretches from the African east coast to the U.S. west coast. The numbers highlight a concerning gap between awareness and actual preparedness to defend against the most urgent cyber threats, including network edge cyberattacks, cyber supply chain risk, and a shifting regulatory landscape facing the federal government.
Government Shutdowns: The Hidden Multiplier
Perhaps the most sobering finding from our survey was the overwhelming consensus about government shutdowns. Fifty-two percent of respondents believe shutdowns have a “major impact” on DoD’s cybersecurity risk posture, with another 40% citing “some impact.”
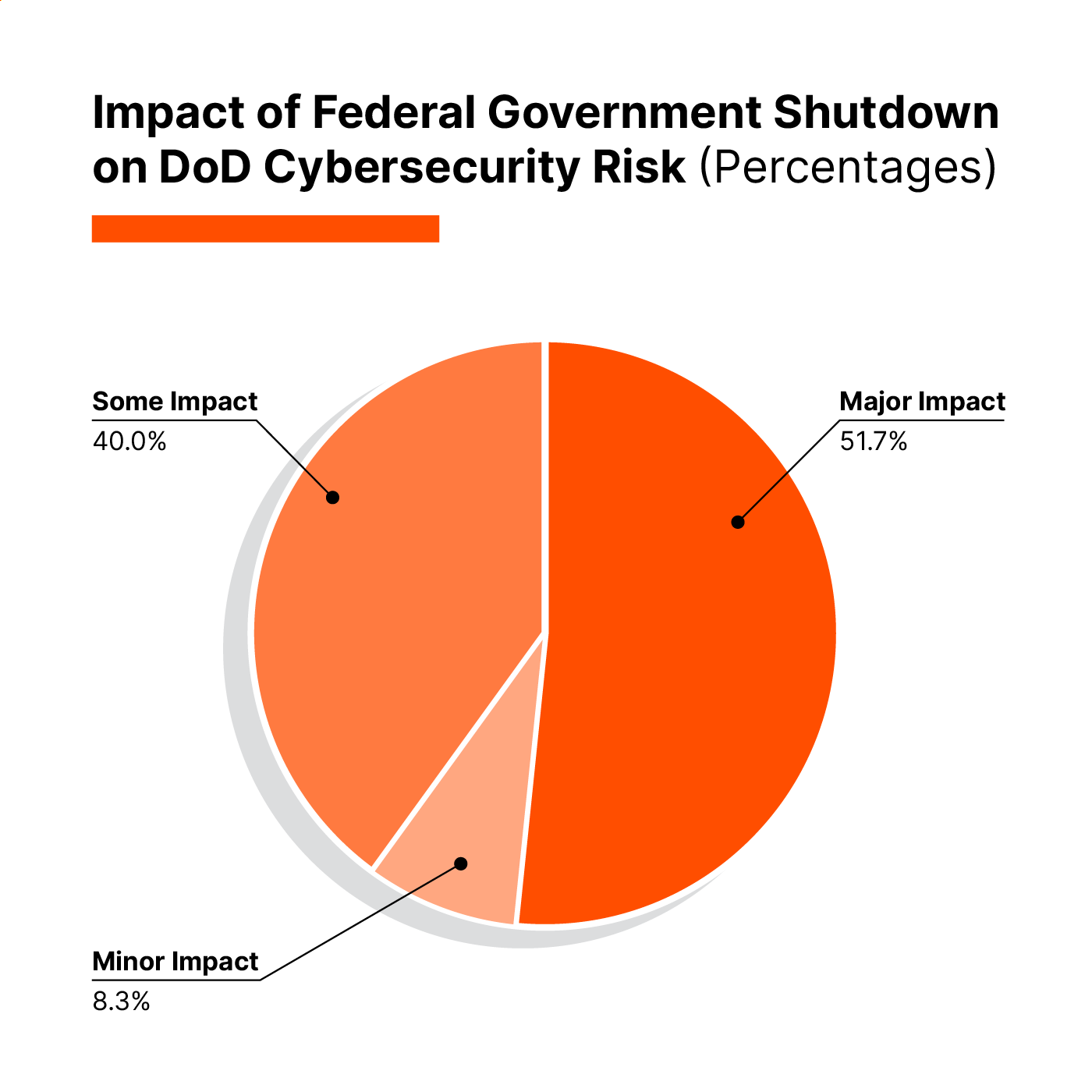
During shutdowns, security teams operate with skeleton crews. Routine patching gets delayed. Threat hunting stops. Vendor support contracts may lapse. The 32-day median remediation time for network vulnerabilities likely extends even further, creating windows of opportunity measured in months rather than weeks.
Consider what happens when a critical vulnerability emerges during a shutdown. Security teams may face difficulty procuring emergency patches. They may not be able to bring in needed specialized expertise, and often can’t even maintain normal monitoring operations. The CISA website itself currently features a caveat stating that it will not be actively managed due to the lapse in federal funding.
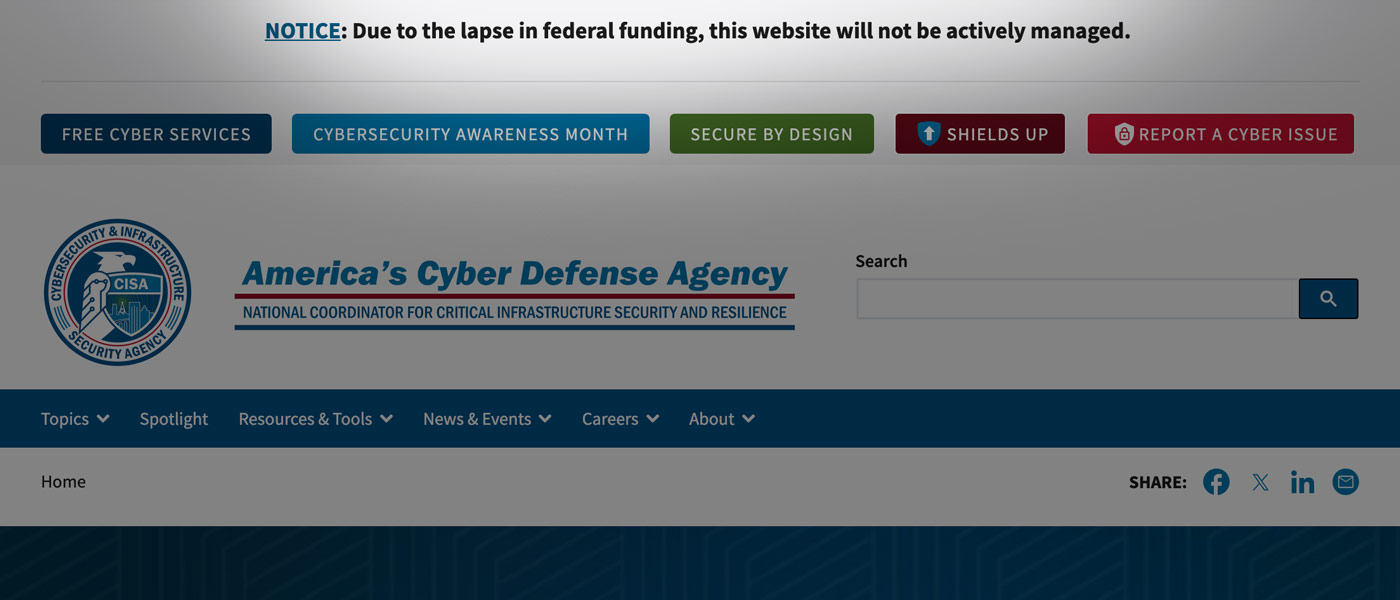
The infrastructure concerns highlighted throughout the survey responses become radically more dangerous when defensive capabilities are degraded.
Network Infrastructure: Where Awareness Meets Reality
The survey first asked which area of IT infrastructure and devices the respondents thought were most vulnerable to stealthy attackers.
The top response, at 35% of respondents, was a concern over network infrastructure. Routers, switches, firewalls, VPNs—represents a massive and growing attack surface. These concerns align directly with findings from the 2025 Verizon Data Breach Investigation Report, which documented an almost 8x increase in network edge device exploitation from 2024-2025.
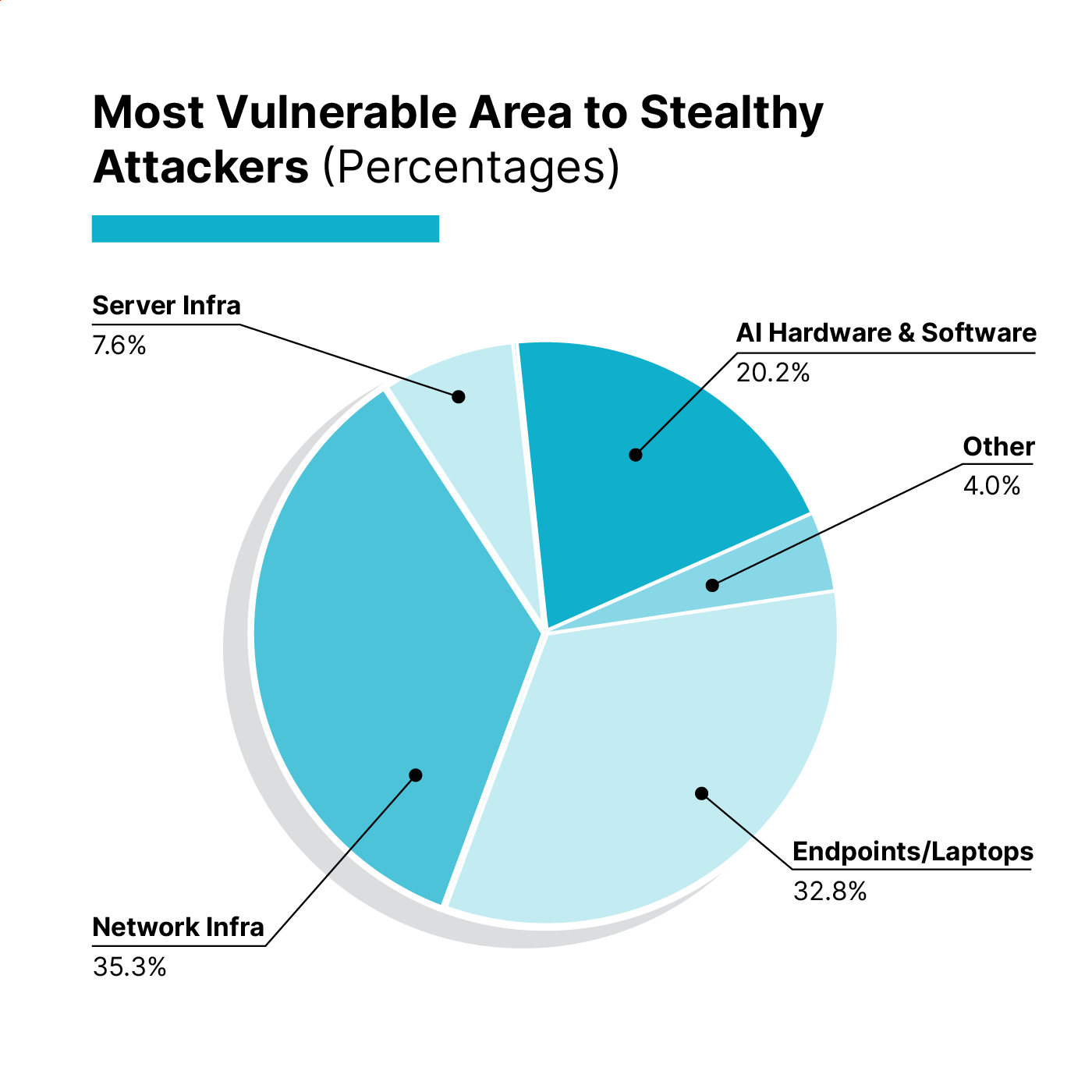
But here’s where the gap emerges: awareness doesn’t equal preparedness. Despite recognizing the vulnerability, 55% of survey respondents reported being only “somewhat confident” in their supply chain security programs to defend against nation-state threats. Another 18% of respondents admitted they’re not prepared at all to meet DoD supply chain security requirements, with 16% more unsure of their status.
This uncertainty has real consequences. The Verizon DBIR found that only 54% of network device vulnerabilities were fully remediated, with a median remediation time of 32 days. For military and government networks, 32 days of exposure represents countless opportunities for adversaries to establish persistence, exfiltrate data, or prepare for more destructive attacks.
In several recent cases of cyberattacks against network edge devices, CISA has issued Emergency Directives mandating that Federal agencies patch or mitigate vulnerabilities in a matter of weeks. Recent attacks against Cisco Adaptive Security Appliances, and a breach at F5, both led to CISA EDs with short remediation timelines.
The Supply Chain Blind Spot
The survey also revealed a critical capability gap in supply chain security. Almost half (47.5%) of respondents reported only being “somewhat prepared” for DoD supply chain mandates. Thirty-four respondents admitted they’re either not capable or unsure about their ability to gather and analyze Software, Hardware, and Firmware Bills of Materials (SBOM/HBOM/FBOM).
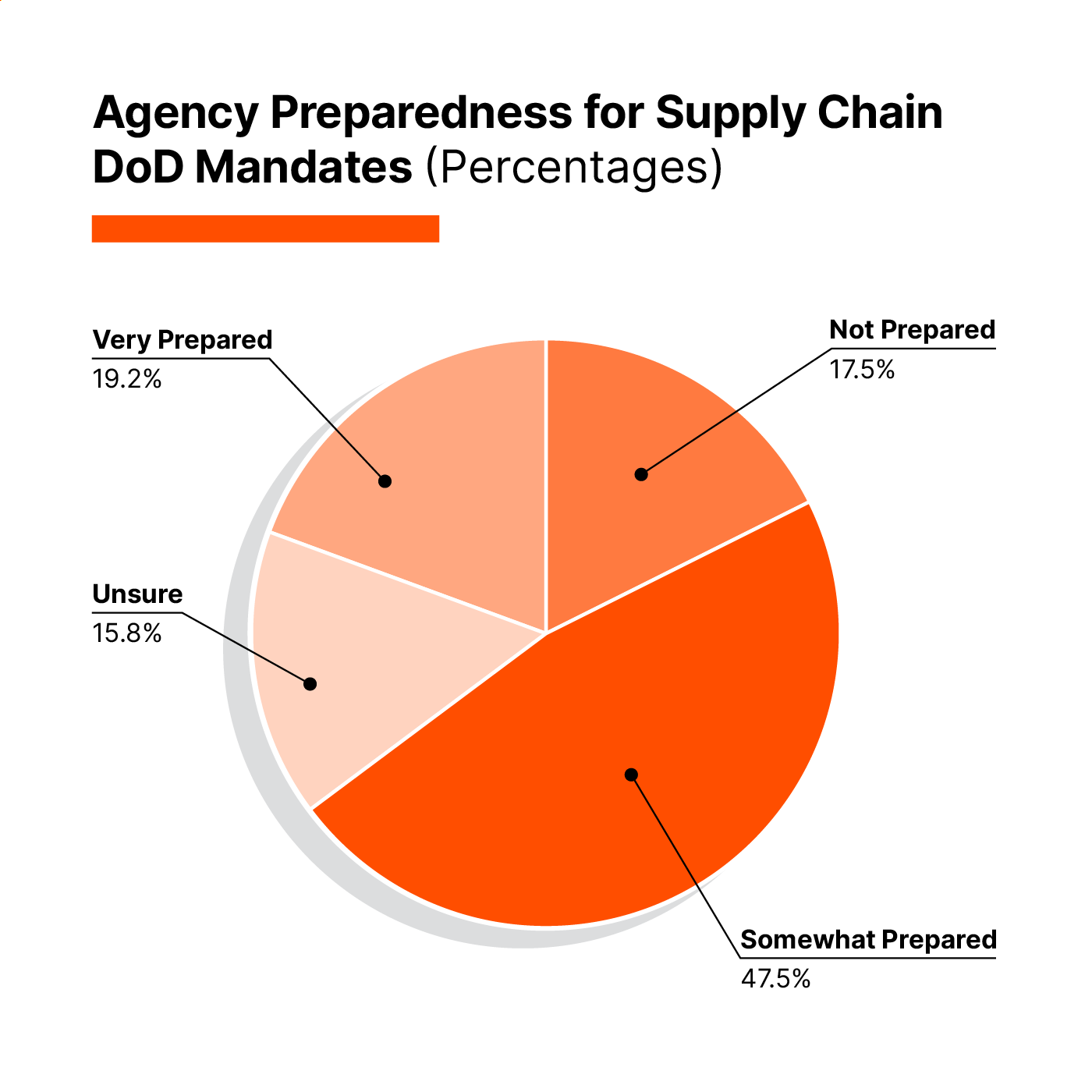
This limitation is particularly problematic given the Verizon DBIR’s finding that third party involvement in breaches doubled from 15% to 30%. Every network device contains components from dozens or hundreds of suppliers, and firmware from numerous providers. Without comprehensive visibility into these components, organizations are essentially trusting their security to the least secure element in their supply chain.
The challenge compounds when you consider that many of these devices sit at the network edge, directly exposed to the internet. They’re the first line of defense, yet they often have the least visibility and the weakest security controls. It’s like posting guards at the gate but never checking if they’re actually awake.
Another survey question gauged awareness around advanced cyber adversary tactics like Living off the Land, specifically associated with advanced threat actors like Salt Typhoon and Volt Typhoon, known to target federal agencies. 45% of respondents reported being somewhat familiar with living off the land risk, and 15% reported no familiarity. Living off the land techniques are often used by the same adversary groups that prioritize targeting network edge devices. The lack of monitoring on these devices, combined with their broad connectivity and access inside the target network, makes them an optimal beachhead for attackers prioritizing stealth and persistence. An APT campaign targeting Juniper routers earlier this year prompted Mandiant to write that:
“The compromise of routing devices is a recent trend in the tactics of espionage-motivated adversaries as it grants the capability for a long-term, high-level access to the crucial routing infrastructure, with a potential for more disruptive actions in the future. A concerted effort is required to safeguard these critical systems and ensure the continued stability and security of the internet.”
The Path Forward
The readiness gap identified in the survey isn’t permanent, but closing it requires honest assessment and systematic improvement. Organizations that recognize network infrastructure as their most vulnerable attack surface are already ahead of those still focused solely on endpoints. Those expressing concern about supply chain security are better positioned than those who haven’t considered the risk.
But recognition alone won’t stop sophisticated adversaries. The same network devices that 35% of survey respondents identified as most vulnerable are the ones seeing explosive growth in exploitation. The supply chain risks that leave 55% of respondents only “somewhat confident” are the same ones adversaries are actively targeting.
At Eclypsium, we see this gap every day in our work with government and commercial organizations. The good news is that comprehensive infrastructure security is achievable. It requires the right technology, processes, and commitment to continuous improvement. Most importantly, it requires moving beyond “somewhat prepared” to fully ready.
The community understands the challenge. Now it’s time to ensure our defensive capabilities match our awareness. We have the technology. But it will require active prioritization of cybersecurity awareness and capability gaps to stay ahead of rapidly advancing adversaries.





