Attackers Use What Works
Something that has caught my attention lately, both in the news and from recent leaks of threat actor groups, is that attackers continue to use what works. The technique could be something elaborate or straightforward. It doesn’t matter to the attackers as long as it works. This is not to say that malicious actors will not put in the work to make something work, then sell or share it. The attack tools and techniques, targeting network devices and IoT specifically, can range from the latest 0-day exploits to those that are 15 years or older.

Often, attackers are targeting IT infrastructure in what I call “the dusty corners”. When I first started consulting many years ago, a friend provided me with valuable guidance. He told me that every organization has dusty corners in IT – those systems, networks, and devices that lie dormant, don’t receive a lot of attention, but could cause a bad day in the future. The advice? Help customers with the dusty corners first, and that will earn trust and lead to more work. Security aside, if you’ve worked in IT, you can more than likely think of several examples of dusty corners (And how nice it would be for someone to clean those up for you?). Typically, the dusty corners contain older network gear and devices that are EOL (End-Of-Life), legacy Windows systems running proprietary software that cannot be upgraded, or applications that have not yet been retired and are missing security patches. The reason for the dust? No one is paying attention to these areas. We sweep and clean the main areas in a house or building, but often overlook the cobwebs behind the furniture. We do the same thing in IT. Some areas lack visibility because we either lack the means to see the problems, simply don’t want to acknowledge our own issues, or the system(s) are scheduled for decommissioning.
Attackers are taking the opposite approach. They focus on the dusty corners precisely because they know IT teams have low visibility and are not focusing detection efforts in these areas. Let’s take a look at a few recent examples, more on a macro level, these examples represent an attacker going after the dusty corners on the Internet at large:
Shadowserver Foundation: Surge in Scans
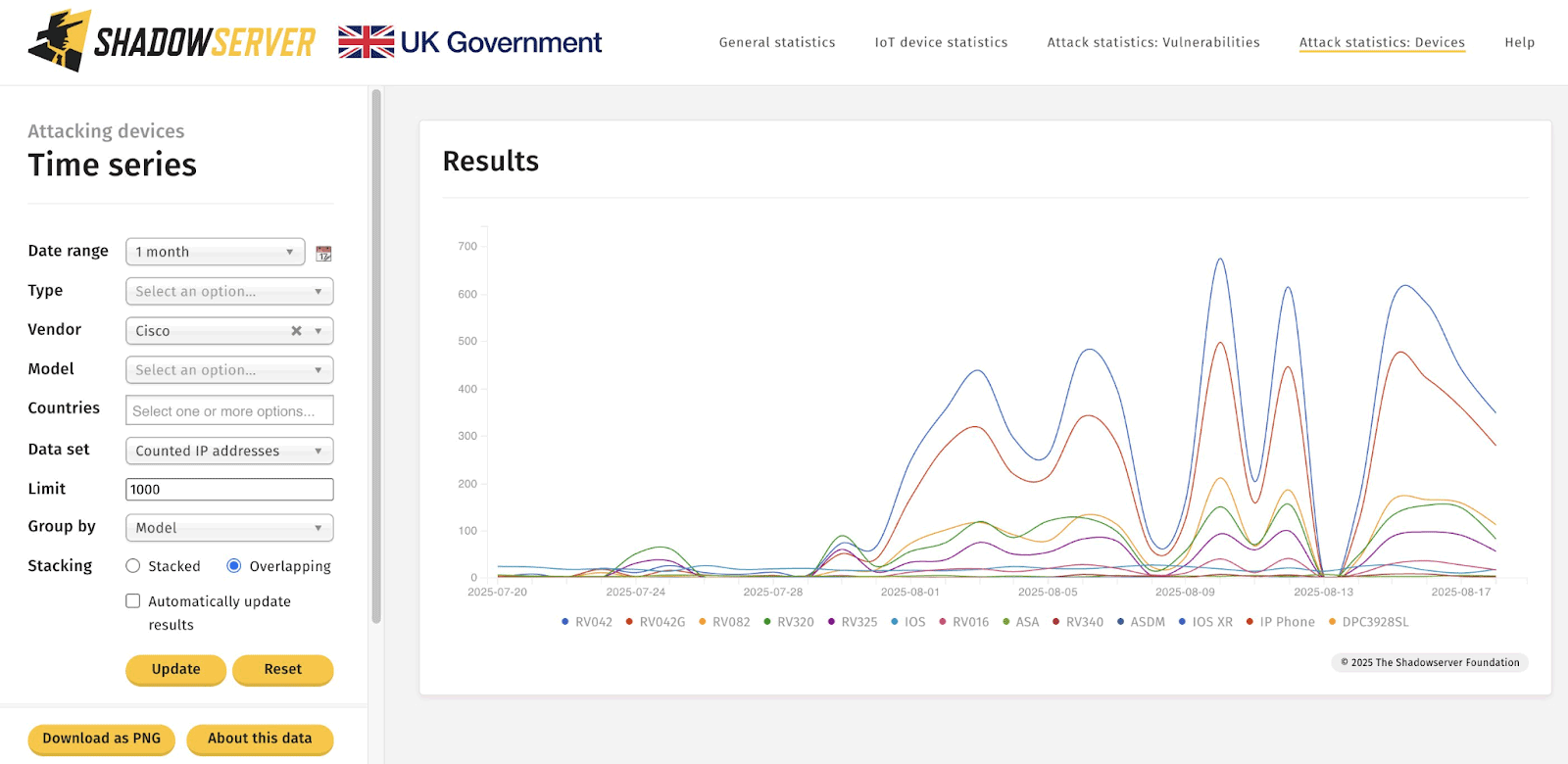
Uptick in scans from select IoT devices. (Credit: Shadowserver Foundation)
A recent surge in malicious scanning has been traced back to compromised Cisco, Linksys, and Araknis routers, affecting both consumer and enterprise equipment. The Shadowserver Foundation reports that this distributed campaign leverages infected devices to conduct reconnaissance scans across the internet, exploiting unpatched firmware vulnerabilities. (Reference). Specifically, attackers are targeting:
- Cisco Small Business RV series routers – Most models are EOL and do not receive support, including firmware updates, from Cisco.
- Linksys LRT series – These models have reached EOL and may receive some extended support from Linksys.
- Araknis Networks (AN-300-RT-4L2W) – This product is EOL, and firmware updates are no longer distributed for this model.
The 7-Year-Old Bug and Russian Threat Actors
Next up, we have a different campaign that also targets EOL devices:
“The FBI and security researchers today warned that Russian government spies exploited a seven-year-old bug in end-of-life Cisco networking devices to snoop around in American critical infrastructure networks and collect information on industrial systems.”
Take these 3 points from the article:
- “targeting outdated networking gear that accepts legacy, unencrypted protocols like Cisco Smart Install (SMI) and Simple Network Management Protocol (SNMP).” – This is the perfect opportunity for attackers, as they are targeting the combination of:
- A management protocol that is accessed over the network, allowing exploitation to happen remotely
- Vulnerabilities in the networking protocols (SNMP and SMI) that provide command execution
- The items listed above are present on a system that is legacy, or EOL, and will not receive firmware updates.
- “They’ve also deployed custom malware for some Cisco devices, such as 2015’s SYNful Knock router implant.” – Similar to J-Magic, this backdoor uses port knocking techniques to help evade detection and provides a stealthy backdoor for attackers. It was initially discovered in the wild by Mandiant in 2015, and it is still in use today.
- “There’s a super-old critical bug in the Cisco Smart Install feature of Cisco IOS and IOS XE software, tracked as CVE-2018-0171, which the networking giant fixed in March 2018.” – A PoC for this vulnerability was posted on GitHub 2 years ago, and even though it is 7 years old, attackers are still using it successfully. Not only is it being used by Russian threat actors, but we’ve also observed it being exploited in the Salt Typhoon attacks.
Losing The Device Security Battle
Breaking down some of the recent reports of threat actor behavior explains why we are losing the battle. This will continue, as we never got around to addressing the issue of legacy network gear being left on the Internet. Attackers love this because:
- Defenders are not looking for compromised consumer routers: There is little visibility, detection, or prevention available for these routers. The existing detection methods (e.g., enterprise log monitoring via SIEMs or advanced forensics techniques) are primarily intended for larger companies, rather than individuals or small businesses. We lack an EDR-style solution on these platforms that provides visibility, allowing attackers to gain a foothold and persist for extended periods. There is no active user, keyboard, or mouse on an IoT device, so no one is there even to notice anything unusual.
- Many routers have reached EOL (End-Of-Life): The vulnerabilities in these devices will not be patched moving forward, creating a ripe target for attacks. Even if a patch is available, many do not apply them!
- Attackers can easily scan the Internet, as devices are now much more computationally capable than ever before; therefore, these scans run at a significantly faster rate. Once the botnet is created, scans come from thousands of different IP addresses, making it difficult to block.
Basic security practices significantly reduce this attack surface. For example:
- Disabling and replacing legacy, unencrypted protocols such as TELNET and SNMP (and for Cisco devices, SMI (Cisco Smart Install))
- Arming ourselves with detection and prevention for 10-year-old+ attacker techniques, primarily through monitoring logs, network traffic, and validating firmware signatures.
- Patching our systems regularly, especially for any of 2018’s vulnerabilities!
Conclusion
Vulnerabilities and attacker techniques are implemented on a timeline that can be random. Sometimes it’s 10 years after a Blackhat talk that we see in-the-wild usages. Here’s the mind bender: Mike Lynn broke open Cisco IOS hacking in 2005, implants were seen in the wild in 2015, and attackers are observed today using these techniques to implant routers. Don’t wait until something is actively being used to defend against it because it will be too late. Eclypsium’s supply chain security platform can help by:
- Anomaly detection: Monitoring device firmware for changes over time and detecting malicious software/firmware components
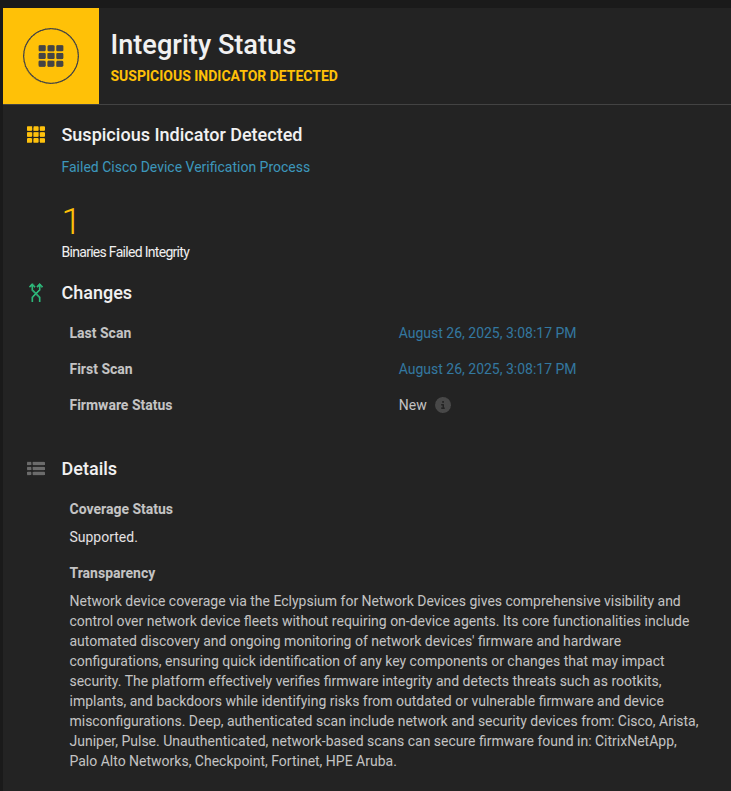
- Integrity checking: Comparing known good firmware with the firmware on the device.
- Vulnerability scanning: Through both authenticated and unauthenticated checks, detect the presence of vulnerabilities on the device
Don’t let attackers dwell in the dusty corners by incorporating all of these defensive techniques across all of your devices!






