The major F5 security incident disclosed on October 15 is still sending ripples (or tsunamis) through the enterprises and governments worldwide. While F5 has issued patches for 44 vulnerabilities that were leaked to attackers during the breach, major concerns still linger about undiscovered or undisclosed risks to F5’s customers.
At the request of our customers, including major financial organizations and telecommunications providers, Eclypsium has been conducting a deep security assessment of F5 devices and the firmware or embedded operating systems that underlie them.
Now that we know a nation state adversary has access to BIG-IP source code, and is likely conducting analysis of it at a deep level to discover vulnerabilities, it is paramount that enterprises with F5 in production conduct a thorough audit of their entire F5 footprint and implement compensating controls to offset the risk of zero days.
The questions arising in our research and our conversations with security leaders in major enterprises were echoed in the questions and tone of concern in F5’s recent earnings call. Based on these interactions, we see several key concerns emerging among global enterprises with F5 deployments:
- Has my organization been impacted by the F5 security incident?
- Can my F5 devices be trusted?
- What are all the F5 devices in my environment?
- What is the current security risk status of my F5 devices?
- What actions can I take to address the risks and threats related to the F5 security incident?
Part of the work Eclypsium has done to help customers understand the security posture of their F5 technology is to extract and analyze the firmware from numerous F5 appliances, conducting deep analysis of not just the firmware package itself, but of each binary contained therein.
There are hundreds of thousands of binaries contained in the F5 firmware packages and embedded OSes for these products, creating a potential enormous playground for attackers seeking to introduce or exploit vulnerabilities. Eclypsium’s intent is to identify potential risk factors, and provide overall greater visibility to F5 users concerned about the integrity of the products going forward.
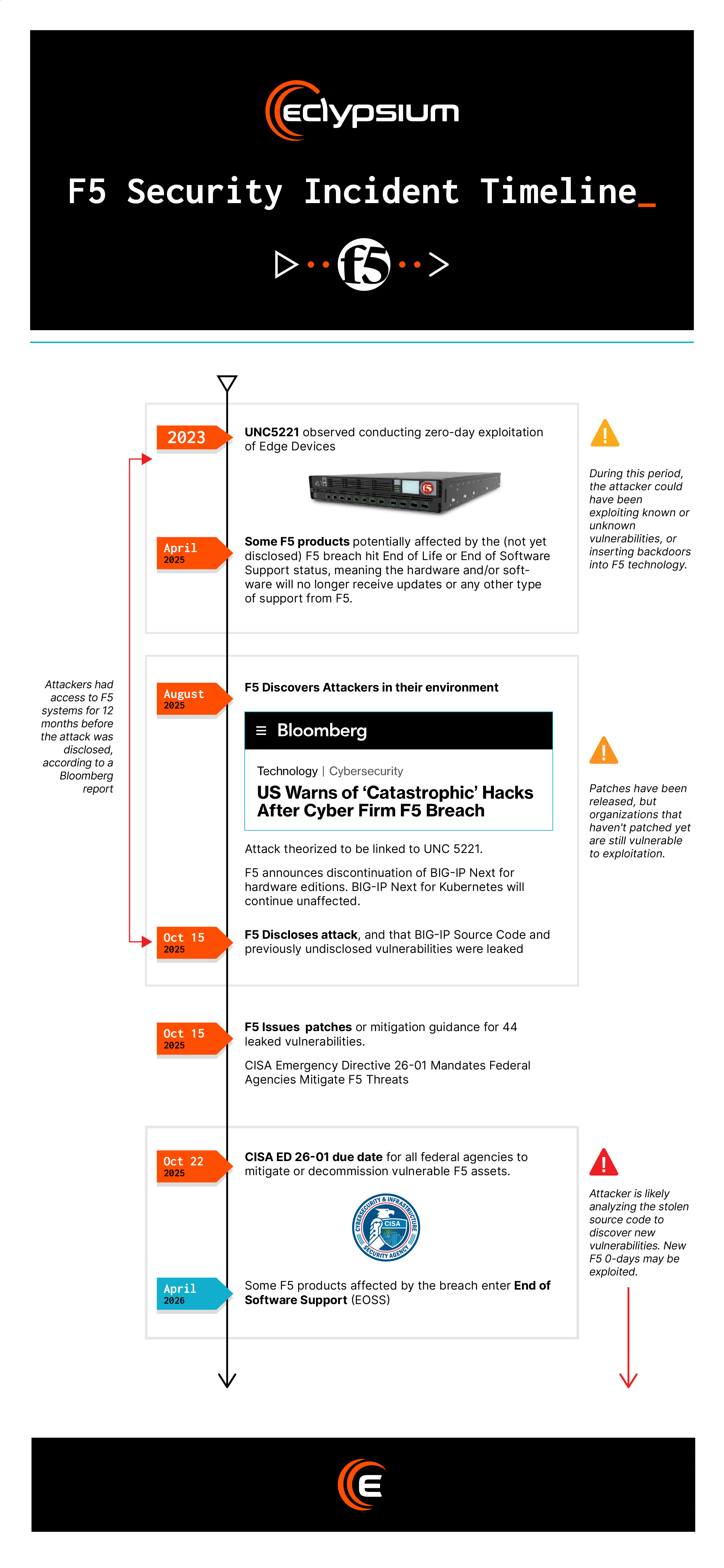
Timeline of Events: From Breach to Patch
We’ll address these five categories of question one by one, but first here’s a quick illustration of the timeline of events, from the best estimate of when the attackers first gained access to F5’s environment up to the current day, and known future dates, such as the end of service and support for affected F5 products.
Question 1: Has my organization been impacted by the F5 incident?
Yes. But the nature of that impact varies from organization to organization. Every organization with F5 devices in production now faces unknown risks that they have to decide how to approach. At minimum, F5 administrators have been forced to roll out a patch at an unexpected time. This is a costly disruption that takes away time and resources from other priorities, regardless of whether your F5 devices have been targeted by cyberattackers.
Furthermore, even if you’ve rolled out the patches that F5 delivered, there may be other previously disclosed or not-yet-discovered vulnerabilities that can cause your systems to become vulnerable when they were previously secure. This breach highlights a gaping hole in the security posture of many organizations: network edge devices.
Network device vulnerability exploitation increased 8x in the past year according to the Verizon Data Breach Investigation Report. The top four exploited vulnerabilities in Mandiant’s M-Trends report were all network perimeter devices. Advanced nation state threat actors prioritize persistence inside their target environments, and network devices are a perfect place to persist. They often use tactics to persist even after a reboot, OS reinstallation, and other remediation efforts on affected devices.
The question of whether the F5 incident has impacted you should be the beginning of a larger ongoing conversation about how you are securing your network edge devices against this rising tide of exploitation.
Question 2: Can my F5 devices be trusted?
A big question on everyone’s mind is “What do the threat actors know about the leaked source code that F5 and the rest of us do not know?” Even after deploying the patches issued by F5, enterprises are right to be concerned about the possibility of new undisclosed threats being discovered or exploited. Whether or not future vulnerabilities are related to the F5 breach, this incident highlights the importance of monitoring and protecting network edge devices, not just trusting that the vendor and their supply chain have delivered a secure product.
F5’s security incident disclosure notes that F5 BIG-IP source code has been leaked, but does not provide further details about the leaked code. F5 also shared that previously undisclosed vulnerabilities had been stolen by the adversary. While patches have been released for those 44 vulnerabilities across numerous F5 products, the potential for unknown vulnerabilities to be disclosed in the future must be factored into every enterprise’s assessment of whether to trust F5 devices.
Eclypsium is conducting in-depth static analysis of the firmware contained in several F5 BIG-IP products, evaluating over 100 model packages containing over 223,000 package binaries. We will continue to monitor and analyze these devices and binaries for potential vulnerabilities and threats over time.
With that said, no device that plugs into your network should be trusted by default. Several of the most exploited vulnerabilities in cybersecurity incidents in the past year affected network edge devices. Palo Alto GlobalProtect and Ivanti VPN products were the top exploited vulnerabilities in incidents investigated by Mandiant in 2024. It is clear that network edge devices in general must be less trusted and better secured than they currently are. The best way to protect against unknown threats and potential zero-day vulnerabilities is through a combination of proactive compensating controls and ongoing monitoring.
Eclypsium recommends regular integrity monitoring at the firmware or embedded OS level for network devices. By regularly checking each of the potentially hundreds of thousands of binaries against a known-good standard firmware image, enterprises can assure that implants, backdoors, and other tampering have not occurred deep in the foundations of their network perimeter devices.
Question 3: What are all the F5 devices in my environment?
Asset inventory is a foundational requirement for successful cybersecurity. In cases like the F5 breach, where source code and unknown vulnerabilities were exposed, asset inventory takes on a new deeper meaning. Knowing what devices you have in your environment is not enough. You need to know the components that make up each appliance, and all of the code that resides and runs on them. You also need to know the end of sale, end of software support, and end of life dates for these products, as it may affect whether past or future vulnerabilities are ever patched in your specific device versions.
F5 has conveyed to customers that they have no knowledge of any compromise of their software supply chain. But F5 customers are not wrong to be asking this question. When a nation state adversary has access to a system for a year or more, it is worth addressing the possibility that they introduced backdoors that haven’t been discovered yet. It is common for enterprises to leave network infrastructure in operations past its end of support or end of life date. Such devices are at added risk of having new vulnerabilities discovered, or old vulnerabilities exploited against them.
In F5’s Q4 2025 earnings call that came soon after the breach disclosure, at least one attendee asked whether the breach would impact the timeframe for end of software support dates on affected platforms. The short answer was “no.” You can read the longer answer in the screenshot below.
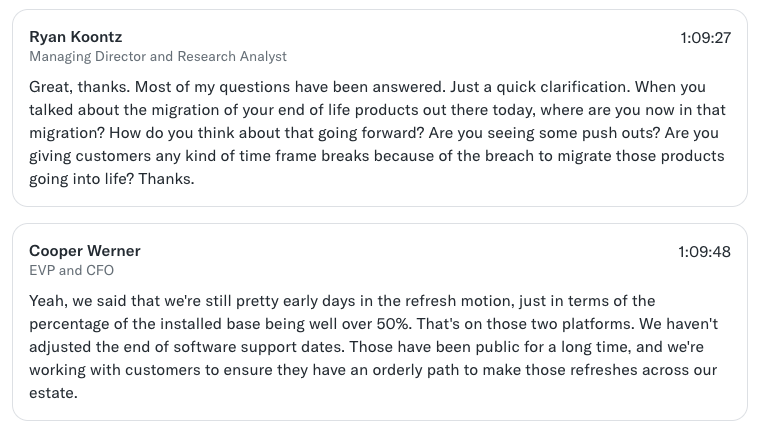
It is worth noting that in August, the same month when F5 discovered the presence of attackers in their environment, they also announced the discontinuation of BIG-IP NEXT. The BIG-IP NEXT project had been positioned as a more agile replacement to the “monolithic” TMOS operating system that underlies many F5 products. Some elements of BIG-IP Next have been scrapped, including those applying to hardware and virtual editions. BIG-IP Next for Kubernetes will continue development unaffected. Some vulnerabilities in BIG-IP Next that were leaked to the adversary during the security incident have not been patched.
This highlights both the importance and the difficulty of having thorough inventory. Knowing what you have in deployment can help minimize and optimize patching efforts, investigations, and incident responses.
Question 4: What is the current security risk status of the F5 devices in my environment?
Understanding the current risk status of F5 devices in your environment requires a level of visibility and monitoring far beyond what most organizations have into their network edge devices. Historically, network edge vendors like F5, Cisco, Palo Alto, and others have not enabled third party monitoring of the inner workings of their devices.
Nonetheless, the security risk of current F5 devices depends on myriad factors, including:
- Current firmware version
- Presence of patched or unpatched vulnerabilities
- End of service or end of life date, especially if these dates have passed
- Exposure of management interfaces either to external or less secure internal network segments
- Vulnerabilities in the underlying Linux version that is the basis for the F5 BIG IP OS
- And many more…
Eclypsium automatically scans F5 devices and other network edge infrastructure to provide a detailed firmware bill of materials, providing a more comprehensive asset inventory to use in risk analysis, attack surface management, and incident response. Eclypsium also detects known vulnerabilities and indicators of compromise on F5 devices, making it much harder for cyber adversaries to hide their activity and live off the land inside critical network infrastructure.
For years, Eclypsium has prioritized the ability to detect and respond to the stealthiest attack tactics targeting network edge devices and firmware. As a result, the Eclypsium platform offers unmatched visibility into vulnerabilities and IOCs used by attacker groups like Salt Typhoon, Volt Typhoon, and Velvet Ant, as well as the emerging category of UEFI bootkits like BlackLotus and HybridPetya.
Question 5: What actions can I take to address the risks and threats related to the F5 security incident?
Mitigating the current and potential future risks stemming from the F5 breach will require both immediate action and ongoing diligence. Eclypsium is advising our customers to take the following short, medium, and long term actions. For further details on how to effectively execute each step, Eclypsium customers can reach out to their account representative. Non customers can reach out to [email protected] or request an Eclypsium demo here to learn more about how we can help.
Short Term (Immediately) – Situational Awareness & Hardening
- Identify all F5 Devices
- Hardening and Exposure Management
- Apply Critical Updates & Patches
- Scan for BRICKSTORM
Medium Term (upcoming weeks) – Monitor & Respond
- Monitor for new Updates and Threat Intelligence
- Disconnect End of Support F5 Devices
- Network Isolation
- Device Integrity Monitoring
- Recurring Scans for Threats
Long Term (upcoming months) – Expand Security Diligence to all Network Devices
- Scan and Monitor all Network Devices
- Replacement Plan for End-of-Support F5 Devices
To learn more about rising attacks targeting network edge devices and IT infrastructure, check out our ebook: Eradicate Hidden Risks in Network Edge Devices: Critical Insights for Security Leaders






