Short Description: CVE-2025-427 (aka “Hydroph0bia”), CVE-2025-3052, and CVE-2025-47827 expose fundamental flaws in how firmware handles Secure Boot validation. Affecting systems using UEFI firmware, these vulnerabilities allow attackers to bypass critical security controls and execute malicious code during early boot phases. Here’s what you need to know:
Executive Summary
Three newly disclosed vulnerabilities in UEFI serve as a wake-up call for organizations relying on Secure Boot as a foundational security control. The three recent vulnerabilities are:
- The “Hydroph0bia” vulnerability (CVE-2025-4275 and VU #211341) in Insyde H2O allows attackers to bypass Secure Boot
- Microsoft patched CVE-2025-3052, a Secure Boot bypass vulnerability affecting more than 50 device makers.
- Zack Didcott disclosed a Secure Boot bypass vulnerability tracked as CVE-2025-47827 affecting IGEL Linux (which could also be used to boot any system and bypass Secure Boot protections).
These flaws allow attackers to bypass Secure Boot validation, gaining pre-OS persistence and the ability to execute arbitrary code at the firmware level. For CISOs, this is not just a technical issue; it’s a strategic risk that threatens the integrity of the entire computing stack, from endpoint devices to critical infrastructure.
Why This Matters
Firmware attacks are no longer theoretical. Over the past five years, Eclypsium research and industry incident response have documented a dramatic rise in real-world exploitation of UEFI and firmware vulnerabilities. Nation-state actors and criminal groups have exploited similar vulnerabilities to implant malware, evade detection, and establish long-term persistence, even surviving OS reinstalls and disk wipes. Hydroph0bia is the latest in a series of vulnerabilities that demonstrate attackers’ growing sophistication and willingness to target the firmware layer.
The business impact is severe:
- Stealth and Persistence: Firmware-level malware, capable of bypassing Secure Boot, enables threat actors to evade traditional EDR, SIEM, and antivirus solutions, operating below the OS and security stack. Malware can survive OS reinstalls and even some hardware resets.
- Supply Chain Risk: Vulnerabilities in widely used firmware, such as Insyde H2O, affect a broad range of OEM devices, amplifying risk across the supply chain.
- Operational Disruption: A compromised firmware environment can be used to disable security controls, steal credentials, or launch destructive attacks, potentially impacting business continuity and regulatory compliance.
Details On The Vulnerabilities
Hydroph0bia (CVE-2025-47827)
The vulnerability stems from improper handling of NVRAM variables in UEFI firmware. Insyde H2O’s firmware update mechanism relies on two variables:
- SecureFlashSetupMode: A trigger to load a certificate.
- SecureFlashCertData: Stores the certificate used to validate firmware update capsules.
Attackers can exploit UEFI’s failure to enforce volatility checks on these variables. By creating non-volatile copies of these variables (via admin-level access in the operating system), attackers can inject their certificate. The firmware then trusts any code signed with this certificate, thereby bypassing Secure Boot and allowing the execution of unauthorized UEFI applications or drivers.
Exploitation requirements:
- Write access to the EFI System Partition.
- Ability to create/modify NVRAM variables (achievable via local privilege escalation).
This vulnerability is particularly dangerous for devices lacking hardware-enforced UEFI protections, such as consumer laptops and embedded systems.
IhisiParamBuffer Memory Corruption (CVE-2025-3052)
CVE-2025-3052 exposes a memory corruption flaw in a UEFI module signed with Microsoft’s third-party certificate (“Microsoft Corporation UEFI CA 2011”). The vulnerability stems from improper handling of the NVRAM variable IhisiParamBuffer, which is read by the module and used directly as a memory pointer without validation. Attackers can manipulate this variable to write arbitrary data to any memory address, enabling them to disable Secure Boot by overwriting the gSecurity2 flag and execute unsigned code during the DXE phase of UEFI initialization. This exploit chain allows attackers to bypass Secure Boot entirely, even though the OS may still report Secure Boot as enabled, creating a stealthy persistence mechanism for bootkits or other malicious payloads.
Exploitation Requirements:
- Admin-level access: Attackers need privileges to modify NVRAM variables (e.g., via local privilege escalation or physical access).
- EFI System Partition (ESP) write access: To replace or modify boot components, such as registering a malicious UEFI application in the Boot Manager.
- Reboot capability: The attack triggers during system restart, when the vulnerable UEFI module executes before the operating system (OS) loads.
While not remotely exploitable, this vulnerability affects any device that trusts the widely used Microsoft UEFI CA 2011 certificate, including most x86 systems and Linux distributions that rely on the shim bootloader. Microsoft mitigated the issue by blacklisting the vulnerable module in its June 2025 Secure Boot DBX update, but unpatched systems remain at risk.
CVE-2025-47827: A Secure Boot Bypass in IGEL OS
CVE-2025-47827 exposes a critical flaw in IGEL OS versions before 11, where the igel-flash-driver kernel module fails to validate the cryptographic signatures of SquashFS root filesystem images properly. Attackers canCVE-2025-47827 exposes a critical flaw in IGEL OS versions before 11, where the igel-flash-driver kernel module fails to validate the cryptographic signatures of SquashFS root filesystem images properly. Attackers can exploit this by booting a Shim loader signed by Microsoft’s 3rd Party UEFI CA, which then loads a vulnerable GRUB and Linux kernel (both signed by IGEL’s Secure Boot Signing CA). Once the compromised kernel and initramfs load, a malicious root filesystem from an unverified SquashFS image is mounted. This allows attackers to replace the running kernel via the kexec_load syscall, bypassing Secure Boot entirely and executing arbitrary code at the kernel level. The vulnerability persists even in patched IGEL OS versions, as both vulnerable and fixed kernels share the same signing certificate.
Exploitation Requirements:
- Secure Boot Configuration: The system must trust the Microsoft 3rd Party UEFI CA (default on most devices).
- Boot Media Control: Attackers either need code execution on the device to be able to write to the ESP or they can use a separate bootable disk such as a flash drive containing the malicious GRUB configurations, kernel, and SquashFS images.
- Persistence Mechanisms: Malicious EFI binaries and kernel files must remain on disk, with the boot order configured to prioritize the compromised components.
The exploit chain illustrates how trust in widely used certificates (e.g., Microsoft’s UEFI CA) can compromise Secure Boot’s integrity, allowing for stealthy firmware-level attacks.
How Eclypsium Strengthens Defenses
Eclypsium’s platform provides critical visibility and protection against firmware-level threats like Hydroph0bia, for example:
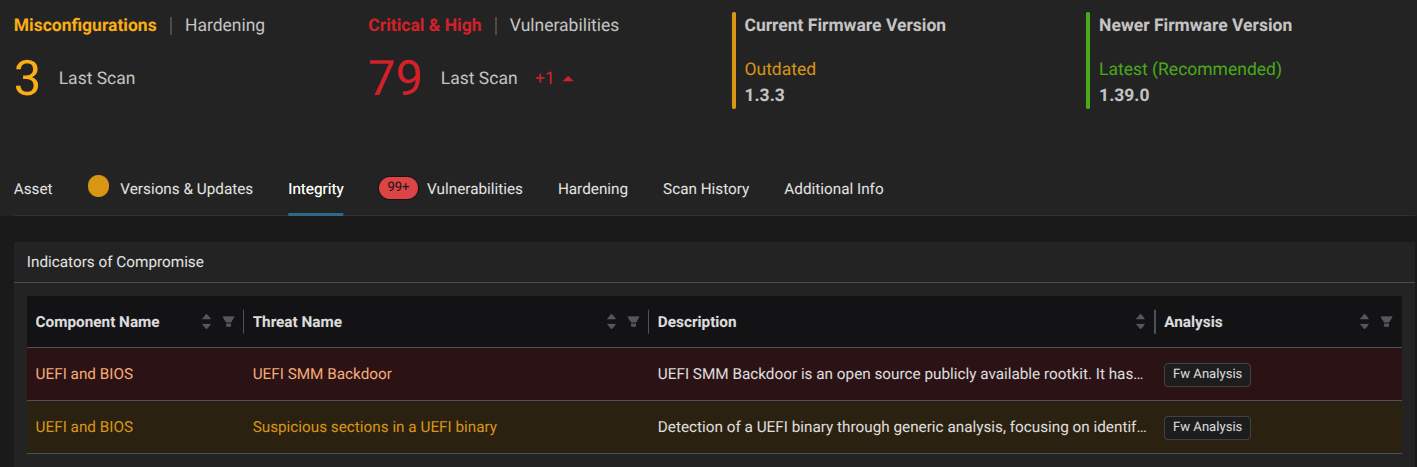
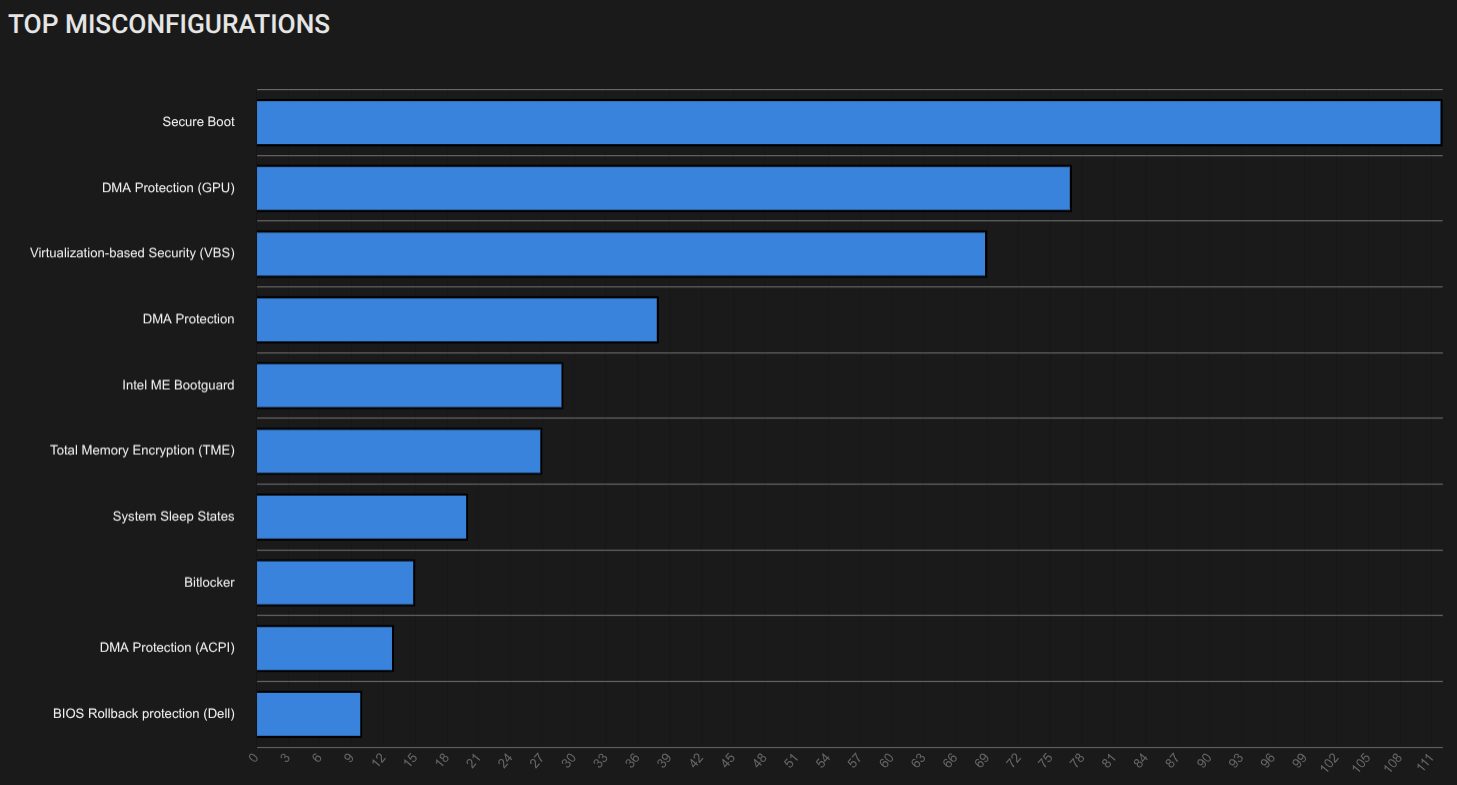
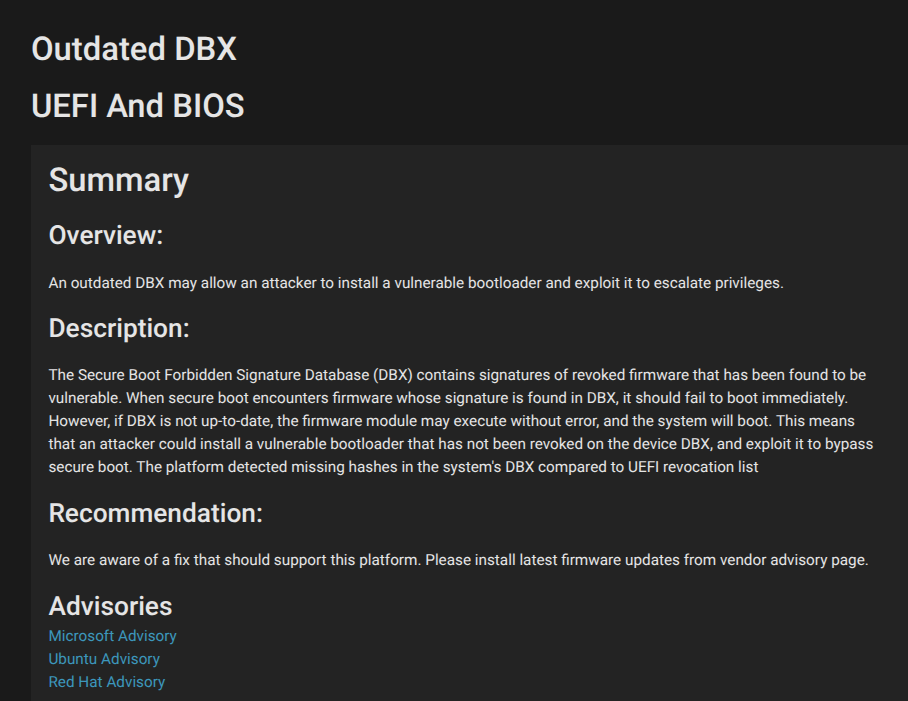
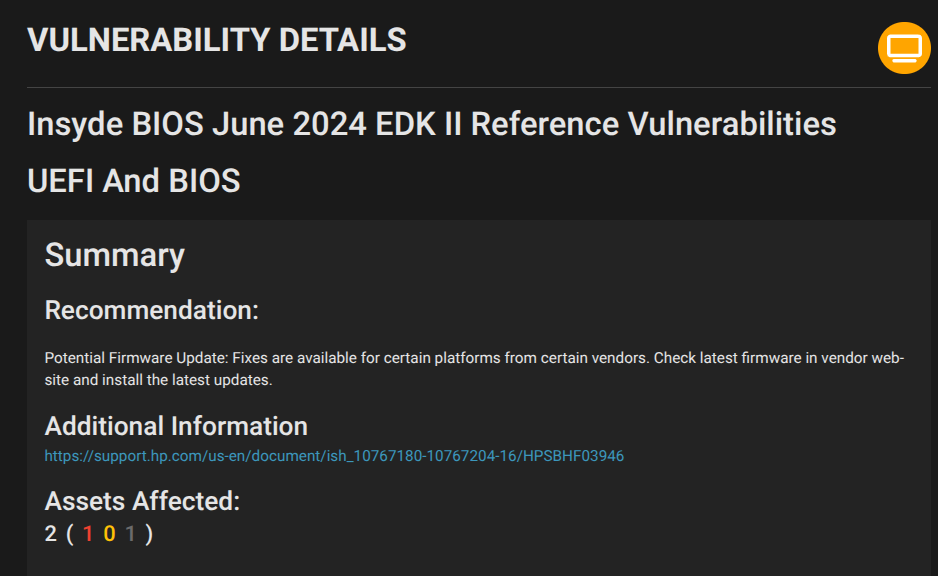
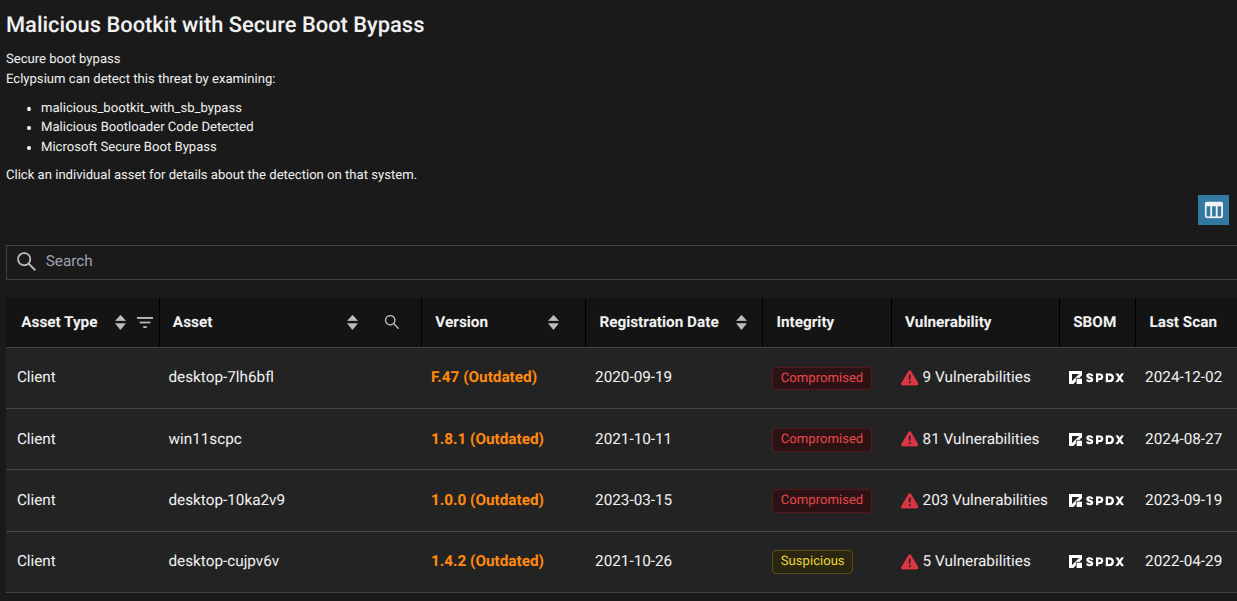
Mitigations and Protections
- Firmware Updates: Immediate application of vendor patches is critical. Insyde has released updates, but OEM adoption and deployment may lag.
- Hardware Protections: Enabling Intel Boot Guard, AMD Hardware Verified Boot, and SPI flash write protections can help prevent unauthorized firmware changes.
- UEFI Variable Locking: Ensuring that critical NVRAM variables cannot be modified outside of authenticated update processes.
- Visibility and Monitoring: Traditional endpoint tools are blind to firmware changes. Continuous monitoring of firmware integrity and Secure Boot status is essential.
Eclypsium’s automated firmware analysis and runtime protection mitigate risks posed by Hydroph0bia and similar vulnerabilities.
The Bigger Picture
The recently disclosed UEFI vulnerabilities underscore systemic issues in UEFI security, echoing earlier findings in the Pacific Rim campaign, where attackers exploited firmware weaknesses in network appliances. As nation-state actors increasingly target firmware, tools like Eclypsium and rigorous patch management are no longer optional—they’re essential to safeguarding the foundation of modern computing.






