Backdoored Juniper networking devices are at the center of two major cybersecurity stories that highlight the ongoing vulnerability and active targeting of network infrastructure by cyber adversaries.
J-Magic and TINYSHELL
The first story broke in January 2025, when researchers at Black Lotus Labs, a research arm of the ISP Lumen Technologies, revealed information about an attack campaign dubbed J-Magic. The campaign involved the attacker dropping a backdoor, based on the open source cd00r backdoor, onto carrier-grade Juniper routers.
The second story, reported by Mandiant on March 11, 2025, also involves a backdoor, this time based on the also popular open source Tiny Shell, also targeting carrier-grade MX-series Juniper routers. The attack has been associated with the UNC-3886 threat actor and is likely targeting telecommunications carriers and internet service providers.
In both cases, the open-source backdoor software had been customized by the attackers to allow for stealthy malicious attacker behavior. The cd00r malware was configured to listen for incoming “Magic Packets” on the network, then set up a reverse shell. The Tiny Shell malware, reported by Mandiant researchers, involved six different variants of the malware, all of which “incorporate a core TINYSHELL backdoor functionality” according to Mandiant’s research.
Why Attackers Target Network Devices
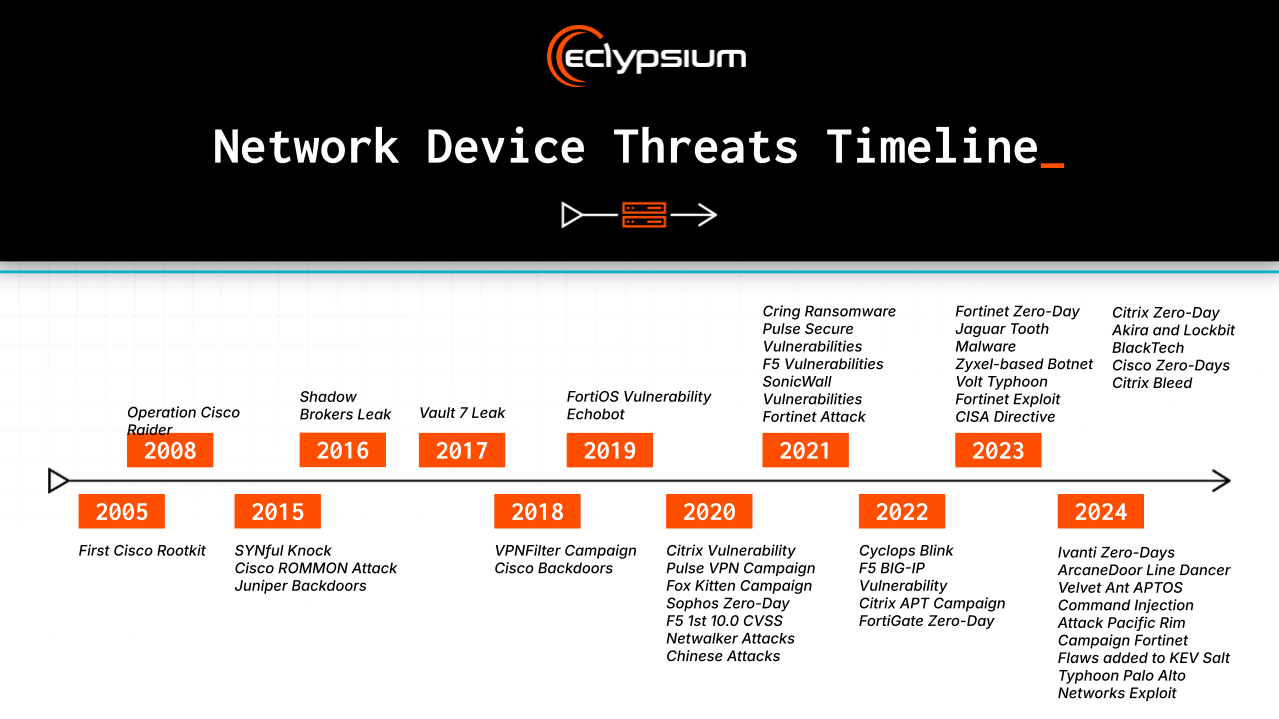
Network devices are often less rigorously monitored and secured than end user endpoints and workstations. Furthermore, network devices feature numerous known exploited CVEs and other risk factors that make them an appealing target for attackers. Our network device threats timeline shows that the volume of attacks against network infrastructure has risen dramatically over the past two decades, with a sharp spike from 2020-2024
In Mandiant’s blog about the TINYSHELL discovery, they noted that the attacker behavior they had observed “showcases a development in UNC-3886’s tactics, techniques and procedures (TTPs), and their focus on malware and capabilities that enable them to operate on network and edge devices, which typically lack security monitoring and detection solutions, such as endpoint detection and response (EDR) agents.”
That lack of security monitoring and detection, along with the sheer ubiquity of a few global network infrastructure providers, including Juniper, plays a role in the increasing number of attacks targeting this gear.
Mandiant also noted that “Investigating further actions taken by the threat actor was hampered by the challenges inherent in analyzing proprietary network devices, which required novel methods for artifact acquisition and analysis.“
They concluded that: “The compromise of routing devices is a recent trend in the tactics of espionage-motivated adversaries as it grants the capability for a long-term, high-level access to the crucial routing infrastructure, with a potential for more disruptive actions in the future. A concerted effort is required to safeguard these critical systems and ensure the continued stability and security of the internet.”
This is not the first time that the vulnerability and increased targeting of network gear has been highlighted. In 2024, CISA released a list of the Top Routinely Exploited Vulnerabilities (from data observed in 2023). Over half of them either directly or peripherally affected network infrastructure vulnerabilities.

Typhoons vs. ISPs

These latest news stories contribute to a growing body of knowledge about how nation-state sponsored APTs are targeting telecommunications carriers and internet service providers. We dubbed 2024 The Year Of The Typhoon because of the numerous disclosures of attacks by Salt Typhoon, Volt Typhoon, Flax Typhoon, and other continuously tracked APTs specifically targeting communications infrastructure.
In early 2025, Silk Typhoon started making headlines for similar reasons. While the specific tactics, techniques, and procedures may vary, the overarching trend of network devices, firewalls, VPN gateways, routers, switches, and application delivery controllers being targeted is unmistakable. The difficulties that Mandiant expressed in their investigation of proprietary network gear are an increasing problem, as more organizations seek to baseline, harden, and protect their critical networks.
An outlier in this sequence of disclosures was the Pacific Rim campaign disclosed by Sophos in late 2024. Sophos had tracked attack attempts for five years. As part of their investigation and defense, they improved their telemetry, detection, and response capabilities, and monitored the entire fleet of Sophos firewalls, providing some of the much needed visibility to illuminate nation state attack tactics.
At the time, Sophos CEO Joe Levy called for a change in how the entire industry handles network security device maintenance.
How Eclypsium Can Help
Eclypsium is able to detect active indicators of compromise that may point to use of the JMagic and TINYSHELL backdoors and their associated behaviors in a target environment. Eclypsium is also able to continuously monitor the integrity of firmware components, as well as spot high-risk misconfigurations in networking devices to enable security teams to harden their enterprise networks against attacks.
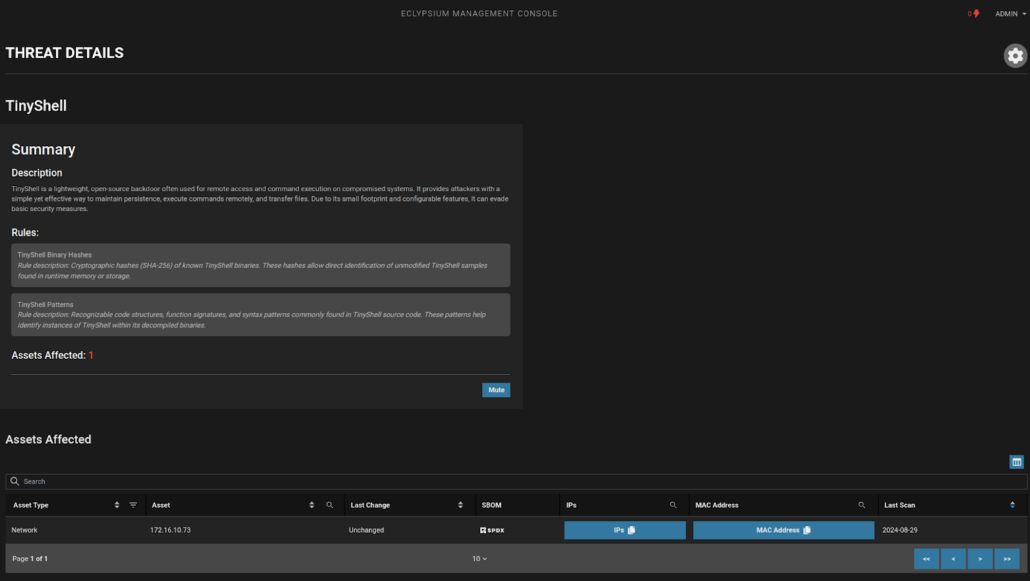
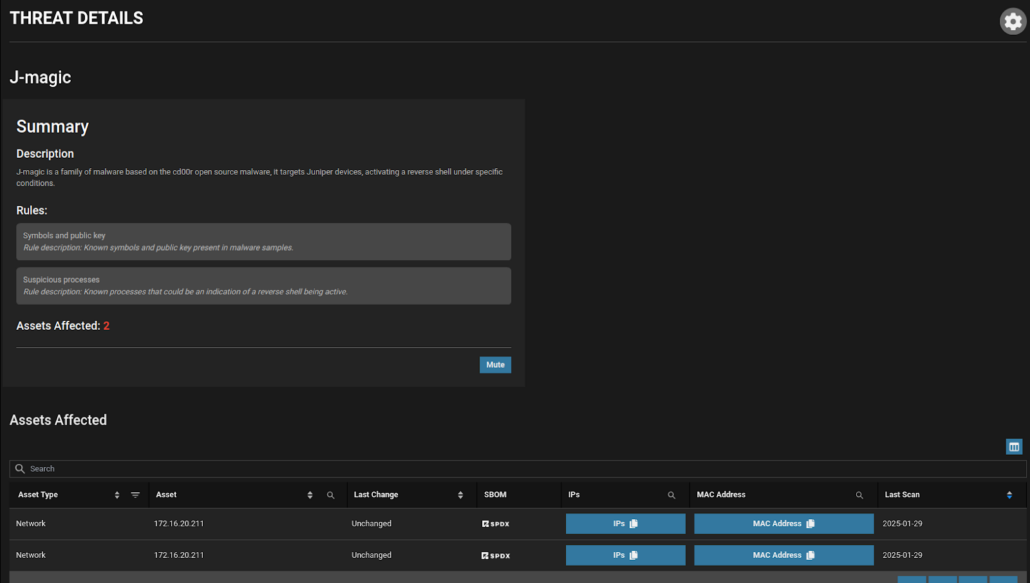
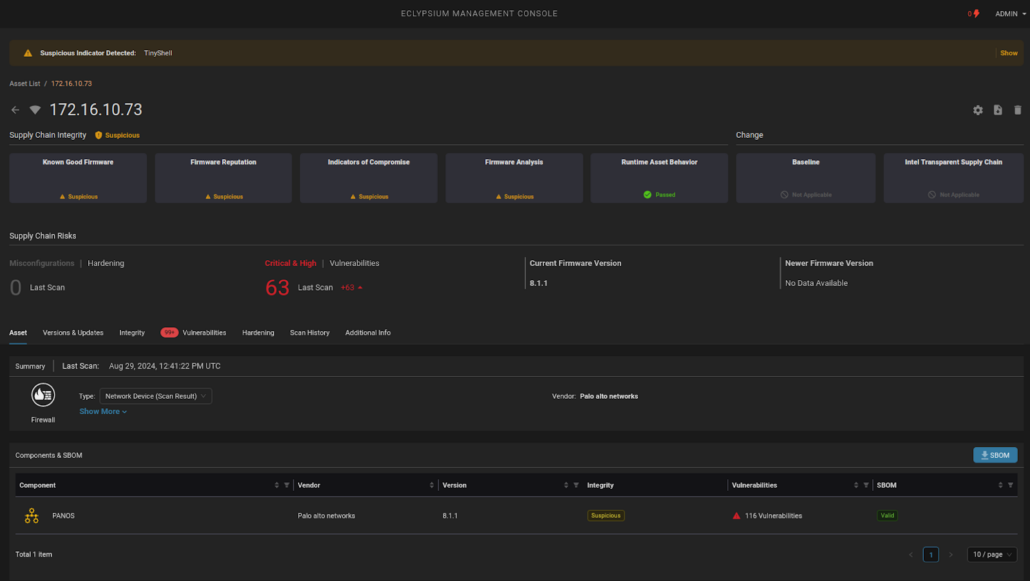
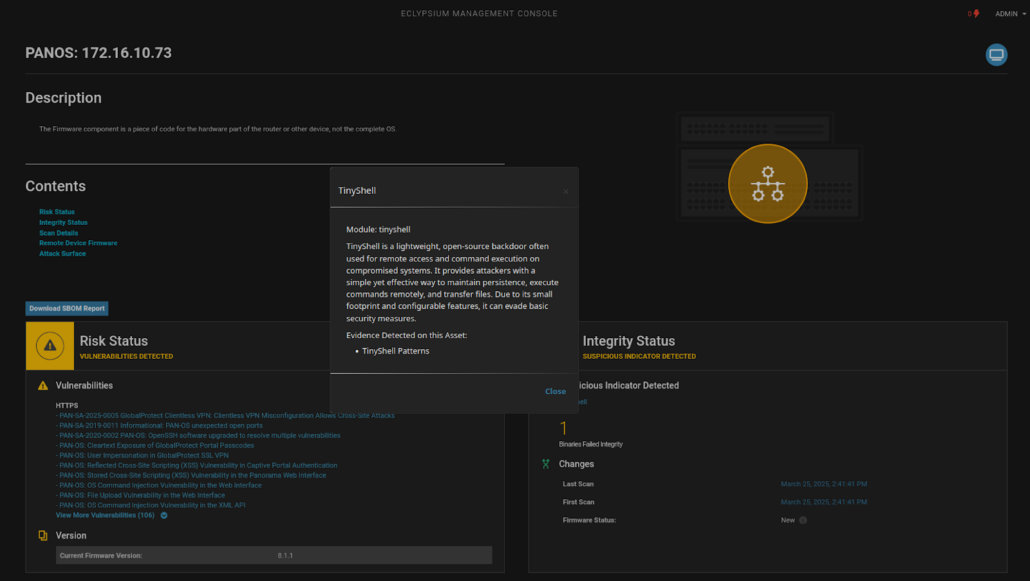
Eclypsium vs. The Typhoons
In addition to hardening against backdoors deployed on Juniper deviced, Eclypsium offers detection and hardening capabilities against the specific tactics and CVEs being used by the Typhoon family of threat actors. Eclypsium also offers a free Salt Typhoon Risk Assessment to telcos and ISPs that are concerned they may be compromised, or may be targeted in the future, by these threat actors.
To learn more about how Eclypsium works in your environment and learn how to baseline, harden, and defend network infrastructure against the growing flood of attacks, you can request a live demo here.






