12,000+ Exposed Juniper Devices Have Critical Vulnerabilities
Juniper Networks is one of the industry’s most long-standing and popular enterprise networking vendors. This history and popularity means there are thousands of Juniper devices in production networks and many of them are relatively old. And where there are older devices, there are likely to be vulnerabilities that will put organizations at risk. On July 13th, 2022, Juniper patched six high-severity vulnerabilities in their own software, along with over 200 vulnerabilities in open source software used in their products.
Organizations depend on multitude of device suppliers like Juniper; these network devices are part of critical ICT supply chain and represent significant supply chain risk. Furthermore, these Juniper devices are built with many 3rd party components and this can inherit critical vulnerabilities from these components. There is also a risk of counterfeit devices; mere days before Juniper released their patches an arrest was made of an individual who sold hundreds of millions of dollars of counterfeit Cisco equipment. In May 2022, Cisco released an advisory urging customers to upgrade their device firmware to protect against counterfeit devices, many of which have been tampered with to bypass security & licensing controls.
As part of our ongoing research on the security of network devices, we wanted to quantify the level of Juniper device exposure on the internet. Using Shodan and a variety of pre-authentication fingerprinting techniques we were able to identify the JunosOS version of 12,876 devices and found that 94% of them contained at least one Critical vulnerability. We identified a further 5,167 devices based on their year of release and determined that 67% of these additional devices were highly likely to contain at least one Critical vulnerability.
Why Bother Looking for Old Vulnerabilities?
Virtually every organization relies heavily on networking equipment, and in recent years, advanced adversaries and ransomware groups have heavily targeted these critical pieces of infrastructure as we mentioned in 2021. In particular, attackers have targeted externally-facing vulnerabilities in these devices as a powerful initial access vector that can be used to spread to other assets in the enterprise.
A growing trend in adversarial tactics is the targeting of network infrastructure, especially relatively old or uncommon devices as seen in recent ransomware attacks against Accellion FTA appliances. This makes it extremely important for network and security teams to find and remediate any vulnerabilities before they can be exploited by adversaries.
Analysis Methods and Findings
Using Shodan, we identified an initial dataset of around 25,000 Junos-based devices. Then we attempted to identify the Junos version running on each device, since specific vulnerabilities can be extrapolated for a device based on its version of Junos. There are a variety of places that we can look to find the Junos version running on a device, such as information embedded in the HTML responses of the user interface or via services such as SNMP. Using such techniques, we were able to identify the Junos version for 12,876 devices. We also collected the copyright date presented on the device’s management page as a less scientific estimate of the age of the device.
It is important to note this data set is built from devices whose management interfaces were accessible via the internet. Security best practices would advise against this, so there are likely many more Juniper devices that were not visible to our analysis. As such, our data should not be used to infer the vulnerability of all Juniper devices. However, it does provide a real-world view of devices that could be accessed and exploited in real-world attacks.
Let’s dive into the data:
Version Statistics
Using the pre-authentication fingerprinting techniques described above, we were able to identify the Junos version running on 12,876 devices. We were not able to identify versions for 10,016 devices. In total, we found 288 unique versions of Junos.
The top 50 most common versions are summarized below (excluding unknown entries). Note that the leading characters of a version number do not reliably signify the year of release; for example, many 15.x versions were released in 2018 and 2019.

Juniper provides lifecycle information, and we can use this to attach end-of-support time to the devices in the dataset.
Some key observations related to these versions:
- Only 114 identified devices are running a version from branches currently supported by Juniper. This is ~1% of all devices with a known version. Devices running newer firmware – which report the year as 2021 and 2022 – are likely from a supported branch as Juniper tends to show version data less often on newer devices.
- 6,210 devices are running versions in 12.1X44 – 12.1X47 branches, which all reached end-of-support between 2015 and 2017.
- 4,252 devices are running versions 15.1X49 and 15.1X53. X49 reached end-of-support on 06/30/2021, and X53 reached end-of-support on 12/05/2018.
- The top 3 entries for 15.1X49 are running firmware released in 2019 (15.1X49-D70.3, 15.1X49-D150.2, 15.1X49-D170.4). This accounts for 2,744 devices out of 4,252 devices running 15.1X branch.
- 657 devices are running versions in the 12.3R branch, which reached end-of-support in 2016.
- 251 devices are running versions in the 11.4R branch, which reached end-of-support in 2015.
- At least 2 devices are running a version as old as 7.1R1.3 from 2005.
In total, we observed most of the fingerprinted devices are running a version that is no longer supported by the vendor, or outdated by 4+ years. The chart below shows the number of known vulnerabilities in each version of Junos.
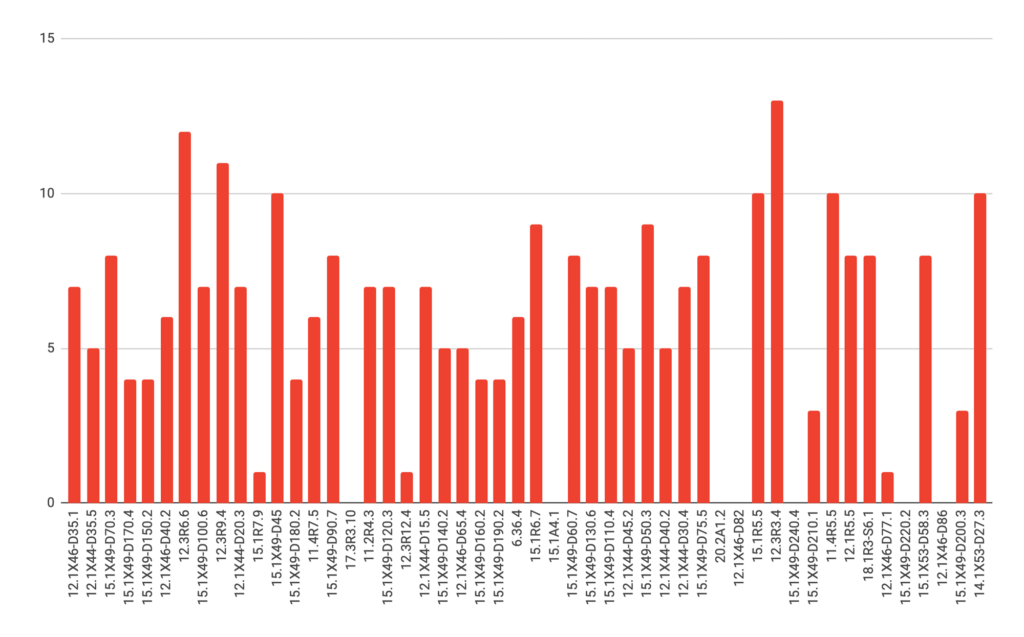
Critical Vulnerabilities
The older the device operating system is, the more exposure it will have to known vulnerabilities. Based on our collected data, we were able to identify devices running versions known to have at least one Critical vulnerability.
For this project we used the vulnerabilities listed in the Juniper advisories below, which includes vulnerabilities in both Juniper proprietary code and ones in open source software; OpenSSL “Heartbleed” for example.
| Year | Juniper Advisories |
| 2012 | JSA10472 |
| 2013 | JSA10547,JSA10574,JSA10594,JSA10597 |
| 2014 | JSA10619,JSA10623 |
| 2015 | JSA10669,JSA10690,JSA10697 |
| 2016 | |
| 2017 | JSA10791,JSA10793,JSA10801,JSA10802,JSA10818 |
| 2018 | JSA10828,JSA10844,JSA10871,JSA10874,JSA10878,JSA10898 |
| 2019 | JSA10906,JSA10916,JSA10930 |
| 2020 | JSA10998,JSA11016,JSA11021,JSA11031,JSA11034,JSA11057 |
| 2021 | JSA11101 |
Known Vulnerable Devices
Of the 12,876 devices with identified versions:
- 12,214 devices contain at least one Critical vulnerability.
- 662 devices are not vulnerable to Critical vulnerabilities.
Additional Likely Vulnerable Devices
In addition to the 12,876 devices with known versions, we were able to identify another 5,167 devices that displayed copyright year but not version data. We do not consider copyright year to be a reliable metric, but it can provide additional insight into these devices. For example, a device which reports 2019 as the copyright year may actually run a newer non-vulnerable firmware version as the copyright year may not necessarily be updated with every release. Conversely, if the copyright year is from 2012 there is high probability the device is running an outdated firmware version.
We estimate that in the best case:
- 3,500 devices are likely to contain at least one Critical vulnerability (copyright year <= 2020)
- 1,667 devices are unlikely to be vulnerable (copyright year >= 2021)
In the worst case, all devices from 2021 may be outdated, leaving only 297 devices with the reported year of 2022 that are unlikely to be vulnerable.
Conclusions
Juniper devices are high-value enterprise assets and carry a very high impact when compromised in a cyberattack. The massive increase in attacks against network devices in the past few years illustrates this is a very real risk. Our analysis indicates there are large numbers of potential Juniper targets which are publicly accessible. As a result, it is imperative that organizations be aware of these vulnerable devices and take appropriate actions to update and protect them before they can be exploited.
Eclypsium’s firmware security platform can help organizations automatically identify vulnerable devices, scan them for threats, and help apply any needed updates. To learn more about this research or the Eclypsium solution, please contact us [email protected].






