In the first part of this series, we described the incident between MSI and a new ransomware group known as Money Message. The group claimed to be able to release malicious firmware with what they had stolen, which included MSI’s development framework and private keys. Since this is a serious situation, we assessed various risks related to the event. We found notable increases in risks related to supply chain, backdoors, and vulnerabilities, but we also re-confirmed the extreme risk already present on MSI systems due to a lack of signatures on updates. Without these signatures, enterprises and consumers have no way to verify known-good firmware binaries before installing them, creating a scenario ripe for abuse by any supply chain attacker.
MSI has given official guidance that updates from trusted sources like their website can be trusted. Eclypsium has since performed comprehensive analysis on MSI’s official firmware updates in order to discover any evidence of malicious activity.
Status Update for April 21, 2023:
Eclypsium has completed analysis of 230,000 of MSI firmware binaries. The analysis was designed to discover techniques used by firmware-based malware over the last 8 years. At the time of writing, no evidence of malicious implants was discovered in the official update images from msi.com.
For the remainder of this post, we will discuss a small subset of our analysis and the historical attacker goals and methods that motivate this analysis.
Proving a Negative
Before diving into the analysis details, it is important to recognize the impossibility of a task like this. Technically, the space of potential malicious code is infinite. Anyone can come up with new and different malicious techniques, and avoiding known detection methods can be a design requirement for the adversary. Security research highlights this dynamic all the time.
However, real-world adversary operations have more constraints than research. Any given attack is limited by what is known, resources available at the time, and the risks to the attacker. The known, easy-to-implement attacks that have been used before present the best case scenario for an attacker exploiting this incident. These are also the cases that are easier for us as defenders to assess. Much of defensive security involves simply increasing the work required for a successful attack. Therefore, the goal of this analysis is simply to raise the economic bar, forcing attackers to do something new and different in order to avoid detection and preserve the advantage firmware-based implants give them.
Time Series Analysis
As discussed in part 1, initial checks focused on the behavior of MSI in releasing updates. This corresponds to the serious risk that the development or firmware distribution infrastructure may have been compromised and the supply chain both upstream and downstream from MSI may be affected. Our analysis included both a comparison of the timing of MSI’s released firmware against the industry as a whole, and an examination of differences over time.
If an attacker was using compromised infrastructure to distribute backdoored updates, we might expect a bunch of new releases to show up. In order to distinguish this signal from the noise of normal updates, we can compare the timing against other OEMs. Both had an uptick in releases recently, so there is no obvious conclusion from this alone.
MSI Releases:

Industry Releases:

Another approach that an attacker might use would be modification of existing updates. To address this concern, we also attempted to compare official MSI updates downloaded recently from those downloaded many months ago. This would alert us to any unexpected changes. No such changes were discovered.
Since these analysis results did not reveal any clear cause for alarm, we moved on to deeper analysis of the firmware itself. Given knowledge of previous insecurity on MSI systems and the associated updates, we were able to quickly re-validate this issue as discussed in part 1. The remaining analyses will focus on searching for specific attack techniques in firmware binaries.
Detecting Persistence on Disk
Attackers are usually familiar with existing malware that has been successfully deployed in the past. Perhaps the most obvious firmware implant method, therefore, is to re-infect a system that has previously been infected after it was wiped/reinstalled or otherwise cleaned. This method was used by Lojax, MosiacRegressor, and others. Detection of this method can focus on access to disk storage and the presence of OS-level executables within firmware. There are some known examples where this can be done by official OEM software, but Eclypsium was able to leverage past research into this to tune the analysis. Again, no unexpected results were discovered.
Detecting In-Memory Modification
Another method for installing malicious implants is to modify processes in memory, sometimes known as “hooking” a piece of code. One would not expect firmware to tamper with the integrity of an OS or application, and this is generally a sound assumption, but firmware-based implants like MoonBounce and CosmicStrand do exactly this sort of thing. No official MSI firmware images triggered this detection method.
Detecting Binary Markers
Other patterns in the loading and execution of firmware can be found by examining uncommon properties of malicious firmware. This could include attributes of the code, the way it accesses resources, or the packaging formats. Eclypsium researchers examined some of the newer firmware implants and picked out attributes that do not appear in normal firmware. When applied to the dataset from MSI firmware updates, it showed no obvious sign for alarm.
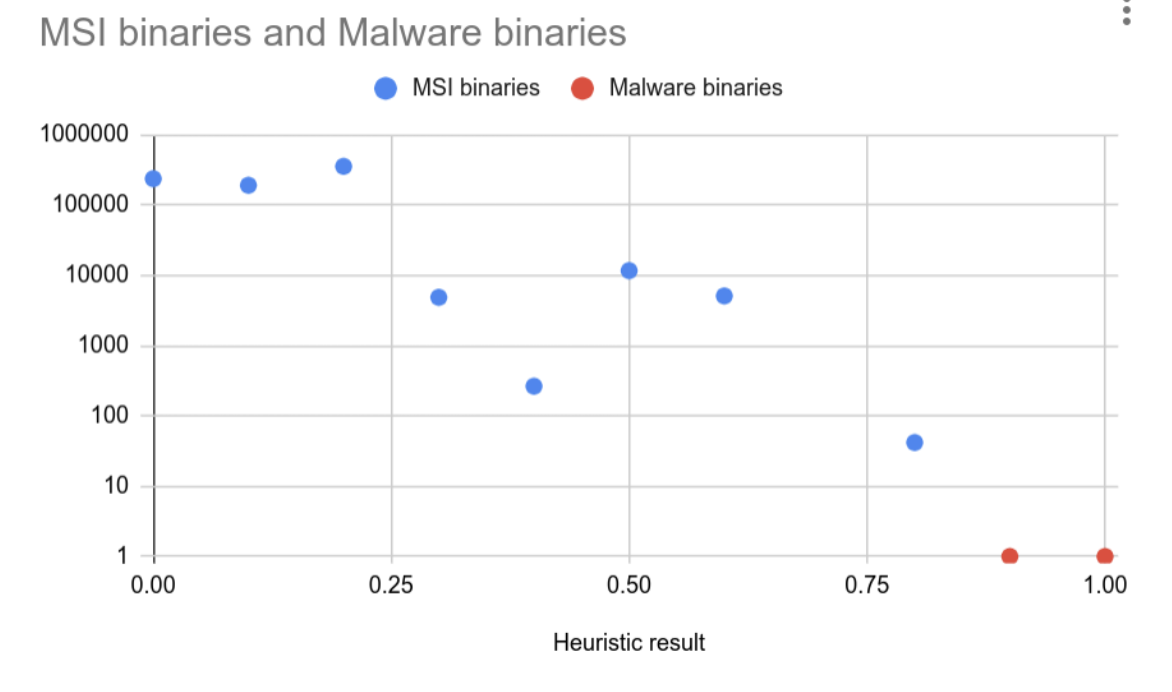
In Conclusion, It Never Ends
In truth, the event surrounding MSI is still unfolding. While a relatively new extortion group, Money Message have exhibited the ability to specifically target the IP of each victim, in order to gain maximum leverage. There is always a chance that the access they have to MSI’s development framework and environment could be sold to 3rd party groups that specialize in carrying out supply chain attack campaigns. Perhaps even Money Message themselves have the skills and intention to do so. We simply don’t know at this early stage. In order to gain some degree of confidence, though, Eclypsium has completed the three analysis methods above without any evidence of malicious implants.
Given MSI firmware is not signed, MSI and their devices remain an ideal supply chain attack target. Such a scenario would give an attacker extremely privileged and difficult-to-detect presence in downstream victim environments, forming the basis for a long-tail espionage campaigns akin to the recent SolarWinds and 3CX supply chain attacks.
Adversaries get a disproportionate advantage by going where defenders aren’t watching, and that puts more pressure on assuring the many complex dependencies inside every piece of technology. As Eclypsium continues to expand into all aspects of the digital supply chain, we expect to do even more at-scale analysis like this across hardware, firmware, and all kinds of software. This, in turn, provides our customers with the best possible enterprise grade technology to proactively defend themselves, get ahead of such threats and high impact scenarios, and be able to react should one arise.






