Security appliances, such as firewalls, VPNs, and secure web gateways, are designed to protect organizations from cyber threats. However, these assets designed to protect enterprises are increasingly the target of attackers who exploit vulnerabilities in security appliances to gain access, evade security teams, and maintain persistence within target organizations.
The issue is that security appliances, ironically, are often very poor regarding their own supply chain security and device integrity. Just as an example, we have recently discovered and/or added detections for vulnerabilities and threats in a variety of security appliances, including:
- Sophos – As part of the Pacific Rim disclosure, we’ve uncovered similar vulnerabilities and added support to our product to detect both the vulnerabilities and attacker IoCs.
- Squashing the Velvet Ant: How Eclypsium Protects Cisco NX-OS and F5 Load Balancers – This article covers the detections we’ve developed for both Cisco NX-OS and F5 load balancers to detect the Velvet Ant campaign.
- Previous research also covered another set of F5 Load Balancer vulnerabilities.
Our latest research has found that these problems extend to Palo Alto Networks devices. We purchased multiple Palo Alto Networks security appliances, expecting a high level of security and resilience. Instead, what we found under the hood was commodity hardware, vulnerable software and firmware, and missing security features.
These weren’t obscure, corner-case vulnerabilities. Instead these were very well-known issues that we wouldn’t expect to see even on a consumer-grade laptop. These issues could allow attackers to evade even the most basic integrity protections, such as Secure Boot, and modify device firmware if exploited.
Eclypsium researchers (primarily Mickey Shkatov and Jesse Michael) conducted evaluations of three Palo Alto Networks appliances:
- PA-3260 – This model’s hardware was marked as end-of-sale on August 31, 2023 and is scheduled for end-of-life on August 31, 2028. The device will support PAN-OS 11.1 released on November 3, 2023, and scheduled for end-of-life on May 3, 2027.
- PA-1410 – This is a newer model NGFW and, according to Palo Alto’s website, fully supported.
- PA-415 – This is also a newer and fully supported NGFW platform.


We found lurking below the surface a host of known vulnerabilities and misconfigured security features. Below are the details of our findings:
Boothole & Secure Boot Bypass Vulnerability
Affected Platforms: PA-3260, PA-415, & PA1410
Secure Boot is a critical security feature that verifies the integrity of the boot process and significantly enhances protection against threats like rootkits, bootkits, and firmware-level attacks by preventing unauthorized or malicious code from executing before the operating system loads. This is a crucial layer of security for all systems, including network and security devices/appliances, as it helps maintain system integrity.
The root of trust is represented by multiple certificates (PK and KEK) in addition to variables that store certificates or hashes of allowed (the DB) and disallowed (DBX) software that may execute during boot. Most PCs, servers, and laptops use certificates provided by the OEM and the operating system vendor (in most cases, the certificates are issued by Microsoft on the desktop). UEFI Secure Boot was designed to allow the user, or a vendor, to provide their certificates and accompanying DB and DBX data sets. Palo Alto has chosen to produce their own set of certificates for their devices, which means the DB and DBX must be updated by Palo Alto and ultimately dictate which software is allowed to run during system boot. In this case, Palo Alto has not updated the DBX to disallow specific software, such as vulnerable versions of the GRUB2 bootloader, allowing an attacker to bypass Secure Boot.
Discovered by Eclypsium researchers in 2020, the BootHole vulnerability (CVE-2020-10713) is a critical security flaw in the GRUB2 bootloader that affects billions of devices running Linux distributions and Windows systems with Secure Boot enabled.
This buffer overflow vulnerability allows attackers with elevated privileges to bypass Secure Boot by manipulating the grub.cfg configuration file, potentially executing arbitrary code during boot and gaining near-total control over the victim device. BootHole enables the installation of persistent and stealthy bootkits or malicious bootloaders, compromising the integrity of the boot process and posing a significant threat to servers, workstations, laptops, and various IoT systems. Even if Secure Boot was enabled on this particular device, attackers could circumvent the protections using this vulnerability:

Palo Alto released an advisory notice about the BootHole vulnerability in 2020. In the advisory, Palo Alto states:
“It is not possible for malicious actors or PAN-OS administrators to exploit this vulnerability under normal conditions. Administrators do not have access to the grub configuration file nor do they have permission to modify it. An attacker would need to first compromise the system and then get the root Linux privileges necessary to perform these actions before they could exploit this vulnerability.”
Fortunately for attackers (and unfortunately for defenders), gaining root privileges on Palo Alto PAN-OS devices is possible by combining exploits for two CVEs: CVE-2024-0012 and CVE-2024-9474, as documented by Watchtowr Labs in November 2024. While the article published by Watchtowr Labs contains all of the details required to create a working exploit, they did not release a PoC (Proof-Of-Concept). However, at least one public exploit exists for these vulnerabilities (use at your own risk!).
Here’s a video demonstration of an attacker exploiting the BootHole vulnerability on a PA-1410:
InsydeH20 UEFI Vulnerability
Affected Platforms: PA-3260
System Management Mode (SMM) vulnerabilities pose significant security risks due to the highly privileged nature of SMM in modern processors (For example: UEFIcanhazbufferoverflow: Widespread Impact from Vulnerability in Popular PC and Server Firmware). SMM vulnerabilities typically arise from flaws in the SMM code, particularly within System Management Interrupt (SMI) handlers, allowing attackers to:
- Escalate privileges to some of the highest levels available on the system
- Bypass Secure Boot and other security features
- Install persistent and stealthy malware
- Modify system configurations
- Access protected memory regions
The Palo Alto PA-3260 uses a UEFI/BIOS from Insyde Software called InsydeH20. The version in use on the appliance contains 6 previously disclosed vulnerabilities, most relating to SMM code:
| CVE Identifier | Description | CVSS |
| CVE-2022-24030 | An out-of-bounds write vulnerability in Siemens InsydeH2O | 7.5 (High) |
| CVE-2021-45970 | A vulnerability in the IdeBusDxe component affecting HP enterprise products | 8.2 (High) |
| CVE-2021-43323 | An SMM callout vulnerability in UsbCoreDxe in InsydeH2O allowing privilege escalation to SMM | 8.2 (High) |
| CVE-2021-42554 | An SMM memory corruption vulnerability in FvbServicesRuntimeDxe in InsydeH2O allowing privilege escalation to SMM | 8.2 (High) |
| CVE-2021-42060 | An Int15ServiceSmm SMM callout vulnerability in Insyde InsydeH2O allowing privilege escalation to SMM | 8.2 (High) |
| CVE-2021-33627 | A vulnerability in Insyde InsydeH2O affecting FwBlockServiceSmm, allowing potential arbitrary code execution | 8.2 (High) |
Even if the device was configured with Secure Boot enabled (and configured properly) and the GRUB bootloader was updated to patch the BootHole vulnerabilities, attackers with high privileges on the system could exploit the vulnerabilities listed above to bypass Secure Boot and various other security protections and implant malware early in the boot process.
LogoFAIL Vulnerability
Affected Platforms: PA-3260
LogoFAIL is a set of critical vulnerabilities discovered in UEFI code that affects various independent firmware/BIOS vendors (IBVs) and numerous device manufacturers. These vulnerabilities stem from flaws in image parsing libraries embedded in the firmware, which are used to display logos during the boot process. Exploitation occurs in the Driver Execution Environment (DXE), a very early stage of the boot process, allowing arbitrary code execution before the operating system and security agents load, allowing for much of the same attacks described above.
PixieFail Vulnerability
Affected Platforms: PA-1410, PA-415
We described the PixieFail vulnerability in detail in the post titled Understanding & Detecting PixieFail UEFI Vulnerabilities. Several vulnerabilities in the DHCPv6 implementation in UEFI were discovered, with the following impact:
“The vulnerabilities affect the network boot process in the PXE environment, which is essential for loading operating systems from the network at boot time. All discovered vulnerabilities are within the DHCPv6 functionality as PXE relies on DHCP at boot time to obtain an IP address and discover the location of the OS image to load…The PixieFail vulnerabilities are notable because they allow remote-code execution (RCE) given the attacker is on the same network.”
Insecure Flash Access Control Vulnerability
Affected Platforms: PA-415
The PA-415 has misconfigured SPI flash access controls, which could allow an attacker to modify UEFI directly and bypass other security mechanisms. More information about this misconfiguration can be found in our post titled Firmware Security Realizations – Part 3 – SPI Write Protections.
TPM Vulnerability
Affected Platforms: PA-415
This vulnerability was discovered by Quarkslabs in Feburary 2023 and Proof-Of-Concept exploit code was published along with the research.
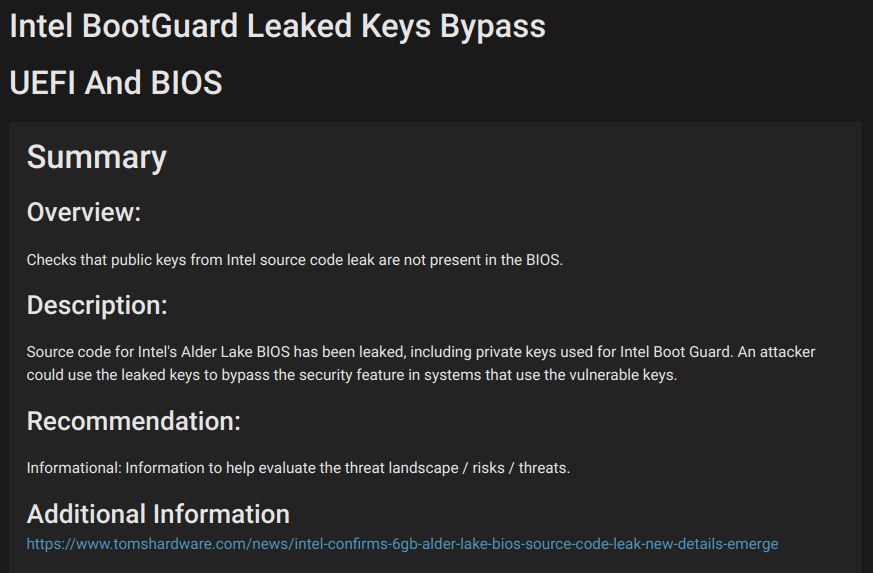
Intel Bootguard Leaked Keys Bypass
Affected Platforms: PA-1410
Conclusion
The security landscape for network appliances is far more complex and vulnerable than many organizations realize. Our examination of Palo Alto Networks appliances reveals various security gaps, from vulnerabilities to evade Secure Boot to multiple instances of unpatched firmware. These findings underscore a critical truth: even devices designed to protect can become vectors for attack if not properly secured and maintained. As threat actors continue to target security appliances, organizations must adopt a more comprehensive approach to supply chain security. This includes rigorous vendor assessments, regular firmware updates, and continuous device integrity monitoring. By understanding and addressing these hidden vulnerabilities, organizations can better protect their networks and data from sophisticated attacks that exploit the very tools meant to safeguard them. In today’s evolving threat landscape, visibility at every level of the technology stack is not just advisable—it’s essential.
Disclosure Timeline
- December 16, 2024 – Initial disclosure to PANW.
- December 18, 2024 – Response from PANW PSIRT: “We are currently triaging the report and will reach out to you once we complete the triage.”
- January 6, 2025 – Eclypsium contacted PANW PSIRT for an update.
- January 7, 2025 – Response from PANW: “We investigated your report and have forwarded it to our product team for further analysis.”
- January 22, 2025 – Request from PANW to wait until PANW has a patch for the affected appliances. No timeline given other than stating Eclypsium will be kept up-to-date on patch availability.






