The Edge Case That Became the Main Event
Network edge devices such as routers, switches, firewalls, VPNs, and access points are being targeted by waves of cyberattacks. The RedNovember attack campaign disclosed by RecordedFuture’s Insikt Group is the latest in a string of campaigns targeting SonicWall, Cisco, Palo Alto, Fortinet, and Ivanti devices inside government, defense, and technology companies.
These devices are critical IT infrastructure, but they’re challenging to protect against attackers. Firewalls and routers typically can’t have endpoint detection and response (EDR) agents installed on them. Vulnerability management tools only offer limited visibility into the firmware and hardware internals of these network edge devices. Furthermore, these devices are often running firmware from three years ago, default credentials, or worse – nobody even knows what firmware version they’re running.
The RedNovember actors understand this perfectly. Rather than trying to break through increasingly sophisticated endpoint protection or cloud security controls, they go after the foundation itself. If bank robbers rob banks because that’s where the money is, today’s cyberattackers target network edge devices “because that’s where the access is.”
What makes all of this particularly insidious is the persistence factor. By compromising network devices, especially at the firmware and hardware component level, attackers establish a beachhead that survives reboots, updates, and even some security sweeps. It’s the difference between breaking into someone’s house and actually changing the locks.
RedNovember’s Playbook: A Case Study in Infrastructure Exploitation
The tactics, techniques, and procedures used by the RedNovember campaign over time demonstrate increased targeting of network edge devices, and increased usage of vulnerability exploitation, often beginning quickly after new vulnerabilities and exploits are disclosed. Insikt Group’s writeup of the campaign specifically noted this increased edge device targeting:
“RedNovember has increasingly focused its initial access efforts on targeting edge devices, including security solutions such as VPNs, firewalls, load balancers, virtualization infrastructure, and email servers.”
RedNovember is not alone in their shift toward targeting network edge devices. The Verizon Data Breach Investigation Report for 2025 indicated a 34% increase in vulnerability exploitation for initial access, and an 8x increase in network edge vulnerability exploitation specifically. The 2025 Mandiant M-Trends report said that 21% of ransomware attacks they responded to featured vulnerability exploitation as the initial access vector.
Insikt Group also noted:
“RedNovember’s activity exemplifies the ability to combine weaponized proof-of-concept (PoC) exploits with open-source post-exploitation frameworks such as Pantegana, lowering the entry barrier for less-capable threat actors.”
The pattern of once-sophisticated attack techniques becoming commoditized and accessible to less advanced attackers is concerning because it means any run-of-the-mill ransomware group could soon use the same stealthy tactics as a nation-state APT. This pattern was reinforced by the recent disclosure of HybridPetya, a ransomware with a built-in UEFI bootkit, bringing ransomware firmly into the realm of firmware-targeting that used to be reserved for more advanced attacks.
When even less-sophisticated attack groups can compromise the very infrastructure that your security controls depend on, all bets are off.
The RedNovember campaign demonstrates several other concerning trends that we’re seeing across the threat landscape:
Persistence Through Firmware: By targeting low-level system components, these attackers achieved the kind of persistence that keeps incident response teams up at night. Even if you think you’ve eradicated an attacker’s presence, compromised firmware can provide a pathway back in. In the case of network devices, the pre-installed operating system behaves like firmware in that it is not user-facing and is minimally visible to the end user, making it challenging to protect.
Supply Chain Implications: Network edge devices are inhospitable to EDR agents, so buyers are forced to trust their vendors that the devices are secure. Unfortunately, RedNovember and countless other recent attacks show that these devices contain vulnerabilities that can and will be exploited. Furthermore, when network edge devices are compromised, they can expose everything else they’re connected to. Traffic interception, credential harvesting, lateral movement – the possibilities are extensive and deeply concerning.
Detection Evasion: Traditional network monitoring tools are designed to detect suspicious traffic patterns, not compromised infrastructure. Endpoint agents and vulnerability managers can’t see deeply enough into edge devices to know if they’ve been hacked. When the infrastructure itself is the attack vector, conventional detection methods fall short.
The Human Factor: Let’s be honest – network edge devices often receive less attention than they deserve. They’re managed by different teams, updated on different schedules, and monitored with different tools. This organizational complexity creates security gaps that sophisticated threat actors are happy to exploit.
The Firmware Frontier: Where Visibility Goes to Die
Here’s where things get really interesting from a security perspective. Most organizations have pretty good visibility into their endpoints, decent logging from their applications, and increasingly sophisticated monitoring of their cloud environments. But ask them what’s running on the firmware of their edge devices? Crickets.
This visibility gap is a fundamental blind spot that threat actors like RedNovember are exploiting systematically. Traditional security tools simply weren’t designed to peer into the firmware layer of network infrastructure. It’s like trying to secure a building while ignoring the foundation it’s built on.
For more info on cyberattacks targeting firmware, read our ebook: The Top Five Firmware and Hardware Attack Vectors
Beyond Reactive Security: The Infrastructure Integrity Imperative
The most effective security strategies are proactive, not reactive. By the time you’re detecting malicious activity from compromised network edge devices, you’re already playing catch-up.
This is where the concept of infrastructure integrity becomes critical. It’s not enough to assume your network devices are trustworthy. You need continuous verification. Every piece of code running on every device in your infrastructure should be known, validated, and monitored for changes.
The challenge, of course, is scale. Modern organizations deploy thousands of network edge devices across multiple locations, vendors, and configurations. Manual verification is impractical. Automated verification is not yet widely deployed. That needs to change.
Practical Recommendations: Securing the Edge
For security professionals and IT administrators dealing with the reality of network edge security, here are some actionable steps:
Inventory Everything: You can’t secure what you can’t see. Maintain comprehensive inventories of all network edge devices, including firmware versions, configuration baselines, and update schedules.
Implement Continuous Monitoring: Periodic scans aren’t sufficient for critical infrastructure. Deploy solutions that provide real-time visibility into firmware integrity and detect unauthorized changes as they occur.
Establish Firmware Hygiene: Develop processes for timely firmware updates, but balance this with integrity verification. Not all firmware updates are created equal, and supply chain compromises can occur at any stage.
Assume Compromise: Design your network architecture with the assumption that edge devices might be compromised. Implement additional layers of monitoring and control that don’t depend solely on the integrity of edge infrastructure.
Cross-Team Collaboration: Break down the silos between network operations, security teams, and infrastructure management. Edge device security requires coordinated effort across multiple disciplines.
Eclypsium’s Approach: Continuous Hardware and Firmware Security
This is precisely the problem that Eclypsium was built to solve. Our platform provides visibility into the dusty corners of IT infrastructure that traditional security tools miss. We’re talking about continuous monitoring of firmware and hardware layers in the network edge devices that campaigns like RedNovember target.
What sets our approach apart is the comprehensiveness of the coverage. We beyond the table stakes features of scanning for known vulnerabilities or firmware versions. We also provide ongoing integrity verification for firmware, BIOS, UEFI, and other low-level components. When something changes that shouldn’t, or when we detect indicators of compromise at the firmware level, our platform alerts security teams before the attack can progress.
Eclypsium’s network edge device coverage is particularly robust. We can inventory firmware versions, detect unauthorized modifications, and identify potential supply chain compromises across a wide range of network infrastructure vendors. It’s like having X-ray vision for your network’s foundation. Eclypsium offers robust coverage of the exact devices and systems targeted by RedNovember, including Cisco ASA, SonicWall, Ivanti VPNs, Palo Alto GlobalProtect systems, and more. Here are a few examples of Eclypsium detections of known vulnerabilities and indicators of compromise:
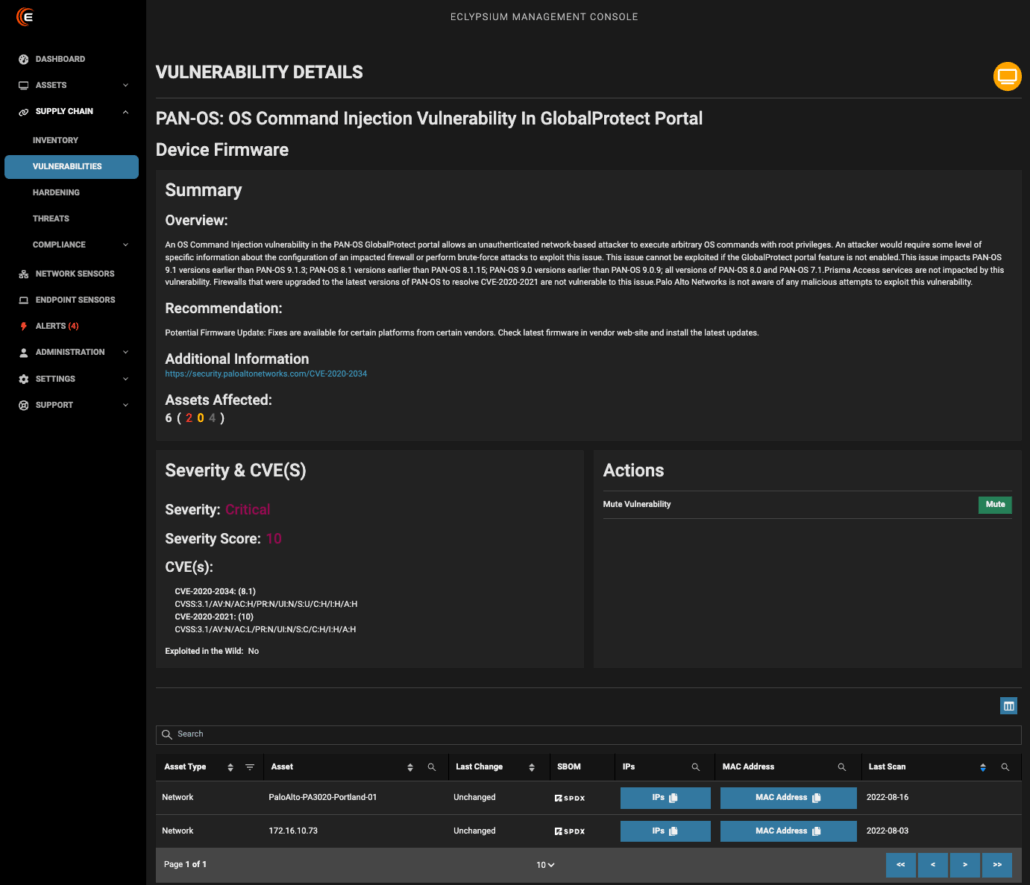
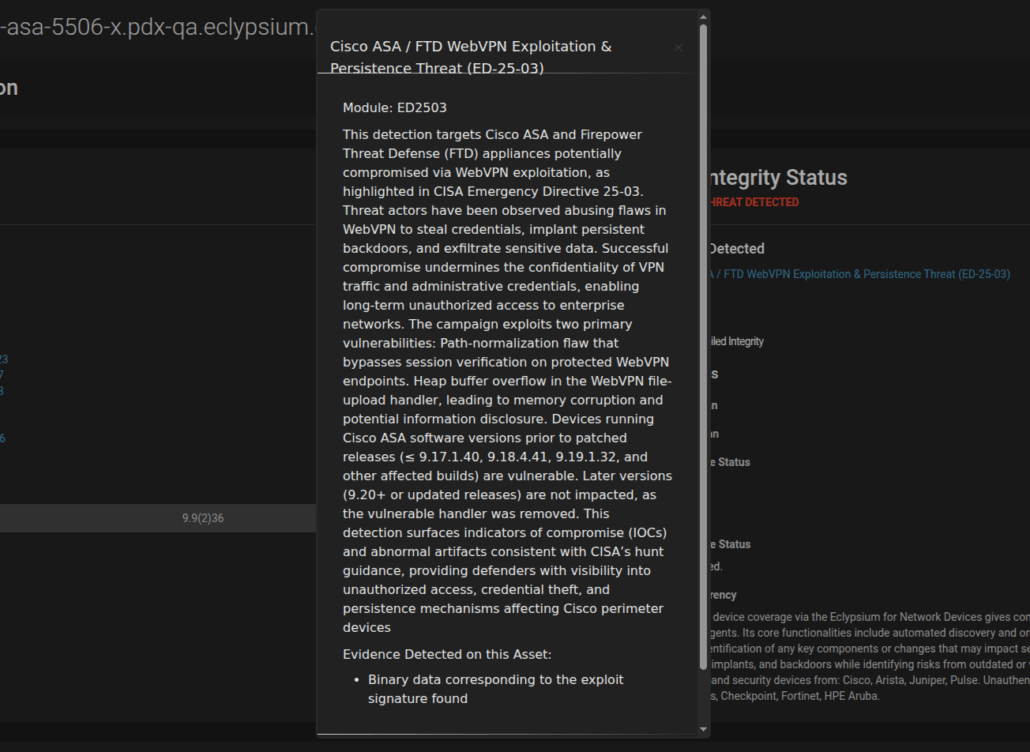
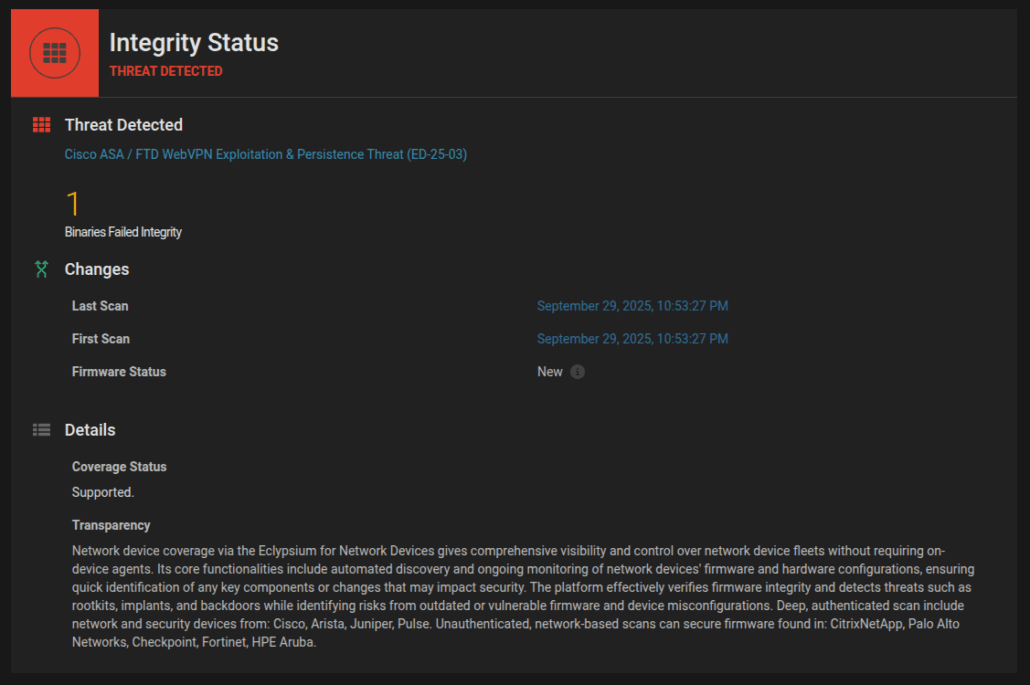
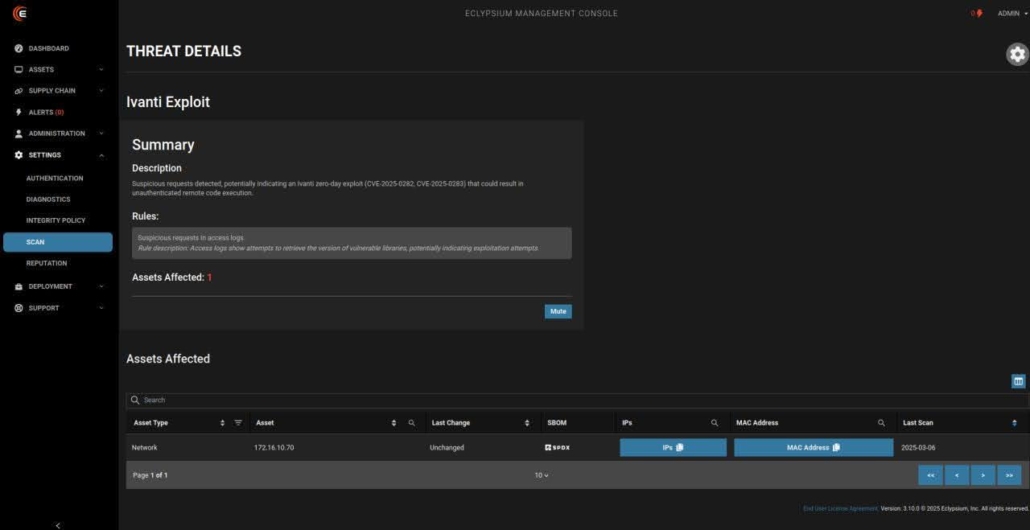
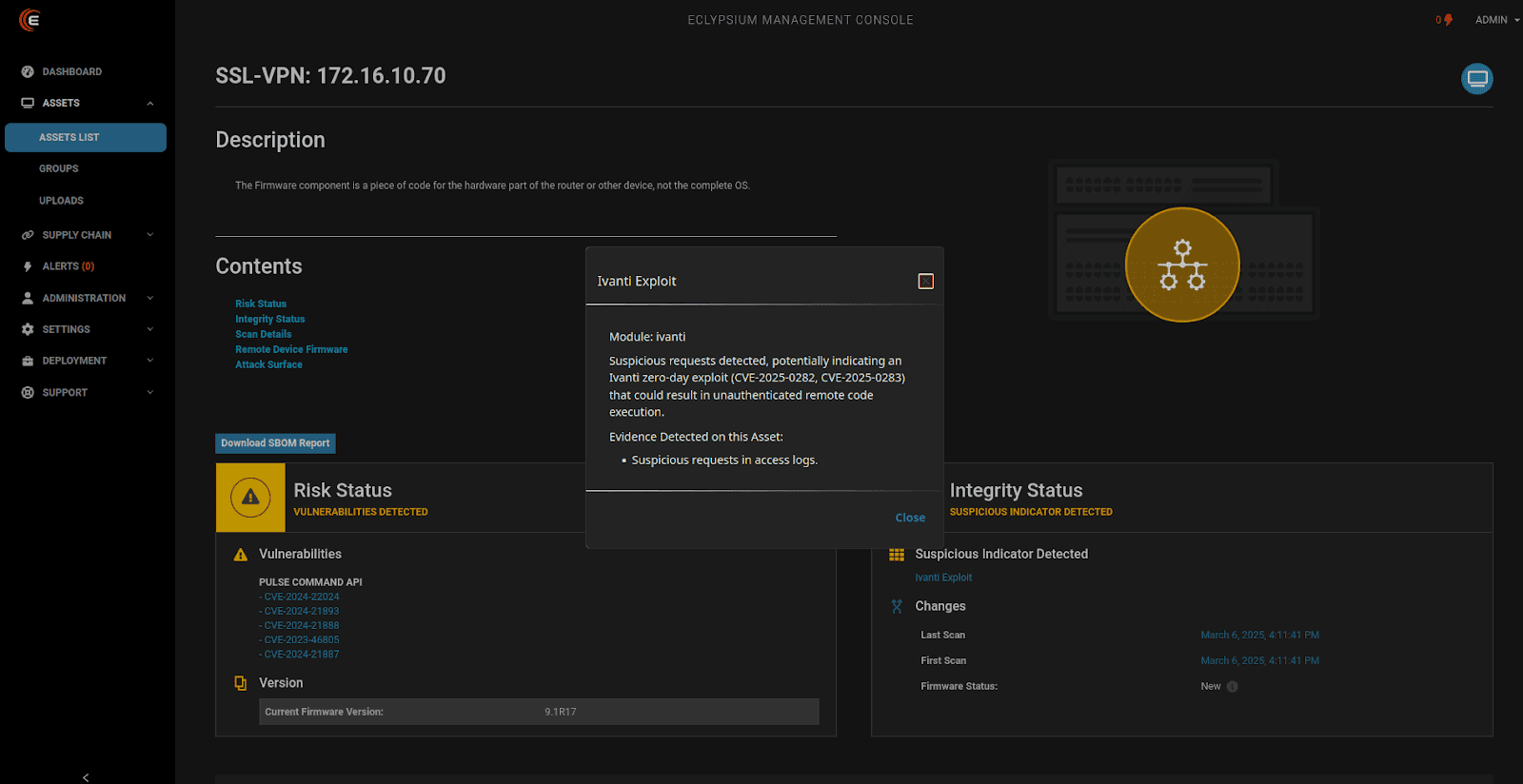
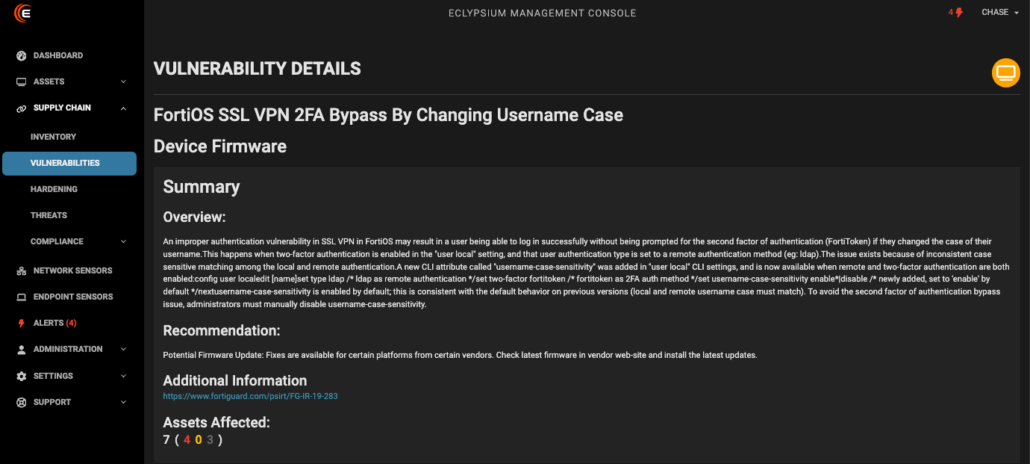
Infrastructure Security Is A Strategic Imperative
The RedNovember campaign should serve as a wake-up call for organizations that have been treating network edge security as an afterthought. In an era where threat actors are increasingly sophisticated and persistent, we can’t afford to ignore any component of our attack surface – especially the foundational infrastructure that everything else depends on.
The question isn’t whether your network edge devices will be targeted – it’s whether you’ll have the visibility and controls in place to detect and respond when they are. In the immortal words of Yoda, “Do or do not, there is no try” – and when it comes to infrastructure security, partial coverage is often no coverage at all.
The path forward requires a fundamental shift in how we think about security architecture. It’s not enough to secure the applications and data – we need to secure the entire stack, from silicon to software. Because as RedNovember has clearly demonstrated, when threat actors control your infrastructure, they control everything that runs on top of it.
To learn how Eclypsium can discover and mitigate against threats targeting network infrastructure visit our network vulnerability scanner page or take a self-guided interactive product tour on hardening your IT infrastructure.






