© 2025 Eclypsium, Inc.
Meet CJIS Security Requirements for Law Enforcement Agencies_
Law enforcement agencies are prime targets for cybercriminals, and the FBI emphasizes that monitoring and updating firmware is a critical component of CJIS compliance. Eclypsium is the only platform that continuously monitors firmware security and integrity in real-time, using a unique database of over 12 million known-good hashes to identify risk and protect law enforcement IT infrastructure against sophisticated attacks.
- Continuously monitor firmware for CJIS compliance
- Detect indicators of attack in criminal justice networks
- Automatically update firmware to maintain security standards
- Rapidly generate CJIS Compliance Reports to demonstrate compliance or identify gaps.
Request A Demo
TRUSTED BY LEADING ENTERPRISES
Protect Criminal Justice Systems from Sophisticated Firmware Attacks_
Traditional security tools, endpoint protection platforms, vendor monitoring, and intrusion detection systems fall short at the firmware level. To maintain CJIS compliance and protect against evolving threats, you need deeper visibility. Eclypsium is the only enterprise-ready firmware security solution that can inventory and monitor the hardware and firmware at the foundation of your criminal justice information systems, where sophisticated attackers establish persistence.
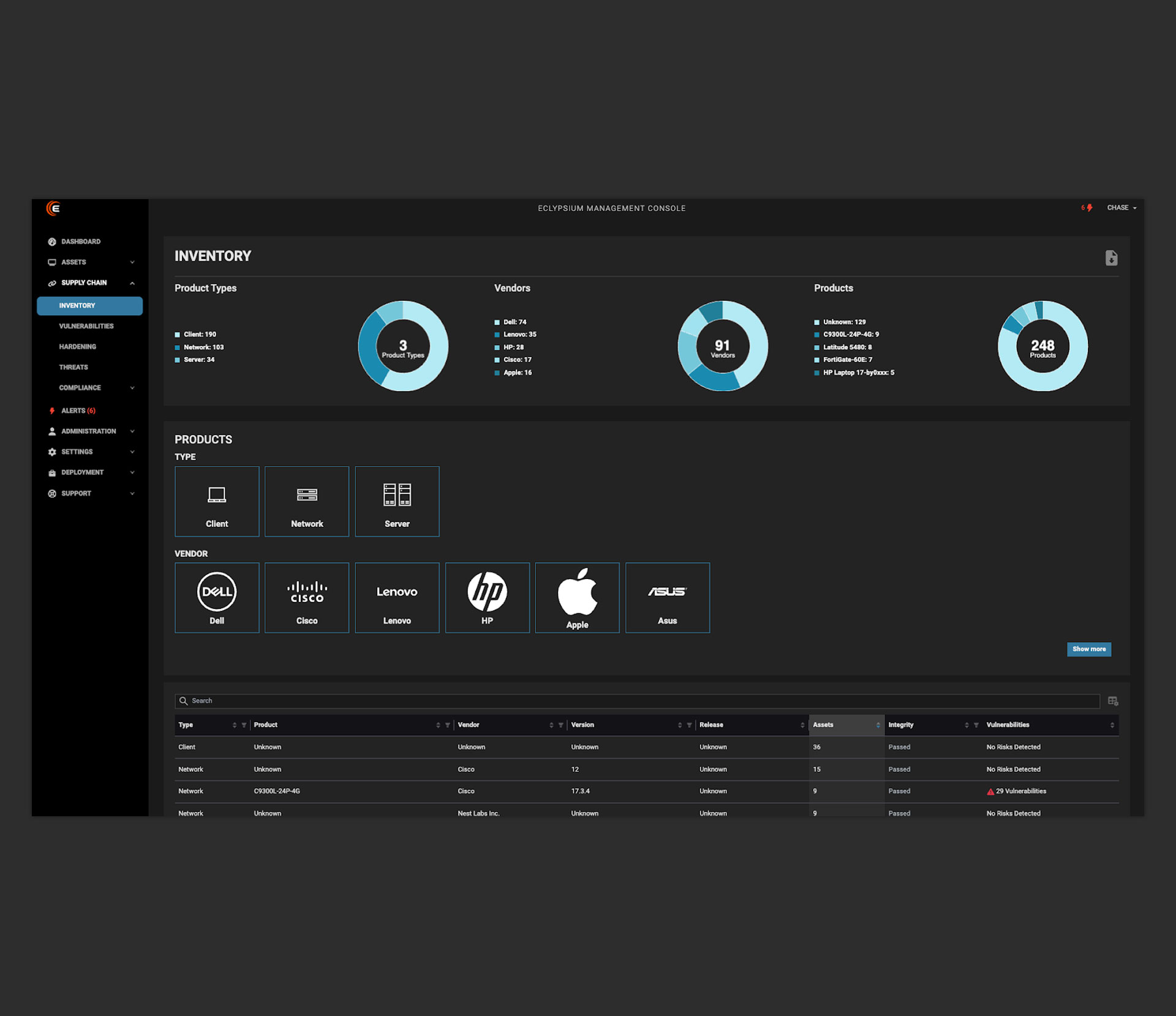
Identify and Inventory
You get a complete inventory of devices in your environment and the firmware versions they’re running, and whether they meet CJIS compliance standards or require immediate remediation.
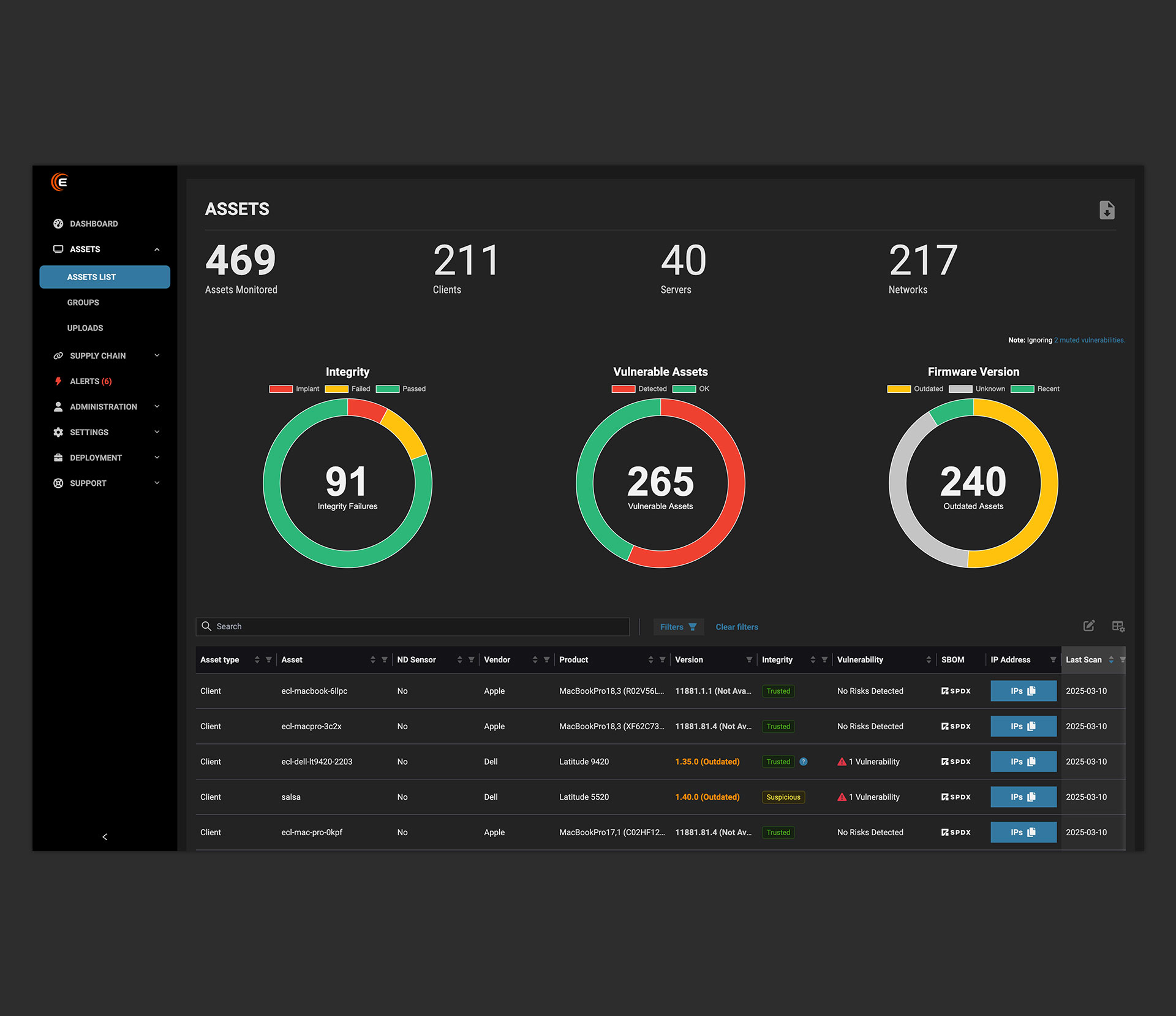
Verify and Validate
You get confirmation that your devices haven’t been compromised or tampered with, ensuring foundational security of devices handling sensitive criminal justice data.
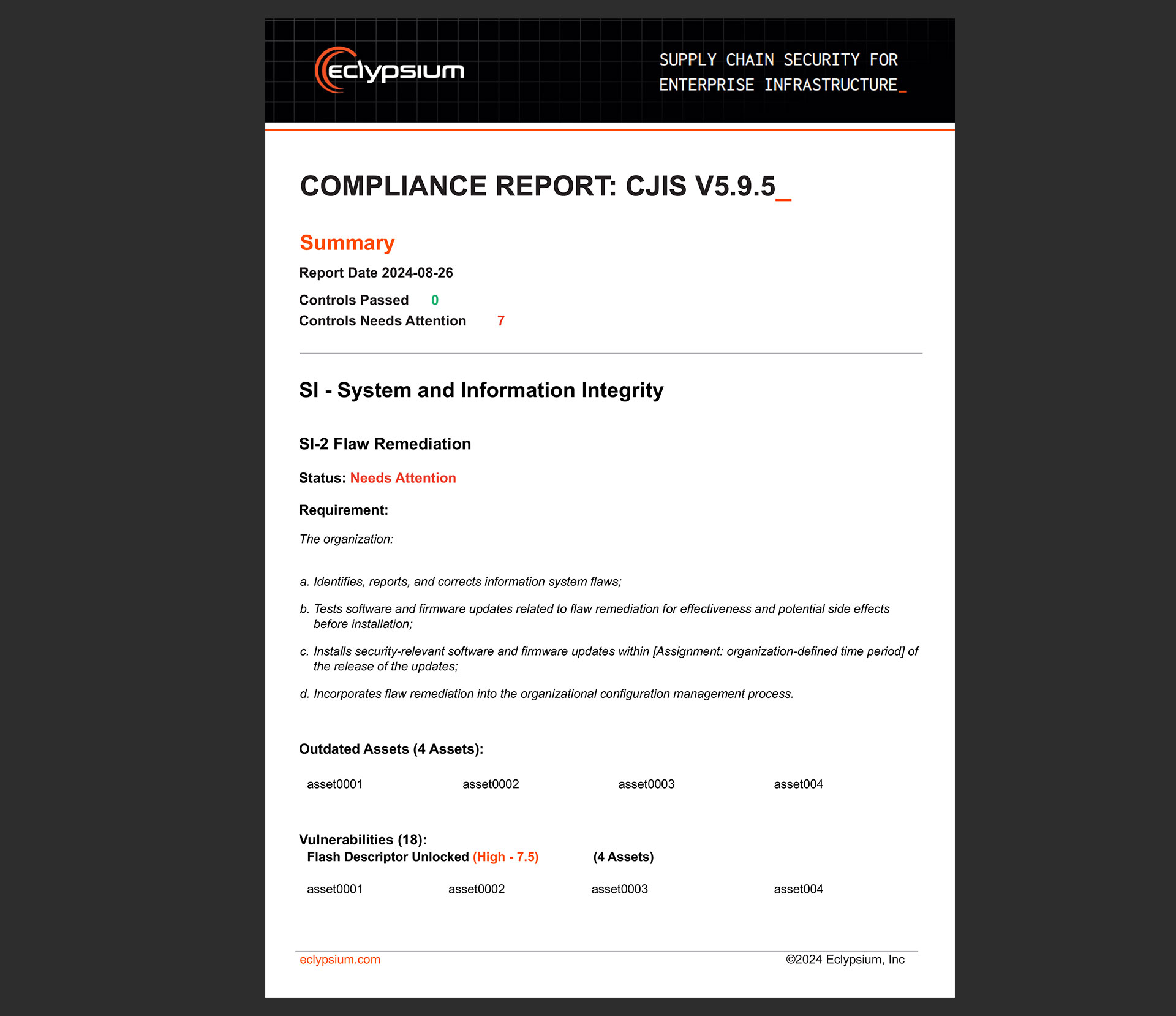
Generate CJIS Compliance Reports On The Fly
Assess device-level configuration and CJIS compliance. Maintain secure operations and extend device lifespan by remotely patching or updating vulnerable infrastructure code.
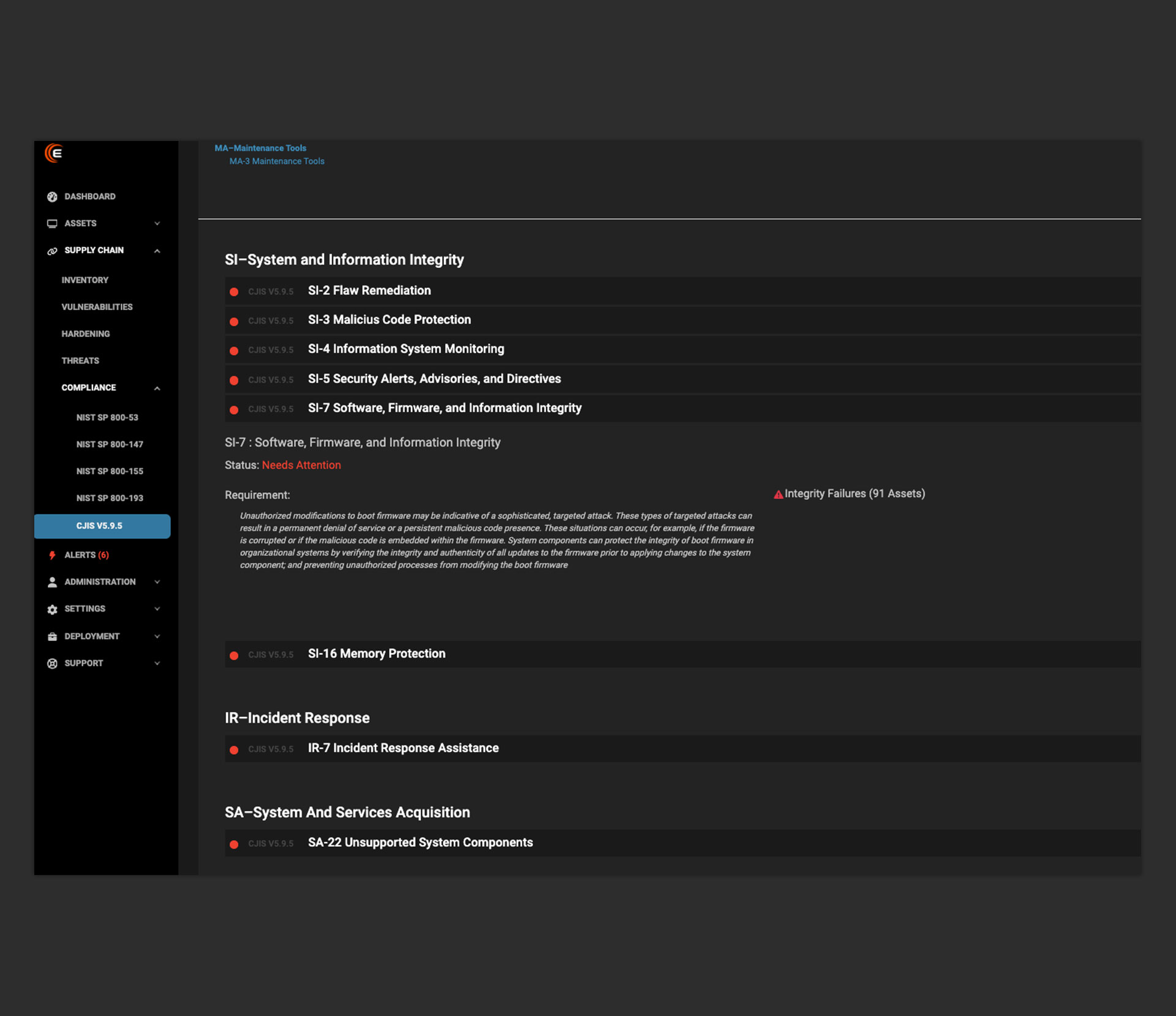
Continuously Monitor Firmware Baselines
Eclypsium continuously monitors software, firmware, and information integrity as required in SI-2, SI-3, SI-4, SI-5, SI-7, and SI-16 sections of CJIS.