© 2025 Eclypsium, Inc.
Fulfill NCUA Firmware Security Requirements for Credit Unions_
Credit unions are a target for cyberattackers, and the FFIEC notes that monitoring and updating firmware is a necessary step to staying protected. Eclypsium is the only platform that monitors firmware security and integrity in real-time, using a unique database over 12 million known-good hashes to identify risk and protect credit unions from stealthy attacks.
- Continuously monitor firmware for vulnerabilities
- Detect indicators of attack in network infrastructure
- Automatically update firmware to stay secure
- Catch advanced threats living off the land
Request A Demo
TRUSTED BY LEADING ENTERPRISES
Protect Credit Unions from Growing Firmware Attacks_
Traditional vulnerability scanners, endpoint monitors, manufacturer monitoring, and security tools stop in the shallow end. To protect against evolving threats, you need to go deeper. Eclypsium is the only enterprise-ready firmware security solution that can inventory and monitor the hardware and firmware at the foundation of your IT infrastructure, where attackers hide until they can strike again.
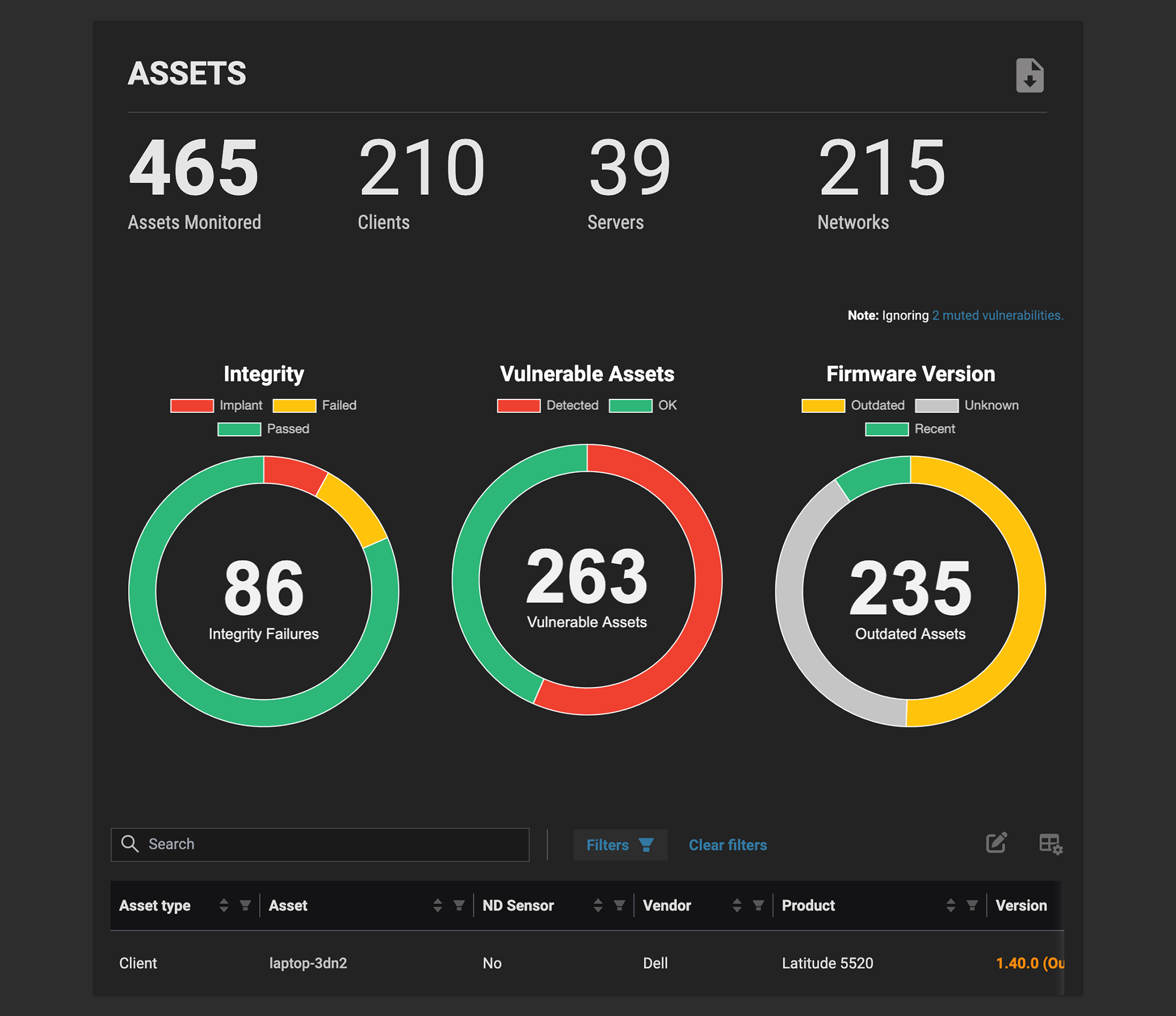
Identify and Inventory
You get a complete inventory of devices in your environment and the firmware versions they’re running, and whether they’re current and secure or outdated and misconfigured.
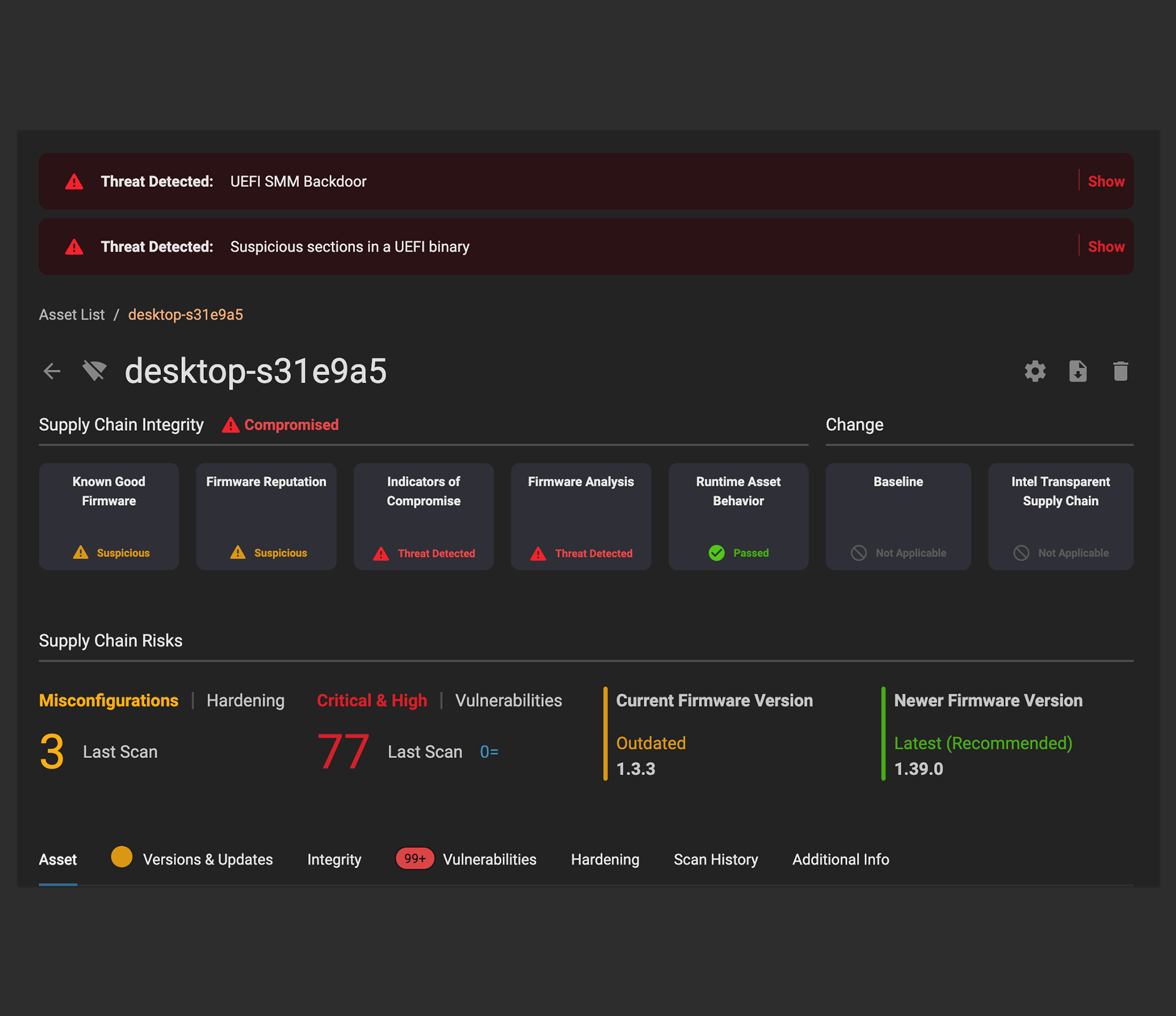
Verify and Validate
You get confirmation that your devices haven’t been compromised or tampered with, and are free of implants and backdoors.
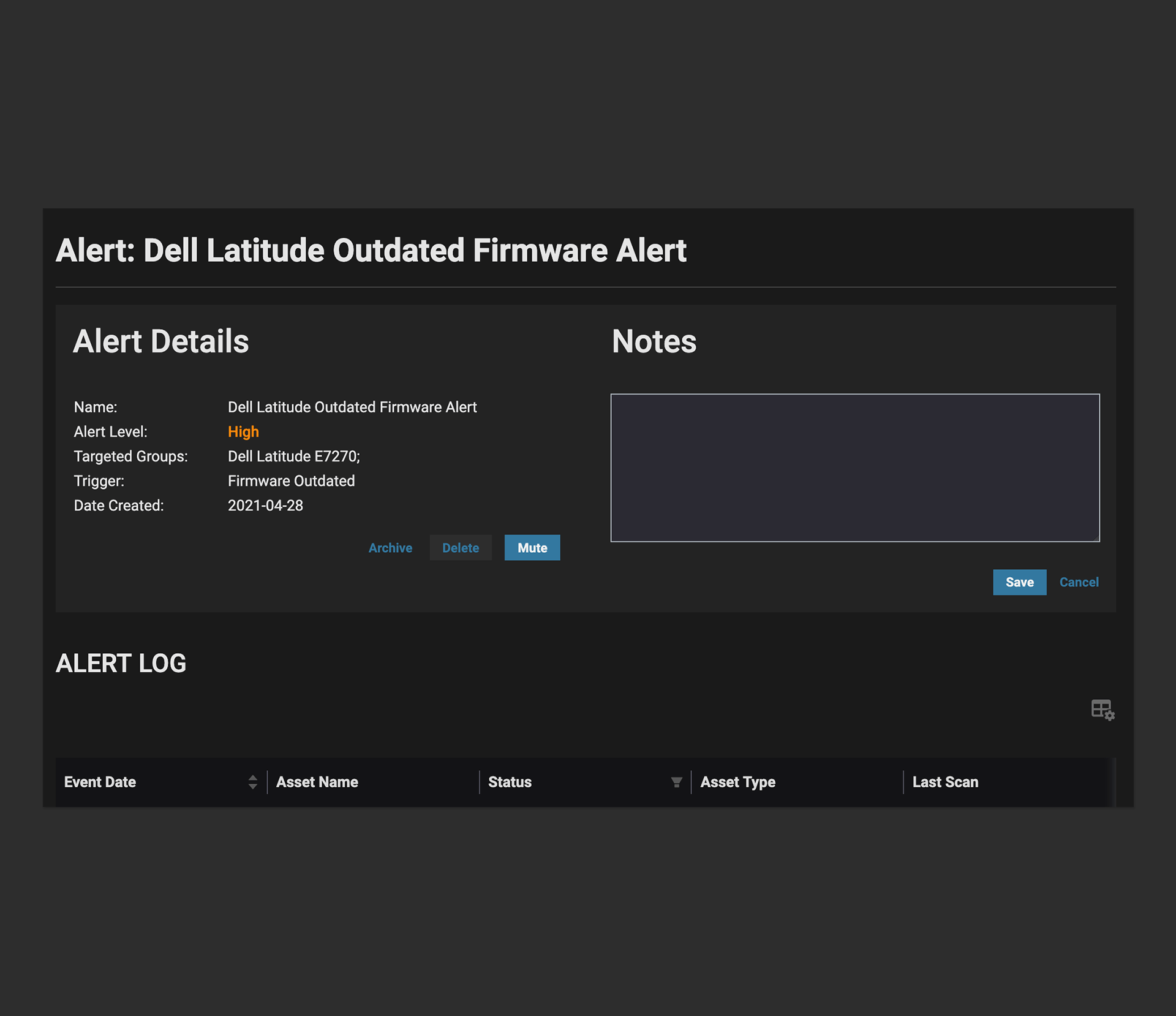
Fortify and Harden
Assess device-level configuration and compliance. Keep devices secure and extend their lifespan by remotely patching or updating out-of-date or vulnerable infrastructure code.
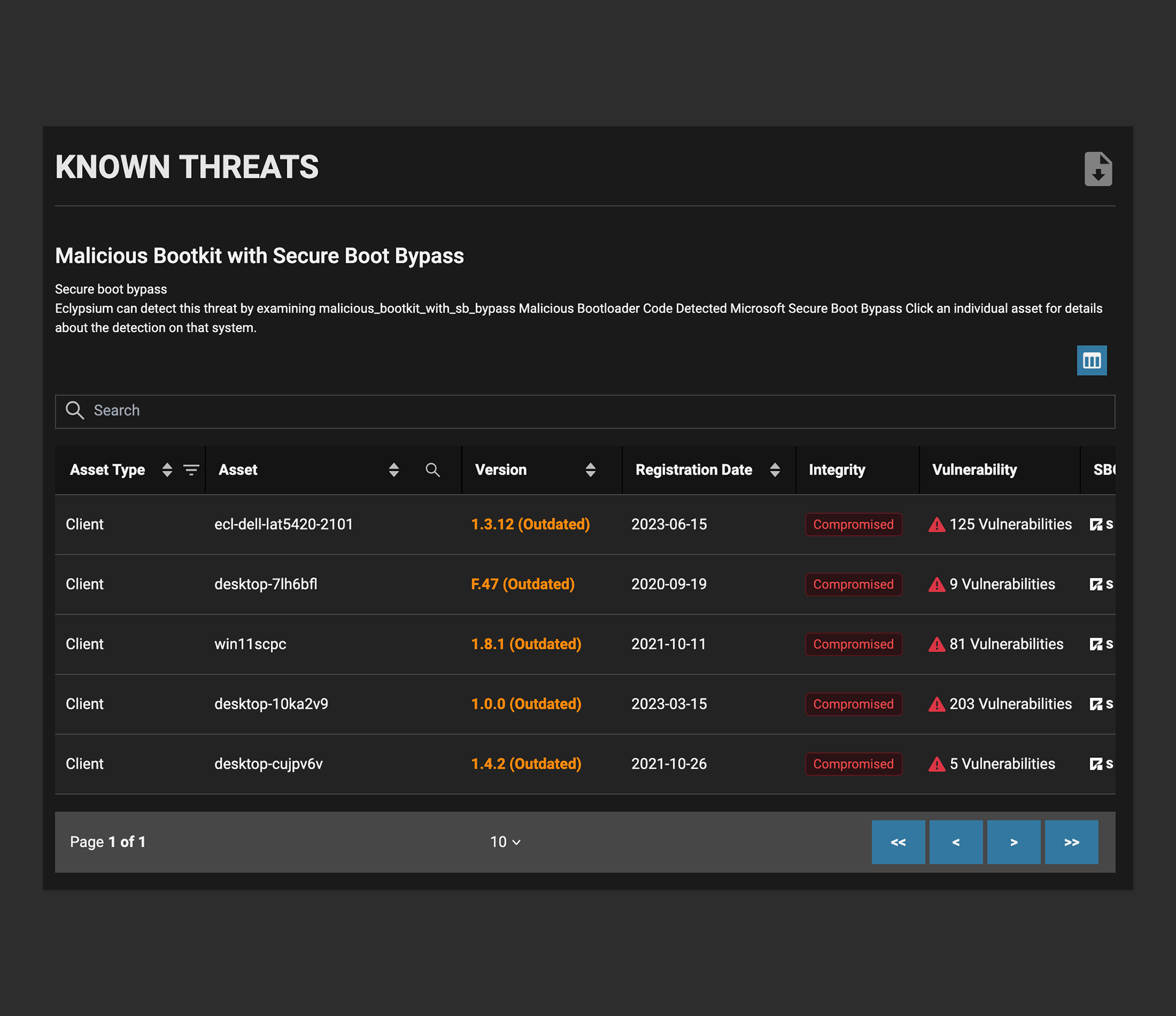
Detect Known and Unknown Threats
Catch malicious implants and backdoors, attacker indicators of compromise, and unpatched vulnerabilities for a comprehensive view of risk in your IT infrastructure.