Demo
Book a Live Demo
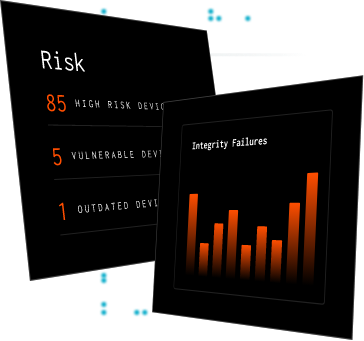
Discover security that goes below the OS_
When work happens everywhere, enterprise teams need to know that each asset is secure, reliable, and ready for anything.
The simple solution to a complicated problem.
Trust every asset, each step of your digital supply chain, and line of your infrastructure’s code, so you can more effectively prioritize the responsibilities that move your business forward.