© 2025 Eclypsium, Inc.
Advanced Network Vulnerability Scanner_
Go beyond traditional vulnerability scanners. Detect vulnerabilities and active attacks against network devices, firmware, and infrastructure that EDR can’t see. Protect against ransomware and APT attacks targeting your VPNs, firewalls, routers, and switches.
Request A Demo
TRUSTED BY LEADING ENTERPRISES
22% of Breaches
now involve network device exploitation (up from 3% in 2024)
32 Days to Remediate
Median time to fix network device vulnerabilitie
Over 1 Year
Chinese APTs hid out inside National Guard network systems after exploiting network router and firewall vulnerabilities
Network Devices Are Under Attack_
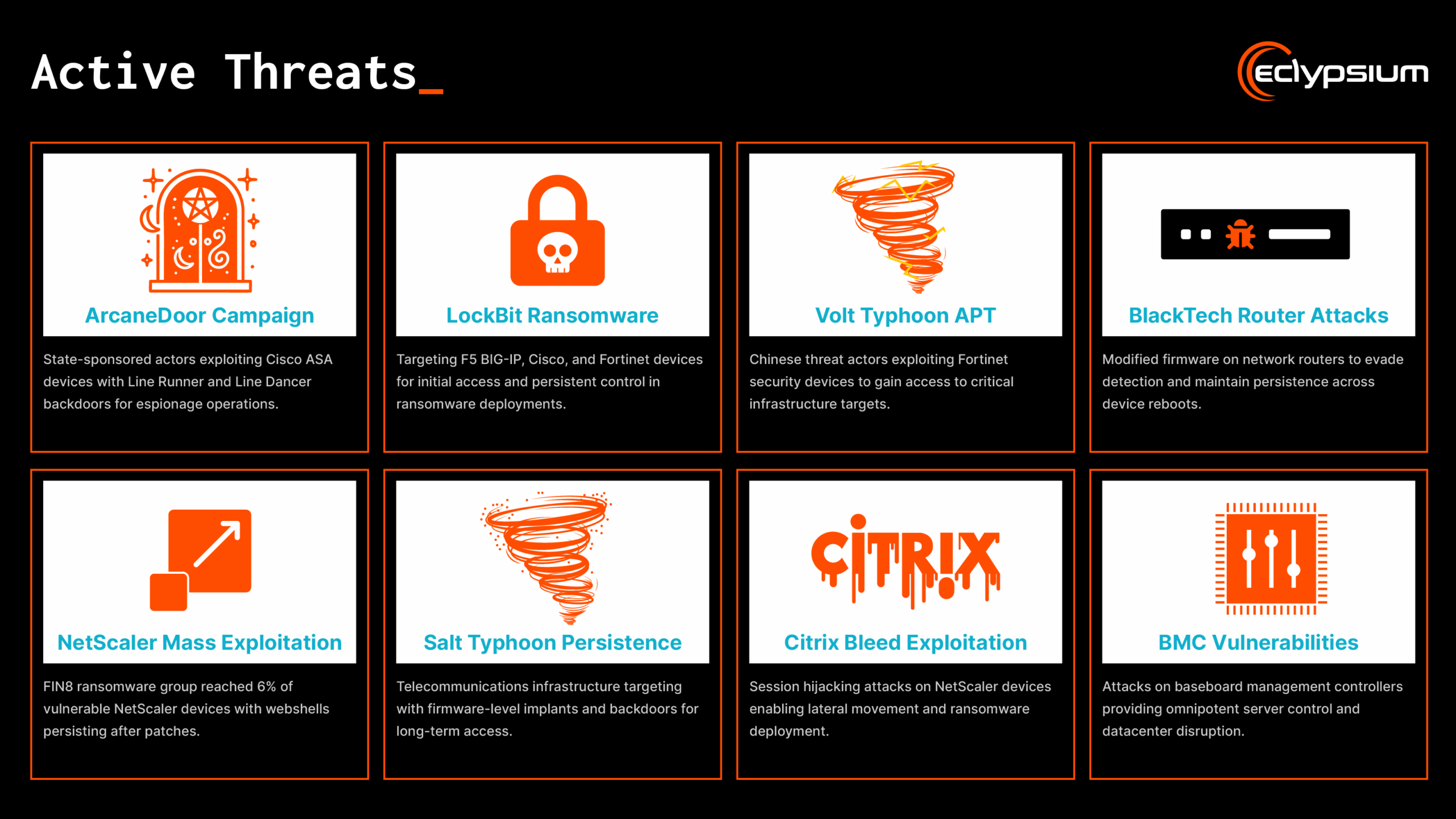
Ransomware groups like LockBit, CACTUS, Akira, and state-sponsored threat actors including Volt Typhoon, BlackTech, and Salt Typhoon are increasingly targeting network infrastructure as their primary attack vector.
Traditional Scanners Miss Critical Threats: Network vulnerability scanners focus on software-level issues but miss firmware vulnerabilities, device misconfigurations, and embedded threats that attackers use to establish persistent access.
No EDR Protection for Network Devices VPNs, firewalls, routers, and switches don’t support traditional endpoint security tools, leaving them as blind spots in your security program while providing attackers unfettered network access.
Complex Supply Chains Create Risk Network devices contain over 100 internal components from multiple suppliers. Each component can harbor vulnerabilities that attackers exploit to compromise devices before they’re even deployed.
Zero Trust Depends on Device Integrity: Your Zero Trust architecture relies on network devices to enforce policies and analyze traffic. If these foundational devices are compromised, your entire security framework becomes vulnerable.
The Solution: Eclypsium Supply Chain Security Platform_
The only network vulnerability scanner that provides complete visibility into network device firmware, hardware, and software components. Detect threats that traditional scanners and EDR solutions miss.
Deep Device Scanning: Scan firmware, BIOS, BMCs, and embedded components in network devices from Cisco, F5, Fortinet, NetScaler, Juniper, and more. Identify vulnerabilities at levels traditional scanners can’t reach.
Integrity Monitoring: Continuously verify device firmware integrity through cryptographic comparison with vendor-published code. Detect unauthorized changes, backdoors, and persistent implants.
Threat Detection: Identify indicators of compromise including modified configurations, reverse shells, persistence modules, and artifacts from known threat actors like ArcaneDoor, Line Dancer, and Salt Typhoon.
Risk Prioritization: Focus on vulnerabilities actively exploited in the wild. Automatically prioritize CVEs on CISA’s Known Exploited Vulnerabilities list and those used by ransomware groups.
Automated Remediation: Streamline firmware updates with automated checking, downloading, and verification of patches. Reduce manual effort while maintaining device security posture.
Protect Against Active Threats_
The Eclypsium platform detects and protects against the latest network device threats observed in the wild.