On 21 June 2022, OpenSSL version 3.0.4 introduced a severe bug (CVE-2022-2274) in the RSA implementation for X86_64 CPUs supporting AVX512IFMA instructions. This allowed for memory corruption on RSA implementations running 2048-bit private keys. An attacker could then perform RCE (Remote Code Execution) over the network against SSL/TLS and other OpenSSL servers that support x86_64 AVX512IFMA instructions.
Fortunately for owners of SSL/TLS servers, this issue has since been patched on 5 July 2022, in version 3.0.5 of OpenSSL. As such, the maximum exposure for potential exploitation of this bug was only two weeks. Many owners had probably not even gotten around to patching their version 3.0.3 (or prior) versions. With no known proof of concept code or attacks in the wild, it is reasonable to say that this vulnerability, while receiving much initial attention (including an alert put out by CISA the very next day), is unlikely to see widespread exploitation.
Teams developing new implementations during this two-week window would have likely discovered this flaw on their own during normal functionality testing, as it results in a failed state readily observable by the developer or QA tester.
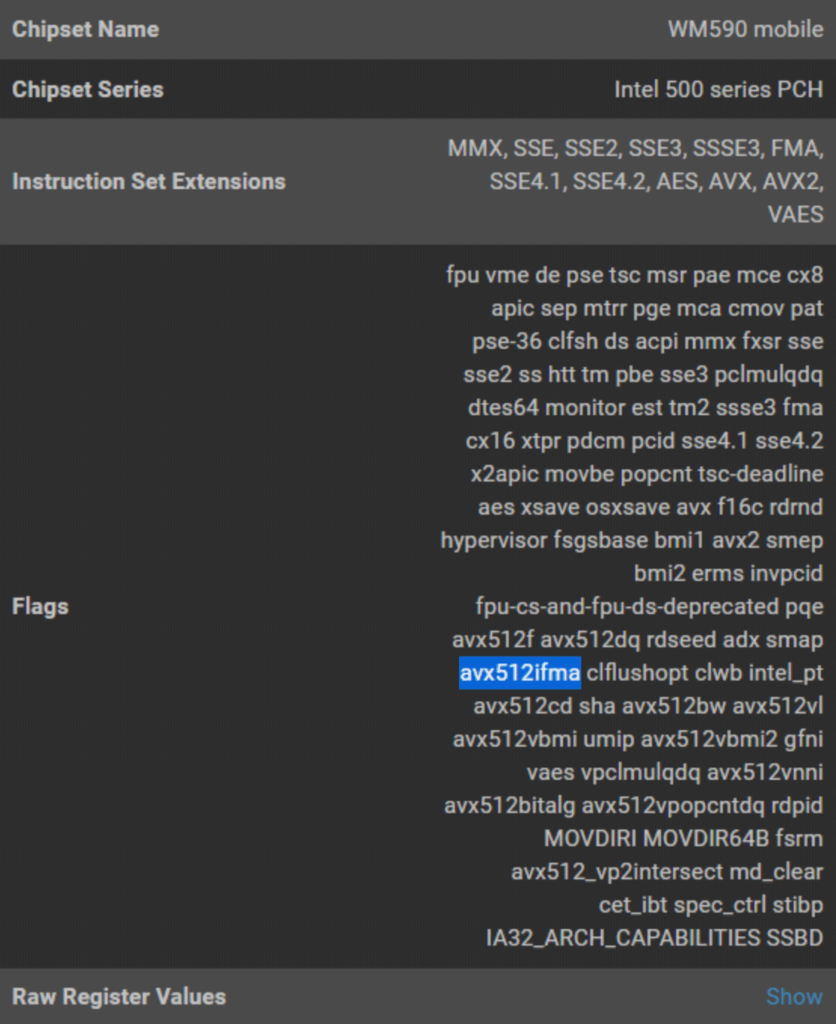
While this particular vulnerability is only associated with a single version of OpenSSL (version 3.0.4), it isn’t enough to simply inventory (via, say, a legacy vulnerability management solution), whether a TLS/SSL server is running a vulnerable version of OpenSSL. In the case of this (and other similar) vulnerabilities, the instruction set supported by the CPU is also a determining factor of exploitability. Instruction-set specific utilization is normally very difficult to assess, but Eclypsium customers enjoy a single dashboard that provides details on CPU instruction support, which can assist with prioritizing server patching.
The device component-level visibility that Eclypsium provides is uniquely designed to give enterprise and production teams the data they need to gauge the risk associated with these types of vulnerabilities.
Recommendations:
- Users of OpenSSL prior to 3.0.3 are not vulnerable to this CVE.
- Users of OpenSSL version 3.0.4 should upgrade immediately to OpenSSL 3.0.5
- To determine whether a device supports the CPU instruction set that renders a device running OpenSLL 3.0.4 vulnerable to exploitation, users can run the following commands locally:
- For Linux devices: The built-in lscpu command will list ‘avx512ifma’ under Flags (If the CPU supports it).
- For Windows devices: The opensource coreinfo.exe tool from Sysinternals can be run as follows:
- c:SI>Coreinfo.exe -f | findstr AVX-512-IFAMA
- Response will be as follows if the vulnerable instruction set is supported:
- AVX-512-IFAMA * Supports AVX-512 integer Fused multiply-add instructions
- Users can leverage CPU IDs in order to discern if a given TLS/SSL server supports AVX512IFMA instructions, and might therefore be exploitable if running OpenSSL version 3.0.4. On the Eclypsium platform, CPU instruction set support details are available at https://<your_company>/device/<device guid>/processor-info by expanding the Instruction Set Extensions panel.