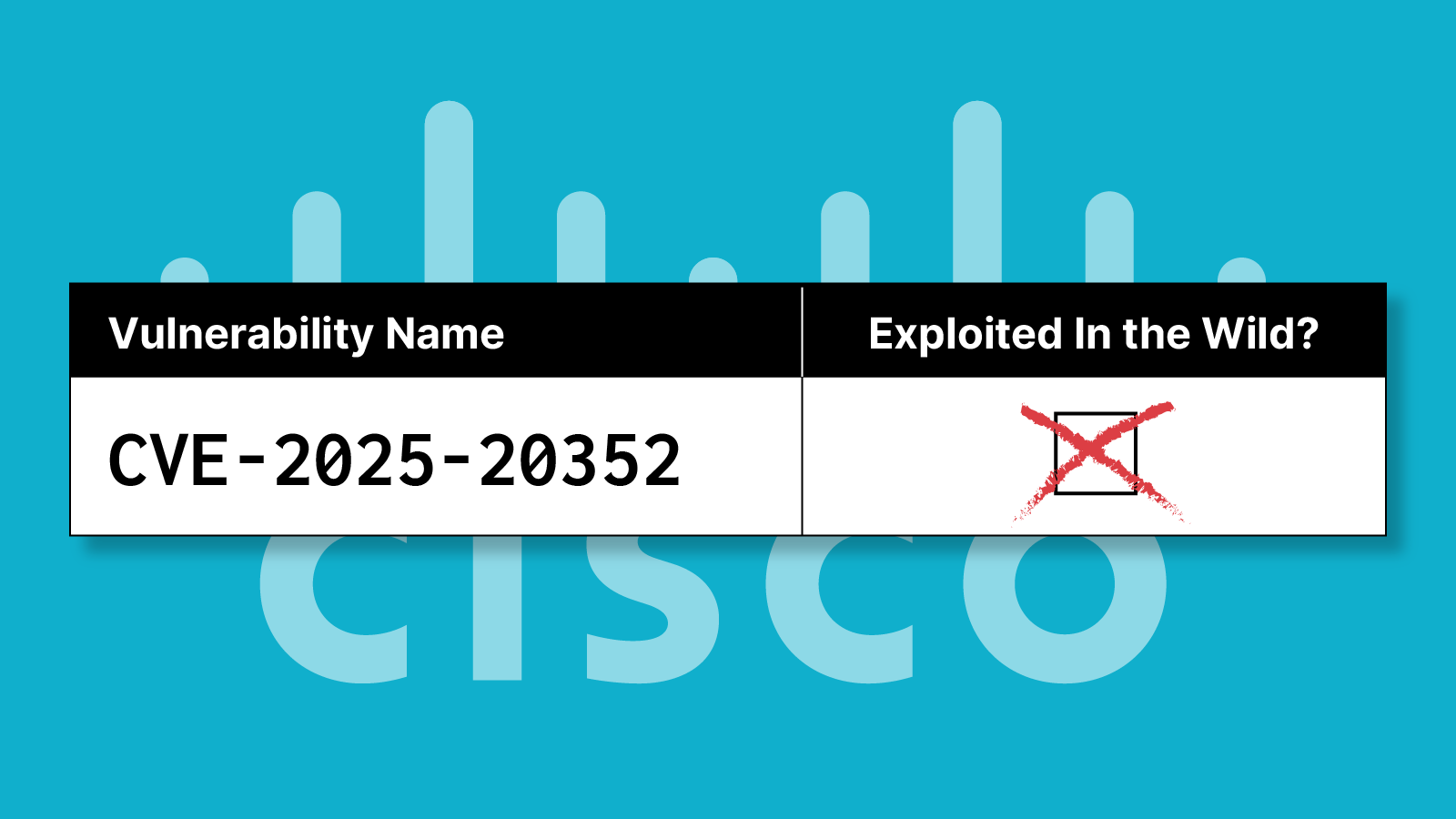
CVE-2025-20352 is a critical SNMP vulnerability in Cisco IOS and IOS XE software, which has been actively exploited in the wild (added to the CISA KEV on September 29th), resulting in reported attacks affecting up to 2 million devices globally. The flaw enables authenticated, remote attackers to trigger denial-of-service (DoS) or execute code as root, threatening the backbone of enterprise, industrial, and service provider networks. The term authenticated relates not only to login credentials via terminal access, but also to SNMP.
What is CVE-2025-20352?
CVE-2025-20352 (CVSS score of 7.7) is a stack overflow vulnerability in the Simple Network Management Protocol (SNMP) subsystem of both legacy Cisco IOS and modern modular IOS XE operating systems. By sending “specially crafted” SNMP packets to vulnerable devices over IPv4 or IPv6, a remote attacker with valid SNMP credentials can cause a device reload (DoS) or, with higher privileges, gain root access for full compromise. Vulnerable software and devices include:
- All SNMP versions (v1, v2c, v3) are affected.
- Meraki MS390 and Catalyst 9300 Series Switches running Meraki CS 17 and earlier are vulnerable.
Why Is This Different?
Unlike past Cisco vulnerabilities, CVE-2025-20352 has already been exploited in the wild. According to Cisco: “This vulnerability was found during the resolution of a Cisco Technical Assistance Center (TAC) support case.”. I have not observed any other reports that detail the nature or scope of this vulnerability being exploited by threat actions.
However, reports indicate that up to 2 million devices on the Internet are potentially vulnerable, including those at ISPs and cloud providers. Cisco’s response was triggered only after attackers gained administrator-level credentials, a troubling escalation reminiscent of trends observed in long-running supply chain and network appliance campaigns.
Attackers are increasingly leveraging authenticated access, sometimes stolen from IT staff or obtained through prior lateral movement, to pivot into critical devices. Attackers then use them not only for direct attacks but also as beachheads for command and control, data exfiltration, and even more damaging supply chain compromises.
Exploitation Scenarios
- Denial-of-Service: Requires SNMPv2c or earlier read-only community string or SNMPv3 credentials.
- Remote Code Execution: Requires the same credentials and privilege 15 (admin/root) access.
Once compromised, attackers can reload devices, disrupt business, or maintain stealthy control under the radar of typical monitoring tools.
Think Like the Attacker
This pattern of exploiting network infrastructure for stealth, persistence, and lateral movement mirrors the tactics of advanced persistent threat actors (APTs), such as Volt Typhoon and Velvet Ant. These groups prize network devices as “quiet corners of the network,” using them for obfuscation networks, data exfiltration, and C2 infrastructure, often bypassing traditional endpoint and network monitoring. As with previous incidents, persistent compromise frequently hinges on administrators not patching, the inherent complexity of supply chains, and the notoriously poor visibility into appliance integrity. Devices may be both Internet-connected and internally connected, giving attackers rare flexibility to build resilient C2 channels undetected.
Mitigation and Recommendations
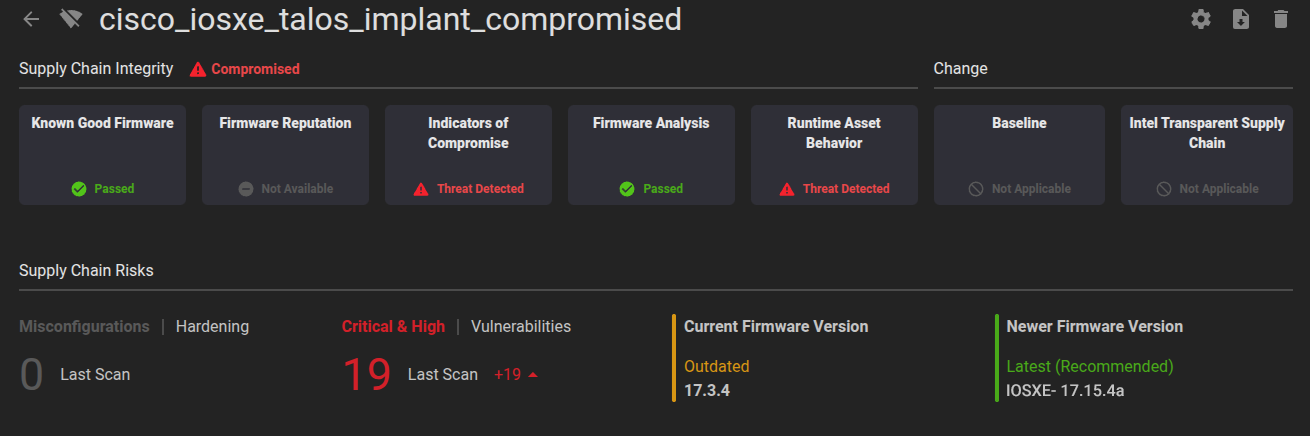
- Patch Now: Cisco has released a software update for IOS XE (17.15.4a). Check with the Cisco Software Checker to confirm your device’s status and upgrade immediately.
- Restrict SNMP Access: Temporarily limit SNMP to trusted users and audit SNMP hosts with show snmp host.
- Disable OID: Administrators may disable the affected object ID, but this could impact SNMP-based management tasks.
- Monitor and Hunt: As with previous APT campaigns, active behavioral monitoring of networking appliances is essential. Validate SNMP configurations, regularly audit privileges, and look for unusual activity or device reboots.
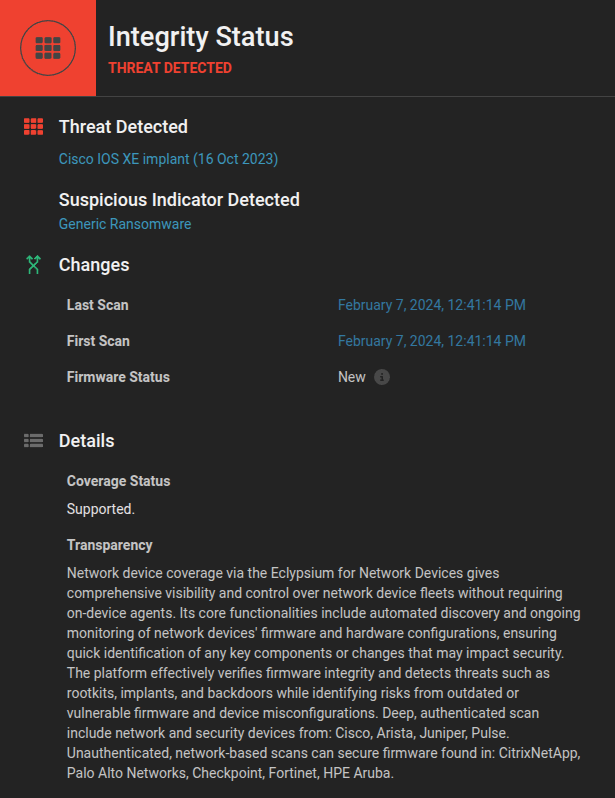
- Visibility and Integrity: Apply supply chain controls, validate firmware integrity, and use modern security platforms for deep inspection—lessons drawn from complex, ongoing device exploitation campaigns.
Final Thoughts
CVE-2025-20352 isn’t just another “patch now” advisory—it’s evidence that attackers will weaponize mismanaged credentials and unpatched edge devices the moment the window opens. Supply chain security, visibility, behavioral monitoring, and privileged access discipline are no longer optional—they’re essential.
The threat surface is deep, the attackers are relentless, and network edge zero-days are now a fact of life for every defender. Treat enterprise hardware as the frontline it is; patch, monitor, and never assume “trusted devices” are truly trustworthy. Attackers are already inside the house.