Palo Alto’s Unit 42 research team recently uncovered a new UEFI bootkit capability as part of the sophisticated Glupteba malware. This blog post will highlight some of the recent findings, outlining the operational mechanisms of Glupteba, its implications for UEFI security, and the steps stakeholders can take to mitigate this threat.
Understanding Glupteba and Its UEFI Bootkit Component
Glupteba, a malware previously known for its role in cryptojacking and theft of personal information, has now been observed exploiting the UEFI (Unified Extensible Firmware Interface) boot process. This represents a continuing shift towards more stealthy and persistent attack vectors, as UEFI firmware is used to initiate the boot sequence before the operating system loads, making detection and remediation particularly challenging.
The UEFI bootkit component of Glupteba allows it to infect the Windows kernel and bypass operating system protections prior to the completion of the boot process. This is achieved by embedding malicious software in the form of a custom loader (based on EfiGuard) to achieve execution at the early stages of device startup. This particular infection method replaces software on the EFI partition, so a full hard disk wipe will remove the malware. Glupteba adds to the growing list of malware that exploits UEFI to gain higher privileges and maintain persistence (See Firmware Attacks: An Endpoint Timeline for a comprehensive list).
Impact and Risks
The integration of a UEFI bootkit with Glupteba malware presents significant risks, including undetected persistence, resistance to common anti-malware solutions, and the potential for widespread damage across various operating systems and devices. The ability of the malware to bypass Windows security features such as PatchGuard and DSE (Driver Signature Enforcement) is especially concerning. By disabling these features Glupteba is able to install a known vulnerable driver, then exploit that driver to effectively hide itself on the system.
Mitigation and Defense Strategies
Addressing the threat posed by Glupteba and its UEFI bootkit component demands a multifaceted approach. Key recommendations include:
- Enhanced Threat Detection: Using the Eclypsium Platform users can detect the presence of Glupteba on a system:
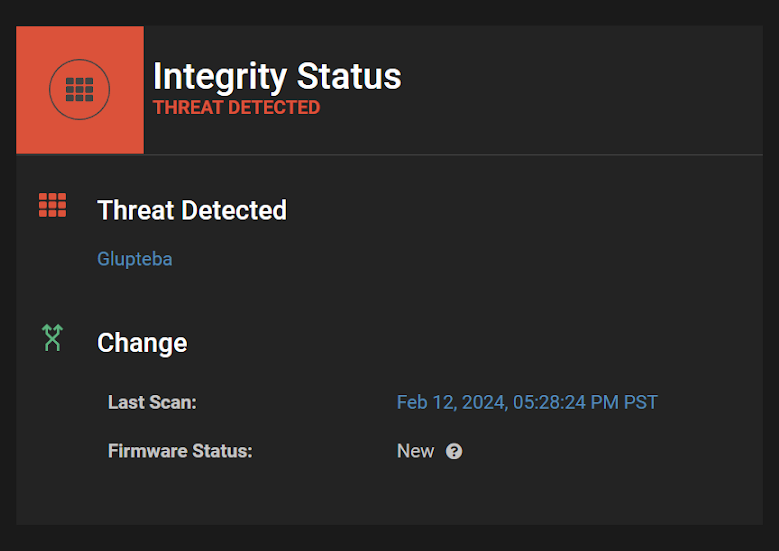
- Harden Firmware Security: Enhancing the security of UEFI firmware through measures such as secure boot, firmware password protection, and regular firmware updates. Eclypsium customers can query the platform to obtain a list of systems that do not have Secure Boot enabled:

- Monitor Changes to Critical Software: The Eclypsium platform can also be used to detect modifications to the bootloader for various operating systems, including Windows. Enable the baseline detection feature as follows to detect changes to bootloaders:
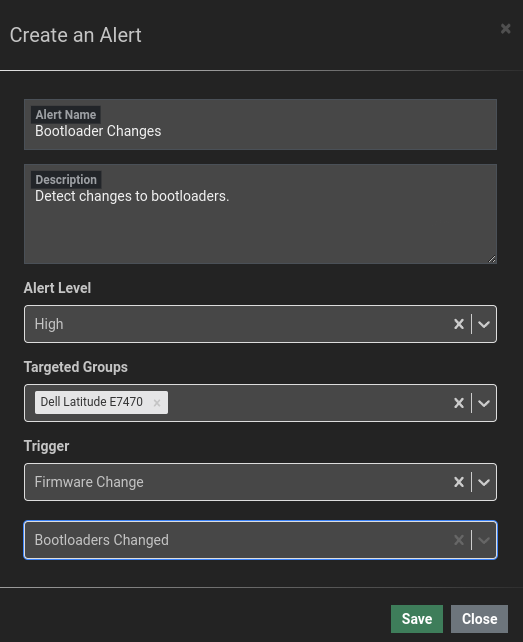
- Vendor Collaboration: Work closely with device manufacturers and UEFI vendors to ensure timely patching of known vulnerabilities and the development of more secure firmware implementations.
- Awareness and Training: Educate IT security teams and end-users about the risks associated with bootkits and firmware-level malware, underscoring the importance of features such as Secure Boot to thwart this type of threat.
Conclusion
The discovery of Glupteba malware leveraging a UEFI bootkit underscores the need for continued focus on supply chain security, specifically centered around lower-level components in UEFI. As attackers explore new methods to exploit the foundational elements of computing devices, the security community must respond with equally advanced defense mechanisms. Collaboration among researchers, security professionals, and vendors will be paramount in mitigating the risks associated with these sophisticated threats and safeguarding against future vulnerabilities.





