The Eclypsium research team has detected in-the-wild exploitation of CVE-2022-1388 by multiple threat actors. This CVE impacts all F5 BIG-IP firmware versions released prior to May 4, 2022.
The attacks were first detected on Eclypsium honeypot devices on May 9th, just five days after the CVE was publicly disclosed. Thus far, attacks have included the installation of a backdoor shell and crypto mining payload. Our initial analysis of these malicious payloads indicates that multiple threat actors are targeting the same vulnerability. While Eclypsium has not directly detected destructive behavior, other reports indicate that adversaries are using the vulnerability to wipe devices. CVE-2022-1388 can be remotely exploited by unauthenticated attackers, providing full control over the device including the ability to execute system commands, create or delete files, or disable services.
Recommended Actions:
- F5 has released a firmware update and recommended mitigations, which can be found here. Recommendations include:
- Update to the latest available firmware.
- Block iControl REST access through the self IP address
- Block iControl REST access through the management interfaceModifying the BIG-IP httpd configuration.
- Eclypsium customers should use the network scanning capability to scan their F5 systems to identify vulnerable systems. Customers can contact Eclypsium Support for any questions related to updating their Eclypsium platform or use of the network scanning features.
- Any devices in which the management interface is logically exposed to attackers or the Internet should be shut off. If the management interface is not exposed, then the device should be patched immediately. Note that if the device is configured with the ‘allow default‘ on the self IP option, then it is vulnerable on the non-mgmt port as well.
- Check F5 devices for the following Indicators of Compromise:
- User Accounts
- New users appearing in the period of 4th of May – 10th of May
- “f5-admin” is the username we observed
- Files
- A file at /etc/init.d/DbSecuritySpt (22 bytes – reverse shell)
- A file at /etc/systemd/system/c3pool_miner.service (185 bytes – crypto miner)
- New binaries in /tmp
- certain auto-generated .sh files should be expected
- Logs
- In /var/log(This feature is not legitimately used from the web ui)
- “method”:”POST”,”uri”:”http://localhost:8100/mgmt/tm/util/bash”,”status”:200
Then, we went ahead and queried all the devices from the list to determine if they are responding for us and to collect copyright year information (from /tmui/login.jsp page), which roughly corresponds to release year of the firmware, and we got the following results:
1139 devices did respond, 49 turned out to be honeypots (returning something other than the expected login page for the device), and 13729 did not respond (might be inaccessible from our IP address or obviously-firewalled devices). Distribution of the devices per copyright year as observed for devices for which we could extract the year:
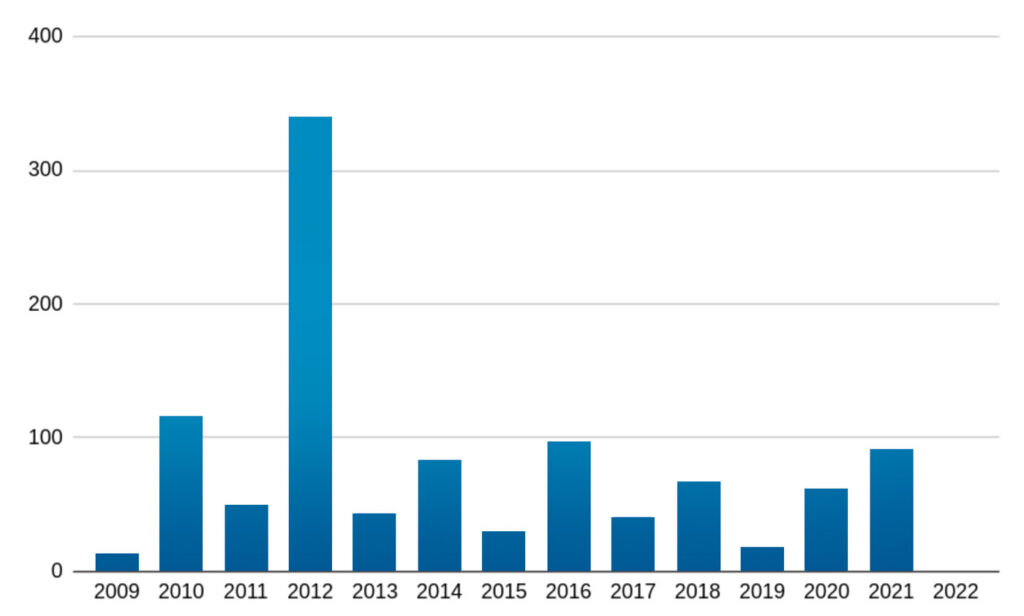
No devices for which we could extract the year – reported their year as 2022. Either those firmwares are using 2021 as the copyright year, or no patched devices could be observed.
We have a few more shodan queries to process through, so more data may be published at a later point.
Additional Background
This is the latest example of the widespread and ongoing trend of adversaries targeting enterprise network infrastructure. As such, we advise organizations to regularly scan their network devices for vulnerabilities and potential threats.
F5 devices have been previously targeted by a wide range of threat actors including:
- Russian SVR
- Actors tied to the Chinese Ministry of State
- Iranian threat actors
- Ransomware groups
- Mirai botnet
In these previous attacks, F5 devices were used to gain initial access, establish ongoing persistence, and spread to additional assets within the target organization.
Much like CVE-2022-1388, previous F5 vulnerabilities were actively exploited within days of their initial disclosure. This highlights the importance that attackers place on these high-value assets and underscores the need for organizations to take immediate action to mitigate any risks related to F5 devices.
Next Steps
Our analysis of this issue is ongoing and we will provide updates to this blog as new information becomes available. Please contact us at [email protected] if you have any questions or comments related to the content published in the blog.





