In our continuing series on the CISA Known Exploited Vulnerabilities (KEV) catalog, we provide an update on the landscape of cyber threats as it has evolved since March 2023. The KEV list, an essential tool for cybersecurity professionals, highlights vulnerabilities that have been actively exploited by cyber adversaries. The KEV is a small subset of total published vulnerabilities and provides the defenders with an idea of what vulnerabilities attackers are actually going after. CISA doesn’t break out the KEVs into categories. But understanding where in your technology stack attackers are aiming their crosshairs can help you to make more informed decisions about which security controls to focus on.
WHAT CHANGED AND WHAT STAYED THE SAME?
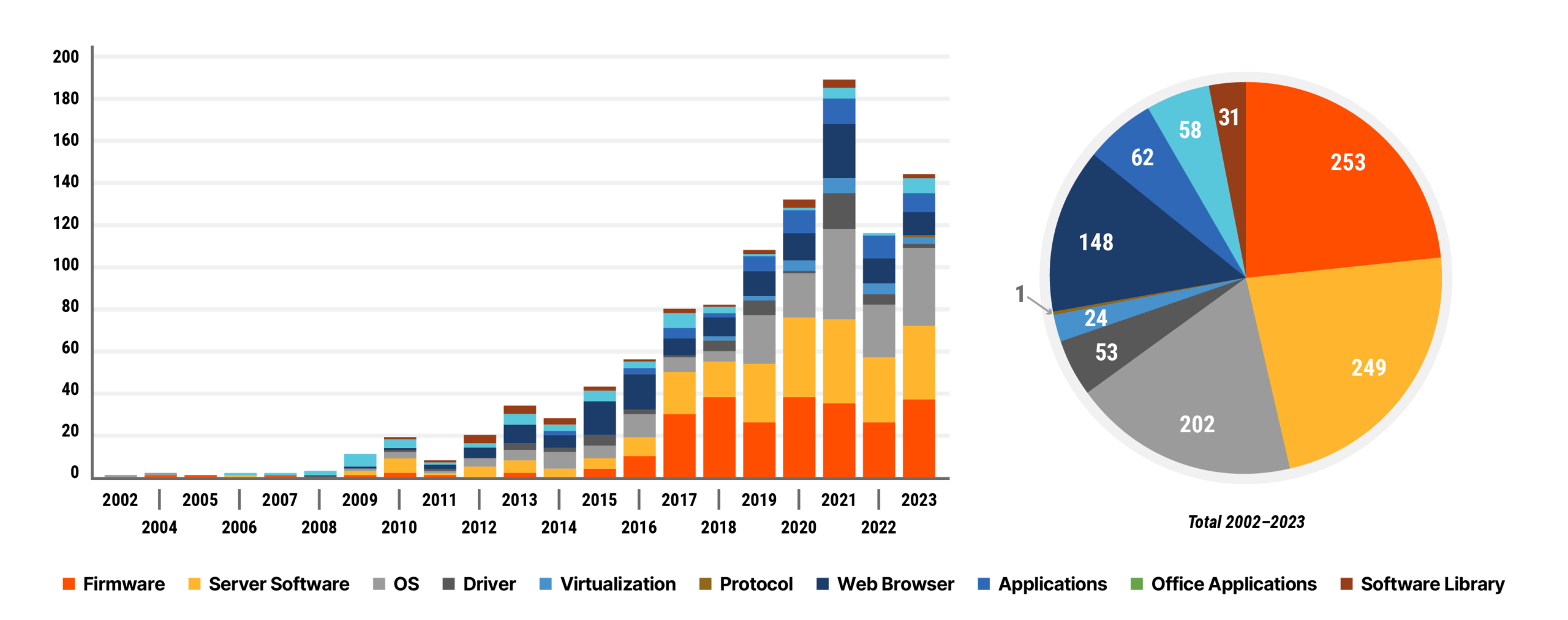
When we first published in June of 2022, the KEV included 778 actively exploited CVEs. In our last update on March 13, 2023, the list had added 111 CVEs for a total of 889. As of today, there are 1,089 with a net new of 204 (CISA removed a few which is why the math doesn’t perfectly add up). The chart below breaks out these 1,089 vulnerabilities in terms of the year they were discovered and the category of vulnerability. Of note, in 2023 attackers exploited new vulnerabilities at roughly twice the rate as the previous year.
As noted above, CISA itself does not yet categorize the vulnerabilities, so we assigned categories to each vulnerability based on the type of asset as follows (the Protocol category is new in 2023):
- Firmware (e.g. Intel AMT, Cisco, F5 Networks)
- Server Software (e.g. Apache, Microsoft Exchange)
- Operating Systems (e.g. Windows, Android)
- Web Browser (e.g. Google Chrome, Internet Explorer)
- Office applications (e.g.. Microsoft Word, Excel)
- Applications (e.g. WinRAR, WhatsApp)
- Software library (e.g. OpenSSL)
- Virtualization (e.g. Docker, VMWare)
- Protocol (e.g. SLP, TCP, BGP)
Network appliances under attack
2023 witnessed a significant surge in attacks targeting network appliances, a trend that underscored the evolving sophistication and evolution of cyber adversaries. This dramatic increase not only highlighted the vulnerabilities inherent in network infrastructure but also magnified the potential for devastating breaches within organizations. As noted in the Mandiant M-Trends report, exploits remained the most common initial access vector (32% of all incidents) in 2023, including exploits of network appliances. Read this blog post to get a better understanding of this trend of attacking network infrastructure. Eclypsium offers EDR-like detection for network devices, adding a much-needed layer of defense to this vulnerable attack surface.
For entities that fell victim to these attacks, the consequences were severe and prompted a reevaluation of cybersecurity defenses. The escalation underscored the necessity for continuous monitoring, timely updates, and a proactive security posture to mitigate the risks associated with these critical vulnerabilities.
To better understand attacks against network infrastructure, we decided to itemize the vendors attacked in the firmware category (see the graph below). This isn’t to single out or shame any specific vendor—they all had a rough year—but we wanted to highlight the fact that very few of the industry leading appliance vendors made it through 2023 unscathed. Organizations reeling from a breach may start considering changing vendors, but the data shows this is not a straightforward process. Vendors who escaped 2023 relatively smoothly are undoubtedly in the crosshairs of malicious actors, as lack of disclosed vulnerabilities only means nobody has reported them yet.
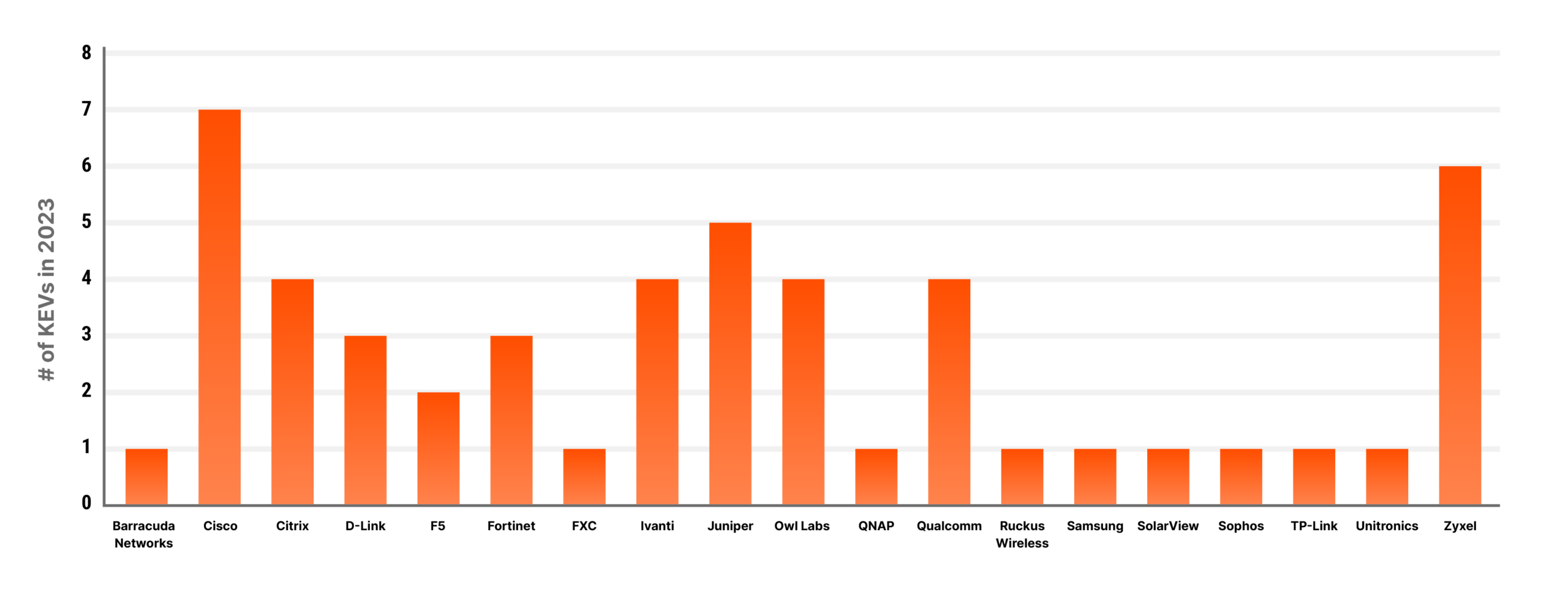
Known exploited vulnerabilities in the CISA KEV database for 2023. Note that these are not necessarily new vulnerabilities.
One cause for optimism is that network device manufacturers are starting to take greater responsibility for the security of their products, according to Secure By Design principles. A group of these vendors formed the Network Resilience Coalition (NRC) last year and in January 2024 published a white paper with recommendations for both vendors and buyers. The founding members of the NRC are: AT&T Inc., Broadcom, BT Group, Cisco Systems Inc., Fortinet, Intel Corp., Juniper Networks, Lumen Technologies Inc., Palo Alto Networks, Verizon and VMware.
Among the recommendations for network device manufacturers:
- Adopt the practices from the NIST Secure Software Development Framework (SSDF)
- Improve communications on product “end of life,” including date ranges and support levels, so that customers can make informed decisions
- Release critical security fixes separately from patches with new features or functionality changes