CISA: Over Half of Top Routinely Exploited Vulnerabilities in 2023 Affected Network Devices and Infrastructure

Over half of the most routinely exploited vulnerabilities worldwide in 2023 affected network devices and infrastructure, according to a cybersecurity advisory issued by CISA and other international cybersecurity agencies in November, 2024. Furthermore, the majority of the routinely exploited vulnerabilities were “initially exploited as a zero-day” which was a change from 2022, when the majority were not zero days.
The trend of attackers increasingly using zero-day exploits and targeting network infrastructure has major implications for how enterprises must secure their IT environments.
Which Devices and Vendors are Routinely Exploited?
Firewalls, application delivery controllers, email security gateways, and more were among the devices affected by the most routinely exploited vulnerabilities in 2023. Citrix, Cisco, Fortinet, Juniper, Ivanti, Microsoft, and many other globally prevalent vendors had products that were affected.
This chart shows the complete breakdown of vendors represented in the top routinely exploited vulnerabilities list.
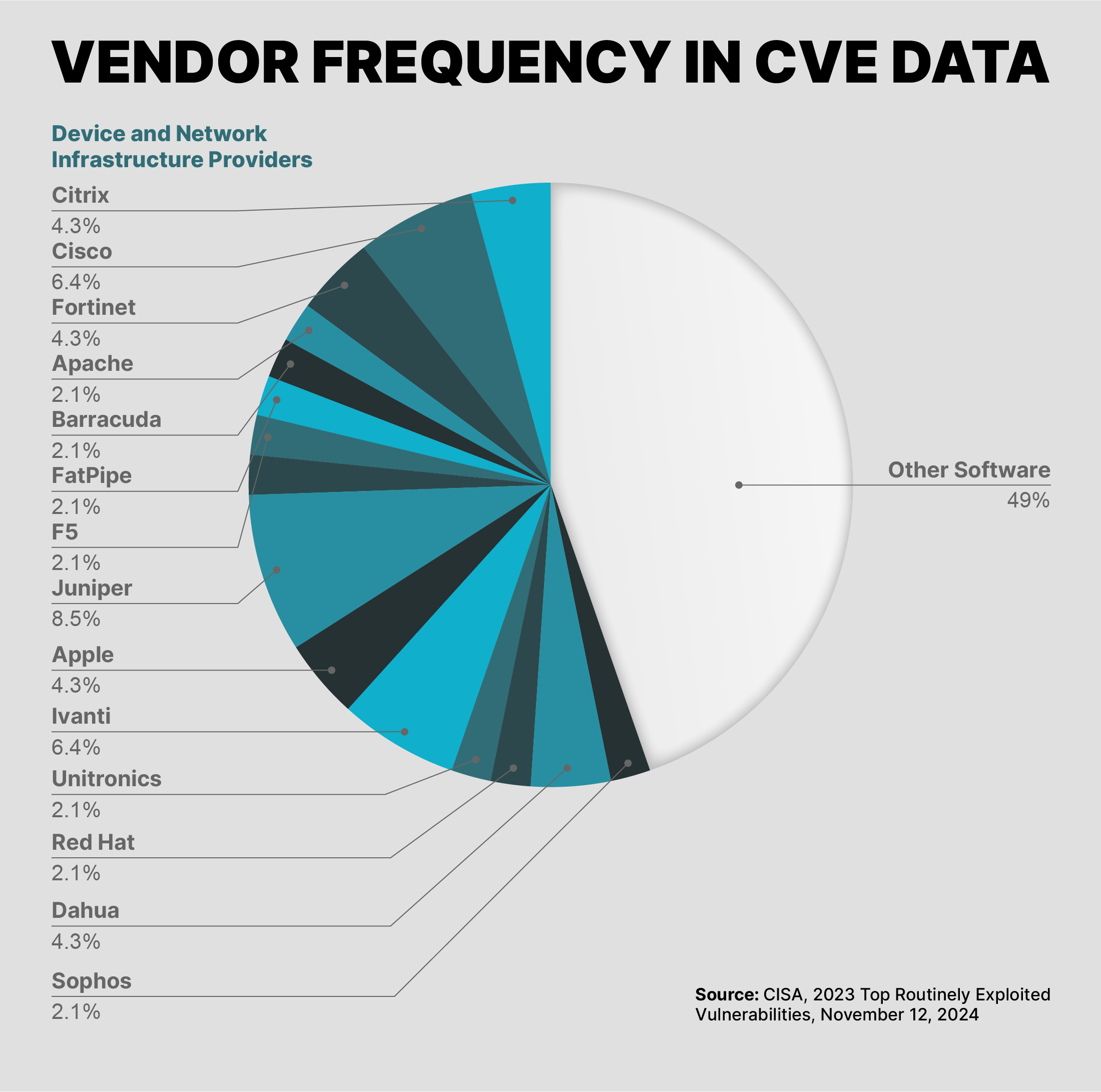
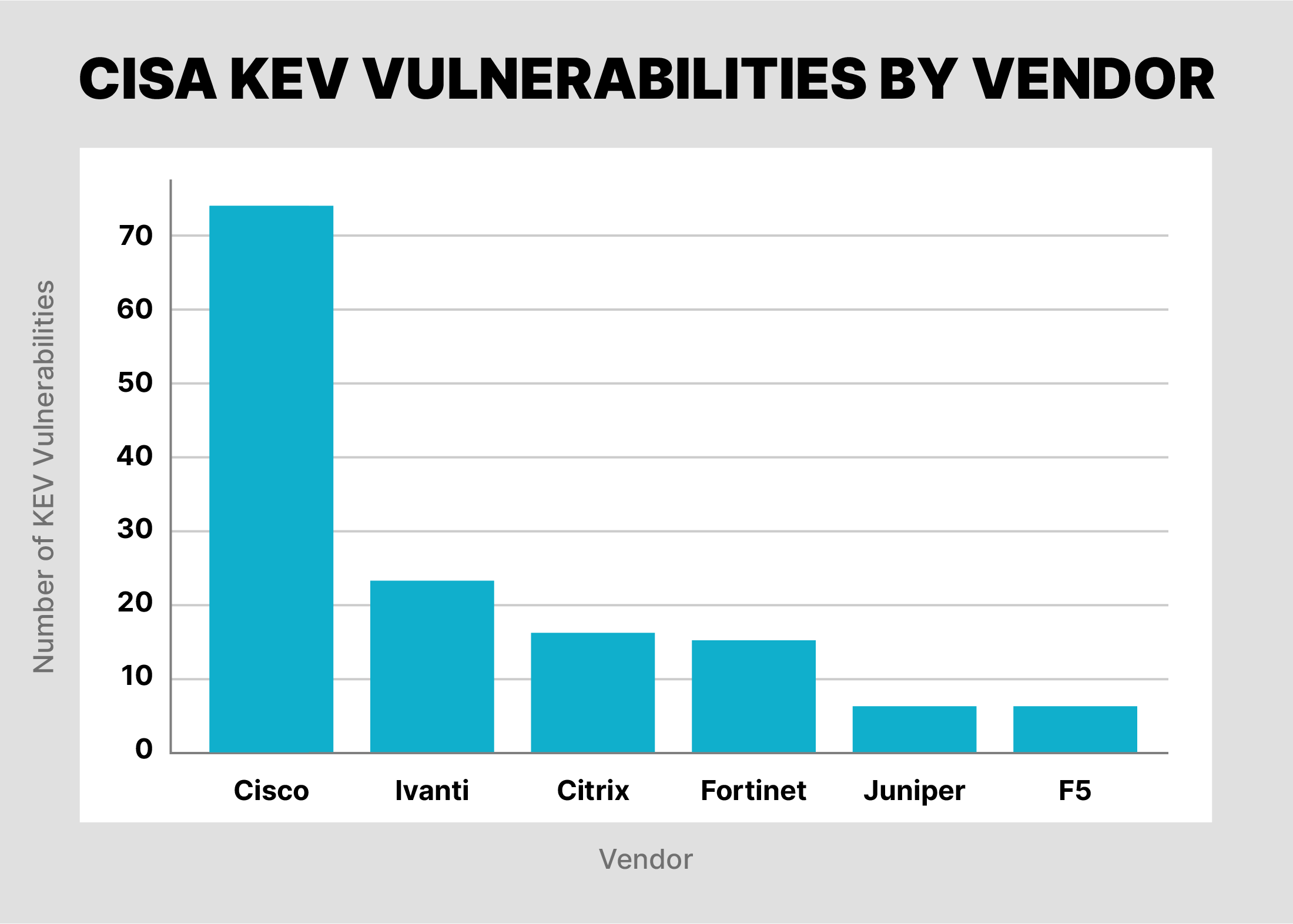
These vendors of network appliances and infrastructure, as well as commonly used enterprise software, are also heavily represented in the larger list of Known Exploited Vulnerabilities (KEV) maintained by CISA, which catalogs thousands of vulnerabilities. The chart below shows how many vulnerabilities these specific network infrastructure providers have listed in the KEV.
Recommended Mitigations
The recent cybersecurity advisory offers recommended mitigations for vendors and developers of software and network equipment, as well as mitigations for end-users of these products. Much of the guidance falls into the category of cybersecurity best practices, such as regularly patching software, conducting routine asset discovery, and maintaining updated cybersecurity incident response plans.
These recommendations are not novel, but the urgency of updating them to account for increasing zero-day attacks on network infrastructure is growing.
A Note On Endpoint Detection and Response (EDR)
The report also noted the importance of EDR for detecting zero-day exploits, claiming that “at least three of the top 15 vulnerabilities from last year have been discovered when an end user or EDR system report[ed] suspicious activity or unusual device malfunctions.”
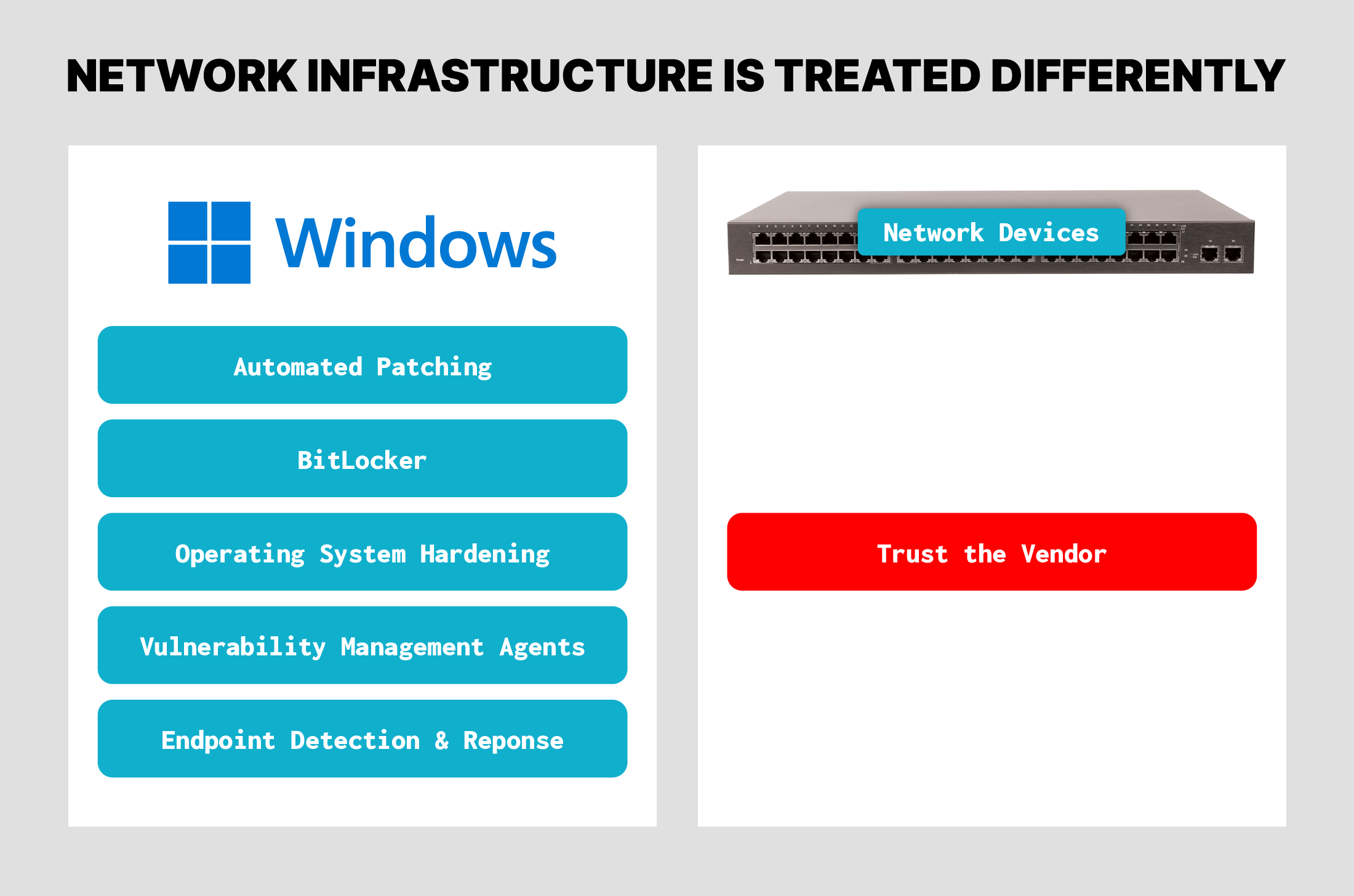
This introduces a conundrum: The types of network devices impacted by many of the vulnerabilities listed in the report are frequently not covered by EDR. Many organizations will not install, or cannot install, EDR agents on the network appliances or other network infrastructure featured in this report.
Furthermore, when routinely exploited vulnerabilities affect security solutions themselves, such as CVE-2022-3236, an RCE vulnerability in Sophos firewalls, it raises questions about the coverage and effectiveness of current cybersecurity practices. Historically, Windows devices such as end-user workstations have been the focus of many security solutions and procedures. In the case of network infrastructure, security has largely been left up to the vendor. This needs to change.
The Role of the Software Supply Chain
The report also includes a section of mitigation recommendations focused on the supply chain. For end-user organizations, this includes recommendations such as:
- Reducing third-party applications and unique system/application builds
- Ensuring software vendors provide a Software Bill of Materials with all products
- Asking about software providers’ secure-by-design practices
- Requiring notification of security incidents and vulnerabilities “within a risk informed time frame”
For vendors and software providers, the report recommends following secure-by-design practices, identifying vulnerabilities in their own software and patching them, establishing vulnerability disclosure programs, and more.
The report also recommends that software vendors “Configure production-ready products to have the most secure settings by default.” This seems obvious, but is not always put into practice. For example, Sophos systems of the type targeted in the Pacific Rim series of attacks were found to have numerous security misconfigurations that left them more vulnerable to firmware-based attacks. Eclypsium’s own analysis of Sophos equipment in the wake of Pacific Rim found that Intel Bootguard was disabled on some vulnerable systems, and that the system featured unlocked legacy SMM, unlocked SMI, and was missing BIOS write protections, among other risk factors. These configuration issues may or may not be noticeable to the end user or even the security team at an enterprise, but they offer valuable attack vectors for cyber adversaries.
This CISA report pairs well with the recent NIST Internal Report titled “Hardware Security Failure Scenarios” which describes 98 scenarios in which hardware previously thought to be invulnerable could be compromised. Many of the scenarios involve exploitation of insecure and/or outdated firmware.
Eclypsium Discovers Zero Days and Vulnerable Software, Firmware, and Hardware on Network Infrastructure
Current EDR solutions do not offer the necessary coverage for early discovery and mitigation of zero day vulnerabilities in network infrastructure. As zero days take up an increasing proportion of the most exploited vulnerabilities, and network infrastructure is increasingly targeted, the need for a new solution grows clear.
Eclypsium offers both agent-driven and agentless discovery of vulnerable network devices, with deep visibility into firmware, and component-level inventory to assure that misconfigurations, vulnerabilities, and indicators of compromise are detected as quickly as possible.





