While it has been coming for years, the industry is now facing its moment of truth for supply chain risks. The accelerating rash of major breaches in the technology supply chain has put threat actors in possession of the source code and secrets that underpin virtually all enterprise infrastructure. This means that critical hardware and software products can be compromised before they are ever delivered to an organization, or can be compromised via updates or exploits after they are deployed – and all of this is happening far beyond the view of existing security controls.
This moment is quite similar to other major inflection points in cybersecurity. In much the same way that attackers shifted from targeting the perimeter to the relative blindspot of lateral movement inside of enterprise networks, attackers have now shifted the fight to attack technology products and devices in our supply chains. The range of supply chain attacks includes exploiting vulnerabilities in critical third-party software and devices and compromising delivery or update mechanisms used by software vendors or manufacturers of these devices. Likewise, in the same way that threats evolved to evade antivirus products, attackers are now able to compromise and introduce implants into seemingly valid code of external software or devices to evade security.
The complexity and size of supply chains of digital technology makes this the biggest challenge facing cybersecurity of enterprises and nations. Organizations can no longer just blindly trust their hardware and software suppliers. Adversaries are perfecting their ability to exploit the blind trust between organizations and their vendors, and are able to exploit that trust at scale to compromise many organizations at the same time. Organizations need to have tools to independently validate all the hardware and software products they buy and use. They must be able to actively validate what these products are made of through the use of SBOMs, and validate their integrity and vulnerability of all key components. It is no easy task and will require concerted industry effort. Securing critical technology supply chains will need independent supply chain security solutions helping enterprises on one side and software and hardware vendors on the other side. This is precisely what a modern supply chain security platform should be built for.
Recent Attacks on the Supply Chain
To understand the risk, we have to look at what is happening in the wild. Beyond the well-known SolarWinds supply chain breach and vulnerable Apache Log4j software, over the past months, ransomware operators have increasingly targeted critical hardware technology providers. Instead of stealing personal information, these actors have acquired source code, build environments, signing keys of hardware and software technology, including the critical system code like firmware that makes devices and components run.
The list below highlights some of the most significant recent breaches affecting supply chain of critical hardware components:
- Western Digital, April 2023, potentially affecting a wide range of storage drives
- MSI, April 2023, affecting motherboards and PCs
- Acer, March 2023, affecting many PCs
- AMI, August 2022, affects BMCs used by many server brands and data centers
- Gigabyte, August 2021, affects Intel and AMD-based devices
- Quanta, April 2021, affects Apple devices
This is an accelerating trend and these are only the breaches that we know about. Adding to the trend are the new vulnerabilities constantly discovered in hardware and software products we use. The consequence of this trend is that we need to do better than just trust external technology products from our vendors.
What it Means for Enterprise Risk
These events have far-reaching consequences for virtually any organization. Let’s look at a few key points.
- Directly impacts enterprise businesses – Virtually every type of enterprise-grade technology whether in the corporate network, at the edge, or in the cloud ultimately runs on devices affected by these breaches.
- The supply chain magnifies each breach – A single breach can affect dozens of downstream vendors that use the victim’s code/components (e.g MSI motherboards, Western Digital storage drives, etc). Impacts can also spread upstream: The Gigabyte and Acer breaches exposed secrets from Intel, AMD, and Apple who needed to provide sensitive code to their downstream partners for development.
- Massive security impact – Threat actors now have TTPs to breach major ICT vendors and compromise their products internally or exploit vulnerabilities when these products are in use by victim organizations. Threats stemming from such breaches are extremely difficult to detect, arriving in the guise of trusted vendor code/components. They are often persistent, hide below the application level and can subvert security in all of the infrastructure built on compromised systems. They have unmatched capability to steal or destroy data, disable devices, or entire fleets disrupting infrastructure.
- Each supply chain breach is felt for a very long time – With access to the technology provider’s environment, threat actors can impact product build, delivery and update infrastructure, discover new vulnerabilities that aren’t known today. Even when the manufacturer releases new “valid” code, those vulnerabilities will likely remain. Threat actors can pursue SolarWinds style of supply chain attacks in which a backdoor is inserted into the manufacturer’s code during the development or update processes. Additionally, the system code in these breaches remains some of the most poorly monitored and managed code. Updating the system code like firmware of entire fleets of devices can take months.
Meet the Modern Supply Chain Security Platform
We are at the point where we need to have the tools and processes to actively and independently verify the technology acquired from our supply chains and to continually monitor it for signs of compromise and newly identified vulnerabilities.
This is a challenge that the team at Eclypsium has spent years preparing for. Building on our decades of experience researching the security of devices and system code, we’ve built a new class of security product that allows our customers to audit their supply chains and monitor critical hardware and software assets. The Eclypsium SBOM (Software Bill of Materials) capability provides an industry-standard view into the components and dependencies within each asset, enabling organizations to verify the integrity of their assets and monitor for critical risks. Ongoing monitoring identifies any modifications in system code and SBOM to reveal system level threats and allows teams to find and patch vulnerabilities that really matter.
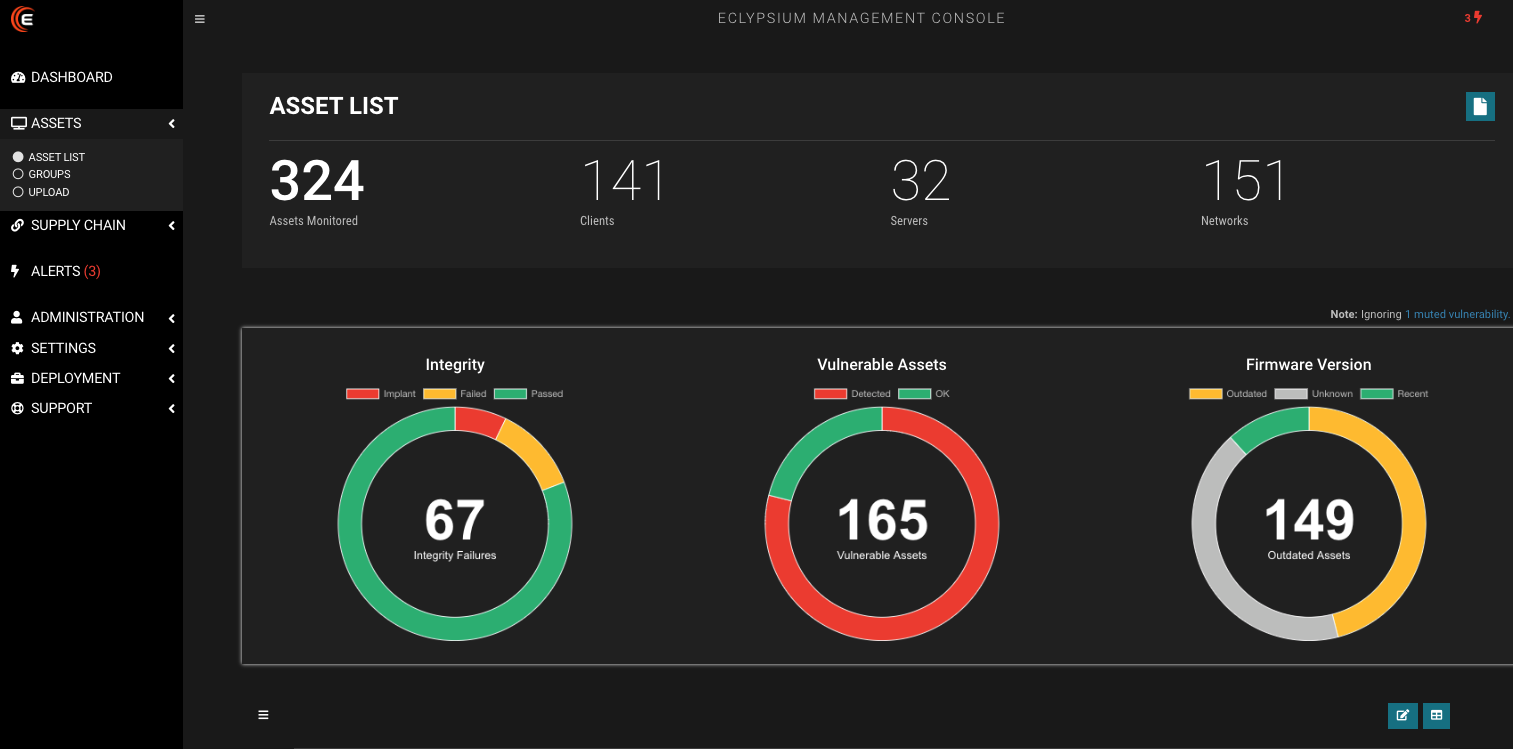
Some of the ways our customers use the Eclypsium Supply Chain Security Platform.
- Understand what devices are made of and what software they run – our customers want to know which assets they buy and deploy that increase their security risk. For example, today they will need to know which hardware assets have Western Digital SSDs, MSI motherboards, or MegaRAC based servers. We provide a comprehensive, easy-to-use bill of materials for each asset with its components and all system code.
- Verify the integrity of all system software – we verify the integrity of all critical code at the system level as well as underlying components. We maintain the industry’s most complete supply chain catalog of devices and critical system code so that our customers can identify if their systems have been altered in any way. Ongoing monitoring of system code and components across device fleets is used to provide continuous supply chain assurance, beyond just point of entry.
- Scan system software in devices for third-party vulnerabilities – we assess all code within systems and components to identify vulnerable and out-of-date software, firmware and hardware. We find vulnerabilities in the system level code and components of upstream suppliers that aren’t seen by traditional vulnerability scans.
- Assess Device-Level Configurations – Eclypsium audits and ensures that all the many built-in protections from multiple vendors are enabled and working together properly. This ensures that OS vendor protections, chipset protections, SecureBoot, dbx, out-of-band management, and many others are all working together at the device level.
- Reduce supply chain risk with vendor updates – Eclypsium gives organizations the tools needed to help address supply chain risks once they are identified by keeping track of, validating and deploying vendor and manufacturer updates to system software and firmware.
- Continuously scan third-party hardware and software assets – Identifying and reducing supply chain risk is not a one time thing. We continue to monitor and verify assets and their bill of materials to identify any unexpected modifications to integrity or uncover new vulnerabilities before they can cause damage.
- Implement a multi-team, full-lifecycle supply chain security approach – our customers are able to integrate supply chain security checks across multiple teams and across the lifecycle of their external technology. Procurement teams can assess prospective hardware and software products and vendors, IT teams can assess newly received products, security operations and vulnerability management teams can monitor and scan deployed assets, incident response teams can evaluate system code in assets involved in a security incident.
These are the capabilities that will help organizations to independently verify the hardware, firmware and software technology from their supply chains. The vulnerability of digital supply chains means that the challenge is here and now. It is why we first launched our product four years ago, and we are going to continue helping our customers address their technology supply chain security challenges.





