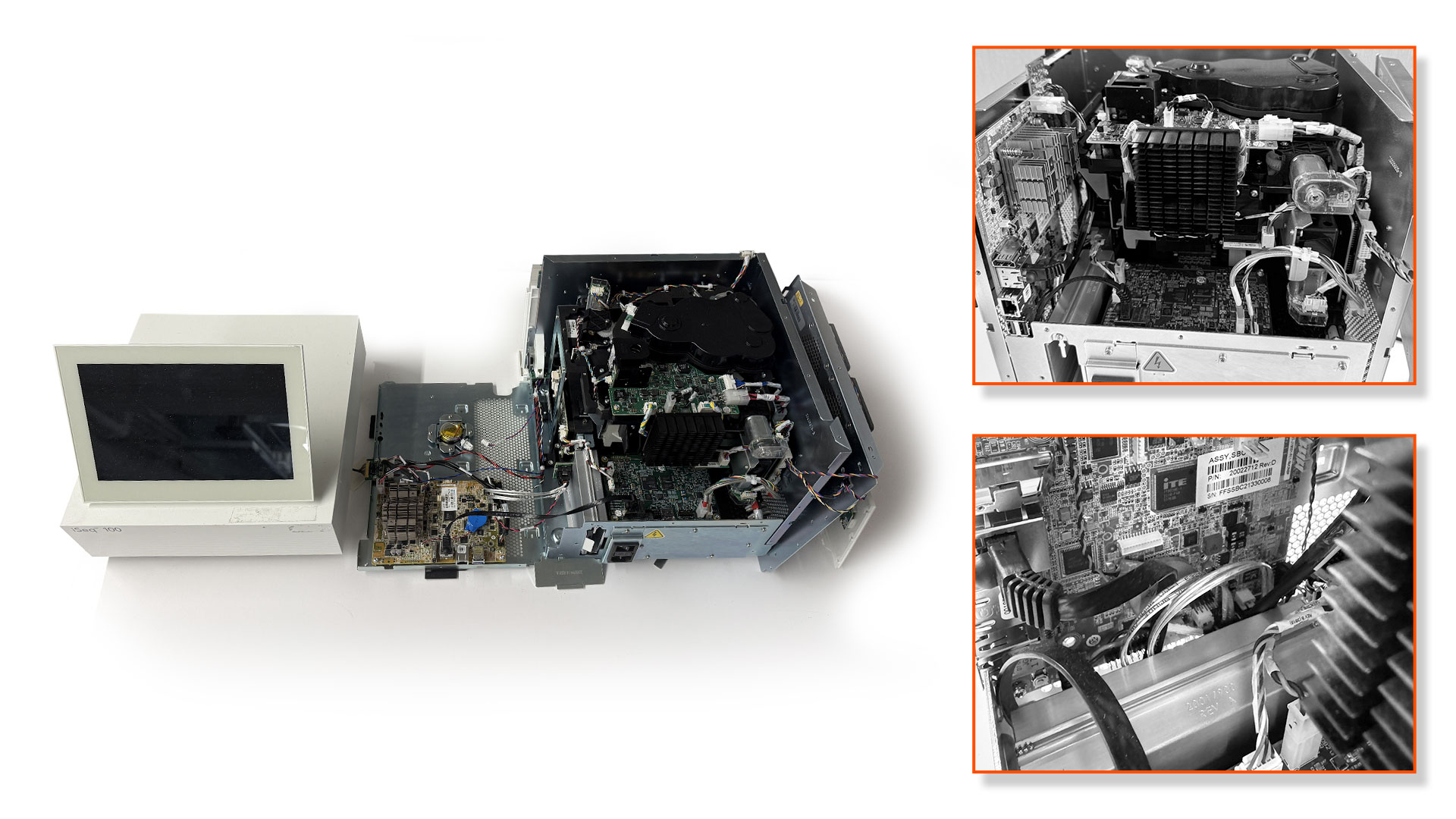
Eclypsium’s research team has identified BIOS/UEFI vulnerabilities in a popular DNA gene sequencer made by Illumina, a leading genomics and healthcare technology vendor. More specifically, we found that the Illumina iSeq 100 used a very outdated implementation of BIOS firmware using CSM mode and without Secure Boot or standard firmware write protections. This would allow an attacker on the system to overwrite the system firmware to either “brick” the device or install a firmware implant for ongoing attacker persistence.
Instances like this of commodity hardware re-use pose significant supply chain security risks due to the potential for embedded malware or backdoors. And since outdated firmware often lacks the latest security updates, it is more vulnerable to exploitation. Supply chain complexity exacerbates the risks of commodity hardware re-use by increasing the number of touchpoints and opportunities for vulnerabilities. In December 2023, NIST published a set of guidelines for the cybersecurity of genomic information that specifically noted the importance of hardware and software security in systems, such as DNA sequencers, that use proprietary software to handle genomic information. NIST recommends stringent configuration management and integrity checking for these devices.
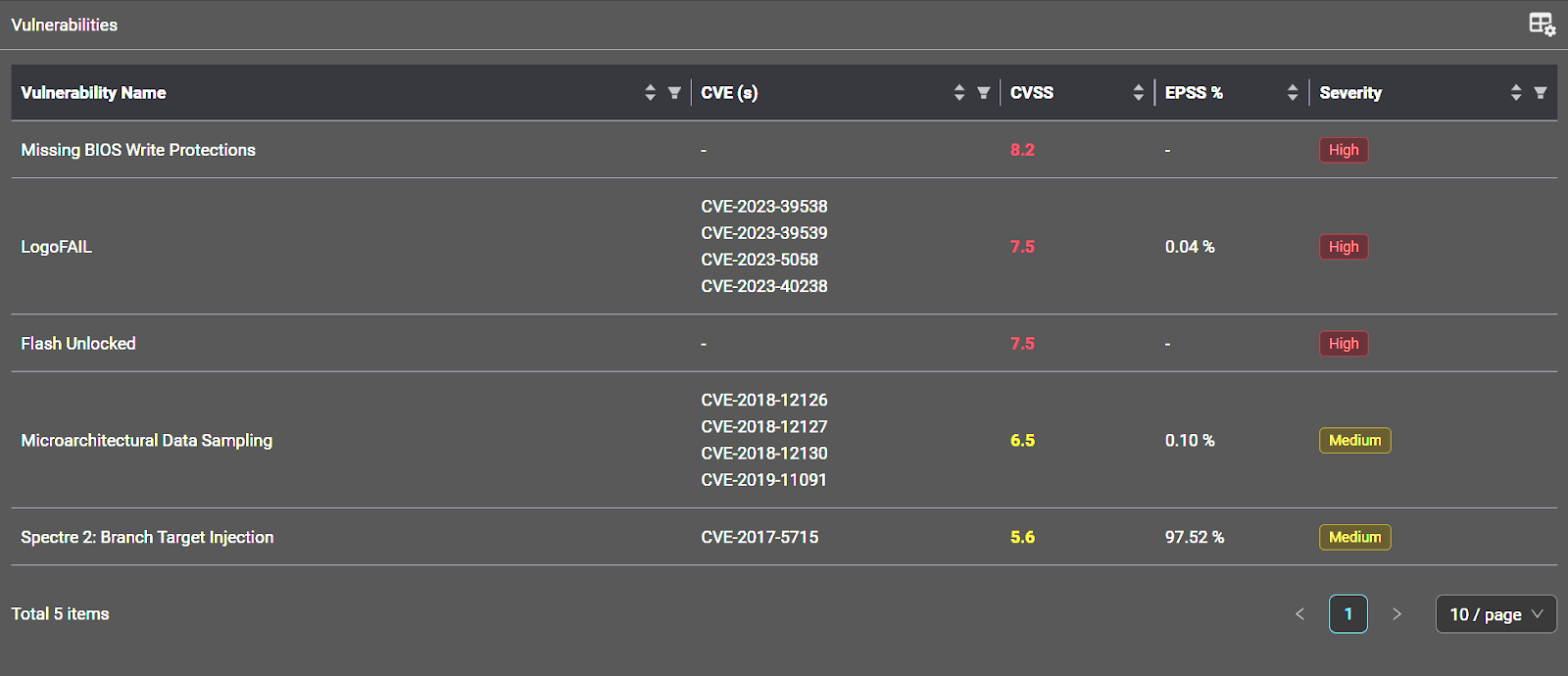
Vulnerability Analysis
Over the past decade, the state of the BIOS/UEFI security landscape has changed considerably. State-based attackers and ransomware operators have pivoted en masse to target firmware both in the supply chain as well as devices already in the field. In response, technology vendors (e.g. motherboards, chipsets, operating systems, OEMs, and ODMs) have added layer upon layer of protections meant to keep this critical code safe. In spite of these efforts, firmware attacks have continued to grow.
The key issues include the following:
- Booting in CSM – UEFI is the modern successor to BIOS firmware. However, Compatibility Support Mode or CSM allows UEFI to boot to legacy BIOS firmware to maintain compatibility with older devices. While this maintains support for old devices that can’t be upgraded, it is not recommended for newer high-value assets.
- Vulnerable BIOS – The iSeq 100 boots to an old version (B480AM12 – 04/12/2018) of BIOS with known vulnerabilities.
- Firmware Protections Are Off – Devices also typically include basic Read/Write protections to tell the hardware where it can read and write firmware. These protections are not enabled on the iSeq 100, meaning an attacker would be free to modify the firmware on the device.
- No Secure Boot – Secure Boot was the first of the industry’s firmware protections and was intended to check that all code related to the boot process was valid, signed, and unaltered. The iSeq 100 does not use Secure Boot, meaning that any malicious changes to the firmware would go undetected.
It should be noted that our analysis was limited specifically to the iSeq 100 sequencer device. However, the issue is likely much more broad than this single model of device. Medical device manufacturers tend to focus on their unique area of expertise (e.g. gene sequencing) and rely on outside suppliers and services to build the underlying computing infrastructure of the device. In this case, the problems were tied to an OEM motherboard made by IEI Integration Corp. IEI develops a wide range of industrial computer products and maintains a dedicated line of business as an ODM for medical devices. As a result, it would be highly likely that these or similar issues could be found either in other medical or industrial devices that use IEI motherboards. This is a perfect example of how mistakes early in the supply chain can have far reaching impacts across many types of devices and vendors.
Exploitability and FDA Guidance
The vulnerabilities we have discussed thus far would allow an attacker with presence on the device to modify the firmware in any way they choose. Unfortunately, this is not a far-fetched scenario given that the Illumina sequencers were recently found to have a critical RCE (Remote Code Execution) vulnerability (CVE-2023-1968). The issue affected a variety of Illumina devices, resulting in an FDA Class II recall as well as an ICS Medical Advisory from CISA.
Illumina has since provided a fix and notified their customers. Thus in order to gain initial access, attackers would need to either find and exploit any unpatched devices, or alternatively, obtain credentials for the device, or find another unknown vulnerability. Once on the device, an attacker would further need to escalate to administrator privileges. But once again there are many well-known privilege escalation options for older versions of Windows 10 as found on the Illumina sequencer (Windows 10 2016 LTSB, Version 1607). At that point, the attacker could write virtually anything to the device’s firmware. This could be custom firmware to enable ongoing malicious activity or simply rewriting the firmware in order to disable the device. Once again, usually there are multiple firmware protections to make this last step more difficult, but they are absent on the Illumina device. This type of exposure actually lowers the bar for attackers seeking to cause damage. Instead of needing genomic expertise and detailed understanding of the system’s software to tamper with test results, attackers could simply brick the device with no further knowledge required.
Issues such as these are why the FDA has increasingly focused on all forms of code in devices including firmware. The FDA’s recent software guidance specifically calls out that:
This guidance is intended to cover device software functions. Examples include, but are not limited to, firmware and other means for software-based control of medical devices, software accessories to medical devices, and software only function(s) that meet the definition of a device.
Of course, there is a gap between what the FDA recommends and what happens in the real world. To close this gap, both device vendors and their customers need tools and procedures to assess the safety and integrity of their assets down to the firmware level. Vendors need to be able to assess the components from their OEM suppliers, and healthcare and research organizations need the ability to evaluate the devices that are allowed into their facilities.
Potential for Real-World Attacks
It is important to note that we have not seen evidence of the iSeq 100 firmware being exploited in the wild. On the other hand, unprotected implementations of BIOS/UEFI have been repeatedly exploited in more traditional devices such as laptops for almost a decade, going back to the 2015 disclosure of the Hacking Team UEFI implant and again in the LoJax and MosaicRegressor firmware implants. In all of these examples, attackers targeted firmware as a way to ensure their malicious code could run below the level of the operating system while also establishing ongoing persistence outside of the physical device storage drives.
Furthermore, adversaries have increasingly targeted the firmware in non-standard devices as a part of attacks against healthcare and research organizations. Network devices, application infrastructure, and IoT devices have all been exploited in order to gain initial access or to establish ongoing persistence. Such devices are prime targets because they are typically trusted on the network yet often do not support a traditional security agent for protection.
Additionally, the ability to overwrite firmware on the iSeq 100 would enable attackers to easily disable the device, causing significant disruption in the context of a ransomware attack. This would not only take a high-value device out of service, it would also likely take considerable effort to recover the device via manually reflashing the firmware. This could significantly raise the stakes in the context of a ransomware or cyberattack. Sequencers are critical to detecting genetic illnesses, cancers, identifying drug-resistant bacteria, and for the production of vaccines. This would make these devices a ripe target for state-based actors with geopolitical motives in addition to the more traditional financial motives of ransomware actors.
Next Steps
In December 2023, NIST published a document about the Cybersecurity of Genomic Data in which they specifically recommend doing stringent security management and integrity checking on DNA Sequencer Hardware. In the same way that DNA is the fundamental code underpinning all complex life, firmware is the most fundamental code within devices. While firmware isn’t nearly as complex as the human genome, it is the first and most privileged code to run. All the complexity of the operating system, applications, and services are ultimately beholden to what happens in the firmware. And if the firmware foundation of a device is vulnerable or compromised, then it is virtually impossible to ensure the security of the device itself. And so, in the same way life scientists need tools to analyze DNA for problems, IT and security teams need tools to assess the fundamental code of their technology. At Eclypsium, we are dedicated to making this a simple and automated process for any organization.
To learn more about this research or how Eclypsium can help protect your device and supply chains, please contact us at [email protected].





