“This is fine” – Network Device Vendors, probably
2025 has been the year of network exploitation, with numerous CISA Emergency Directives issued about Cisco products, the F5 data breach, and an 8x increase in network device exploitation as reported by Verizon.
Now, just in time for the 2025 holiday season, three new network edge device vulnerabilities, some actively exploited, have been disclosed. They highlight common threads across many network-edge vulnerabilities disclosed in the past year:
- The speed of exploitation, either after disclosure or even sooner in the case of zero days.
- The total reliance on vendor-issued patches to secure business-critical infrastructure.
- The difficulty in prioritizing vulnerabilities when an old, medium-risk CVE becomes the skeleton key to exploiting a new zero-day.
Multiple Fortinet Products’ Forticloud SSO Login Authentication Bypass (CVE-2025-59718 & CVE-2025-59719)
With a critical CVSS Score of 9.1, Fortinet describes these as “Improper Verification of Cryptographic Signature” (CWE-347) flaws that allow an unauthenticated attacker to bypass the FortiCloud SSO login authentication using a crafted SAML message, if FortiCloud SSO is enabled on the device. Practically, this class of bug usually means the device is accepting a forged or improperly validated SAML assertion/response (e.g., failing to correctly validate the signature, trust chain, issuer/audience constraints, or allowing a signature-wrapping style bypass), so the attacker can present a SAML blob that the device treats as a valid login. Fortinet’s PSIRT also notes an important nuance: FortiCloud SSO isn’t enabled by default, but multiple researchers and incident responders observed that it can be enabled during registration flows unless explicitly disabled by the administrator.
This means attackers scan for exposed Fortinet admin interfaces where FortiCloud SSO is enabled, then send a crafted SAML message to the SSO login endpoint to authenticate without credentials. Arctic Wolf reports that they observed malicious activity shortly after disclosure and explicitly calls out the crafted SAML bypass behavior. Once authenticated as an admin (or admin-equivalent), the attacker can do the high-value stuff, such as:
- Pull system configuration
- Modify rules/policies
- Create new admin accounts or API tokens,
- Enable remote management features
BleepingComputer reports attackers are using this to gain unauthorized access and steal system configuration files, which can contain sensitive network topology, policy logic, and credential material (or credential artifacts) that accelerate lateral movement. CISA added CVE-2025-59718 to the KEV catalog based on evidence of active exploitation.
Eclypsium is able to detect the presence of this vulnerability in the environment.

HPE OneView Remote Code Execution (CVE-2025-37164)
HPE’s advisory is blunt: a remote unauthenticated user can exploit the CVSS 10 flaw to achieve remote code execution. All versions of HPE OneView prior to v11.00 are affected. The combination of remote and unauthenticated code execution is a nightmare since OneView is commonly deployed with broad privileges to orchestrate compute, storage, and network resources. The only solution is to patch, and patch quickly. But even after patching, organizations must conduct further investigations to ensure they have not already suffered an enterprise-wide compromise
Because the vendor bulletin is light on root-cause specifics, we can’t responsibly claim an exact primitive (e.g., deserialization vs. command injection) without additional primary detail. What we can say, grounded in what HPE confirms, is how exploitation typically plays out operationally: an attacker reaches a network-exposed OneView service (often its web/API interface), triggers the vulnerable code path to execute arbitrary code, and then uses that foothold to steal secrets, tamper with inventory/configuration, and push malicious changes downstream to managed infrastructure. The “management plane” angle matters: compromise isn’t just “one server,” it’s potentially control over provisioning, firmware baselines, network configurations, and stored credentials used to talk to your environment.
This vulnerability highlights the folly of fully entrusting network security to the vendor. Every other realm of technology has third-party compensating controls. But network technology is currently opaque, making it impossible to install agents or other protections.
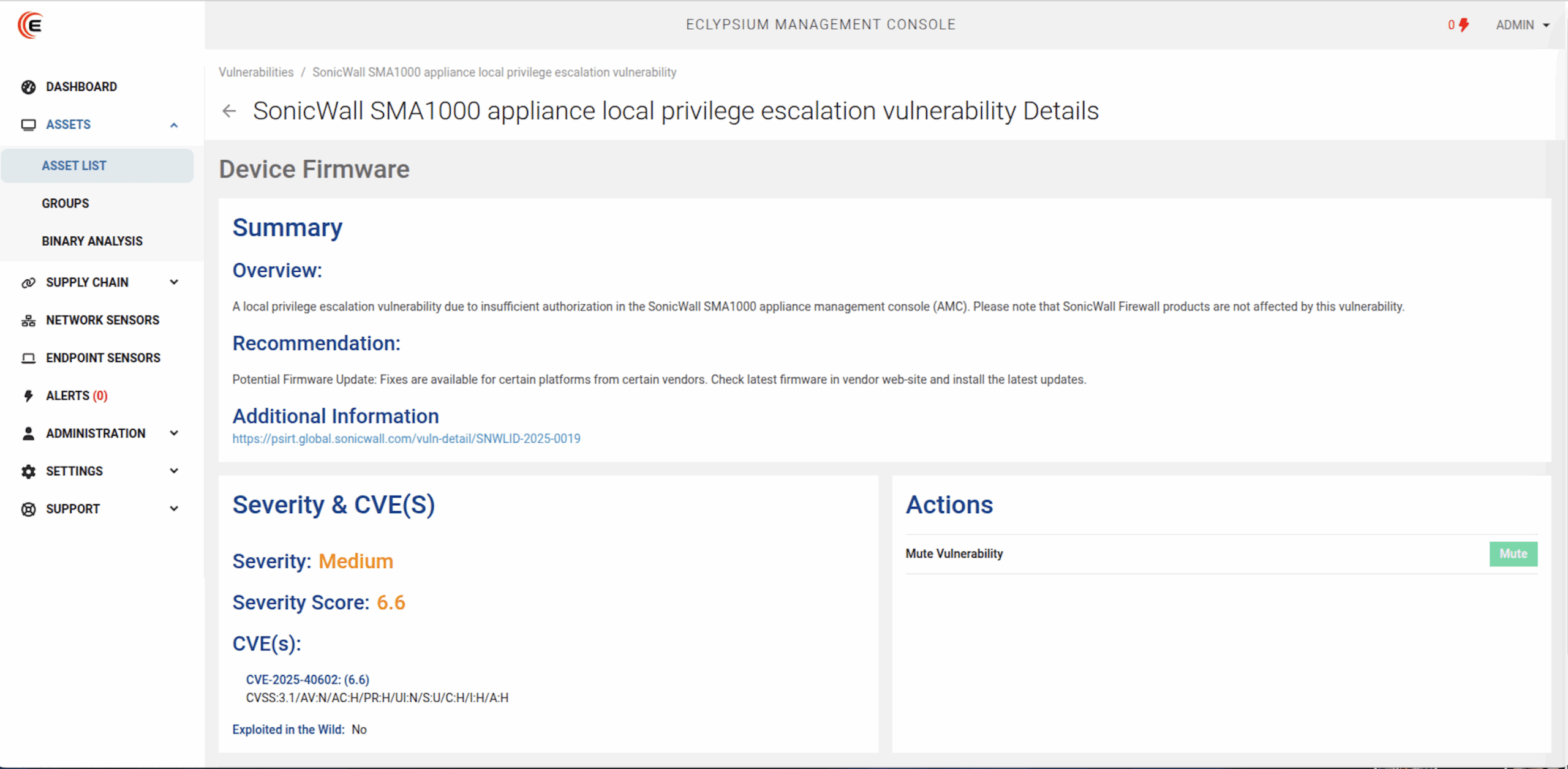
SonicWall SMA1000: Local Privilege Escalation Used in Zero-Day Attacks (CVE-2025-40602), chained with CVE-2025-23006
SonicWall’s PSIRT describes CVE-2025-40602 as a local privilege escalation caused by insufficient authorization in the SMA1000 Appliance Management Console (AMC), with a medium risk CVSS v3 score of 6.6.
On its own, that doesn’t sound so bad, but now multiple reports have emerged stating that attackers are chaining CVE-2025-40602 with CVE-2025-23006, a previously disclosed pre-auth deserialization flaw that can yield remote code execution. In other words, CVE-2025-23006 can get the attacker onto the box and CVE-2025-40602 can help them escalate privileges (up to root in reported chains), turning an initial foothold into complete appliance takeover.
BleepingComputer’s write-up captures the chain in concrete terms: remote unauthenticated attackers chained the LPE bug with the pre-auth deserialization flaw to execute arbitrary OS commands, and SonicWall acknowledges that CVE-2025-40602 was leveraged with CVE-2025-23006 to achieve unauthenticated RCE with root privileges under certain conditions.
CISA has added CVE-2025-40602 to the KEV catalog. Recommended mitigations include restricting SSH/management access to trusted admin networks and removing public exposure of the management interface.
This attack perfectly illustrates the sneaky and destructive potential of chaining exploits. Often, vulnerabilities that are not immediately actively exploited, or have low to medium risk scores, are deprioritized compared to the seemingly endless flood of critical vulnerabilities. Then, when an older, lower-risk vulnerability exposes a new critical attack, defenders are left scrambling.
Network Devices Give Attackers Everything, Everywhere, All At Once
The Mandiant M-Trends report for 2025 listed several VPN vulnerabilities across Ivanti and Palo Alto products as the top vulnerabilities exploited in incidents investigated by Mandiant. One cyberinsurer reported that, among its customers, using on-prem VPNs was associated with up to 6.8x the risk of a cyberattack compared to no VPN at all.
Why are these devices, which are often brought in to improve security and reduce risk, such a juicy target for attackers?
These systems sit at trust boundaries and often have broad visibility or authority over internal environments, as perfectly illustrated in the HPE OneView case. When cracks appear at the edge, such as authentication bypasses, unauthenticated RCE, misconfigurations, or exploitable zero-days, the impact is disproportionately valuable to attackers. A single weakness can translate into complete administrative control, lateral movement, or persistent access, which is why these bugs attract immediate attention from attackers.
Another common thread is speed. In multiple cases, exploitation followed disclosure within days, sometimes hours. This reflects a mature, well-resourced attacker ecosystem that actively monitors advisories, reverse-engineers patches, and quickly operationalizes exploits. It also highlights a recurring reality: disclosure is no longer the start of an extended grace period. Once details are public, defenders are racing adversaries who already understand how to weaponize the issue, especially when management interfaces are internet-reachable or widely deployed.
There’s also a pattern around complexity and feature creep. Eclypsium’s own analysis of network device update packages in 2025 found one that had grown in size by 10x over the past 2 years and by 100x since 2020. The same package had gone from zero Python imports to over 140, with at least one package having a known vulnerability. The undersecured, opaque embedded OS and firmware underlying network devices are increasingly exposed to risks in the open-source software supply chain.
SSO integrations, centralized management platforms, and layered access models expand the attack surface in subtle ways. Individually, some flaws might look narrow or require chaining, but in real environments those chains are practical. From a defender’s perspective, the takeaway is clear: edge devices and management platforms deserve top-tier patch priority, strict exposure controls, and continuous monitoring. Treat them less like appliances and more like critical servers—minimize enabled features, restrict management access, and assume that once a high-impact bug is disclosed, attackers are already moving.
What Needs To Change?
All three of these latest vulnerabilities require vendor patches and upgrades, as well as potential configuration changes and other compensating controls. And while there are oft-stated, obvious mitigations like “don’t expose management interfaces to the internet,” it is clear that a more systemic change is needed to counter the success attackers are having at the network edge.
- “Trust The Vendor” needs to evolve, or go away. Currently, network devices contain increasingly complex and risky embedded code. Whether you call it firmware or the underlying operating system, the code inside network devices is introducing risk that’s difficult to measure and manage. Requiring SBOMs and keeping a detailed inventory of all network appliances and their subcomponents is the first step in rapid remediation when these vulnerabilities are disclosed, until vendors start providing more transparency into these highly targeted devices.
- Treat network appliances as a source of risk: That means monitoring them and pointing threat detection capabilities at them, just as you would any endpoint. Unfortunately, this is often impossible by design. Vendors do not design their appliances to be monitored with EDR, vulnerability management, or other established security tool categories. Eclypsium brings in-depth, continuous monitoring to network appliances. Correlating VPN, firewall, edge access logs, SBOMs and other contextual data with active threat detection on network appliances can provide early warning to mitigate the growing risk of attacks.
- Use Proactive Compensating Controls – When the F5 breach was disclosed, it was revealed that 44 vulnerabilities had been known to attackers before F5 could disclose or patch them. Many organizations have established “n-1” firmware update protocols for their network gear to ensure their appliances remain up to date. But unless you’re actively monitoring the integrity of that firmware or the underlying operating system, you might never know when it’s compromised. Using third-party validation and vulnerability management tools not provided by the vendor is a crucial proactive step to ensure you know which vulnerabilities are in your environment and whether they’re being exploited, whether the vendor discloses them or not.
How Eclypsium Can Help
Eclypsium’s platform gives defenders the visibility and control they’ve long lacked over the hidden layers of network infrastructure. Eclypsium continuously monitors device firmware and underlying operating systems, configurations, and components that traditional tools can’t see.
By correlating deep device inventory with vulnerability, integrity, and threat intelligence, Eclypsium helps security teams detect exploitation attempts early across all types of devices, from firewalls, routers, and VPNs to more traditional workstations and servers. This kind of foundational visibility and automated protection is a force multiplier for defenders trying to stay ahead of the new network-edge exploitation strategy that attackers are pursuing with increasing intensity.
Try a self-guided tour of Eclypsium.






