The reputable and widely used Open Web Application Security Project (OWASP) Top 10 list just got its 8th update, and first update since 2021. One major and welcome change is that supply chain security has gone from not being a category at all to being the number three spot on the list. OWASP is shaking things up in other ways too, with one other new risk category and one consolidation.

Here’s OWASP’s own pithy illustration of what’s changed in this Release Candidate for the updated Top 10:
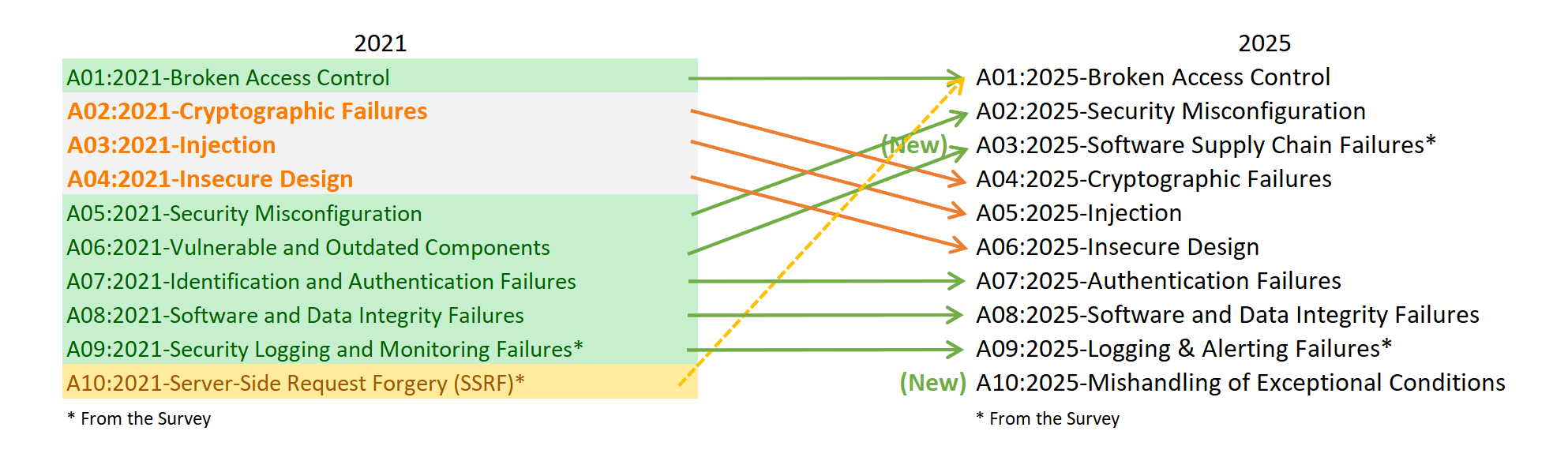
Many of the changes represent relatively minor shifts. Many entries have stayed the same. But there are also some notable changes that are worth a closer look.
Here’s what’s new, and what we think the most meaningful changes are in this foundational cybersecurity document.
What’s New in OWASP Top 10 – 2025
The two new categories in OWASP Top 10 – 2025 are as follows:
- A03:2025 – Software Supply Chain Failures is an expansion of A06:2021-Vulnerable and Outdated Components to include a broader scope of compromises occurring within or across the entire ecosystem of software dependencies, build systems, and distribution infrastructure. This category was overwhelmingly voted a top concern in the community survey. This category has 5 CWEs and a limited presence in the collected data, but we believe this is due to challenges in testing and hope that testing catches up in this area. This category has the fewest occurrences in the data, but also the highest average exploit and impact scores from CVEs.
- A10:2025 – Mishandling of Exceptional Conditions is a new category for 2025. This category contains 24 CWEs focusing on improper error handling, logical errors, failing open, and other related scenarios stemming from abnormal conditions that systems may encounter.
Expanding Vulnerable and Outdated Components into a broader supply chain category is a good move that reflects the broader conditions both of the technology environment and of the cyber threat landscape. Supply chain attacks have had massive impact on enterprises since the last OWASP update in 2021. The Log4J and XZUtils incidents painfully hammered home the risk in widespread usage of low-level open source packages. Meanwhile, the F5 breach and ongoing attacks on Cisco ASA devices, Palo Alto PAN-OS products, and other network edge devices demonstrates the risks inherent in the opaque supply chain of network edge and enterprise IT infrastructure products.
OWASP makes a notable caveat about the relatively low number of Common Weakness Enumerations (CWEs) in their Software Supply Chain Failures listing. This category only has 5 CWEs (the average across the top 10 is 24.8, and the highest is 40). 5 is the lowest number of CWEs mapped to a category, with the only other category having such a low number being A09-2025: Logging and Alerting Failures. In spite of the relatively low number of CWEs, the Supply Chain Failures item was “overwhelmingly voted a top concern in the community survey” with 50% of respondents ranking it their #1 concern.
Yet another wrinkle is that the category of Software Supply Chain Failures has the highest Average Weighted Impact. You can read how OWASP did the math on that here. Loosely, this means that the potential business impact of supply chain failures is extremely high even though the number of CWEs and CVEs associated with the category is relatively low. OWASP attributes this disparity to challenges in testing. Basically, it is harder to identify and categorize supply chain failures, but anyone who is watching the cybersecurity space can tell by looking that this category is having enormous impact.
OWASP Analysis Challenges Highlight Growing Cybersecurity Complexity
OWASP analyzes a phenomenal amount of data to come up with their top 10 list, and their description of the process highlights an industry-wide challenge in categorizing and describing cyber risks. There are hundreds of thousands of Common Vulnerabilities and Exposures (CVEs). OWASP extracted 220,000 of them that are mapped to CWEs, for their analysis. As the number of CVEs has increased enormously over the years, so has the number of CWEs. OWASP notes that the 2017 edition of the Top 10 had only 30 CWEs to work with. That number has grown nearly 10x, to 589 CWEs analyzed in the 2025 edition.
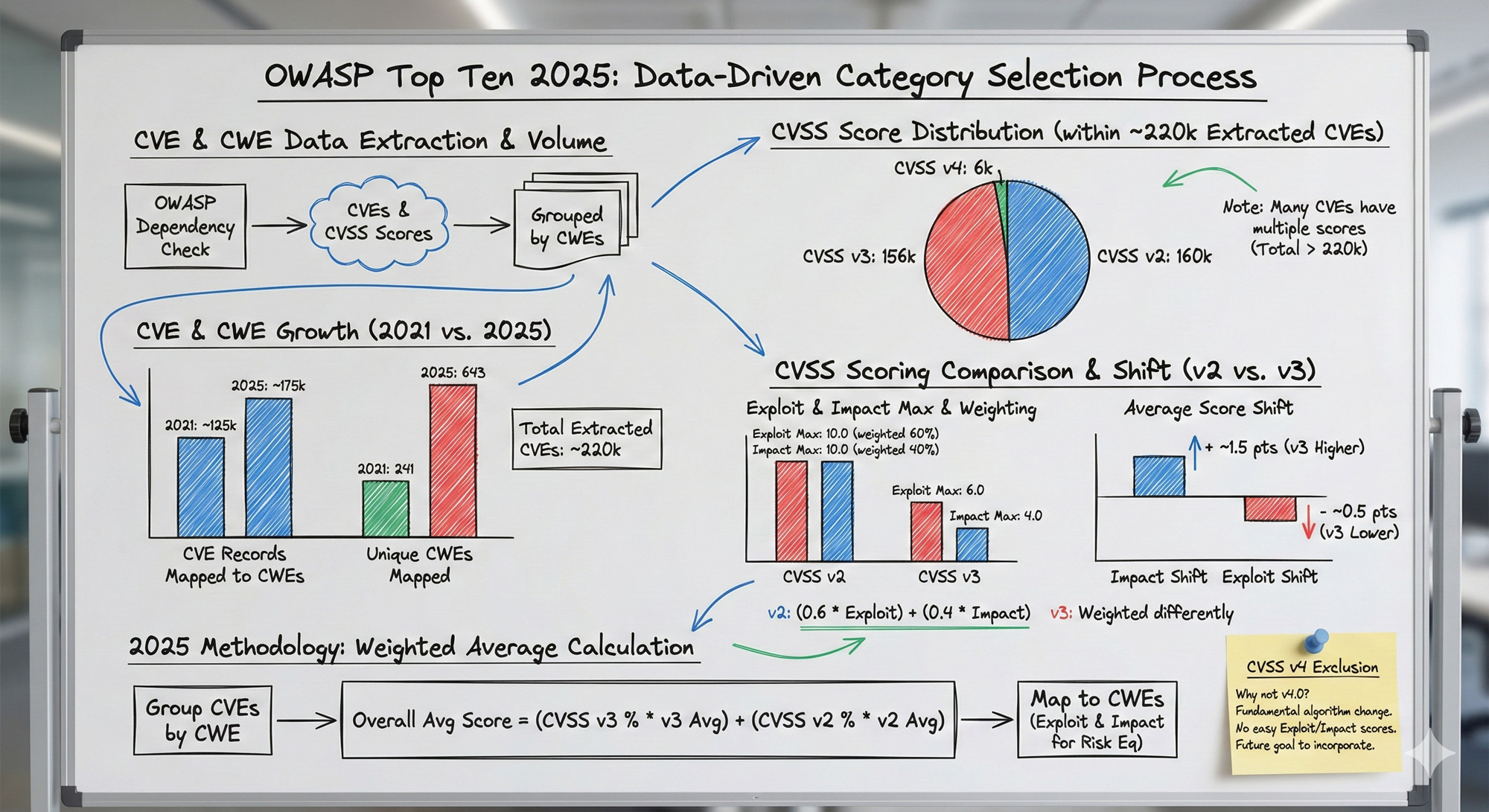
Beyond that, many CVEs receive a risk score in either CVSS 2.0, CVSS 3.0, or CVSS 4.0 format. These CVSS versions are different enough that it introduces significant challenges in coming up with a unified, easy-to-understand risk score or impact score for any category of vulnerability. OWASP did not incorporate CVSS 4.0 risk scores into their weighted averages because of the complexity of reconciling the data with the previous CVSS versions.
OWASP has been doing their Top 10 list for a lot of years. They are professionals. If they’re struggling to reconcile the various vulnerability databases and risk scoring methodologies, how are enterprise security teams supposed to keep up with these systems?
Mitigating Supply Chain Failure At Every Link
The OWASP Top 10 is primarily oriented toward builders of software. The Software Supply Chain Failure category is written to this audience, and the mitigations they offer are targeted at developers, DevOps professionals, CI/CD pipelines, etc.
But in 2025, with the addition of the Software Supply Chain Failures category, OWASP has expanded the relevance of the Top 10 list to enterprises that are the end users of technology that includes vulnerable, outdated, or unsupported software components that introduce risk.
This emphasis on the risks that third-party technology providers and vendors can introduce is more urgent now than ever. OWASP references the high profile SolarWinds example in their example scenarios of a supply chain security failure. And while the SolarWinds incident may seem like a distant memory, 2025 has already seen source code leaks from major technology vendors like F5 and LG. In the case of F5, the attackers gained access to 45 vulnerabilities that F5 had not yet disclosed and patched. The risk introduced by such incidents is yet to be fully measured. But these incidents are raising awareness, and causing enormous amounts of work inside enterprises that use the products. The impact of supply chain failures is not limited to actual cyberattacks. It is also manifested in the increasing complexity of monitoring, management, and incident response that takes a toll on enterprise IT infrastructure and security operations teams.
Furthermore, new laws such as the European Union’s Cyber Resilience Act are making supply chain security measures much more stringent. The need for visibility and security tools and expertise in organizations at every link in the supply chain for digital products has never been higher.
How Eclypsium Helps Reduce Risk from the Software and Hardware Supply Chain
Eclypsium supports enterprise security and IT infrastructure teams in monitoring their risk of supply chain attacks by providing:
- Complete inventory down to the component level of hardware, firmware, and software that is deployed in the environment, including endpoints, servers, and network edge devices.
- Vulnerability monitoring and management for devices EDR can’t monitor, such as VPNs, firewalls, load balancers, routers, and switches
- Active threat detection against threats living off the land in network infrastructure, where legacy security solutions can’t see
- Automated firmware updates and patching to mitigate supply chain risk deep in the components of the IT infrastructure.
To learn more about how Eclypsium protects our customers from software and hardware supply chain failures, check out our eBook: Eradicate Hidden Supply Chain Risks in Network Edge Devices or request a demo of the Eclypsium Supply Chain Security Platform.






