Researchers disclosed 9 vulnerabilities in the PXE environment within UEFI. Attackers need only be on the same network segment as the affected hosts to exploit.
What Is PixieFail?
The “PixieFail” vulnerabilities are a set of nine critical security flaws discovered in Tianocore’s EDK II IPv6 network stack. These vulnerabilities are primarily found in the Preboot Execution Environment (PXE) of the UEFI specification, which is crucial for network booting in enterprise systems. While PXE is more common in server environments, it is also used in desktop environments as well.
Vulnerability Details
The vulnerabilities affect the network boot process in the PXE environment, which is essential for loading operating systems from the network at boot time. All discovered vulnerabilities are within the DHCPv6 functionality as PXE relies on DHCP at boot time to obtain an IP address and discover the location of the OS image to load.
The PixieFail vulnerabilities are diverse and include integer underflows, buffer overflows, out-of-bounds reads, infinite loops, and the use of weak pseudorandom number generators. These flaws can lead to a range of exploits like remote code execution (RCE), denial-of-service (DoS) attacks, DNS cache poisoning, and sensitive data leakage.
Key vulnerabilities include improper handling of DHCPv6 Advertise messages leading to integer underflow (CVE-2023-45229), buffer overflows in the DHCPv6 client due to Server ID options (CVE-2023-45230 and CVE-2023-45235), and issues in parsing IPv6 Destination Options headers causing infinite loops (CVE-2023-45232 and CVE-2023-45233). Proof of concept scripts to detect the presence of the vulnerabilities are located here.
This type of exploit is particularly insidious as it occurs before the operating system loads, bypassing many traditional security measures such as antivirus software or operating system-level security features.
Impact and Severity
The PixieFail vulnerabilities are notable because they allow remote-code execution (RCE) given the attacker is on the same network. Eclypsium discovered early RCE vulnerabilities in UEFI, such as BIOSDisconnect, which only affected Dell systems. In contrast, the PixieFail flaws impact a wide range of vendors who utilize Tianocore’s EDK II UEFI implementation and its NetworkPkg module. At the time of this writing AMI, Insyde Software, Intel, and Phoenix Technologies are officially listed as affected. Microsoft, based on the disclosure timeline details, is also likely affected but has not updated the CERT KB with an official status.
The vulnerabilities were disclosed to the affected vendors, and coordinated efforts have been underway to address them (for full details, and perhaps one of the most interesting disclosure timelines published recently, see the Quarkslab post disclosure timeline section). However, as of the latest information, most vendor patches are still in testing or non-validated states, and Tianocore has provided fixes for the first seven vulnerabilities.
Detection and Mitigation
Importantly, attackers must have access to the same network as the target devices to exploit the PixieFail vulnerabilities. Quarkslab has released proof-of-concept (PoC) exploits to help network administrators detect vulnerable devices. IT teams are advised to stay updated with vendor communications and apply patches as they become available. These vulnerabilities underscore the importance of rigorous security practices in network boot environments. Additional countermeasures include applying firmware updates when available, network monitoring to detect exploitation attempts, and monitoring usage of PXE (especially DHCPv6 traffic).
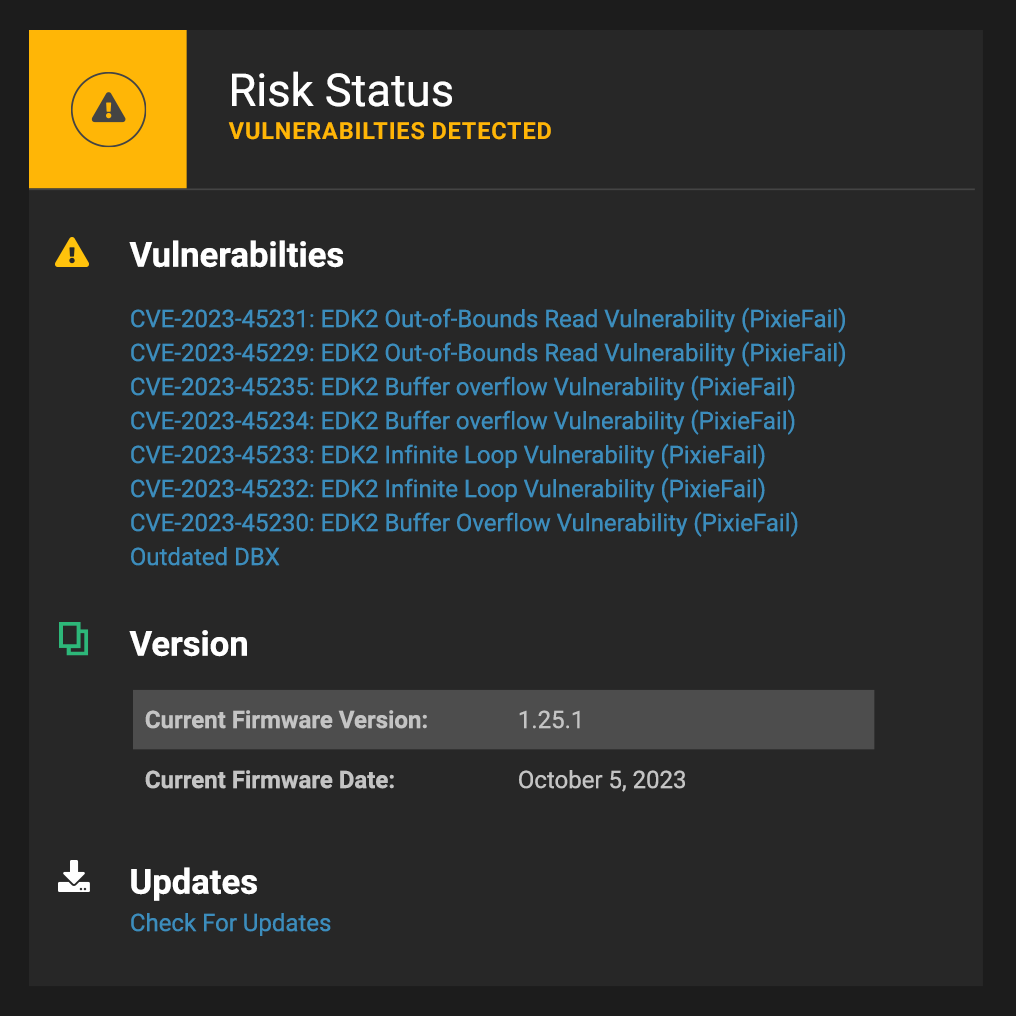
In light of the critical vulnerabilities identified as “PixieFail,” it’s worth noting that Eclypsium’s supply chain security platform was already equipped to detect these threats, offering immediate protection to its customers. This capability underscores Eclypsium’s commitment to proactive security measures and its ability to safeguard enterprise environments against evolving threats. By leveraging Eclypsium’s advanced detection tools, organizations can swiftly identify and mitigate vulnerabilities such as PixieFail, ensuring the integrity of their UEFI firmware against potential exploits. This demonstrates the tangible value Eclypsium brings to its customers through continuous security intelligence and cutting-edge protection features. Contact us for a demo of these capabilities.
Complexity in the UEFI Supply Chain
In August 2023 (coincidentally, the same month that Quarkslab started the PixieFail disclosure process), the UEFI Forum published a white paper titled, Decoding UEFI Firmware Unraveling the Intricacies of System Firmware, its Ecosystem and Supply Chain. The paper is worth a read if you want to understand the complex web of suppliers involved in producing finished UEFI-compliant firmware. As illustrated with the PixieFail vulnerabilities, software defects can have cascading results that are difficult to remediate. The paper summarizes the challenge, “The flexibility of the UEFI standard has helped this dynamic ecosystem evolve by supporting this model, but it also contributes to the difficulty of responding to security vulnerabilities.”
The diagram below shows how the PixieFail vulnerabilities in the EDK II NetworkPkg IP stack has a wide-reaching impact on downstream component suppliers and OEMs.







