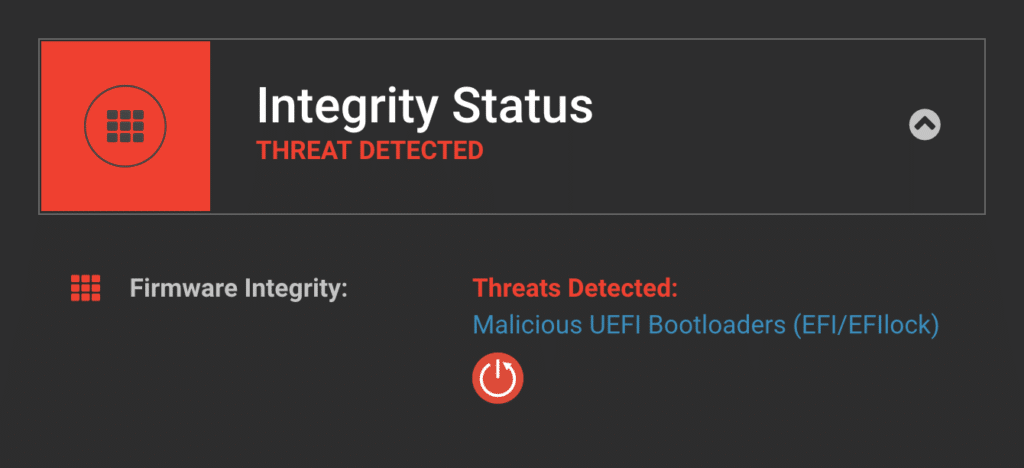
ESET researchers have recently identified a new ransomware technique being used in the wild in which attackers replace the victim’s legitimate bootloader with a malicious version. The malicious bootloader prevents the compromised computer from completing the boot process at which point the attacker demands payment to recover the device.
It is important to note that this EFILock attack only affects systems that are not protected by Secure Boot as the malicious bootloader is unsigned. With Secure Boot enabled, the unsigned bootloader would be blocked from executing and thus no ransomware message would be shown to the user.
This style of threat underscores both the critical importance of Secure Boot as well as the damaging power of vulnerable or malicious bootloaders. The integrity of the boot process is one of the most critical aspects of security for any device. In general, the earlier code is loaded, the more privileged it is because it has the potential to alter the code that is run after it. For example, if the boot process is compromised, attackers can gain control over the operating system and subvert all higher-layer security controls on the device.
Defending Against Threats to the Boot Process
Organizations need the ability to detect and respond to weaknesses and threats at this level. One key step is to ensure that all devices in the environment have Secure Boot enabled. Additionally, teams need to be aware of vulnerabilities that could affect the boot process such as vulnerable bootloaders. Organizations also need to validate the integrity of their bootloaders and components to detect the presence of malicious code.
Eclypsium’s device security platform can automate the discovery of misconfigurations, vulnerabilities, and threats to the boot process. If vulnerabilities are found, the system can remotely patch systems to mitigate the risk. Likewise, any changes to integrity can generate alerts and trigger automated responses via the Eclypsium API.
To learn more about malicious bootloaders or about protecting your devices, contact the Eclypsium team at [email protected].





