Earlier this year, researchers at FireEye disclosed a series of attack campaigns attributed to the Chinese hacking group known as APT41. These attacks were notable both for their scale as well as the technologies that they targeted. FireEye researchers described the attacks as “one of the most widespread campaigns we have seen from China-nexus espionage actors in recent years”, and noted that a wide range of industries and geographies were affected.
The attacks targeted a variety of enterprise technologies including Cisco routers, Citrix Application Delivery Controllers, and Zoho IT Management.
- The attacks against Citrix infrastructure took advantage of CVE-2019-19781 which affects the Citrix ADC (formerly NetScaler ADC) and Citrix Gateway. After using the vulnerability to gain code execution, attackers then downloaded backdoors to the affected systems. The installation of backdoors was observed by FireEye and corroborated by other 3rd party analysis.
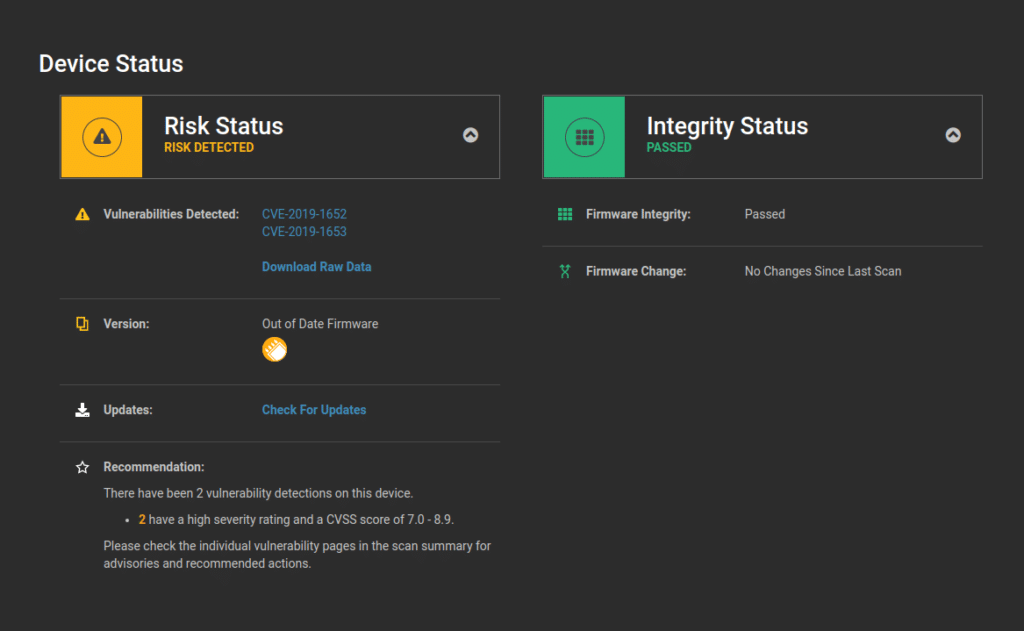
- APT41 also targeted Cisco RV320 and RV325 WAN VPN routers using CVE-2019-1652 and CVE-2019-1653. These vulnerabilities allowed remote unauthenticated attackers to obtain a router’s configuration information and gain full control over the device. Attackers in addition to APT41 have been observed scanning for and exploiting these vulnerabilities to compromise Cisco routers.
- The Zoho ManageEngine Desktop Central was targeted via CVE-2020-10189. Once exploited, attackers were observed installing multiple backdoors including Cobalt Strike BEACON as well as Meterpreter. Compromising the ManageEngine Desktop Central would allow attackers to spread to other systems managed by the solution.
These vulnerabilities are particularly significant because they target high-impact components of an enterprise’s infrastructure that could cause significant damage if compromised. They are also vulnerabilities that can be easily overlooked when IT teams are overburdened patching traditional laptops and servers.
The Eclypsium device protection platform provides the ability to automatically detect these and many other similar vulnerabilities in network devices and other enterprise infrastructure. The solution uses a variety of techniques to scan the local environment for vulnerable systems and can even actively confirm if a system is vulnerable to exploitation.